Briefing: 2025 Cybersecurity Threat Landscape and Incident Analysis
Executive Summary
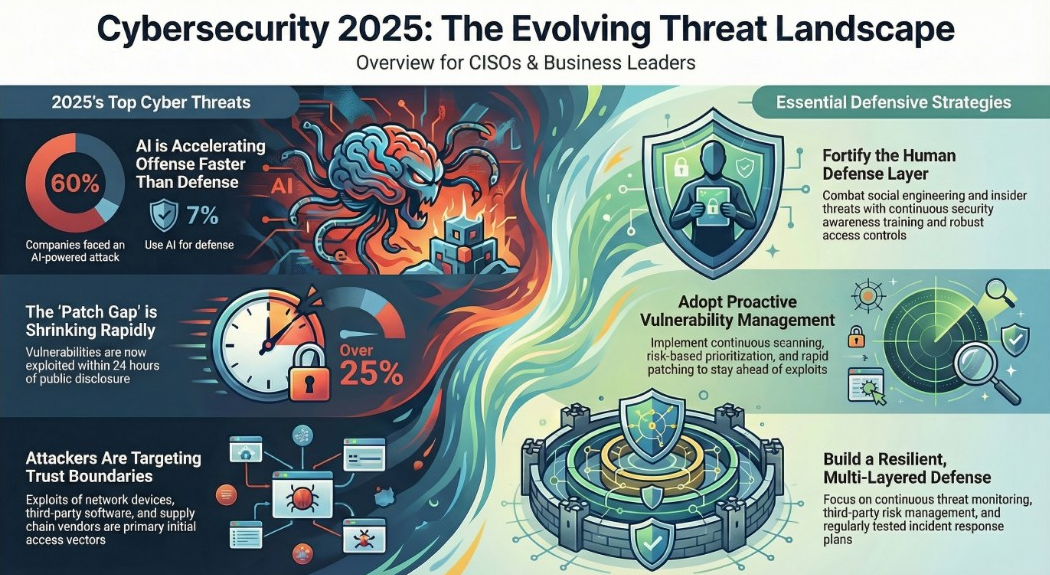
The 2025 cybersecurity landscape is characterized by an escalating velocity and sophistication of attacks, with adversaries leveraging artificial intelligence, exploiting supply chain dependencies, and systematically targeting critical infrastructure. A global survey by Boston Consulting Group found that 60% of companies believe they experienced an AI-powered cyberattack in the past year, yet only 7% have deployed AI-enabled defenses, highlighting a significant capabilities gap.
Key trends indicate that threat actors are operating at a global scale, with ransomware remaining a dominant and increasingly costly threat. Data from KELA shows that between January and September 2025, ransomware incidents surged to 4,701, with half of these attacks targeting critical infrastructure sectors like manufacturing, healthcare, and energy. Third-party and supply chain compromises have become a primary initial access vector, responsible for 44% of all breaches in 2025, a sharp increase from 32% in the previous year.
Nation-state actors from Russia, China, North Korea, and Iran continue to conduct espionage, disruption, and financially motivated campaigns, often targeting critical services and using hacktivist groups as proxies. Concurrently, regulatory pressure is intensifying, with agencies like the SEC increasing enforcement and frameworks such as CMMC 2.0 and CISA's Cybersecurity Performance Goals 2.0 setting new baselines for resilience. In this environment, passive defense is obsolete; survival depends on proactive, multi-layered security strategies that include robust third-party risk management, continuous monitoring, and a deep focus on mitigating insider threats and social engineering.
I. The Evolving Threat Landscape in 2025
Analysis of incidents throughout 2024 and 2025 reveals a threat environment defined by rapid adaptation, strategic targeting of systemic weaknesses, and the weaponization of emerging technologies.
Increased Sophistication and Scale
Cyberattacks in 2025 have become faster to execute and more global in scope. Nation-state actors are leveraging cyber capabilities to target multinational corporations, critical infrastructure, and international supply chains. These operations often involve cross-border collaboration between state-sponsored actors, cybercriminal groups, and hacktivists, presenting significant challenges to international cybersecurity efforts.
The Proliferation of Artificial Intelligence (AI)
AI has emerged as a transformative force for both attackers and defenders. A report from Boston Consulting Group, AI Is Raising the Stakes in Cybersecurity, indicates that AI is accelerating offense faster than defense.
- Offensive AI: Attackers use AI to enhance tactics like ransomware, sophisticated phishing campaigns, voice cloning, and deepfake video fraud, making threats "faster, more deceptive, and more scalable."
- Defensive AI: While 88% of organizations plan to deploy AI-enabled defense tools, only 7% have done so. This adoption lag leaves most companies "stuck with outdated tools and underfunded strategies, leaving them highly exposed."
As stated by Vanessa Lyon, global director of BCG’s Center for Leadership in Cyber Strategy, "Attackers are moving at machine speed. The only winning strategy is to meet autonomy with autonomy."
Dominance of Ransomware and Data Extortion
Ransomware has evolved into a systemic threat to national resilience. Financially motivated threat clusters like UNC5227 and the affiliates of REDBIKE (aka Akira) have been highly active, often using a double-extortion model of encrypting data and exfiltrating it for public release if the ransom is not paid.
- Attack Volume: Between January and September 2025, there were 4,701 recorded ransomware incidents, a significant increase from 3,219 during the same period in 2024.
- Critical Sector Targeting: 50% of all 2025 ransomware attacks (2,332 incidents) targeted critical infrastructure sectors, a 34% year-over-year increase in the number of attacks on these industries. The manufacturing sector saw the steepest growth, with attacks surging 61% from 520 to 838 incidents.
II. Primary Attack Vectors and Vulnerabilities
Adversaries continue to rely on a combination of technical exploits and human manipulation to gain initial access, with supply chains and insider threats representing expanding areas of risk.
Third-Party and Supply Chain Compromises
Attacks targeting supply-chain partners, vendors, and software providers have become a primary infiltration method, allowing threat actors to bypass traditional perimeter defenses. This vector was responsible for 44% of breaches in 2025.
- Software Vulnerabilities: The Boeing breach (October 2023) was traced to a vulnerability in Citrix’s software (Citrix Bleed), which was exploited by the LockBit 3.0 ransomware group. The Western Alliance Bank breach (March 2025) stemmed from a zero-day vulnerability in a secure file transfer tool from Cleo, exploited by the Clop ransomware group.
- Compromised Service Providers: The attack on multinational energy firm Schneider Electric (January 2024) by the Cactus group compromised its Sustainability Business Division, which provides consulting services to high-profile companies like PepsiCo, Walmart, and Hilton, exposing sensitive data related to their industrial control systems. Similarly, breaches at Marks & Spencer, Harrods, and Volvo Group all originated from compromised third-party vendors.
- SaaS Platform Exploits: A major 2025 campaign saw hackers compromise OAuth tokens for the Salesloft Drift application, granting them unauthorized access to the Salesforce environments of hundreds of customers, including Google, TransUnion, and Stellantis.

Insider Threats
Data breaches originating from within an organization remain a significant concern, driven by motives ranging from financial gain to treachery.
- Malicious Insiders: In March 2024, a Google software engineer, Linwei Ding, exploited his insider access to steal 500 confidential files related to the company's AI chip designs and supercomputing data centers.
- Compromised Insiders: In a breach disclosed in May 2025, overseas customer support contractors for Coinbase were bribed to leak the personal data of nearly 70,000 users.
- State-Sponsored Infiltration: Mandiant tracks a unique insider threat, UNC5267, involving North Korean IT workers who use stolen or fabricated identities to gain employment at Western companies. Their goal is to generate revenue for the North Korean regime, and their elevated access presents a significant risk of data theft and extortion.
Credential Theft and Social Engineering
Phishing and credential abuse remain top initial access methods. Infostealer malware, which collects sensitive user information like credentials and browser cookies, has become a primary enabler for major intrusions.
- Snowflake Campaign: Beginning in April 2024, the threat actor UNC5537 used credentials stolen primarily via infostealer malware to access the Snowflake customer instances of multiple organizations, including Ticketmaster (560 million customers affected).
- Social Engineering: A social engineering scam targeting an employee led to a data breach at DoorDash in October 2025, exposing customer contact information. The threat group Scattered Spider has been particularly effective at using social engineering to trick IT help desks into granting system access, bypassing MFA protections.
Exploitation of Known and Zero-Day Vulnerabilities
Attackers continue to exploit software flaws, with privilege escalation vulnerabilities being a key focus. Satnam Narang, a research engineer at Tenable, noted, “For the past two years, elevation of privilege flaws have led the pack and, so far in 2025, account for over half of all zero-days exploited.” A notable example is CVE-2025-29824, a zero-day flaw in the Windows Common Log File System (CLFS) exploited by the group Storm-2460 to deploy ransomware.
III. High-Impact Incidents and Sector-Specific Threats
The strategic targeting of critical infrastructure and the sheer scale of data exposure in mega-breaches defined the impact of cyber incidents in 2025.
Targeting of Critical Infrastructure
The FBI’s Internet Crime Complaint Center (IC3) has identified healthcare as the most frequent target of ransomware attacks among 16 critical sectors. State-sponsored groups have also demonstrated both the capability and intent to disrupt essential services.
- Healthcare: A ransomware attack on Ardent Health Services (November 2023), which operates 30 hospitals, forced the diversion of emergency room patients and the rescheduling of medical procedures in at least three states.
- Water Systems: The U.S. Department of Justice indicted Victoria Eduardovna Dubranova for her role in the Russian GRU-funded group CyberArmyofRussia_Reborn (CARR). The group is accused of tampering with public drinking water systems across several U.S. states, causing damage to controls and spilling hundreds of thousands of gallons of water. Craig Pritzlaff of the EPA stated, "These criminal charges serve as an unequivocal warning to malicious cyber actors... EPA’s Criminal Investigation Division... will not tolerate threats to our nation’s water infrastructure."
- Finance: A ransomware attack on ICBC Financial Services (November 2023) disrupted the clearing of U.S. Treasury trades, temporarily leaving the brokerage owing BNY Mellon $9 billion and highlighting the systemic risk of cyber incidents in interconnected financial markets.
- Transportation and Logistics: A cyberattack on DP World Australia (November 2023), one of the country's largest port operators, shut down port operations for three days and created a backlog of approximately 30,000 shipping containers.
Notable Data Breaches and Mega-Incidents (2024-2025)
The period saw several breaches of unprecedented scale, exposing the personal information of billions of individuals worldwide.
Victim Organization | Date of Incident/Disclosure | Impact | Attack Vector / Cause |
Chinese Surveillance Network | June 2025 | 4.0 billion records leaked (addresses, biometric data) | Publicly exposed police and surveillance databases |
National Public Data Broker | April 2024 | 2.9 billion records of US, UK, Canadian citizens | Undisclosed breach; data included SSNs and addresses |
Ticketmaster | May 2024 | 560 million customers (personal & payment info) | Credential stuffing on a Snowflake data warehouse account |
UnitedHealth | February 2024 | 192.7 million people | BlackCat ransomware attack via compromised Citrix portal |
PowerSchool | Late 2024 / Early 2025 | 62 million students & 10 million teachers | Stolen contractor credentials |
Mr. Cooper | October 2023 | 14.7 million customers, $25M in costs | Ransomware attack |
Marks & Spencer | April 2025 | 16.9 million customers, $27M in costs | Cyberattack linked to Scattered Spider |
700Credit | May-Oct 2025 | 5.8 million records (SSNs, names, addresses) | Unauthorized access to web application 700Dealer.com |
TransUnion | July 2025 | 4.4 million individuals | Third-party application breach |
IV. Regulatory, Legal, and Governmental Response
Governments and regulatory bodies have responded to the escalating threat environment with new frameworks, increased enforcement, and international law enforcement actions.
Updated Cybersecurity Frameworks
In December 2025, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) released Cybersecurity Performance Goals (CPG) 2.0. This update aligns with the NIST Cybersecurity Framework (CSF) 2.0 and introduces a new "Govern" function to integrate leadership accountability and risk management into cybersecurity practices. CPG 2.0 also includes new goals to address threats from third-party providers and emphasizes zero-trust principles. For organizations in the defense supply chain, compliance with CMMC 2.0 remains a critical requirement.
Regulatory and Enforcement Activity
The U.S. Securities and Exchange Commission (SEC) continues to prioritize cybersecurity.
- In February 2025, the SEC created a Cyber and Emerging Technologies Unit (CETU) to combat cyber-related misconduct.
- The SEC's Division of Examinations views cybersecurity as a "perennial examination priority," with a new focus on security controls related to artificial intelligence.
- The agency voluntarily dismissed its lawsuit against SolarWinds and its CISO in late 2025 after a federal judge dismissed the SEC's novel theory that cybersecurity control deficiencies violated statutory internal accounting controls requirements.
Law Enforcement and International Actions
The U.S. government has taken direct action against state-sponsored threat actors. The FBI's Operation Red Circus is an ongoing effort to disrupt Russian state-sponsored cyber threats. As part of this, the Department of Justice unsealed indictments against Victoria Dubranova for her role in attacks by the Russian-backed groups CARR and NoName057(16). The U.S. Treasury has also sanctioned other CARR members for their roles in cyber operations against U.S. critical infrastructure.
V. Key Defensive Strategies and Recommendations
The source materials collectively outline a strategic shift from reactive defense to proactive, resilient security postures. Key recommendations include:
- Implement Robust Third-Party Risk Management (TPRM): Organizations must establish formal processes to assess the security posture of vendors, ensure they meet security requirements, and monitor their compliance over time. This includes reviewing vendor due diligence and contractual safeguards.
- Adopt Zero Trust and Secure-by-Design Principles: Restrict access based on verified necessity, not assumed trust. All access requests should be evaluated for compromise indicators before authentication tokens are issued. Systems should be built with security as a foundational component, not an add-on.
- Strengthen Identity and Access Management: Enforce phishing-resistant multi-factor authentication (MFA) methods, such as hardware security keys. Implement cookie expiration and password rotation policies to limit the lifespan of compromised credentials.
- Enhance Security Awareness Training: Educate all employees, especially IT and help desk teams, on social engineering tactics like phishing and impersonation to prevent attackers from gaining an initial foothold.
- Develop and Test Incident Response Plans: Having a documented incident response plan is critical, but it must be tested through realistic tabletop exercises to identify weak spots, refine procedures, and reduce downtime during an actual incident.
- Maintain Continuous Monitoring and Visibility: Attackers move quickly, so real-time threat detection is essential. Comprehensive logging and monitoring across on-premises, cloud, and SaaS environments are required to spot suspicious behavior, unauthorized changes, and misconfigurations before they are exploited.
- Prioritize Vulnerability Management: A robust vulnerability management program is necessary to discover, categorize, and prioritize vulnerabilities for remediation. This is crucial as attackers are increasingly chaining older, lower-risk vulnerabilities with new exploits.
- Embrace Data-Centric Security: Implement measures like data-centric encryption to ensure that even if data is exfiltrated, it remains unusable to attackers.

95 Major 2025 Data Breaches and Cyber Incidents XLSX