Chinese state-sponsored Espionage Group Silk Typhoon Targets IT Supply Chain
Microsoft has identified a significant shift in tactics by the Chinese state-sponsored espionage group Silk Typhoon (also tracked as HAFNIUM), which now targets IT supply chains and cloud applications to breach downstream organizations14. This technical brief outlines their evolving tradecraft, historical patterns, and mitigation strategies.
Executive Summary
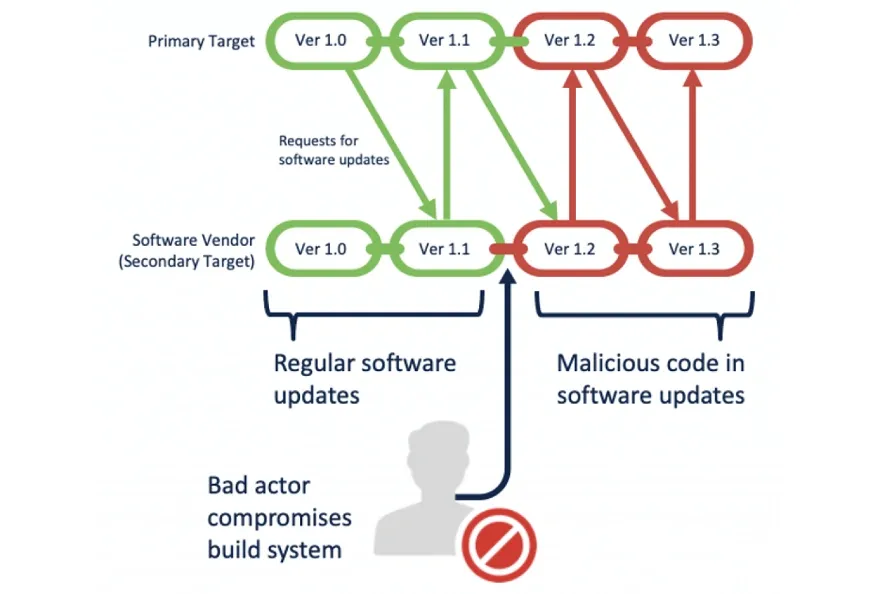
Silk Typhoon has transitioned from direct exploitation of edge devices to supply chain compromises, leveraging stolen API keys, credentials, and zero-day vulnerabilities in IT management tools. Their objectives include espionage, data exfiltration, and lateral movement across cloud environments. Recent campaigns focus on MSPs, PAM providers, and cloud app vendors to infiltrate government, defense, healthcare, and energy sectors globally1420.
Recent Activity & Tradecraft
Initial Access
- Supply Chain Compromise: Abuse of stolen API keys/credentials from IT service providers (e.g., RMM, PAM, cloud data management) to access downstream customers14.
- Zero-Day Exploits: Rapid operationalization of vulnerabilities like CVE-2025-0282 (Ivanti Pulse Connect VPN) and historical exploits in Palo Alto Networks’ GlobalProtect (CVE-2024-3400) and Citrix NetScaler (CVE-2023-3519)1311.
- Credential Harvesting: Password spraying, GitHub reconnaissance for leaked credentials, and abuse of dormant administrative accounts14.
Post-Compromise Tactics
- Lateral Movement to Cloud:
- OAuth/Service Principal Abuse:
- Log Manipulation: Clearing logs post-activity to evade detection14.
Covert Infrastructure
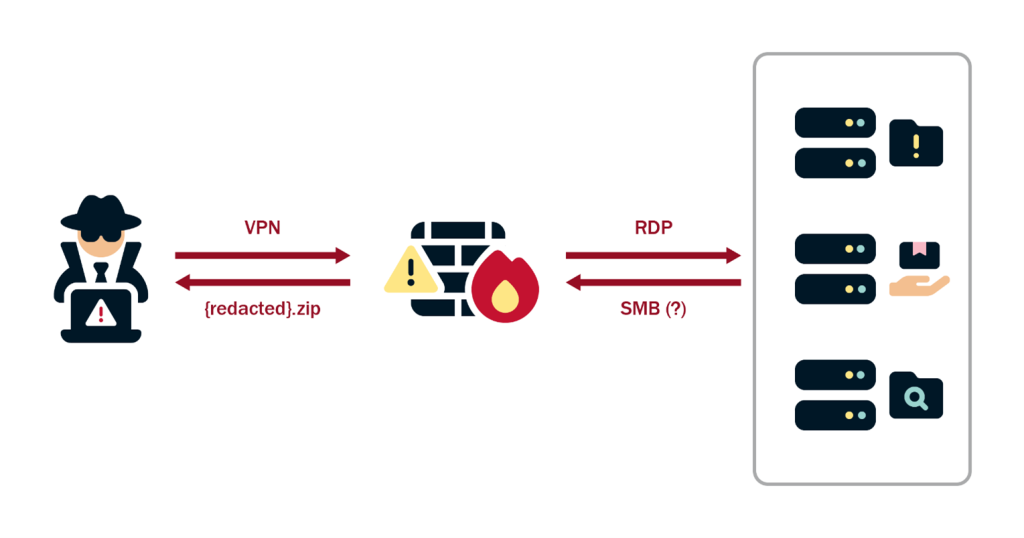
- CovertNetwork: Egress traffic routed through compromised devices (Cyberoam appliances, Zyxel routers, QNAP NAS)13.
- Short-lived VPS infrastructure for command-and-control1.
Historical Exploitation Patterns
Silk Typhoon has a track record of exploiting zero-days in public-facing services:
| Vulnerability | Product | Impact |
|---|---|---|
| CVE-2021-26855 | Exchange Server | SSRF → RCE as SYSTEM14 |
| CVE-2024-3400 | Palo Alto PAN-OS | Unauthenticated RCE13 |
| CVE-2023-3519 | Citrix NetScaler | Unauthenticated RCE111 |
| CVE-2025-0282 | Ivanti Pulse Connect | Privilege escalation13 |
Web shells like China Chopper and AspxSpy were deployed for persistence during earlier campaigns111.
Detection & Mitigation
Hunting Guidance
- Entra Connect Servers: Monitor for anomalous password resets, user creation, or sync anomalies116.
- Service Principals: Audit for new secrets, unused apps accessing APIs, and Graph/EWS data exfiltration14.
- VPN Logs: Investigate unpatched Ivanti/Citrix/Palo Alto devices for configuration changes during exploitation windows13.
Microsoft Defender XDR Integration
- Alerts: "Silk Typhoon activity group," "Suspicious Entra sync password change," "Anomalous MailItem access via GraphAPI"1.
- Sentinel Queries: Deploy analytics for web shells, password sprays, and key vault access anomalies111.
Critical Recommendations
- Patch Public-Facing Systems: Prioritize Ivanti, Citrix, and Exchange servers13.
- Enforce Zero Trust:
- Restrict on-premises service accounts from cloud resource access1.
- Implement Conditional Access policies and risk-based MFA14.
- Audit OAuth Apps:
- Remove unnecessary EWS permissions (EWS.AccessAsUser.All, EWS.full_access_as_app)1.
- Use Microsoft’s App Governance to detect anomalous API activity111.
- Credential Hygiene: Rotate passwords exposed via GitHub/leaks and enforce MFA for admin accounts14.
Microsoft Security Tooling
- Defender Vulnerability Management: Identify unpatched systems (CVE-2025-0282, ProxyLogon)1.
- Security Copilot: Automate incident response with pre-built prompts (e.g., "Threat actor profile")1.
- External Attack Surface Management: Detect vulnerable edge devices via Attack Surface Insights1.
Silk Typhoon’s adaptability underscores the need for layered defenses, particularly in hybrid cloud environments. Organizations should assume breach and validate detection capabilities against the TTPs outlined in Microsoft’s full report1420.
For ongoing updates, follow Microsoft Threat Intelligence1.
What specific vulnerabilities has Silk Typhoon exploited recently
Silk Typhoon, a Chinese state-sponsored espionage group, has recently exploited several critical vulnerabilities in IT infrastructure to enable supply chain attacks and cloud environment infiltration. Below is a detailed breakdown of their active and historical exploitation patterns, with a focus on recent campaigns:
Recent Exploited Vulnerabilities (2024–2025)
| CVE | Product/Service | Vulnerability Type | Impact |
|---|---|---|---|
| Ivanti Pulse Connect VPN | Privilege Escalation Zero-Day | Unauthorized access to downstream entities via VPN appliances1357 | |
| Palo Alto PAN-OS | Unauthenticated RCE | Exploited to breach GlobalProtect Gateways and deploy web shells167 | |
| Citrix NetScaler ADC/Gateway | Unauthenticated RCE | Used to execute arbitrary code on unpatched Citrix appliances137 |
Key Campaigns and Tactics
- Ivanti Pulse Connect VPN (CVE-2025-0282)
- Palo Alto PAN-OS (CVE-2024-3400)
- Citrix NetScaler (CVE-2023-3519)
Historical Vulnerabilities Still Actively Exploited
| CVE | Product/Service | Notes |
|---|---|---|
| Microsoft Exchange | ProxyLogon exploit chain (SSRF → RCE). Actively scanned by GreyNoise as of March 202567. | |
| Apache Log4j | Log4Shell exploited for cloud-to-on-premises pivoting6. |
Post-Exploitation Techniques
- Cloud Lateral Movement: Targeting Microsoft Entra Connect servers to synchronize on-premises AD with cloud environments, enabling credential dumping and privilege escalation13.
- OAuth Application Abuse: Hijacking service principals to exfiltrate email, SharePoint, and OneDrive data via Microsoft Graph API37.
- Log Manipulation: Deleting logs post-compromise to evade detection14.
Mitigation Recommendations
- Patch Prioritization: Immediately apply updates for Ivanti, Palo Alto, and Citrix systems.
- Credential Hygiene: Rotate API keys, enforce MFA, and audit GitHub for leaked credentials25.
- Cloud Monitoring: Hunt for anomalous Entra Connect sync activity and OAuth app permissions17.
Silk Typhoon’s rapid weaponization of zero-days underscores the need for proactive vulnerability management. Organizations should assume breach and validate defenses against these TTPs.
What are the key tactics used by Silk Typhoon in their supply chain attacks
Silk Typhoon, a Chinese state-sponsored espionage group, has refined its tradecraft to exploit IT supply chains through sophisticated tactics. Below is an analysis of their key methods based on recent campaigns:
Supply Chain Targeting
- API Key & Credential Abuse: Compromising IT service providers (e.g., PAM, RMM, cloud app vendors) to steal API keys and credentials, enabling access to downstream customers like government agencies and IT firms146.
- Multi-Tenant Cloud Apps: Hijacking administrative access to cloud data management platforms for lateral movement into customer environments48.
Initial Access Techniques
- Zero-Day Exploits: Rapid weaponization of vulnerabilities:
- Credential Harvesting:
Lateral Movement & Cloud Exploitation
- Entra Connect Server Targeting: Compromising synchronization tools to bridge on-premises AD with cloud environments, enabling credential dumping and privilege escalation458.
- OAuth/Service Principal Abuse: Creating malicious Entra ID applications (e.g., "Office 365 Backup") to exfiltrate data via Microsoft Graph API (email, SharePoint, OneDrive)38.
Persistence & Evasion
- Web Shells: Deploying China Chopper and AspxSpy for command execution23.
- User Account Manipulation: Resetting default admin accounts and creating new users to maintain access14.
- Log Deletion: Erasing activity logs post-compromise to evade detection14.
Infrastructure
- CovertNetwork: Routing traffic through compromised devices (Cyberoam, Zyxel routers, QNAP NAS)39.
- Short-Lived VPS: Using ephemeral cloud infrastructure for C2 operations3.
Strategic Shift
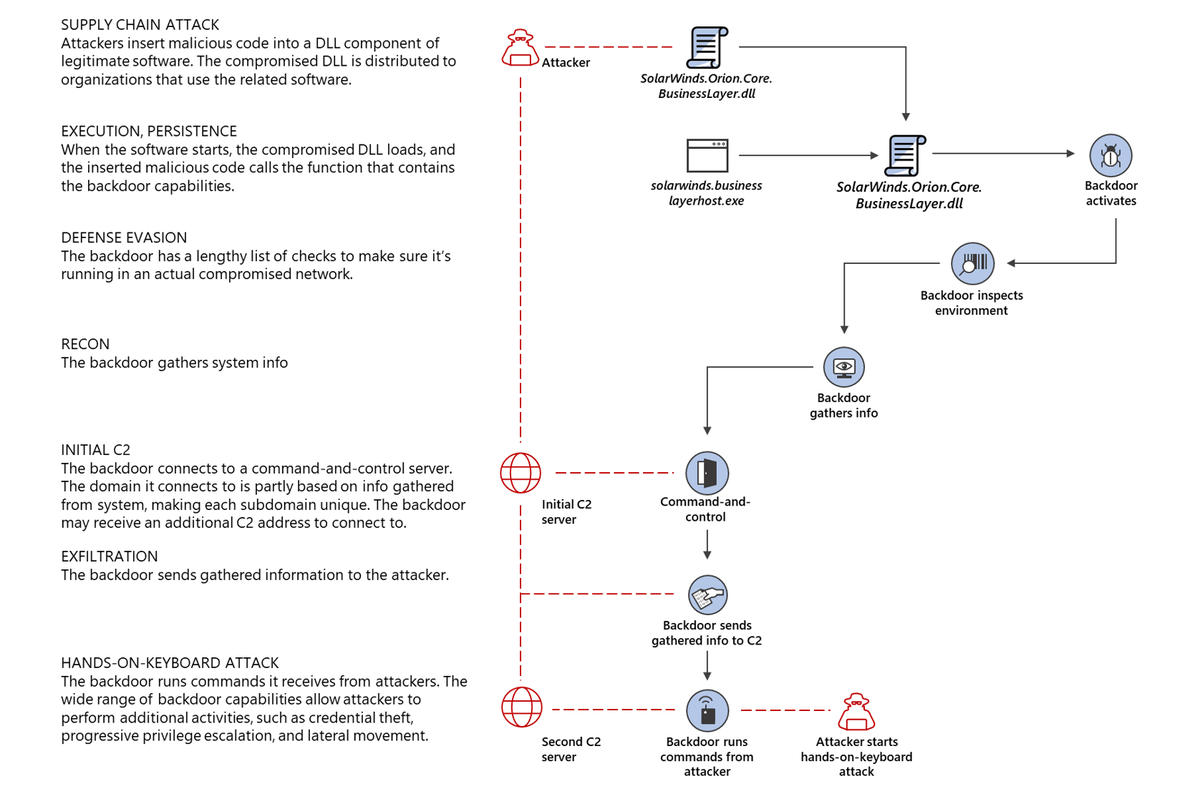
Silk Typhoon has pivoted from direct edge-device exploits to supply chain-centric campaigns, prioritizing IT providers to maximize access to high-value targets. This shift mirrors historical breaches like SolarWinds and MOVEit15. Their adaptability underscores the need for:
- Zero Trust Policies: Restricting service account privileges and enforcing MFA46.
- Cloud Monitoring: Hunting for anomalous Graph API activity and Entra ID sync anomalies8.
- Patch Management: Prioritizing updates for Ivanti, Citrix, and Palo Alto systems23.
Organizations must assume breach and validate defenses against these evolving TTPs.
Citations:
- https://www.microsoft.com/en-us/security/blog/2025/03/05/silk-typhoon-targeting-it-supply-chain/
- https://informationsecuritybuzz.com/silk-typhoon-targets-it-supply-chain/
- https://www.csoonline.com/article/3840546/chinese-apt-silk-typhoon-exploits-it-supply-chain-weaknesses-for-initial-access.html
- https://thecyberexpress.com/silk-typhoon-campaign/
- https://www.infosecurity-magazine.com/news/silk-typhoon-exploits-common/
- https://www.greynoise.io/blog/active-exploitation-silk-typhoon-linked-cves
- https://rhisac.org/threat-intelligence/silk-typhoon-it-supply-chain/
- https://www.darkreading.com/remote-workforce/china-silk-typhoon-it-supply-chain-attacks
- https://www.youtube.com/watch?v=TLbppVXjMWs
- https://www.redlegg.com/blog/threat-profile-brsilk-typhoon
- https://www.microsoft.com/en-us/security/blog/2025/03/05/silk-typhoon-targeting-it-supply-chain/
- https://www.csoonline.com/article/3840546/chinese-apt-silk-typhoon-exploits-it-supply-chain-weaknesses-for-initial-access.html
- https://www.bleepingcomputer.com/news/security/silk-typhoon-hackers-now-target-it-supply-chains-to-breach-networks/
- https://www.microsoft.com/en-us/security/blog/2025/03/05/silk-typhoon-targeting-it-supply-chain/
- https://www.infosecurity-magazine.com/news/silk-typhoon-exploits-common/
- https://www.aha.org/h-isac-white-reports/2025-03-06-h-isac-tlp-white-threat-bulletin-microsoft-releases-new-report-silk-typhoons-evolving-ttps
- https://za.investing.com/news/company-news/microsoft-alerts-of-chinese-hackers-spying-on-cloud-tech-93CH-3590548
- https://www.techradar.com/pro/security/microsoft-says-chinese-silk-typhoon-hackers-are-targeting-cloud-and-it-apps-to-steal-business-data
- https://www.waterisac.org/portal/tlpclear-silk-typhoon-another-chinese-affiliated-threat-actor-targets-it-supply-chains
- https://www.reddit.com/r/msp/comments/1j49evx/microsoft_threat_intelligence_silk_typhoon/
- https://www.scworld.com/news/microsoft-reveals-silk-typhoons-recent-supply-chain-targeting
- https://www.microsoft.com/en-us/security/security-insider
- https://www.threatable.io
- https://www.microsoft.com/en-us/security/security-insider/silk-typhoon
- https://www.theregister.com
- https://rhisac.org/threat-intelligence/silk-typhoon-it-supply-chain/
- https://itnerd.blog/category/commentary/
- https://www.microsoft.com/en-us/security/blog/tag/silk-typhoon-hafnium/
- https://www.marketscreener.com/quote/stock/MICROSOFT-CORPORATION-4835/news/Microsoft-Says-Chinese-Sponsored-Hackers-Targeting-Cloud-Applications-49247742/
- https://www.darkreading.com/remote-workforce/china-silk-typhoon-it-supply-chain-attacks
- https://www.microsoft.com/en-us/security/blog/tag/typhoon/