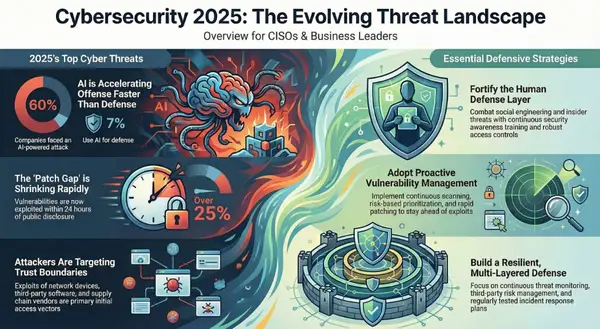
Decoding the 2025 Malware Landscape: A Technical Deep Dive
The cybersecurity landscape is in constant flux, demanding continuous adaptation and a deep understanding of emerging threats. ThreatDown's "2025 State of Malware" report offers crucial insights into the anticipated evolution of malware, highlighting significant shifts in attacker tactics and the increasing sophistication of their tools. This article delves into the key technical findings of the report, providing a detailed analysis of the challenges that lie ahead.
The Dawn of Agentic AI in Cybercrime
One of the most significant predictions in the report is the increasing impact of agentic Artificial Intelligence (AI) on cybercrime. While generative AI tools like ChatGPT have already been leveraged for tasks such as discovering vulnerabilities, writing malware, and setting up command and control infrastructure, the emergence of agentic AI promises a new level of automation and autonomy for threat actors.
Agentic AI is expected to arrive within the next few years, enabling AI agents to plan, act, reason, and use tools to achieve complex objectives with less human intervention. This has profound implications for cybersecurity, particularly in the hands of attackers. The report suggests that agentic AI could be used to scale up the number and speed of attacks, allowing well-funded ransomware gangs to target multiple victims simultaneously. Furthermore, malicious AI agents might be tasked with searching out and compromising vulnerable targets, running and fine-tuning malvertising campaigns, or determining the best method for breaching victims' systems.
The impact of AI extends beyond offensive capabilities. The report notes that AI is also being integrated into defensive technologies for malware detection, leveraging machine learning and zero-day analysis. ThreatDown's engine, for instance, employs numerous techniques powered by autonomous learning to detect various forms of malware, including ransomware, adware, and fileless attacks.
The Evolving Ransomware Landscape: Rise of the "Dark Horse"
Ransomware remains a critical threat, and the report highlights a significant shift in the landscape. While "big game" ransomware attacks targeting large organizations continue to be prevalent, 2024 saw the emergence of smaller, more agile ransomware groups, dubbed "dark horse" gangs. This "democratization" of ransomware is driven by the increasing availability of tools and tactics, lowering the barrier to entry for cybercriminals.
Historically, large ransomware operations dominated by offering ransomware-as-a-service (RaaS) to affiliates. However, the decline of major players like LockBit, partly due to law enforcement actions, has accelerated the rise of these smaller, less known entities. These "dark horse" groups often rely on similar tactics but operate with greater stealth, making them harder to track and attribute. In 2024, the top 10 most active ransomware groups accounted for only 37% of known attacks, indicating the growing significance of these smaller players.
Living Off The Land (LOTL) Tactics: Leveraging Legitimate Tools for Malicious Purposes
Cybercriminals are increasingly employing Living Off The Land (LOTL) tactics, utilizing legitimate software and administration tools already present in target environments to conduct their attacks. This approach allows them to blend in with normal system activity, making their malicious actions more difficult to detect.
The report identifies the top 5 most popular LOTL techniques detected by ThreatDown in 2024:
- Network service scanning: Attackers scan the internal network to identify open ports and potential vulnerabilities.
- Hosts file change: Modifying the hosts file allows attackers to redirect network traffic.
- Create local account: Creating new accounts can provide persistent access to compromised systems.
- PowerShell suspicious execution: Abusing PowerShell for malicious purposes is a common tactic due to its powerful administrative capabilities.
- Suspicious link execution: Tricking users into clicking malicious links remains a significant entry point.
Remote access tools like Windows Remote Desktop Protocol (RDP) and management and monitoring (RMM) software such as AnyDesk and ConnectWise are also frequently abused for initial access and persistence. The report highlights that RDP was the most common method of initial access in ransomware cases analyzed by ThreatDown in 2024, accounting for 58% of cases.
macOS Stealers: A Growing Threat on the Apple Ecosystem
While traditionally Windows has been the primary target for malware, the macOS threat landscape is evolving, with a notable increase in sophisticated information stealers. In 2024, the emergence of stealers like Atomic Stealer (AMOS) and Poseidon signifies a growing focus on the Mac platform by cybercriminals.
These macOS stealers are designed to steal sensitive information, including credit card details, authentication cookies, passwords, and cryptocurrency wallets. They often employ social engineering tricks to bypass macOS security features like Gatekeeper during installation. Poseidon, in particular, has quickly gained prominence since its launch, becoming the dominant stealer on macOS.
Android Phishing Malware: Targeting Mobile Devices
Android continues to be a significant target for phishing attacks, with malware designed to steal credentials and bypass two-factor authentication (2FA). Phishing campaigns targeting Android users are often highly scalable and adaptable, leveraging social engineering to trick users into installing malicious apps or providing their login information.
The report highlights that in 2024, ThreatDown detected 22,800 phishing-capable apps and 5,200 malicious apps containing code for reading OTPs from SMS messages. Criminals are increasingly using sophisticated techniques to overlay legitimate login screens, intercept SMS-based one-time passwords, and steal other sensitive data. The rise of 2FA theft underscores the need for more robust authentication methods and user awareness training.
Conclusion: Navigating the Evolving Threat Landscape
The ThreatDown 2025 State of Malware report paints a picture of an increasingly complex and automated threat landscape. The anticipated rise of agentic AI, the proliferation of "dark horse" ransomware groups, the sophisticated use of LOTL tactics, and the growing threats targeting macOS and Android platforms all demand a proactive and multi-layered security approach. Organizations must prioritize robust endpoint detection and response (EDR) solutions, implement strong security hygiene practices, and stay informed about the evolving tactics of cybercriminals to effectively defend against these emerging threats.