Countries Shore Up Digital Defenses as Global Tensions Raise the Threat of Cyberwarfare

As the world enters a new era of heightened geopolitical tension, the digital battlefield has become as crucial as any physical front. Over the past year, governments and businesses worldwide have scrambled to reinforce their cyberdefenses, spurred by a surge in state-sponsored cyberattacks, shifting alliances, and the looming specter of trade wars124.
The New Face of Conflict: Cyberattacks on Critical Infrastructure
Last spring, hackers linked to the Russian government targeted municipal water plants in rural Texas. In Muleshoe, a town of 5,000, the attack caused water to overflow, forcing officials to disconnect automated systems and operate the plant manually. This breach wasn’t about ransom or sabotage—it was a calculated probe, designed to expose vulnerabilities in America’s public infrastructure and serve as a stark warning: digital security is now integral to national security1249.
Such incidents are no longer isolated. As global tensions rise—driven by wars in Ukraine and the Middle East, trade disputes, and shifting alliances—the risk of cyberattacks causing economic damage, disrupting vital services, or escalating into military confrontation is at an all-time high14811.

A Global Digital Arms Race
National security and cybersecurity experts warn that the world is entering a digital arms race. Countries are investing heavily in both offensive and defensive cyber capabilities. The stakes are high: a successful cyberattack can cripple power grids, disrupt financial systems, or compromise sensitive government and corporate secrets1214.
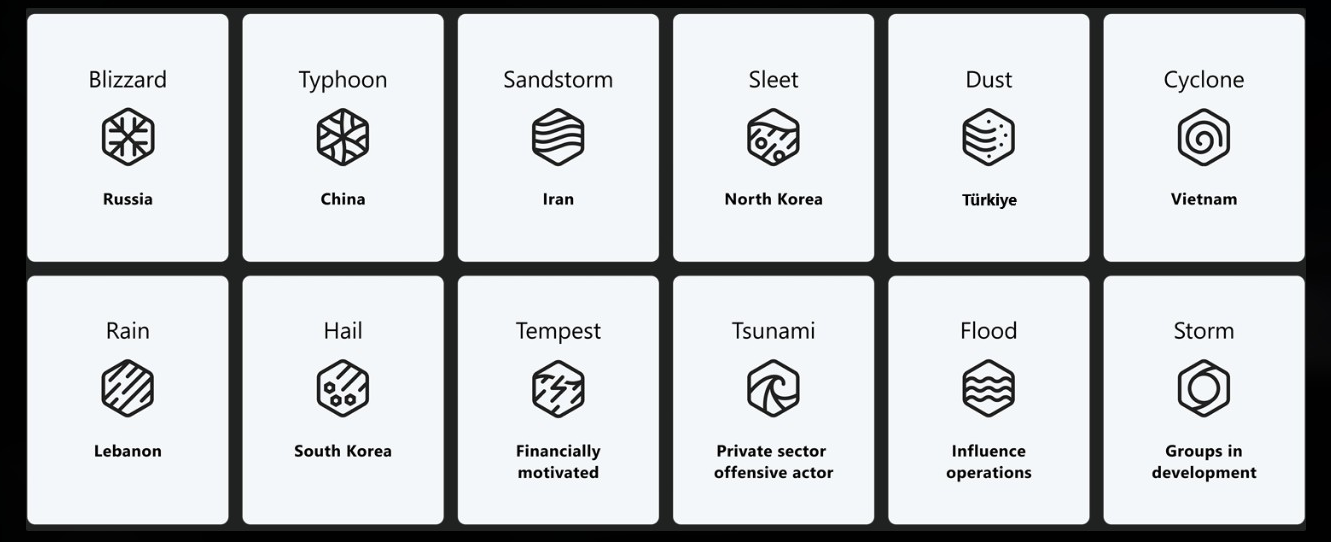
Espionage remains a primary motive. Recent campaigns tied to Chinese hackers, such as “Salt Typhoon,” sought to infiltrate the phones of U.S. officials—including former President Trump—prior to the 2024 election. These operations aim to gather intelligence for leverage in trade negotiations or military planning, often remaining undetected for extended periods149.
Other attacks are more overt, serving as warnings or political statements. Iran, for example, has demonstrated a willingness to use cyberattacks to make geopolitical points149.
Perhaps most concerning are “deep” intrusions—attacks that embed backdoors or malware in critical infrastructure, poised to be activated in the event of a larger conflict. The Chinese “Volt Typhoon” campaign reportedly compromised U.S. telephone networks, potentially giving China the ability to disrupt power plants, pipelines, hospitals, and financial systems if tensions escalate, particularly over Taiwan19.
Shifting Alliances and Cyber Cooperation
The risk landscape is further complicated by increased cyber cooperation among U.S. adversaries. China, Russia, Iran, and North Korea are forging tighter economic, military, and political relationships, sometimes exchanging cyber capabilities and intelligence. For example, Iran has reportedly supplied drones to Russia in exchange for intelligence and cyber expertise, with Russia acting as a catalyst for this expanded cooperation, particularly in the context of its war in Ukraine1811.
This web of alliances raises the risk of coordinated cyber campaigns and makes attribution—and retaliation—more complex and dangerous. Any tit-for-tat cycle of cyber conflict could quickly spiral, increasing the risk of military escalation1811.

The Trump Administration’s Cybersecurity Shakeup
Amid these mounting threats, the U.S. has seen significant changes in its approach to cybersecurity. President Donald Trump has fired the four-star general leading the National Security Agency (NSA) and U.S. Cyber Command, reduced staffing at key cybersecurity agencies, and slashed funding for election security initiatives1249.
These moves have drawn criticism from national security experts and lawmakers, who argue that the U.S. faces “unprecedented cyber threats” and should be bolstering—not shrinking—its cyber defenses. Virginia Senator Mark Warner, the top Democrat on the Senate Intelligence Committee, has questioned how such changes make Americans safer129.
The administration, however, contends that these changes will streamline operations, eliminate waste, and focus resources on emerging threats. The Pentagon, for example, is investing in artificial intelligence to strengthen cyberdefenses19.

The Expanding Attack Surface
The proliferation of connected devices—from fitness trackers to industrial control systems—has vastly expanded the number of potential targets. Each networked device, whether in a home, business, or critical facility, represents a possible entry point for hackers14914.
Supply chains are particularly vulnerable. While large corporations may have robust cybersecurity teams, smaller suppliers often lack the resources to defend against sophisticated attacks, making them attractive targets for adversaries seeking to compromise larger networks189.
The Private Sector’s Growing Role
Businesses are increasingly on the front lines of this digital conflict. According to a recent report by NCC Group, companies are more concerned than ever about cyberattacks, and many are calling for clearer government guidance and stronger public-private partnerships124.
The cybersecurity workforce gap remains a critical challenge. Federal estimates suggest the industry needs to hire an additional 500,000 professionals to meet current threats. Experts stress the need for a comprehensive “playbook” to help companies understand best practices for defense and incident response19.

Signs of Progress and the Push for Global Cooperation
Despite the challenges, there are glimmers of progress. More than 20 nations have signed onto an international framework governing the use of commercial spyware, with the U.S. signaling its intent to join. There is also broad bipartisan agreement in Congress on the need to help private industry strengthen its defenses19.
The World Economic Forum’s Global Cybersecurity Outlook 2025 highlights the growing complexity of the cyber environment, shaped by geopolitical tensions, emerging technologies, and supply chain dependencies. It calls for a security-first approach and greater international collaboration to address these evolving threats1418.
Conclusion
The digital frontier is now a central arena for global competition and conflict. As nations shore up their cyberdefenses, the line between peace and war grows increasingly blurred in cyberspace. The stakes are high—not just for governments, but for businesses, critical infrastructure, and ordinary citizens. In this new era, vigilance, cooperation, and innovation are essential to safeguarding the systems that underpin modern society1414.
Citations:
- https://apnews.com/article/cybersecurity-trump-china-russia-iran-north-korea-9eceaf30ddc984ed482f067db5dee405
- https://www.helpnetsecurity.com/2025/04/01/global-tensions-cybersecurity-problem/
- https://abcnews.go.com/Politics/wireStory/countries-shore-digital-defenses-global-tensions-raise-threat-120987665
- https://www.csis.org
- https://www.dni.gov/index.php/gt2040-home/emerging-dynamics/international-dynamics
- https://www.pwc.com/us/en/services/consulting/cybersecurity-risk-regulatory/library/cybersecurity-geopolitical-conflict-board-ceo-response.html
- https://wtop.com/government/2025/04/countries-shore-up-their-digital-defenses-as-global-tensions-raise-the-threat-of-cyberwarfare/
- https://www.yahoo.com/news/countries-shore-digital-defenses-global-122458101.html
- https://www.click2houston.com/click2vote/
- https://www.ajc.com/news/nation-world/countries-shore-up-their-digital-defenses-as-global-tensions-raise-the-threat-of-cyberwarfare/II3NHFUW7FFJRGBEHJRKRFKLDI/
- https://gjia.georgetown.edu/articles/conflict-and-securit/
- https://hbr.org/2024/11/navigating-the-new-geopolitics-of-tech
- https://industrialcyber.co/reports/wef-global-cybersecurity-outlook-2025-report-addresses-geopolitical-tensions-emerging-threats-to-boost-resilience/
- https://www.iseoblue.com/post/impact-of-geopolitical-conflicts-on-cybersecurity-risks
- https://www.weforum.org/stories/2025/01/global-cybersecurity-outlook-complex-cyberspace-2025/
- https://www.infosecurity-magazine.com/news-features/cybersecurity-challenges/
- https://reports.weforum.org/docs/WEF_Global_Cybersecurity_Outlook_2025.pdf
- https://thecyberexpress.com/geopolitical-cybersecurity-tension/amp/










