CrowdStrike Confirms Insider Threat Linked to Scattered Lapsus$ Hunters Cybercrime Alliance
Breaking: Cybersecurity Giant Terminates Employee Who Allegedly Sold Screenshots to Notorious Hacking Collective
Executive Summary
In a stark reminder that insider threats remain one of the most challenging security vulnerabilities, CrowdStrike has confirmed it terminated an employee last month who allegedly shared internal system screenshots with the notorious Scattered Lapsus$ Hunters cybercrime collective. The incident, disclosed November 21, 2025, represents a troubling escalation in tactics by a hacking supergroup that has already compromised hundreds of major corporations through sophisticated social engineering campaigns targeting Salesforce and other enterprise platforms.

The disclosure comes as the same threat actors claim responsibility for a massive new wave of data theft attacks affecting over 280 companies through compromised Gainsight applications connected to Salesforce, with high-profile victims including Google, LinkedIn, GitLab, Atlassian, Verizon, and Malwarebytes among those allegedly impacted.
The CrowdStrike Insider Incident: Key Facts
What Happened
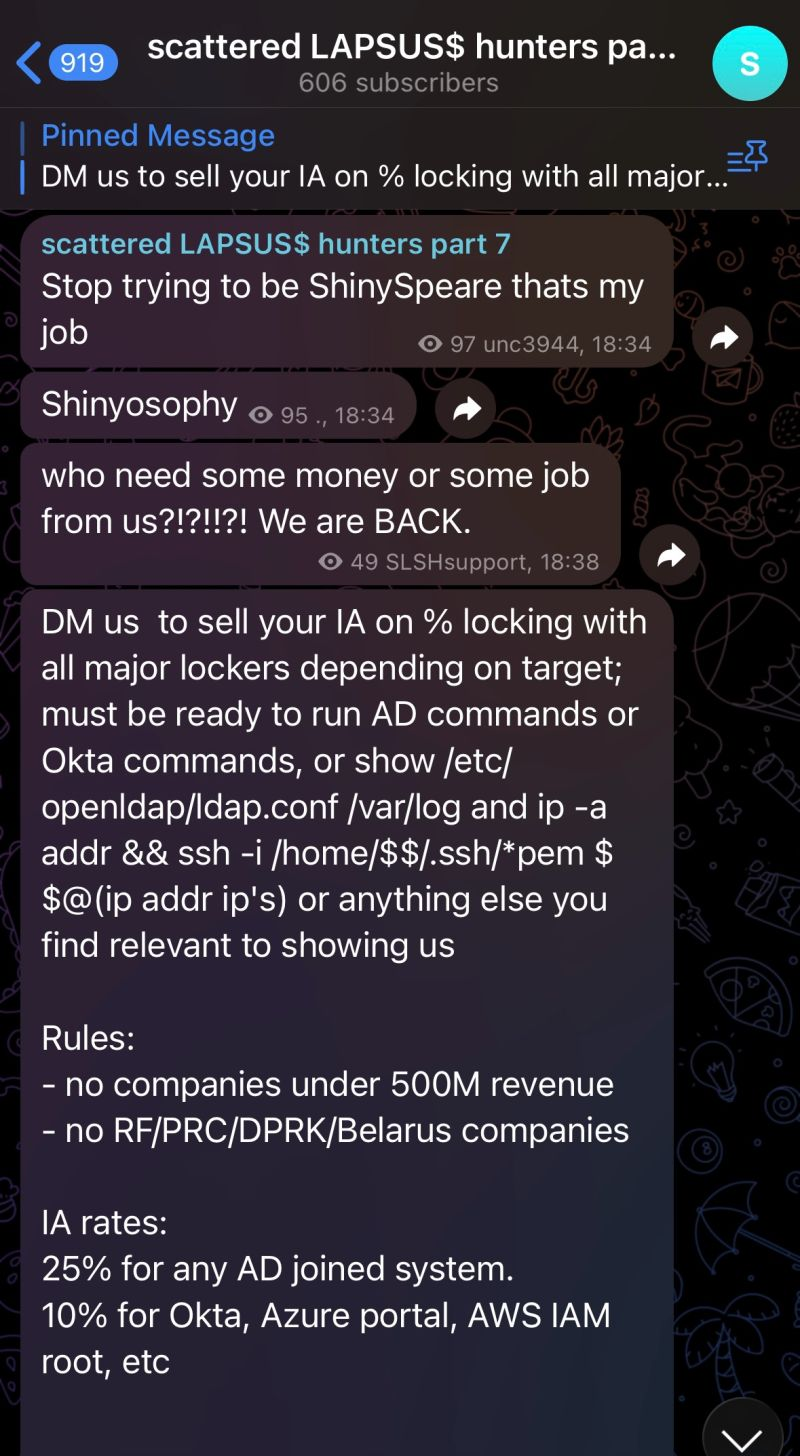
CrowdStrike identified and terminated what the company describes as a "suspicious insider" following an internal investigation that determined the employee had shared pictures of computer screens with external parties. The screenshots were subsequently leaked on Telegram by members of the Scattered Lapsus$ Hunters threat collective, which operates as an alliance of three infamous cybercrime groups: ShinyHunters, Scattered Spider, and Lapsus$.
"We identified and terminated a suspicious insider last month following an internal investigation that determined he shared pictures of his computer screen externally," a CrowdStrike spokesperson stated. "Our systems were never compromised and customers remained protected throughout. We have turned the case over to relevant law enforcement agencies."
The Alleged Transaction
According to ShinyHunters representatives who spoke with security researchers, the threat actors allegedly agreed to pay the insider $25,000 to provide them with access to CrowdStrike's network. The group claims they ultimately received SSO (Single Sign-On) authentication cookies from the insider, but by that time, CrowdStrike had already detected the suspicious activity and shut down the employee's network access.
The screenshots posted on Telegram reportedly showed internal dashboards containing links to company resources, including an Okta dashboard used by employees for accessing internal applications.
The extortion group also stated they attempted to purchase CrowdStrike intelligence reports on ShinyHunters and Scattered Spider themselves, but did not receive them before the insider was terminated.
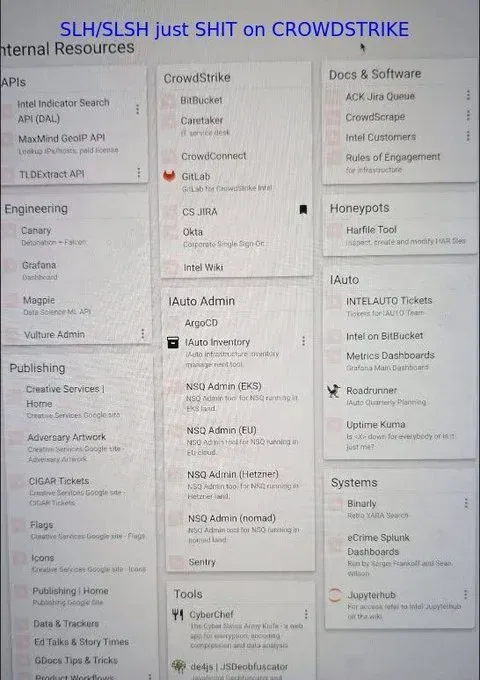
Critical Context: No System Breach
CrowdStrike has been emphatic that while an insider shared screenshots, their systems were never actually breached. This distinction is important—the incident represents a human vulnerability rather than a technical compromise of CrowdStrike's cybersecurity infrastructure. Customer data was not compromised, and protective capabilities remained intact throughout the incident.
The Broader Scattered Lapsus$ Hunters Campaign
Understanding the Threat Alliance
Scattered Lapsus$ Hunters represents a cybercrime supergroup that emerged in 2025 as a formalized alliance between three previously separate but overlapping threat actors:
- ShinyHunters: Active since 2020, known for massive database breaches and data theft operations targeting cloud infrastructure
- Scattered Spider: Specialized in social engineering, help desk impersonation, and vishing (voice phishing) attacks
- Lapsus$: Notorious for insider recruitment, source code theft, and high-profile breaches of major technology companies
This alliance combines the technical capabilities and social engineering expertise of each group into a coordinated operation that has proven devastatingly effective against enterprise targets.
The Gainsight Campaign: Another Supply Chain Catastrophe
On November 20, 2025, Salesforce issued a security advisory confirming that threat actors had gained unauthorized access to customer data through applications published by Gainsight, a customer success platform provider. This represents the second major supply chain attack against Salesforce customers in just three months.
Scale of the Breach:
- Google Threat Intelligence Group reports awareness of more than 200 potentially affected Salesforce instances
- ShinyHunters claims to have stolen data from nearly 1,000 organizations across both the Salesloft and Gainsight campaigns combined
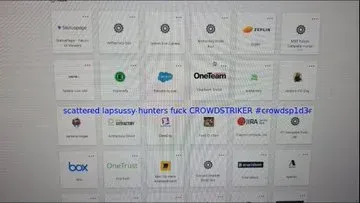
- High-profile victims allegedly include Verizon, GitLab, F5, SonicWall, LinkedIn, Atlassian, Thomson Reuters, DocuSign, and Malwarebytes
Attack Methodology: The attackers compromised Gainsight through secrets stolen during a previous breach of Salesloft's Drift platform. By obtaining OAuth tokens and API access through these trusted third-party integrations, the threat actors bypassed traditional authentication mechanisms and gained direct access to Salesforce customer data.
Salesforce responded by revoking all active access and refresh tokens associated with Gainsight-published applications and temporarily removing them from the AppExchange marketplace.
The Salesloft/Drift Precedent
The current Gainsight campaign follows an eerily similar pattern to an August 2025 attack that compromised over 700 organizations through Salesloft's Drift integration. A comprehensive analysis of this supply chain attack reveals how threat actors exploited OAuth tokens stolen from the Drift integration to access customer Salesforce environments.
Previous Victims Included:
- Google (confirmed breach of corporate Salesforce instance)
- Cloudflare
- Cisco
- Palo Alto Networks and Zscaler
- Allianz Life
- Farmers Insurance
- Qantas Airways
- Adidas
- Workday
- LVMH subsidiaries (Dior, Louis Vuitton, Tiffany & Co.)
In the Salesloft case, investigators traced the root cause to threat actors who had gained access to Salesloft's GitHub repositories as far back as March 2025, establishing persistent access that went undetected for months before the August data exfiltration campaign.
Tactics, Techniques, and Procedures (TTPs)
Social Engineering Excellence
Scattered Lapsus$ Hunters has distinguished itself through sophisticated social engineering campaigns that exploit human vulnerabilities rather than technical flaws:
Voice Phishing (Vishing):
- Impersonating IT support staff with convincing scripts
- Using spoofed caller IDs and potentially voice-altering technology
- Conducting extensive OSINT research to gather employee information
- Accurately providing employee IDs and answering verification questions during help desk calls
Help Desk Manipulation:
- Convincing IT support to reset credentials
- Bypassing multi-factor authentication through social manipulation
- Requesting installation of malicious applications disguised as legitimate tools
Insider Recruitment: The CrowdStrike incident exemplifies another key tactic: actively recruiting insiders through dark web channels. The group has posted recruitment messages on Telegram seeking individuals with access to:
- Okta
- Microsoft SSO
- Citrix VPN
- GitHub/GitLab repositories
OAuth Token Abuse
A consistent pattern across multiple campaigns involves the exploitation of OAuth tokens and third-party integrations:
- Compromise trusted third-party vendors (Salesloft, Gainsight)
- Steal OAuth tokens and API credentials from these vendors
- Use stolen credentials to access customer Salesforce instances without exploiting any vulnerability in Salesforce itself
- Export large volumes of CRM data through legitimate API calls
- Extort victims with threats to publish stolen data
Infrastructure and Obfuscation
The group employs sophisticated operational security measures:
- Mullvad VPN and TOR network routing
- Custom Python scripts for data exfiltration
- Modified versions of legitimate tools (e.g., Salesforce Data Loader)
- Rotating Telegram channels (at least 25 different channels created between August and October 2025)
The ShinySp1d3r Ransomware Operation
In a concerning evolution, ShinyHunters and Scattered Spider have switched to a new ransomware-as-a-service platform called "ShinySp1d3r" after previously using encryptors from ALPHV/BlackCat, RansomHub, Qilin, and DragonForce.
The group promotes this RaaS platform as being faster and more adaptive than competitors like LockBit, positioning themselves not just as data thieves but as a comprehensive cybercriminal service provider.
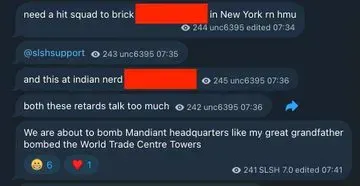
Concerning Escalation: Physical Threats
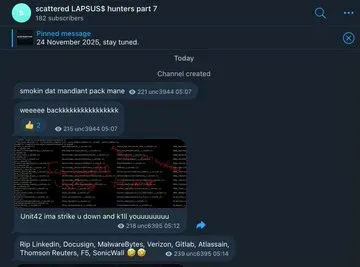
Perhaps most disturbing are recent reports that Scattered Lapsus$ Hunters members have made violent threats against security researchers and threat intelligence personnel. According to security researcher Brian Krebs, members sent malware-laden messages threatening physical violence to employees at Google Threat Intelligence and Mandiant.
Social media posts referenced attempts to "orchestrate the murders of Google Threat Intelligence employees in New York," though the credibility and seriousness of these threats remain under investigation by law enforcement. The group specifically demanded the termination of Austin Larsen and Charles Carmakal from Google Threat Intelligence.
The group has also claimed to be seeking cooperation with Mexican drug cartels to sell personal data of FBI employees—claims that underscore the increasingly chaotic and dangerous nature of this threat collective.
This represents a concerning evolution where cybercriminals escalate beyond data theft to directly targeting security professionals, marking a dangerous new phase where human capital becomes a weapon in cyber warfare.
Attribution Challenges and Law Enforcement Response
The Identity Problem
Scattered Lapsus$ Hunters operates as what security researchers describe as a "decentralized brand" rather than a cohesive organization. This creates significant attribution challenges:
- Multiple actors using the same identity: Individual criminals can operate under the ShinyHunters or Scattered Spider names for reputation and intimidation value
- Fluid membership: Members move between groups or operate independently while claiming affiliation
- Overlapping toolsets: Similar TTPs used by different actors make definitive attribution difficult
Google Threat Intelligence tracks various aspects of their activity under multiple UNC (Uncategorized) designations:
- UNC6040: Initial compromise activities
- UNC6240: Extortion operations
- UNC6395: OAuth token exploitation campaigns
Arrests and Continued Activity
Despite multiple arrests, the collective continues to operate:
Recent Law Enforcement Actions:
- June 2024: Several alleged ShinyHunters members arrested
- August 2025: Noah Michael Urban (20, Florida) sentenced to 10 years in federal prison and ordered to pay $13 million in restitution
- April 2025: Tyler Robert Buchanan (23, Scotland) extradited from Spain to face charges of wire fraud, conspiracy, and identity theft
- September 2025: Multiple Scattered Spider members arrested in UK including Owen Flowers (18) and Thalha Jubair (19) in connection with Transport for London attack
- October 2025: FBI seizure of BreachForums, the primary marketplace used by these groups
The persistence of the group despite these arrests suggests either:
- Arrested individuals represent only a fraction of the collective
- New members continuously join to replace those caught
- The decentralized nature allows operations to continue despite individual losses
The "Advanced Persistent Teenagers" Phenomenon
Security researcher Kevin Beaumont coined the term "Advanced Persistent Teenagers" (APT-T) to describe this phenomenon of young cybercriminals conducting sophisticated attacks against major corporations. Many identified members have been surprisingly young—in their late teens or early twenties—yet capable of causing hundreds of millions of dollars in damages.
Industry Impact and Financial Toll
The scale of damage attributed to Scattered Lapsus$ Hunters operations in 2025 is staggering:
- Jaguar Land Rover: Over £196 million ($220 million) in damages from a single breach
- UK Retail Sector: £440M in damages to M&S, Co-op, and Harrods
- Insurance Industry: Systematic targeting of major insurers including Aflac, Allianz Life, and Farmers
- Aviation Sector: Coordinated attacks on Hawaiian Airlines, WestJet, and Qantas
- 700+ organizations impacted in the Salesloft/Drift campaign
- 200+ organizations potentially affected in the Gainsight campaign
- Billions of customer records stolen across multiple campaigns
The group operates a sophisticated extortion model:
- Steal data through compromised integrations
- Contact victims privately with ransom demands
- If payment is not received, publish stolen data on dedicated leak sites
- Target media outlets to maximize pressure on victims
The SaaS Supply Chain Vulnerability
These incidents expose a fundamental weakness in modern enterprise security architecture: the SaaS supply chain. Organizations increasingly rely on interconnected cloud applications that share data through OAuth tokens and API integrations. This creates:
Expanded Attack Surface:
- Each third-party integration represents a potential entry point
- Trust relationships between vendors create lateral movement opportunities
- OAuth tokens often have broad permissions that enable extensive data access
Cascading Failures:
- Compromise of a single vendor can affect hundreds or thousands of their customers
- Organizations have limited visibility into their vendors' security practices
- Traditional perimeter security is ineffective against trusted application abuse
Incident Response Challenges:
- Difficulty determining if your organization was affected
- No direct control over compromised vendor systems
- Potential for long dwell times before detection
Defensive Recommendations
For Organizations
Immediate Actions:
- Audit All Third-Party Integrations
- Review every connected app in Salesforce and other SaaS platforms
- Remove or restrict integrations that don't require broad API access
- Document business justification for each integration
- Rotate OAuth Tokens
- Immediately rotate vendor OAuth tokens, especially for Salesforce integrations
- Treat any token with broad permissions as high-risk
- Implement token expiration policies
- Review Authentication Logs
- Look for unusual SSO activity
- Monitor for OAuth token usage from unexpected geographic locations
- Watch for API calls outside normal usage patterns
Strategic Improvements:
- Enhanced Vendor Risk Management
- Conduct security assessments of all SaaS vendors
- Require vendors to demonstrate security controls
- Include security requirements in vendor contracts
- Monitor vendor security incidents affecting other customers
- Principle of Least Privilege for Integrations
- Grant integrations only the minimum necessary permissions
- Regularly review and reduce excessive permissions
- Segment data access by integration purpose
- Social Engineering Defenses
- Implement strict verification procedures for IT support requests
- Never share credentials or MFA codes over phone/email
- Establish out-of-band verification for credential resets
- Train employees to recognize vishing attacks (as used in Scattered Spider's playbook)
- Create clear escalation paths for suspicious requests
- Consider that English-speaking threat actors can be particularly convincing in social engineering attacks
- Insider Threat Programs
- Monitor for unusual data access patterns by employees
- Implement behavioral analytics
- Conduct regular security awareness training
- Establish confidential reporting mechanisms
- Consider implementing privileged access management (PAM) solutions
- API and OAuth Security
- Implement OAuth token rotation policies
- Monitor API usage for anomalies
- Use API gateways to control and log access
- Implement rate limiting on sensitive API endpoints
- Consider zero-trust architecture for API access
For Individuals
- Be Skeptical of IT Support Calls
- Legitimate IT never asks for passwords or MFA codes
- Hang up and call back using official company numbers
- Verify requests through secondary communication channels
- Report Suspicious Activity
- Immediately report unusual IT support contacts
- Document details of suspicious calls or messages
- Don't be embarrassed to report potential social engineering attempts
- Protect Personal Information
- Limit publicly available information on LinkedIn and social media
- Be cautious about job title and responsibility details
- Consider the OSINT value of your public profile
The Bigger Picture: Systemic Vulnerabilities
The Scattered Lapsus$ Hunters campaign exposes several concerning trends in enterprise cybersecurity:
Human Vulnerability Persists
Despite billions spent on technical security controls, sophisticated social engineering continues to bypass even the most advanced defenses. Organizations must invest equally in human-centric security:
- Continuous security awareness training
- Realistic phishing and vishing simulations
- Cultural emphasis on security skepticism
- Psychological safety to report potential compromises
Supply Chain Security is Immature
The SaaS ecosystem lacks robust supply chain security frameworks:
- No standardized vendor security assessments
- Limited visibility into vendor security practices
- Insufficient incident disclosure requirements
- Weak contractual security obligations
OAuth and API Security Models Need Evolution
Current OAuth implementations often grant overly broad permissions that enable significant data exfiltration if tokens are compromised. The industry needs:
- More granular permission models
- Mandatory token rotation policies
- Better visibility into token usage
- Standardized OAuth security baselines
The Insider Threat Remains Underestimated
The CrowdStrike incident demonstrates that even security-focused organizations face insider risks. The ease with which threat actors recruit insiders suggests:
- Financial incentives are compelling (as seen in cases of government contractors and corporate employees)
- Detection capabilities may be inadequate
- Deterrence through consequences is insufficient
- Organizations need better insider threat programs
The pattern of insider recruitment by sophisticated threat actors extends beyond cybersecurity companies to include military personnel and research institutions, demonstrating the widespread nature of this threat vector.
What's Next?
Threat Evolution
Scattered Lapsus$ Hunters continues to evolve its tactics:
- Announced "temporary shutdown" in September 2025, but activity has continued
- Shifting between different ransomware platforms
- Exploring new supply chain targets beyond Salesforce
- Increasingly brazen public threats and extortion tactics
The collective's activity throughout August 2025 alone demonstrated the unprecedented scale of their operations, with dozens of high-profile victims across multiple sectors.
Law Enforcement Pressure
Multiple international law enforcement agencies are actively investigating:
- FBI issued FLASH alerts in September 2025
- Europol coordination on international arrests
- Increased collaboration between private sector threat intelligence and law enforcement
- Potential for additional arrests based on ongoing investigations
Regulatory Response
These incidents may trigger regulatory action:
- Potential new disclosure requirements for SaaS vendors
- Enhanced breach notification timelines
- Mandatory security standards for third-party integrations
- Increased liability for vendors in supply chain attacks
Conclusion
The CrowdStrike insider incident, while contained without customer impact, serves as a sobering reminder that even the world's leading cybersecurity companies face threats from insiders who can be recruited by sophisticated adversaries. When combined with the massive Gainsight and Salesloft breaches affecting hundreds of organizations, the Scattered Lapsus$ Hunters campaign represents one of the most significant cybersecurity challenges of 2025.

tThe group's success stems not from technical sophistication, but from exploiting fundamental weaknesses in how humans and organizations manage trust, identity, and access. Their targeting of supply chain integrations—particularly OAuth-based SaaS connections—has exposed architectural vulnerabilities that affect virtually every enterprise organization.
As organizations rush to audit their Salesforce integrations and third-party connections, the broader lesson is clear: modern cybersecurity must address the human element and supply chain risks with the same rigor applied to technical controls. The era of perimeter security is definitively over—in today's interconnected enterprise environment, security is only as strong as the weakest link in an increasingly complex chain of trusted relationships.
For cybersecurity professionals, the message is urgent: audit your integrations, train your people, and prepare for a threat landscape where social engineering and supply chain attacks will continue to be the most effective attack vectors against even the most technically sophisticated defenses.

Key Takeaways
- CrowdStrike terminated an insider who allegedly sold screenshots to Scattered Lapsus$ Hunters for $25,000, though no systems were breached
- Gainsight breach affects 200+ Salesforce customers, following similar Salesloft attack that compromised 700+ organizations
- Combined campaigns may have affected nearly 1,000 enterprises including Google, LinkedIn, Verizon, and major corporations
- Social engineering remains dominant tactic: Vishing, help desk impersonation, and insider recruitment prove more effective than technical exploits
- OAuth token abuse enables widespread data theft through legitimate API access without exploiting platform vulnerabilities
- Supply chain security is critically immature, with third-party integrations creating cascading failure scenarios
- Immediate action required: Organizations must audit all SaaS integrations, rotate OAuth tokens, and enhance social engineering defenses
Disclaimer: Information in this article is compiled from public sources including quoted CrowdStrike statements, security researcher disclosures, and media reports. Organizations concerned about potential impact should contact their security vendors and review their specific configurations.
‼️ Scattered LAPSUS$ ShinyHunters members have returned with new breaches and serious threats.
— International Cyber Digest (@IntCyberDigest) November 21, 2025
They are attempting to orchestrate the murders of Google Threat Intelligence employees in New York.
They also claim to have breached FBI Cellebrite accounts, CrowdStrike, Salesforce,… pic.twitter.com/jyklKjY82s














