Cybersecurity Threat Landscape and 2026 Outlook
Executive Summary
The global cybersecurity environment in 2025 is defined by a complex interplay of evolving threats, advancing defensive technologies, and persistent vulnerabilities. While the global average cost of a data breach has seen a 9% decrease to $4.44 million, this figure masks a concerning surge in the United States, where costs have reached an all-time high of $10.22 million due to escalating regulatory fines and detection expenses. Organizations have improved their response capabilities, with the mean time to identify and contain a breach falling to a nine-year low of 241 days. However, the human element remains a critical weakness, implicated in 60% of all breaches.
Artificial Intelligence (AI) has emerged as a dual-edged sword. Threat actors are leveraging AI for sophisticated attacks, with one in six breaches in 2025 involving AI-driven methods like advanced phishing and deepfakes. Conversely, organizations extensively using security AI and automation realize substantial benefits, including an 80-day faster response time and cost savings of nearly $1.9 million per breach.
Key attack vectors continue to be dominated by the exploitation of public-facing applications and the use of valid credentials. Supply chain compromises have surged to become the second most prevalent and second costliest attack vector, averaging $4.91 million. Ransomware persists as a dominant threat, involved in up to 44% of breaches and accounting for half of all attacks against critical infrastructure sectors in 2025.
Looking ahead to 2026, predictions indicate a seismic shift driven by autonomous "agentic AI," which will become both a primary target and a tool for attack, creating a new class of "autonomous insider" threats. Identity is solidifying as the new security perimeter, with a forecasted 82:1 ratio of machine-to-human identities creating a vast new attack surface. The strategic "harvest now, decrypt later" approach by adversaries is accelerating the imperative for post-quantum cryptography, while legal precedent is expected to establish personal liability for executives in cases of rogue AI actions.
I. The Current Data Breach Landscape: Key Statistics for 2025
The financial and operational impacts of data breaches remain substantial, though global trends show nuanced shifts. Analysis from authorities including IBM, Verizon, and the Identity Theft Resource Center (ITRC) paints a detailed picture of the current environment.
Financial Impact
Metric | 2025 Value | Comparison / Context | Source |
Global Average Breach Cost | $4.44 million | 9% decrease from 2024 all-time high ($4.88M); return to 2023 levels. | IBM |
U.S. Average Breach Cost | $10.22 million | All-time high for any region; a 9% surge from 2024. | IBM |
Healthcare Sector Breach Cost | $7.42 million | Ranks as one of the highest-cost industries. | Bright Defense |
Cost of Lost Business | $1.38 million | Includes system downtime, lost customers, and reputation damage. | IBM |
Breach Notification Costs | $390,000 | Nearly a 10% decrease from $430k in 2024. | IBM |
Cost per Record (Customer PII) | $160 | Personally Identifiable Information remains a high-value target. | IBM |
Cost per Record (Intellectual Property) | $178 | The most expensive data type per record. | IBM |
Several factors significantly influence the total cost of a data breach:
- Cost Amplifiers: The most significant cost-increasing factors include supply chain breaches, security system complexity, shadow AI, noncompliance with regulations, and a security skills shortage. A high-level skills shortage can increase the average breach cost by 43% (from $3.65M to $5.22M).
- Cost Mitigators: The top factors that decrease costs are implementing a DevSecOps approach, using AI and machine learning-driven insights, employing security analytics (SIEM), leveraging threat intelligence, and extensive employee training. Adopting a Zero-Trust architecture was found to reduce breach costs by an average of $1.76 million.
- Passing Costs to Consumers: 45% of breached organizations reported increasing the cost of their services and products to offset breach expenses.
Breach Lifecycle and Detection
Metric | 2025 Value | Comparison / Context | Source |
Mean Time to Identify & Contain | 241 days | A nine-year low. | Secureframe |
Average Time to Identify (2024) | 194 days | Slight decrease from 2023. | Varonis (citing IBM) |
Average Time to Contain (2024) | 64 days | 9 days less than in 2023. | Varonis (citing IBM) |
Breaches with Lifecycle < 200 Days | N/A | Associated with 29% cost savings ($1.14M). | IBM |
Identification by Internal Teams | 50% | Significant increase from 42% in 2024 and 33% in 2023. | IBM |
- Detection Source Matters: Breaches identified internally by security teams cost an average of $4.18 million, compared to $5.08 million when disclosed by the attacker.
- Threat Intelligence Advantage: Organizations using threat intelligence identify threats 28 days faster on average.
II. Dominant Attack Vectors and Threat Actor Tactics
Cyber adversaries are employing a mix of established and evolving techniques, with a clear trend towards exploiting credentials, supply chains, and automated tools.
Initial Access and Intrusion Methods
- Top Initial Access Vectors: The most common initial attack vectors are the exploitation of public-facing applications and the use of valid account credentials, each accounting for 30% of incidents responded to by IBM X-Force.
- Stolen Credentials: The use of stolen or compromised credentials was a factor in 53% of all data breaches (Verizon DBIR 2025) and these breaches take the longest to resolve (292-day lifecycle).
- Phishing: Phishing remains a primary vector, present in 16% of breaches with an average cost of $4.8 million.
- Malware-Free Attacks: Adversaries are shifting away from traditional malware. In 2024, malware-free activity accounted for 79% of detections, a significant increase from 40% in 2019 (CrowdStrike).
- Vulnerability Exploitation: Attacks against critical infrastructure saw 26% of incidents exploit vulnerabilities in public-facing applications. Notably, 60% of the top 10 vulnerabilities discussed on the dark web had publicly available exploit code within two weeks of disclosure.
Ransomware and Extortion
Ransomware remains one ofthe most disruptive and financially damaging threats, characterized by its high cost and widespread impact.
- Prevalence: Ransomware was involved in 23% to 44% of breaches and, combined with extortion, makes up 59-66% of financially motivated cyberattacks.
- Cost: The average cost of a ransomware or extortion incident is high at $5.08 million.
- Detection Time: Ransomware breaches take approximately 49 days longer to detect than other incident types.
- Victim Response: Most organizations (63%) refused to pay the ransom in 2025, while 37% agreed to pay. Concurrently, fewer organizations are involving law enforcement, with engagement dropping from 52% in 2024 to 40% in 2025.
- Impact on Critical Infrastructure: 28% of critical infrastructure organizations faced destructive ransomware attacks. Globally, 50% of all ransomware attacks in 2025 (Jan-Sep) targeted critical sectors, with manufacturing, healthcare, and energy being the top targets.
Supply Chain and Third-Party Risk
Attacks targeting the supply chain have become a primary concern due to their widespread, cascading impact.
- Prevalence and Cost: Supply chain compromise was the source of 15% of breaches, making it the second most prevalent attack vector. It was also the second costliest, averaging **4.91 million** per incident, just behind malicious insider attacks (4.92M).
- Disproportionate Impact: In the first half of 2025, supply chain attacks accounted for less than 5% of all compromises but affected nearly half (47%) of all individuals impacted by breaches.
Malicious Insiders
Insider threats, whether malicious or accidental, remain a significant and costly risk.
- Cost: Malicious insider attacks are the single most expensive breach type, averaging $4.92 million.
- Prevalence: Internal actors were responsible for 29% of breaches (Verizon DBIR 2025). Human error alone caused 26% of breaches (IBM).
III. The Rise of Artificial Intelligence in Cybersecurity
AI is fundamentally reshaping the conflict between attackers and defenders, serving as both a powerful weapon and an indispensable shield.
Adversarial Use of AI
Attackers are leveraging AI to increase the scale, speed, and sophistication of their campaigns.
- Prevalence: 16% of all data breaches in 2025 involved attackers using AI.
- Top AI Attack Methods: The most common methods were AI-generated phishing (37%) and deepfakes (35%).
- Capabilities: Adversaries use AI to spin up convincing phishing messages in minutes, create flawless real-time deepfakes (e.g., "CEO doppelgängers"), and exploit vulnerabilities at scale.
- Shadow AI: The unsanctioned use of AI tools within an organization ("Shadow AI") is a top factor increasing breach costs, adding approximately $670,000 to the average incident.
Defensive Use of AI and Automation
Security teams are increasingly adopting AI-powered tools to counter advanced threats and augment strained workforces.
- Cost and Time Savings: Organizations with extensive use of security AI and automation identified and contained breaches 80 days faster and saw cost savings of nearly $1.9 million compared to those with no AI use.
- Key Defensive Capabilities:
- Analyzing large volumes of data to flag anomalous activity.
- Using real-time threat intelligence to block malicious URLs and files.
- Augmenting security teams by reducing false positives and prioritizing alerts.
- Supporting layered defenses like EDR, MFA, and passkeys.
IV. Strategic Vulnerabilities: Critical Infrastructure and Holiday Windows
Threat actors demonstrate strategic planning by targeting high-value, high-impact sectors and capitalizing on periods of reduced organizational vigilance.
Attacks on Critical Infrastructure
The targeting of critical infrastructure, particularly power grids, exemplifies the potential for cyberattacks to cause widespread societal disruption. The Russian cyberattacks on the Ukrainian power grid serve as a key case study.
- Power Grid Structure: Attacks can target three broad areas: Generation, Transmission, and Distribution.
- Case Study: 2015 Sandworm Attack (Ukraine):
- Initial Access: A spear-phishing campaign using malicious Microsoft Office macros installed the BlackEnergy 3 toolkit.
- Reconnaissance & Credential Theft: The toolkit, along with the Mimikatz plugin, was used to harvest credentials from Windows memory by exploiting weaknesses in NTLM and Kerberos authentication protocols.
- Attack Execution: The multi-pronged attack involved taking over Human-Machine Interfaces (HMIs), conducting a Telephone Denial-of-Service (TDoS) attack to disrupt the command-and-control center, and deploying firmware attacks to permanently "brick" serial-to-ethernet converters at over 30 substations.
- Case Study: 2016 Electrum Attack (Ukraine):
- Method: This more refined attack used a new program called CRASHOVERRIDE, designed to attack highly automated industrial control systems. It was not vendor-specific, allowing it to target a wider range of components.
- Execution: CRASHOVERRIDE was used to open and close breakers, followed by a data wiper component to erase critical Windows files needed for remote resets. A planned third phase to disable protective relays failed, limiting the attack's physical damage.
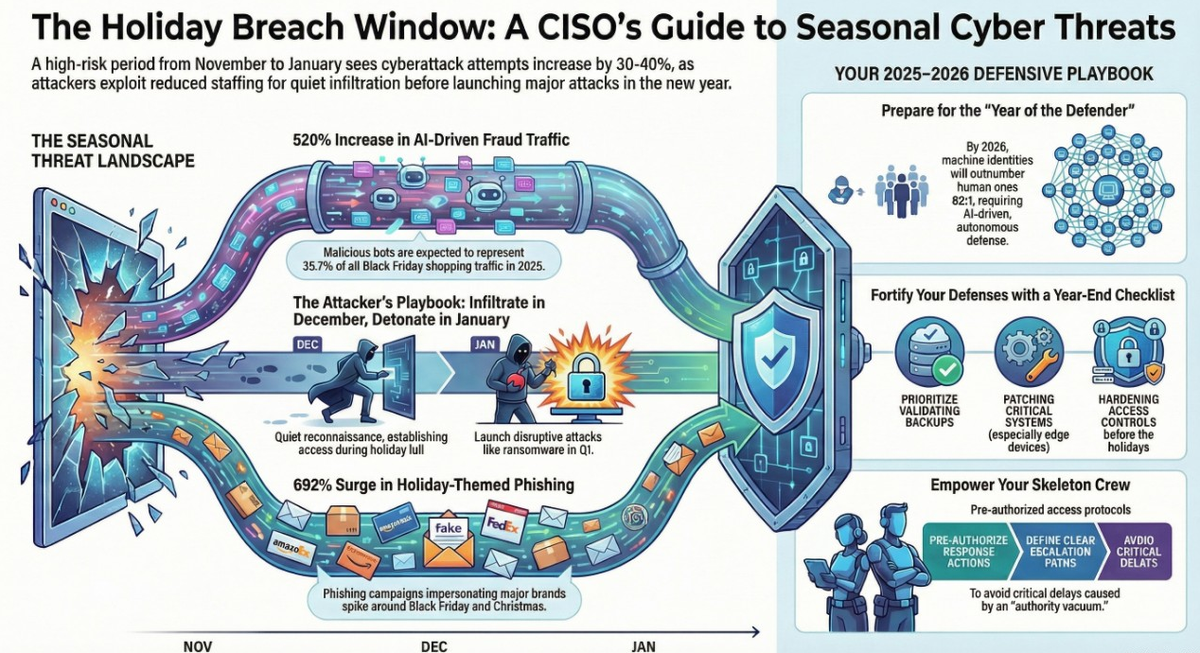
The Holiday Breach Window
The period from mid-November through early January is a strategically exploited timeframe characterized by reduced staffing and increased online activity, creating a high-risk environment.
- Increased Threat Volume: Reports indicate a 30-40% increase in cyberattack attempts during festive and public-holiday periods.
- Attacker Strategy: Threat actors use the "holiday lull" for deep reconnaissance, lateral movement, and staging attacks that are often not discovered until January. This leads to a consistent "January disclosure trend" for breaches that occurred in Q4.
- Key Threats:
- Phishing and Social Engineering: Holiday-themed scams proliferate, with Black Friday-themed phishing rising by 692% and Christmas-themed phishing by 327% in 2024.
- Credential Abuse: Over 1.57 million login accounts tied to major e-commerce sites were collected from stealer logs in the three months leading up to the 2025 holiday season.
- E-commerce Vulnerabilities: Attackers actively exploit vulnerabilities in platforms like Adobe/Magento (CVE-2025-54236), Oracle E-Business Suite (CVE-2025-61882), and WooCommerce (CVE-2025-47569).
V. Organizational Response, Resilience, and Mitigation
Effective cybersecurity requires a proactive stance that integrates technology, robust processes, and a well-trained workforce.
Incident Response and Preparedness
A comprehensive Incident Response Plan (IRP) is critical, acknowledging that breaches are a matter of "when, not if."
- Key IRP Components: An IRP should outline procedures for detection, response, and recovery, with clear roles, responsibilities, and communication channels.
- Drills and Simulations: Regular tabletop exercises and drills are essential to test the plan and ensure staff familiarity.
- The Human Factor: On-call policies must be clearly defined, addressing response time expectations, compensation (per-call or minimum time), and the psychological toll (e.g., alert fatigue, PTSD from ringtones) to prevent burnout and maintain effectiveness.
Recommended Mitigation Strategies
Strategy | Description |
Enhance Employee Training | Regular, engaging security awareness training is crucial to mitigate insider risks and phishing. Educated employees are less likely to cause breaches. |
Implement Strict Access Controls | Enforce the principle of least privilege, granting access only to necessary resources. Conduct regular audits to prevent "privilege creep." |
Adopt a DevSecOps Approach | Integrating security into the development lifecycle is a top factor for reducing breach costs. |
Utilize Encryption | Strong encryption for data at rest and in motion is a key cost-mitigating factor and can render stolen data unusable. |
Deploy Application Whitelisting | Recommended by CISA, this practice only allows pre-approved programs to run on static systems like HMI computers, preventing many exploits. |
Invest in Security AI & Automation | Use GRC automation platforms and AI-driven tools for continuous monitoring, risk assessment, vendor management, and automated remediation. |
Conduct Year-End Maintenance | Before holiday periods, organizations should conduct a full IT audit: update all software and firmware, validate backups, disable inactive accounts, change default passwords, and review vendor SLAs. |
Organizational Investment Trends
- Post-Breach Spending: Only 49% of organizations planned to increase security spending after a breach in 2025, a notable drop from 63% in 2024.
- Recovery Times: While only 35% of organizations reported full recovery from a breach in 2025, this was a significant increase from 12% in 2024. However, of those who recovered, 76% needed more than 100 days.
VI. Predictions and Future Outlook for 2026
The cybersecurity landscape is projected to undergo significant transformation in 2026, driven primarily by the maturation and weaponization of AI.
AI-Centric Threats and Defenses
- Rise of Agentic AI Attacks: Autonomous AI agents will execute complex, multi-step attacks with minimal human intervention, becoming powerful independent threats.
- The AI "Insider" Threat: Trusted autonomous agents with privileged access will become a new class of insider threat, requiring specialized AI firewall governance to prevent their compromise and misuse.
- AI-Powered Social Engineering: Flawless deepfakes and hyper-personalized AI will make business email compromise and extortion scams nearly impossible for humans to detect.
- Data Poisoning: A new frontier of attack will involve invisibly corrupting the data used to train AI models, creating hidden backdoors and a "crisis of data trust."
Infrastructure and Security Paradigm Shifts
- Identity as the New Perimeter: With a forecasted 82:1 machine-to-human identity ratio, traditional network perimeters and VPNs will become obsolete. Securing every human, machine, and AI agent identity will be the primary defensive strategy.
- The Quantum Imperative: The "harvest now, decrypt later" threat, where adversaries steal encrypted data today to decrypt with future quantum computers, is shrinking the quantum timeline from a ten-year to a three-year problem. This will force a massive, complex migration to Post-Quantum Cryptography (PQC).
- The Browser as the Workspace: As the browser evolves into an agentic platform executing tasks, it becomes the new enterprise OS and the largest unsecured attack surface, forcing adoption of cloud-native models that enforce zero trust inside the browser.
Threat Actor and Organizational Evolution
- Convergence of APTs and Cybercrime: The line between nation-state actors and criminal gangs will blur as they share infrastructure and tactics, accelerating the scale and sophistication of global attacks.
- Executive Accountability for AI: The gap between rapid AI adoption and mature security will lead to the first major lawsuits holding executives personally liable for rogue AI actions, elevating AI risk to a critical board-level liability.
- Atrophy of Critical Thinking: Widespread GenAI use is predicted to cause a "surge of lazy thinking," leading 50% of organizations to implement "AI-free" skills assessments for hiring to ensure independent problem-solving abilities.





