Clop Ransomware: Inside One of the World's Most Dangerous Cybercrime Operations

The Complete Profile of TA505/FIN11 and Their Evolution from Ransomware to Mass Data Extortion
Executive Summary
Clop (also stylized as Cl0p or CL0P) stands as one of the most sophisticated and financially successful cybercrime organizations in history. Since emerging in February 2019, this Russian-speaking ransomware operation has evolved from traditional file-encrypting attacks to become the dominant force in mass data theft extortion, exploiting zero-day vulnerabilities in enterprise software to steal data from thousands of organizations simultaneously.
With estimated earnings exceeding $500 million and a track record of compromising over 2,773 organizations in a single campaign, Clop represents the cutting edge of modern cybercrime. The group's systematic targeting of managed file transfer (MFT) software has fundamentally changed the ransomware landscape, demonstrating how supply chain vulnerabilities can be weaponized for unprecedented scale.

Key Facts:
- Active Since: February 2019
- Also Known As: TA505, FIN11, Graceful Spider, Lace Tempest, Spandex Tempest, DEV-0950, GOLD TAHOE
- Estimated Total Extorted: Over $500 million USD
- Origin: Russian-speaking, believed to operate from Commonwealth of Independent States (CIS) countries
- Primary Tactic: Zero-day exploitation of managed file transfer software
- Largest Campaign: MOVEit Transfer (2023) - 2,773 organizations affected
- Business Model: Ransomware-as-a-Service (RaaS) with data theft focus
- US Government Reward: $10 million for information linking Clop to foreign government
Origins and Evolution
The Birth of Clop (2019)
Clop ransomware first appeared in February 2019 as a variant of the CryptoMix ransomware family, which itself evolved from earlier malware strains dating back to 2015-2016. The name "Clop" derives from the Russian word "клоп" (klop), meaning "bedbug" — a small but persistent pest that's notoriously difficult to eradicate.
The ransomware was initially deployed by the cybercriminal group TA505 in large-scale spear-phishing campaigns. What made Clop distinctive from the start was its use of verified and digitally signed binaries, allowing it to masquerade as legitimate software and evade many security detection systems.
Strategic Evolution: From Encryption to Extortion
Clop's operational strategy has evolved through three distinct phases:
Phase 1: Traditional Ransomware (2019-2020)
- File encryption with ransom demands
- Large-scale phishing campaigns
- Deployment through macro-enabled documents
- Average ransom payments: $220,298
Phase 2: Double Extortion (2020-2021)
- Data theft before encryption
- Threats to publish stolen data
- Launch of "CL0P^_-LEAKS" data leak site
- Notable attacks on Accellion FTA users
Phase 3: Pure Data Theft Extortion (2021-Present)
- Focus on data exfiltration without encryption
- Exploitation of zero-day vulnerabilities in MFT software
- Mass compromise through supply chain attacks
- Quadruple extortion tactics targeting executives, customers, and business partners
This evolution represents a fundamental shift in ransomware operations. By abandoning encryption in favor of pure data theft, Clop reduced operational complexity while maintaining leverage over victims. The group recognized that the threat of data exposure could be just as effective as crypto-locking files, while requiring less technical overhead and reducing the risk of mistakes that could lead to data loss.
The Organization: TA505/FIN11
Identity and Attribution
The relationship between Clop, TA505, and FIN11 represents one of the more complex attribution challenges in cybersecurity:
TA505 is a financially motivated threat actor group active since at least 2014, known for frequently changing malware and driving global trends in criminal malware distribution. The group has been involved in phishing, malspam, financial fraud, and large-scale botnet operations.
FIN11 is often described as either a subset of TA505, an affiliate, or a closely related group with significant operational overlap. Mandiant began tracking FIN11 separately in 2016 due to distinct post-compromise tactics, techniques, and procedures (TTPs) not publicly associated with TA505.
Clop is the ransomware/extortion brand operated by these groups, though evidence suggests the brand may be used by multiple threat clusters with varying TTPs.
The FBI and CISA have stated that Clop and TA505 are identical, though some researchers maintain they are separate but overlapping entities. For practical purposes, security professionals should understand that these names all refer to a loose collective of Russian-speaking cybercriminals engaged in similar activities.
Geographic Origins and Safe Harbor
Multiple lines of evidence point to Russian or CIS origins:
- Russian Language Artifacts: File metadata, code comments, and communications contain Russian language elements
- Geographic Avoidance: Clop ransomware is specifically programmed not to execute on systems with Russian or CIS keyboard layouts
- Target Selection: The group avoids attacking organizations within Russia and former Soviet states
- Operational Patterns: Activity aligns with working hours in Eastern European time zones
- Holiday Patterns: Observed drops in activity during Russian New Year and Orthodox Christmas
Despite these indicators, Clop actors explicitly deny any political affiliation or nation-state sponsorship. Their ransom notes and communications emphasize purely financial motivations. However, the group's ability to operate with apparent impunity from Russian territory has led to speculation about implicit state tolerance, if not direct support.
Organizational Structure
As a Ransomware-as-a-Service (RaaS) operation, Clop maintains a sophisticated organizational structure:
Core Developers
- Maintain the ransomware/malware codebase
- Research and develop zero-day exploits
- Manage infrastructure and leak sites
- Believed to be based in Russia, protected from law enforcement
Affiliates/Operators
- Deploy attacks against specific targets
- Handle initial access and data exfiltration
- Conduct negotiations with victims
- More geographically distributed, including Ukraine
Money Laundering Network
- Cash-out operators who convert cryptocurrency
- Money mules who move funds
- Most vulnerable to law enforcement action
- Six members arrested in Ukraine in June 2021
Initial Access Brokers (IABs)
- Provide credentials and access to target networks
- Often purchase stolen credentials from infostealer malware logs
- May operate independently and sell to multiple groups
Business Model and Operations
The Ransomware-as-a-Service Model
Clop operates on a mature RaaS business model where:
- Core developers maintain the malware and infrastructure
- Affiliates pay subscription fees or profit-sharing arrangements
- Affiliates execute attacks and handle victim negotiations
- Profits are split according to pre-arranged percentages (typically 60-80% to affiliates)
This decentralized structure provides several advantages:
- Scalability: Multiple affiliates can conduct simultaneous campaigns
- Deniability: Core operators maintain distance from actual attacks
- Resilience: Arrests of affiliates don't disable core operations
- Specialization: Different groups focus on areas of expertise
Multi-Level Extortion Strategy
Clop pioneered and perfected what's known as "quadruple extortion":
Level 1: Direct Victim Pressure
- Initial ransom demand to prevent data publication
- Deadlines create urgency
- Threats of data destruction or sale
Level 2: Public Shaming
- Listing victims on CL0P^_-LEAKS site
- Publishing sample stolen data
- Gradual data release to maintain pressure
Level 3: Customer/Partner Harassment
- Contacting victims' customers directly
- Emailing business partners with breach notifications
- Creating reputational damage and third-party pressure
Level 4: Regulatory/Legal Pressure
- Threatening to report GDPR/compliance violations
- Notifying regulators of data breaches
- Creating legal liability for victims
This multilayered approach dramatically increases the probability of payment by attacking from multiple angles simultaneously.
Supply Chain Attack Strategy
Clop's most successful campaigns have targeted the software supply chain rather than individual organizations:
Traditional Approach:
- Breach Company A
- Steal data from Company A
- Extort Company A
Clop's Supply Chain Approach:
- Identify widely-used software (e.g., MOVEit Transfer)
- Develop zero-day exploit for that software
- Compromise hundreds or thousands of software users simultaneously
- Extort each affected organization individually
This approach provides exceptional return on investment. A single zero-day development effort can yield hundreds of victims, each capable of paying ransoms ranging from hundreds of thousands to tens of millions of dollars.

Attack Methodology and Technical Capabilities
Zero-Day Exploitation Focus
Unlike many ransomware groups that rely on phishing or stolen credentials, Clop has distinguished itself through systematic exploitation of zero-day vulnerabilities in enterprise software. This requires:
Significant R&D Investment:
- Dedicated vulnerability research teams
- Exploit development capabilities
- Testing infrastructure
- Evidence suggests Clop invests substantial ransom proceeds back into offensive research
Target Selection Criteria:
- Widely deployed enterprise software
- Systems that handle or transfer sensitive data
- Internet-facing applications with large attack surfaces
- Software used by high-value targets (fortune 500, government agencies)
Rapid Exploitation:
- Clop typically exploits zero-days within weeks or months of discovery
- Operates covertly before patches become available
- Achieves maximum victim count before detection
- Intelligence suggests some exploits were held and refined for years before use
Attack Chain and Methodology
A typical Clop attack follows this pattern:
Phase 1: Initial Access (Days 1-7)
- Exploit zero-day vulnerability in target software
- Deploy custom web shells (DEWMODE for Accellion, LEMURLOOT for MOVEit, GOLDVEIN for Cleo/Oracle)
- Establish command-and-control communication
- Authenticate using hardcoded passwords
- Enumerate accessible data and systems
Phase 2: Reconnaissance (Days 7-30)
- Map victim environment
- Identify high-value data
- Assess security controls
- Determine victim's ability to pay
- Check for offline backups
- Screenshot capture for intelligence gathering
Phase 3: Data Exfiltration (Days 30-90)
- Compress and stage data for extraction
- Exfiltrate via encrypted channels
- Typically using HTTP/HTTPS to blend with normal traffic
- Removal of access logs
- Sometimes deployment of additional persistence mechanisms
Phase 4: Extortion (Day 90+)
- Send high-volume extortion emails to executives
- Provide proof of data theft (sample files)
- Establish ransom amount based on victim assessment
- Negotiate through secure channels
- Threaten public disclosure on specific deadlines
Phase 5: Escalation (If Payment Refused)
- List victim on leak site
- Publish sample data
- Contact customers and partners
- Gradual data release
- Eventual full data dump
Technical Sophistication
Clop demonstrates advanced technical capabilities:
Exploit Chaining: Clop frequently chains multiple vulnerabilities together. For example, the Oracle EBS attack (CVE-2025-61882) involved:
- Server-Side Request Forgery (SSRF)
- Carriage Return/Line Feed (CRLF) injection
- Authentication bypass
- XSL template injection
- Remote code execution
Evasion Techniques:
- Digitally signed binaries to appear legitimate
- Living-off-the-land tactics using legitimate tools (PowerShell, Cobalt Strike)
- Fileless malware execution
- Memory-only payloads
- Indicator removal and log deletion
Anti-Analysis Measures:
- Checks for CIS keyboard layouts (refuses to execute)
- Virtual machine detection
- Sandbox evasion
- Encrypted communications
- Obfuscated code
Major Campaigns and Victims
Timeline of Major Clop Campaigns
2019: Emergence and Early Operations
- December 2019: Maastricht University attack
- 267 Windows systems encrypted
- €200,000 ransom paid
- One of the first high-profile Clop attacks
2020-2021: Accellion FTA Campaign
- Exploit: Multiple zero-day vulnerabilities in Accellion File Transfer Appliance
- Web Shell: DEWMODE (PHP-based)
- Victims: Nearly 100 organizations
- Notable Targets:
- Bombardier (defense contractor blueprints stolen)
- Kroger (US grocery chain)
- Jones Day (law firm)
- Qualys (security firm)
- Singtel (Singapore telecom)
- Stanford University School of Medicine
- University of Maryland
- University of California
- Impact: Marked Clop's shift to pure data theft without encryption
2021: SolarWinds Serv-U FTP
- Exploit: Zero-day vulnerability in SolarWinds Serv-U FTP software
- Scale: Limited compared to other campaigns
- Significance: Demonstrated continued zero-day exploitation capabilities
Early 2023: GoAnywhere MFT
- Exploit: CVE-2023-0669 (zero-day)
- Timeline: 10-day exploitation window before detection
- Victims: 130+ organizations
- Sectors: Banking, healthcare, financial services
- Notable Targets: Major financial institutions
- Technique: Limited to platform itself, no lateral movement into victim networks
Mid-2023: PaperCut Vulnerability
- Exploit: CVE-2023-27350
- Co-exploitation: Also exploited by LockBit ransomware gang
- Target: Print management software solution
- Significance: Showed opportunistic targeting beyond MFT platforms
May-August 2023: MOVEit Transfer - The Largest Campaign
- Exploit: CVE-2023-34362 (SQL injection zero-day)
- Web Shell: LEMURLOOT (C#-based)
- Attack Window: May 27-31, 2023 (primary exploitation)
- Patch Released: May 31, 2023
- Total Victims: 2,773 organizations worldwide
- Individuals Affected: 95+ million people
- Estimated Cost: $12.15 billion
- Estimated Clop Earnings: $75-100 million
Notable MOVEit Victims:
- Energy: Shell, Siemens Energy, Schneider Electric
- Professional Services: PricewaterhouseCoopers (PwC), Ernst & Young (EY)
- Aviation: British Airways, American Airlines
- Media: BBC (British Broadcasting Corporation)
- Healthcare: Multiple healthcare providers
- Education: National Student Clearinghouse (affecting 3,600+ colleges)
- Government: Multiple US federal agencies, Louisiana, Oregon state governments
- Financial: 1st Source, First National Bankers Bank, Putnam Investments
- Technology: Sony, Cognizant
- Pharmaceuticals: AbbVie, multiple pharmaceutical companies
- Retail: TJX Companies (T.J. Maxx)
- Other: UCLA, New York City Department of Education, Estée Lauder
Late 2024: Cleo File Transfer Software
- Exploits: CVE-2024-50623 and CVE-2024-55956 (two zero-days)
- Affected Products: Cleo Harmony, VLTrader, LexiCom
- Timeline: October-December 2024
- Victims: 380+ known organizations
- Notable Targets:
- Hertz (rental car company)
- WK Kellogg (breakfast cereal company)
- Home Depot Mexico
- Malware: GOLDVEIN downloader (PowerShell variant)
- Technique: Drip-fed victim announcements over weeks/months
2025: Oracle E-Business Suite
- Exploits: CVE-2025-61882 (zero-day) plus July 2025 vulnerabilities
- CVSS Score: 9.8 (Critical)
- Timeline: July 10 - October 2025 (ongoing)
- Earliest Breach: August 9, 2025
- Detection: September 29, 2025 (extortion emails began)
- Victims: Dozens confirmed, potentially 100+
- Malware: GOLDVEIN.JAVA, Sagegift/Sageleaf/Sagewave family
- Ransom Demands: Up to $50 million
- Notable Victims:
- Harvard University
- American Airlines (Envoy Air subsidiary) - Read our detailed coverage of the American Airlines breach
- Technique: High-volume extortion campaign using hundreds of compromised email accounts
Victim Profile and Targeting
Industry Distribution (2023 Data): Based on Trend Micro analysis of Clop's leak site and Smart Protection Network detections:
Top Targeted Industries by Successful Attacks:
- IT/Technology: Leading target sector
- Healthcare/Pharmaceutical: Second highest (75 detections in banking per Trend Micro SPN)
- Finance/Banking: 75 detections via Trend Micro Smart Protection Network
- Professional Services: Fourth highest
- Retail: 42 detections via Trend Micro SPN
- Manufacturing/Engineering: Significant presence
- Telecommunications: Multiple attacks
- Energy: Including oil and gas
- Aerospace: Including defense contractors
- Transportation & Logistics: Airlines, shipping
- Education: Universities and K-12 systems
- Government: Federal and state agencies
Attack Attempt Patterns (January-May 2023): Trend Micro Smart Protection Network data revealed:
- Turkey: 94 attack attempts (highest)
- Canada: 80 attack attempts (second highest)
- May 2023 Surge: 245 attack attempts in a single month, significantly higher than January-April
- Geographic spread across North America, South America, Asia Pacific, Europe, and Middle East
Notably, unlike some ransomware groups that claim to avoid healthcare, Clop actively targets the healthcare sector, with healthcare remaining in the top five targeted industries throughout 2023.
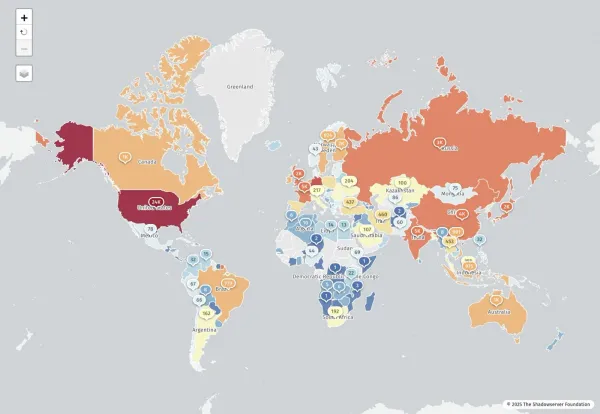
Geographic Distribution:
- North America: 64 organizations (57.7%)
- United States: 54 victim organizations (Trend Micro OSINT, Jan-May 2023)
- Canada: 10+ organizations
- Europe: 17 organizations (15.3%)
- United Kingdom: 10+ organizations
- Asia Pacific: Emerging target region
- Australia: Notable presence
- India: Growing targets
- Latin America: Growing presence
- Colombia and Mexico: Increasing attacks
- Middle East & Africa: Smaller presence
Organization Size Distribution (Trend Micro Data, Jan-May 2023):
- Large Enterprises: Majority of victims
- Small and Medium Businesses (SMBs): Close second in victim count
- Critical Infrastructure: Increasing focus
This distribution indicates Clop doesn't discriminate by organization size, though large enterprises with substantial financial resources remain the primary targets.
Big Game Hunting Strategy: Clop practices "big game hunting" - specifically targeting organizations with:
- Substantial financial resources
- Sensitivity to public disclosure
- Valuable intellectual property
- Large customer bases
- Regulatory compliance requirements
- Critical infrastructure dependencies
The group assesses victims' ability to pay and adjusts ransom demands accordingly, sometimes reaching $20-50 million for high-value targets.
Financial Impact and Ransom Demands
Total Financial Damage
Direct Extortion:
- Total extorted: $500+ million USD (as of 2021)
- Continued earnings: $75-100 million from MOVEit alone (2023)
- Estimated 2024-2025 earnings: Undisclosed but substantial
Indirect Costs to Victims:
- Total cost of MOVEit incident: $12.15 billion
- Remediation costs per victim: $1-10 million average
- Legal and regulatory fines: Substantial GDPR and compliance penalties
- Reputational damage: Difficult to quantify but significant
- Business disruption: Lost revenue during recovery
Ransom Demand Structure
Average Demands by Period:
2021 Q1:
- Average: $220,298
- Median: $78,398
- Notable 43% increase from previous quarter
2023-Present:
- Range: $200,000 - $50 million
- Victim-specific pricing based on:
- Company revenue and market capitalization
- Data sensitivity and compliance implications
- Number of affected individuals
- Public disclosure potential
- Insurance coverage indications
- Previous willingness to pay
Record Demands:
- Software AG (October 2020): $20+ million
- First known ransomware demand over $20 million
- Oracle EBS victims (2025): Up to $50 million reported
- Large enterprises: Typically $5-20 million range
- SMBs affected via supply chain: $200,000 - $2 million
Payment and Negotiation Process
Communication Methods:
- Encrypted email addresses on leak site
- Secure communication channels (encrypted chat)
- Direct contact with executives
- Use of compromised email accounts for initial contact
Negotiation Tactics:
- Initial high demand with room for negotiation
- Deadline pressure (typically 2-4 weeks)
- Gradual data release to demonstrate seriousness
- Proof of data possession (sample files)
- Threats of regulatory notification
- Customer/partner contact threats
Payment Requirements:
- Cryptocurrency only (Bitcoin, Monero)
- Complex laundering chains
- Use of mixing services
- Conversion through multiple exchanges
- Cash-out through money mules
Payment Rate and Victim Response
While exact payment rates are unknown (many victims pay secretly), industry estimates suggest:
- 10-30% of victims pay ransoms
- Higher payment rates for smaller organizations
- Large enterprises more likely to refuse and restore from backups
- Government entities generally refuse payment
- Healthcare organizations show higher payment rates due to urgency
The low payment rate is offset by the massive scale of Clop's supply chain attacks, making the overall operation highly profitable despite most victims refusing to pay.
Tools and Malware Arsenal
Core Ransomware
Clop/Cl0p Ransomware
- Type: File-encrypting ransomware
- Family: CryptoMix variant
- Encryption: RSA 1024-bit + RC4
- Extension: .Clop, .Cl0p, .C_L_O_P, .C_I_0P, .Cllp
- Ransom Notes: ClopReadMe.txt, README_README.txt, !!!READ!!!.RTF
- Unique Features:
- Digitally signed binary for evasion
- CIS keyboard layout detection (execution prevention)
- Active Directory targeting
- Group Policy abuse
- Shadow copy deletion
- Network propagation via SMB shares
Initial Access Tools
Get2 Downloader
- Function: Malware dropper
- Delivery: Macro-enabled documents in phishing campaigns
- Capabilities: Downloads SDBot and FlawedGrace malware
- Usage: Early Clop campaigns (2019-2020)
TrueBot
- Type: First-stage downloader
- Developer: Attributed to Silence hacking group
- Capabilities:
- System information collection
- Screenshot capture
- Shell code loading
- DLL side-loading
- Self-deletion
- Function: Downloads FlawedGrace or Cobalt Strike beacons
Remote Access Tools (RATs)
FlawedAmmyy/FlawedGrace
- Type: Remote Access Trojan
- Capabilities:
- Information collection
- C2 communication
- Additional malware deployment
- Credential harvesting
- Notable: Used across multiple TA505 campaigns
SDBot
- Type: IRC-based RAT
- Capabilities:
- Infection propagation
- Vulnerability exploitation
- Application shimming for persistence
- Network share infection
- Removable drive propagation
Web Shells
DEWMODE
- Target: Accellion FTA devices
- Language: PHP
- Capabilities:
- MySQL database interaction
- Data extraction
- Remote command execution
- File system access
- Campaign: 2020-2021 Accellion attacks
LEMURLOOT
- Target: MOVEit Transfer platform
- Language: C#
- Authentication: Hard-coded 36-character password
- Capabilities:
- File downloads from MOVEit
- Azure system settings extraction
- Detailed record retrieval
- User management (create, insert, delete)
- Data compression (gzip)
- Database interaction
- Campaign: 2023 MOVEit attacks
- Disguise: Initially named human2.aspx to masquerade as legitimate human.aspx
GOLDVEIN Family
- GOLDVEIN (PowerShell): First observed December 2024 in Cleo attacks
- GOLDVEIN.JAVA: Java variant for Oracle EBS attacks
- Capabilities:
- Second-stage payload download
- C2 communication disguised as TLS handshake
- Execution result logging
- HTTP response via HTML comments
Sage Malware Family
- Sagegift: Loader payload
- Sageleaf: In-memory dropper
- Sagewave: Malicious Java servlet filter
- Function: Deploy AES-encrypted ZIP archives with Java classes
- Campaign: 2025 Oracle EBS attacks
Post-Exploitation Tools
Cobalt Strike
- Type: Commercial penetration testing tool (abused)
- Function: Network expansion after AD compromise
- Capabilities:
- Lateral movement
- Beacon deployment
- Command execution
- Credential dumping
- Process injection
- Pivoting
MITRE ATT&CK Framework Mapping
Initial Access:
- T1566 (Phishing) - Spear-phishing with malicious attachments/links
- T1190 (Exploit Public-Facing Application) - Zero-day exploitation
Execution:
- T1059.001 (PowerShell)
- T1059.003 (Windows Command Shell)
- T1204 (User Execution)
Persistence:
- T1505.003 (Web Shell) - DEWMODE, LEMURLOOT, GOLDVEIN
- T1547.006 (Application Shimming) - SDBot technique
Privilege Escalation:
- T1068 (Exploitation for Privilege Escalation)
- T1055 (Process Injection)
Defense Evasion:
- T1070 (Indicator Removal) - Log deletion
- T1574.002 (DLL Side-Loading)
- T1055 (Process Injection)
- T1036 (Masquerading) - Signed binaries
Discovery:
- T1018 (Remote System Discovery)
- T1082 (System Information Discovery)
- T1083 (File and Directory Discovery)
Lateral Movement:
- T1021.002 (SMB/Windows Admin Shares)
- T1570 (Lateral Tool Transfer)
Collection:
- T1005 (Data from Local System)
- T1039 (Data from Network Shared Drive)
- T1113 (Screen Capture) - TrueBot
Command and Control:
- T1071 (Application Layer Protocol)
- T1132 (Data Encoding)
- T1573 (Encrypted Channel)
Exfiltration:
- T1041 (Exfiltration Over C2 Channel)
- T1048 (Exfiltration Over Alternative Protocol)
- T1020 (Automated Exfiltration)
Impact:
- T1486 (Data Encrypted for Impact) - When ransomware deployed
- T1485 (Data Destruction) - Backup deletion
- T1490 (Inhibit System Recovery) - Shadow copy deletion
Law Enforcement Actions
June 2021: Ukrainian Raids
Operation Details:
- Date: June 16, 2021
- Location: Kyiv and surrounding regions, Ukraine
- Participating Agencies:
- National Police of Ukraine
- South Korean law enforcement
- United States law enforcement
- Interpol coordination
Arrests and Seizures:
- Suspects Arrested: 6 individuals
- Searches Conducted: 21 residences
- Assets Seized:
- Computer equipment and servers
- Smartphones and mobile devices
- 5 million Ukrainian Hryvnia ($185,000 USD in cash)
- Multiple luxury vehicles (Tesla, Mercedes, Lexus)
- Server infrastructure used for attacks
Attributed Damages:
- Total financial damages: $500 million
- Victims: US and South Korean companies
- Charges: Unauthorized interference in computer systems, money laundering
Assessment and Impact: Intelligence firm Intel 471 assessment:
- Arrests limited to cash-out/money laundering operations
- Core actors not apprehended (likely based in Russia)
- Core developers believed protected in Russian territory
- Expected minor overall impact on operations
Post-Arrest Activity: Despite arrests, Clop operations continued:
- Data leak site remained operational
- New victims posted within days of arrests
- Core infrastructure untouched
- Operations resumed with minimal disruption
Lessons Learned:
- Decentralized structure provides resilience
- Core operators maintain operational security
- Money launderers are replaceable
- Russian safe harbor remains primary challenge
- International cooperation necessary but insufficient
US Government Response
Rewards for Justice Program:
- Bounty Amount: $10 million USD
- Condition: Information linking Clop ransomware activities to foreign government
- Program: US Department of State Rewards for Justice
- Objective: Establish nation-state sponsorship or tolerance
FBI and CISA Actions:
- Joint cybersecurity advisories (AA23-158A for MOVEit)
- Indicators of compromise (IOCs) publication
- Technical guidance for victims
- Private sector partnerships
- Victim notification programs
Diplomatic Pressure:
- Biden-Putin summit discussions (June 2021)
- Russia pledged cooperation on cybercrime
- Limited practical results
- Ongoing diplomatic engagement
International Law Enforcement Cooperation
Successes:
- Multi-country coordination for Ukrainian arrests
- Intelligence sharing between agencies
- Victim identification and notification
- Asset seizure and cryptocurrency tracking
Challenges:
- Jurisdictional limitations
- Russia's refusal to extradite cybercriminals
- Cryptocurrency laundering complexity
- Attribution difficulties
- Speed of operations vs. law enforcement response
Current Activities (2024-2025)
Evolution of Tactics
Late 2024: Cleo Campaign Refinements The Cleo file transfer software attacks demonstrated Clop's continued innovation:
Technical Advancements:
- Dual zero-day exploitation (CVE-2024-50623, CVE-2024-55956)
- GOLDVEIN downloader development (PowerShell variant)
- Improved operational security
- Longer dwell time before detection
Operational Changes:
- Drip-feeding victim announcements over months
- Strategic timing to maximize pressure
- More selective victim publication
- Enhanced negotiation tactics
2025: Oracle E-Business Suite Campaign
The Oracle EBS campaign represents Clop's most sophisticated operation to date:
Technical Complexity:
- Exploit chain combining 5+ vulnerabilities
- Zero-day (CVE-2025-61882) plus July 2025 vulnerabilities
- Java-based post-exploitation framework
- In-memory malware execution
- Advanced evasion techniques
Scale and Impact:
- Three-month head start (July-October 2025)
- Dozens to potentially 100+ organizations affected
- High-value targets including Harvard University
- Enterprise resource planning system compromise
- Potential exposure of critical business data
New TTPs Observed:
- Use of hundreds of compromised email accounts for extortion
- Credentials sourced from infostealer malware logs
- Multiple exploit chains (redundancy strategy)
- Selective victim disclosure
- Enhanced reconnaissance capabilities
GOLDVEIN.JAVA and Sage Family: Development of Java-based malware specifically for Oracle environments:
- GOLDVEIN.JAVA downloader
- Sagegift/Sageleaf/Sagewave backdoor family
- In-memory execution
- Database-resident payloads
- Fileless operation
Ransom Escalation:
- Demands up to $50 million reported
- Seven and eight-figure demands now common
- Victim-specific pricing algorithms
- Enhanced pressure tactics
Current Threat Posture (October 2025)
Activity Level: Clop surpassed LockBit as the most prolific ransomware group in Q1 2025 based on publicly disclosed breaches. In Q4 2024, Clop overtook RansomHub and Akira to become the most active ransomware group.
Target Preferences:
- Enterprise resource planning (ERP) systems
- Managed file transfer (MFT) software
- Internet-facing business applications
- Supply chain software
- Cloud-based enterprise services
Geographic Focus:
- Continued emphasis on North America (especially US)
- European targets increasing
- Asia-Pacific emerging as growth market
- Avoidance of CIS countries maintained
Collaboration and Overlap: Evidence suggests Clop may be collaborating with or overlapping with:
- FIN7 (Sangria Tempest): In May 2023, FIN7 was observed using POWERTRASH malware to launch the Lizar toolkit in attacks that began in April 2023, ultimately distributing Clop ransomware on compromised machines
- Scattered LAPSUS$ Hunters: Exploit sharing (Oracle EBS)
- UNC5936: Suspected FIN11 threat cluster (Cleo/Oracle campaigns)
- Multiple IAB (Initial Access Broker) groups
Predictions for Future Activity
Based on observed patterns and capabilities:
Short-Term (6-12 Months):
- Continued exploitation of MFT and ERP software
- Possible targeting of cloud service providers
- Expansion into new geographic markets
- Further development of fileless malware
- Increased use of legitimate tools (LOTL tactics)
Medium-Term (1-2 Years):
- Potential AI/ML integration for victim selection
- Automated reconnaissance and data classification
- Enhanced evasion of EDR/XDR solutions
- Possible supply chain attacks on software developers
- Expansion of quadruple extortion tactics
Long-Term Concerns:
- Critical infrastructure targeting
- Nation-state collaboration or sponsorship
- Development of wiper malware variants
- Integration with other APT groups
- Attacks on backup and recovery systems
Indicators of Clop Operations
Technical Indicators of Compromise (IOCs)
File Indicators:
- Extensions: .Clop, .Cl0p, .C_L_O_P, .C_I_0P, .Cllp
- Ransom notes: ClopReadMe.txt, README_README.txt, !!!READ!!!.RTF
- Web shells:
- human2.aspx (LEMURLOOT disguise)
- Various PHP files (DEWMODE)
- Suspicious Java servlets
Network Indicators:
- C2 communication patterns
- Unusual outbound traffic volumes
- HTTP requests with specific headers (X-siLock-Comment for LEMURLOOT)
- Suspicious PowerShell or Java execution from service accounts
Process Indicators:
- PowerShell execution from unexpected processes
- Java processes spawning bash shells
- Cobalt Strike beacons
- Suspicious use of legitimate tools (PsExec, WMI)
Registry/System Indicators:
- Shadow copy deletion commands
- Group Policy modifications
- Service creation for persistence
- Startup folder modifications
Behavioral Indicators
Pre-Attack Reconnaissance:
- Unusual Active Directory queries
- Enumeration of file shares
- Mapping of network topology
- Database queries for sensitive data
- Cloud service enumeration
Data Staging:
- Large file compression operations
- Creation of archives in unusual locations
- Network file transfers to staging locations
- Use of legitimate tools for data collection (7-Zip, WinRAR)
Exfiltration Signs:
- Sustained outbound traffic to unusual destinations
- Large data transfers outside business hours
- Encrypted traffic to known malicious infrastructure
- DNS requests to suspicious domains
Email Indicators
Extortion Email Characteristics:
- Sent from compromised third-party accounts
- Addresses multiple executives simultaneously
- Contains specific company details proving breach
- Includes contact addresses: [email protected], [email protected]
- Mentions CL0P^_-LEAKS site
- Provides sample stolen data as proof
- Creates urgency with deadlines
Phishing Campaign Patterns (Historical):
- Macro-enabled Office documents
- HTML attachments with redirects
- Spoofed sender addresses
- Business-themed social engineering
- Malicious links to dropper sites
Defense Strategies
Prevention
Vulnerability Management:
- Patch Management:
- Emergency patching for MFT software zero-days
- Regular patching schedule for all enterprise software
- Prioritization of internet-facing applications
- Testing in development environments before production
- Software Inventory:
- Complete asset inventory of MFT/ERP software
- Version tracking and update status
- Internet-facing application identification
- Third-party software risk assessment
- Configuration Hardening:
- Disable unnecessary features in MFT software
- Strong authentication requirements
- Network segmentation of critical applications
- Principle of least privilege
Access Controls:
- Network Segmentation:
- Isolation of MFT/ERP systems
- DMZ for internet-facing applications
- Internal network segmentation
- Jump hosts for administrative access
- Multi-Factor Authentication (MFA):
- MFA on all administrative accounts
- MFA for VPN access
- MFA for remote access solutions
- Hardware token consideration for high-value accounts
- Privileged Access Management (PAM):
- Just-in-time access
- Session recording and monitoring
- Regular privilege reviews
- Break-glass procedures
Email Security:
- Anti-Phishing Measures:
- Advanced email filtering
- URL sandboxing and analysis
- Attachment scanning and quarantine
- DMARC, SPF, DKIM implementation
- User Training:
- Regular security awareness training
- Phishing simulation exercises
- Reporting mechanisms for suspicious emails
- Executive-focused training (high-value targets)
Backup Strategy:
- 3-2-1 Backup Rule:
- 3 copies of data
- 2 different media types
- 1 off-site/air-gapped copy
- Immutable Backups:
- Write-once-read-many (WORM) storage
- Air-gapped backup systems
- Regular backup testing and restoration drills
- Encrypted backup storage
Detection
Monitoring and Logging:
- Enhanced Logging:
- Web application logs (especially MFT/ERP)
- PowerShell script block logging
- Process creation logging
- Network traffic logs
- Authentication logs
- SIEM Integration:
- Real-time log aggregation
- Correlation rules for Clop TTPs
- Alerting on suspicious patterns
- Retention of logs for forensics (90+ days recommended)
Threat Hunting:
- Proactive Searches:
- Hunt for web shells in MFT applications
- Search for suspicious PowerShell/Java execution
- Identify abnormal data access patterns
- Look for lateral movement indicators
- Java processes spawning bash shells (bash -i)
- PowerShell launched by service accounts
- Cobalt Strike beacon indicators
Specific Hunting Queries:For Oracle EBS:
-- Check for malicious templates
SELECT * FROM XDO_TEMPLATES_B WHERE TEMPLATE_CODE LIKE 'TMP%' OR TEMPLATE_CODE LIKE 'DEF%' ORDER BY CREATION_DATE DESC;
SELECT * FROM XDO_LOBS ORDER BY CREATION_DATE DESC;
For Suspicious Processes:
EDR/XDR Deployment:
- Endpoint Detection and Response:
- Deploy on all critical systems
- Enable behavioral detection
- Configure for fileless malware detection
- Integration with threat intelligence feeds
- Extended Detection and Response:
- Cross-layered visibility
- Automated response capabilities
- Integration of network, endpoint, email, cloud
Response
Incident Response Plan:
- Preparation:
- Documented incident response procedures
- Designated IR team with clear roles
- Contact information for external resources
- Legal and regulatory notification procedures
- Detection and Analysis:
- Rapid triage of alerts
- Forensic evidence collection
- Scope determination
- Impact assessment
- Containment:
- Network segmentation activation
- Disable compromised accounts
- Block C2 communications
- Isolate affected systems
- Eradication:
- Remove web shells and backdoors
- Hunt for persistence mechanisms
- Clean affected systems
- Reset credentials
- Recovery:
- System restoration from clean backups
- Verification of clean state
- Gradual service restoration
- Enhanced monitoring during recovery
- Post-Incident:
- Root cause analysis
- Lessons learned documentation
- Security posture improvements
- Communication with stakeholders
Ransom Negotiation Considerations:
- Do Not Pay Recommendation:
- FBI and CISA advise against payment
- No guarantee of data deletion
- Funds criminal operations
- Encourages future attacks
- If Considering Payment:
- Engage specialized negotiation firm
- Consult legal counsel
- Check sanctions compliance
- Document all communications
- Legal and Regulatory:
- Report to law enforcement (FBI IC3)
- GDPR/CCPA breach notifications
- Industry-specific requirements (HIPAA, etc.)
- Insurance claim procedures
Organizational Preparedness
Governance and Culture:
- Security Culture:
- Top-down commitment to security
- Security awareness programs
- Regular security communications
- Reward security-conscious behavior
- Risk Management:
- Regular risk assessments
- Cyber insurance evaluation
- Business continuity planning
- Disaster recovery testing
- Third-Party Risk:
- Vendor security assessments
- Contractual security requirements
- Supply chain security reviews
- Continuous monitoring of vendors
Specific Guidance for High-Risk Organizations:
Managed File Transfer Software Users:
- Apply patches immediately upon release
- Restrict internet exposure of MFT systems
- Implement additional authentication layers
- Regular security audits
- Monitor for web shell indicators
Oracle EBS Customers:
- Apply October 2023 CPU (prerequisite)
- Install October 4, 2025 emergency patch
- Hunt for malicious templates in database
- Review logs dating to July 2025
- Restrict outbound internet access from EBS systems
Healthcare Organizations:
- Enhanced backup procedures (frequent targets)
- Offline backups of patient data
- Incident response drills
- HIPAA compliance focus
- Regulatory reporting preparation
Conclusion: The Persistent Threat
Clop ransomware represents the evolution of cybercrime into a sophisticated, well-funded, and resilient business operation. The group's systematic exploitation of zero-day vulnerabilities in widely-deployed enterprise software has fundamentally changed the ransomware landscape, demonstrating how supply chain attacks can achieve unprecedented scale and impact.
Key Takeaways
Clop's Success Factors:
- Strategic Innovation: Shift from encryption to pure data theft extortion
- Technical Excellence: Consistent zero-day discovery and exploitation
- Operational Security: Core operators remain unreachable in Russian territory
- Business Model: RaaS structure provides scalability and resilience
- Target Selection: Focus on supply chain vulnerabilities for maximum impact
The Ongoing Challenge: Despite law enforcement efforts, Clop continues to operate with apparent impunity. The June 2021 arrests in Ukraine disrupted money laundering operations but left core infrastructure intact. The group's ability to maintain operations demonstrates the challenges of combating well-resourced, geographically dispersed cybercrime organizations operating from safe havens.
Industry Impact: Clop has forced fundamental changes in how organizations approach cybersecurity:
- Emergency patching is now critical business function
- Managed file transfer software is recognized as high-risk
- Data theft alone (without encryption) can be catastrophic
- Supply chain vulnerabilities require continuous attention
- Backup strategies must assume breach
Future Outlook: Based on current trajectory, Clop is likely to:
- Continue targeting MFT and ERP software
- Expand into new software categories
- Increase technical sophistication
- Grow ransom demands for high-value targets
- Maintain pace of major campaigns (1-2 per year)
The group's estimated $500+ million in proceeds provides substantial resources for research and development, suggesting their zero-day capabilities will continue to improve. Organizations must assume Clop will discover and exploit vulnerabilities in whatever software they use next.
Final Recommendations
For Organizations:
- Implement defense-in-depth strategies
- Prioritize patching of internet-facing applications
- Maintain air-gapped backups
- Prepare incident response plans
- Consider cyber insurance with ransomware coverage
- Engage in threat intelligence sharing
- Report incidents to law enforcement
For Vendors:
- Conduct regular security audits
- Implement secure development practices
- Maintain vulnerability disclosure programs
- Provide rapid security updates
- Communicate clearly with customers about risks
For Policymakers:
- Strengthen international cybercrime cooperation
- Address safe haven issues diplomatically
- Consider sanctions on ransomware-enabling services
- Support victim notification and assistance programs
- Invest in law enforcement cybercrime capabilities
Clop's success demonstrates that ransomware is not merely a technical problem but a complex challenge requiring coordinated responses from organizations, vendors, law enforcement, and governments. Only through sustained, multi-layered efforts can the cybersecurity community hope to mitigate the threat posed by groups like Clop.
Additional Resources
In-Depth Analysis:
- Trend Micro Ransomware Spotlight: Clop - Comprehensive technical analysis with detection data and infection chains
Official Advisories:
- CISA AA23-158A: #StopRansomware: CL0P Ransomware Gang Exploits CVE-2023-34362 MOVEit Vulnerability
- FBI IC3 Alert: CL0P Ransomware Gang
- Canadian Centre for Cyber Security: Profile: TA505 / CL0P ransomware
Threat Intelligence:
- MITRE ATT&CK: TA505 Group Profile
- Mandiant/Google Threat Intelligence Group: Oracle E-Business Suite Zero-Day Analysis
- CrowdStrike: Clop/TA505 Intelligence Reports
Technical Resources:
- Oracle Security Alert: CVE-2025-61882
- Progress Software: MOVEit Transfer Security Updates
- CISA Known Exploited Vulnerabilities Catalog
Related Coverage:
- American Airlines Subsidiary Hit by Clop Ransomware in Oracle Zero-Day Attack - Detailed analysis of the Envoy Air breach
Reporting:
- FBI Internet Crime Complaint Center (IC3): www.ic3.gov
- CISA Cybersecurity: www.cisa.gov/report
- Rewards for Justice: rewardsforjustice.net
Document Version: 1.0 Last Updated: October 17, 2025 Classification: Public Information / Threat Intelligence Author: Cybersecurity Research Team
This article is provided for informational and educational purposes. Organizations should consult with cybersecurity professionals and legal counsel for specific guidance on addressing the Clop ransomware threat.