Asus Confirms Supplier Breach After Everest Ransomware Claims 1TB Data Theft
Major tech manufacturer faces supply chain attack exposing critical phone camera source code
December 8, 2025
Asus, one of the world's largest computer hardware manufacturers, has confirmed a significant cybersecurity incident affecting one of its suppliers after the Everest ransomware group claimed to have stolen over one terabyte of sensitive data from the company. The breach, which involves proprietary camera technology for Asus smartphones, represents another stark example of how supply chain vulnerabilities continue to plague even the most prominent technology companies.
The Breach: What We Know
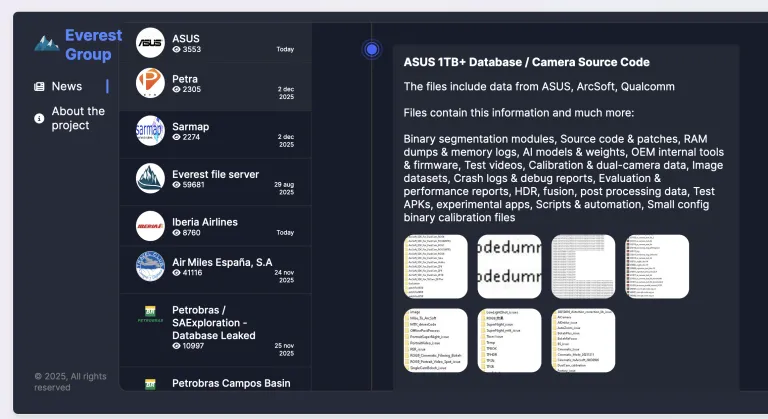
On December 2, 2025, the Everest ransomware group added Asus to its dark web leak site, announcing it had exfiltrated more than 1TB of data from the company. The stolen information allegedly includes complete camera source code, internal development tools, and sensitive technical documentation related to Asus's smartphone camera systems.
According to screenshots published by Everest as proof of the breach, the compromised data includes:
- Complete camera-related source code and internal patches
- Software development kits (SDKs) for multiple Asus ROG phone models (ROG 5, ROG 6, ROG 7, and ZF series)
- Qualcomm chipset-specific test patches
- AI models and their associated weights
- RAM dumps and segmentation modules
- Camera tuning configurations and post-processing scripts
- Test videos, calibration data, and dual-camera information
- Debug reports, crash logs, and evaluation documents
- Experimental applications and internal tools
The attack also appears to have affected Asus's technology partners, with references to ArcSoft (a major imaging software provider) and Qualcomm appearing in the leaked file structures.
Asus's Response
Following the public disclosure by Everest, Asus issued a carefully worded statement confirming the incident while attempting to minimize concerns about its impact:
"An ASUS supplier was hacked. This affected some of the camera source code for ASUS phones. This incident has not impacted ASUS products, internal company systems, or user privacy. ASUS continues to strengthen supply chain security in compliance with cybersecurity standards."
Notably, Asus declined to name the compromised supplier or specify exactly what code was taken. The company emphasized that the breach occurred at a third-party vendor rather than within Asus's own infrastructure, and maintained that customer data and internal systems remain secure.
The Everest Ransomware Group
The attack bears the hallmarks of Everest, a sophisticated Russian-speaking cybercriminal organization that has been active since late 2020. The group has evolved significantly over the past five years, transitioning from traditional ransomware operations to a hybrid model that combines data theft, extortion, and initial access brokering.
Key Characteristics of Everest:
Operational Evolution: Everest initially operated as a standard ransomware group, encrypting victim files and demanding payment for decryption keys. However, the group has increasingly shifted toward "data-only" extortion, stealing sensitive information and threatening to leak or sell it without necessarily deploying encryption malware.
High-Profile Targeting: The group has claimed responsibility for attacks on major organizations across multiple sectors, including Under Armour, Sweden's power grid operator Svenska Kraftnät, Petrobras (Brazil's state oil company), Dublin Airport, and Collins Aerospace. In 2025 alone, Everest has claimed over 100 victims.
Attack Methods: Everest typically gains initial access through:
- Exploitation of vulnerable Remote Desktop Protocol (RDP) services
- Compromised or stolen credentials purchased from other cybercriminals
- Corporate insider recruitment programs (launched in October 2023)
- Vulnerable file transfer systems and VPN services
- Weak or default passwords on internet-facing systems
Monetization Strategy: Beyond demanding ransoms from victims, Everest operates as an Initial Access Broker (IAB), selling network access to other threat actors. The group maintains a dark web leak site where it publishes stolen data and offers it for sale. In the Asus case, Everest set a minimum price of $700,000 for the stolen database.
The Supply Chain Vulnerability
This incident highlights a critical and growing threat in cybersecurity: supply chain attacks. Rather than directly targeting well-defended organizations, threat actors increasingly focus on compromising suppliers, vendors, and partners that may have weaker security postures but maintain trusted connections to high-value targets.
Why Supply Chain Attacks Are Surging:
According to recent cybersecurity research, third-party involvement in data breaches has doubled in the past year, rising from 15% to 30% of all breaches. The average cost of a data breach now exceeds $4.4 million globally, with supply chain-related incidents often costing more and taking longer to resolve.
Several factors contribute to this trend:
Trust Exploitation: Attackers leverage the implicit trust between organizations and their suppliers. Once inside a supplier's network, threat actors can access multiple downstream customers through legitimate connections.
Weakest Link Strategy: Organizations often implement robust security measures for their own infrastructure while failing to adequately vet or monitor third-party suppliers. A single compromised vendor can create a pathway into dozens or hundreds of organizations.
Complexity and Visibility Gaps: Modern supply chains involve multiple tiers of suppliers (third-party, fourth-party, and beyond), making it extremely difficult to maintain visibility and enforce consistent security standards across the entire ecosystem.
Access Requirements: Suppliers often require privileged access to customer systems, data, and networks to provide their services, creating numerous potential entry points for attackers.
Implications of the Asus Breach
While Asus maintains that the breach has not affected end users or product security, cybersecurity experts warn that the theft of complete camera source code carries significant risks:
Vulnerability Discovery: With access to complete source code, security researchers (or malicious actors) could analyze the code to identify previously unknown vulnerabilities. Any security flaws discovered could potentially be exploited across all devices using the compromised camera modules.
Intellectual Property Loss: Camera technology represents significant research and development investment. The leaked source code could provide competitors with insights into Asus's proprietary imaging algorithms, AI models, and technical approaches.
Partner Exposure: The apparent inclusion of code and data related to ArcSoft and Qualcomm suggests the breach may have exposed sensitive information belonging to multiple companies in the supply chain, potentially requiring coordinated incident response across multiple organizations.
Firmware and Driver Risks: As noted by cybersecurity expert Nicola Vanin, the theft of firmware-level code creates risks beyond the camera itself. Vulnerabilities in camera drivers or firmware could potentially serve as entry points for broader system compromise.
Industry Context: A Pattern of Supply Chain Attacks
The Asus incident is far from isolated. 2025 has seen a dramatic surge in supply chain attacks, with incidents occurring at roughly twice the rate observed in early 2024. Some notable recent examples include:
- CDK Global (2024): Ransomware attack on software provider affected nearly 15,000 North American car dealerships
- Collins Aerospace (September 2025): Everest compromised the aviation supplier, causing disruptions at major European airports including Heathrow, Brussels, and Berlin
- Under Armour (October 2025): Everest leaked customer information after breaching the athletic apparel company
- MOVEit Transfer (2023): Vulnerability in file transfer software affected hundreds of organizations globally
According to Cyble Research, supply chain attacks began surging in April 2025, with 31 incidents reported that month alone. Since then, such attacks have averaged 26 per month—double the rate seen from January through March 2025.
The Regulatory Response
The increasing frequency and severity of supply chain attacks has prompted regulatory action. New regulations introduced in 2025 hold organizations directly accountable for third-party breaches:
- DORA (EU): Digital Operational Resilience Act requires financial institutions to assess and manage cybersecurity risks associated with third-party service providers
- NIS2 (EU): Updated Network and Information Security Directive expands requirements for supply chain security
- NIST Frameworks (US): Cyber Supply Chain Risk Management (C-SCRM) guidance emphasizes continuous monitoring and vendor oversight
- HIPAA, PCI DSS, ISO 27001: Various frameworks increasingly require proof of vendor oversight and supply chain security
Organizations that fail to adequately secure their supply chains now face not only operational disruption and data loss but also potentially costly fines and legal action.
Best Practices for Supply Chain Security
The Asus breach underscores the critical importance of robust supply chain security programs. Organizations should consider implementing the following measures:
Vendor Risk Management:
- Rigorous Due Diligence: Conduct thorough security assessments before onboarding any vendor, evaluating their cybersecurity controls, incident response capabilities, and adherence to relevant standards (NIST, ISO 27001, SOC 2)
- Continuous Monitoring: Implement ongoing monitoring of vendor risk rather than relying solely on point-in-time assessments
- Security Requirements: Include specific cybersecurity requirements in vendor contracts, with clear consequences for non-compliance
- Regular Audits: Perform periodic security audits and penetration testing of vendor access points
Technical Controls:
- Multi-Factor Authentication: Enforce MFA for all remote access, vendor connections, and privileged accounts
- Network Segmentation: Limit lateral movement by properly segmenting networks and restricting vendor access to only necessary systems
- Access Monitoring: Deploy security information and event management (SIEM) systems to detect unusual activity from third-party accounts
- Software Bill of Materials (SBOM): Maintain detailed inventories of all third-party components and dependencies, enabling rapid vulnerability identification
Operational Practices:
- Incident Response Planning: Include supply chain breach scenarios in incident response playbooks and conduct regular tabletop exercises
- Data Resilience: Implement immutable, air-gapped backup strategies that protect against ransomware and extortion attempts
- Threat Intelligence: Monitor dark web forums and threat intelligence feeds for indicators of compromise affecting suppliers
- Communication Channels: Establish clear protocols for security communication with vendors to enable rapid threat containment
Governance and Compliance:
- Supply Chain Security Policy: Develop comprehensive policies addressing third-party risk management
- Executive Oversight: Ensure C-level executives understand supply chain risks and allocate appropriate resources
- Compliance Alignment: Map vendor security requirements to relevant regulatory frameworks
- Transparency: Maintain transparency with customers about supply chain security measures and incident response capabilities
Looking Ahead
As organizations become increasingly interconnected and dependent on complex supply chains, supply chain attacks will likely continue to grow in frequency and sophistication. Cybersecurity Ventures projects that the global annual cost of software supply chain attacks will reach $60 billion in 2025.
The Asus incident serves as a reminder that even major technology companies with substantial security resources can fall victim to supply chain compromises. The attack's success stemmed not from weakness at Asus itself, but from a vulnerability at one of its suppliers—highlighting that organizational security is truly only as strong as the weakest link in the supply chain.
For Asus, the immediate priority will be working with the compromised supplier to understand the full scope of the breach, assess potential impacts, and implement remediation measures. The company will also need to determine whether any vulnerabilities exist in products that incorporate the stolen code and take appropriate action to protect customers.
More broadly, the incident reinforces the urgent need for organizations across all sectors to elevate supply chain security from a compliance checkbox to a strategic imperative. As threat actors like Everest continue to refine their techniques and target the supply chain as the path of least resistance, organizations must respond with more sophisticated approaches to third-party risk management, continuous monitoring, and collaborative defense.
Key Takeaways
- Supply chain attacks are accelerating: Third-party breaches have doubled to 30% of all incidents, with attacks occurring at twice the normal rate in 2025
- Everest remains highly active: The Russian-speaking group has claimed over 100 victims in 2025, targeting critical infrastructure, major corporations, and technology suppliers
- Source code theft carries significant risks: While Asus maintains no customer impact, the stolen camera code could enable vulnerability discovery and intellectual property theft
- Supplier relationships require scrutiny: Organizations must implement rigorous vendor security assessments, continuous monitoring, and clear contractual requirements
- Regulations are tightening: New compliance requirements hold organizations accountable for third-party breaches, making supply chain security a legal imperative
- Proactive defense is essential: Effective supply chain security requires moving beyond periodic assessments to continuous monitoring, threat intelligence, and coordinated incident response
The Asus supplier breach represents another data point in an alarming trend. As the threat landscape continues to evolve, organizations that fail to adequately secure their supply chains will find themselves at increasing risk of significant financial loss, reputational damage, and regulatory penalties.
For more cybersecurity insights and breach coverage, visit breached.company and compliancehub.wiki