Discord Hit by Third-Party Customer Service Data Breach: Government IDs and User Data Exposed
Executive Summary
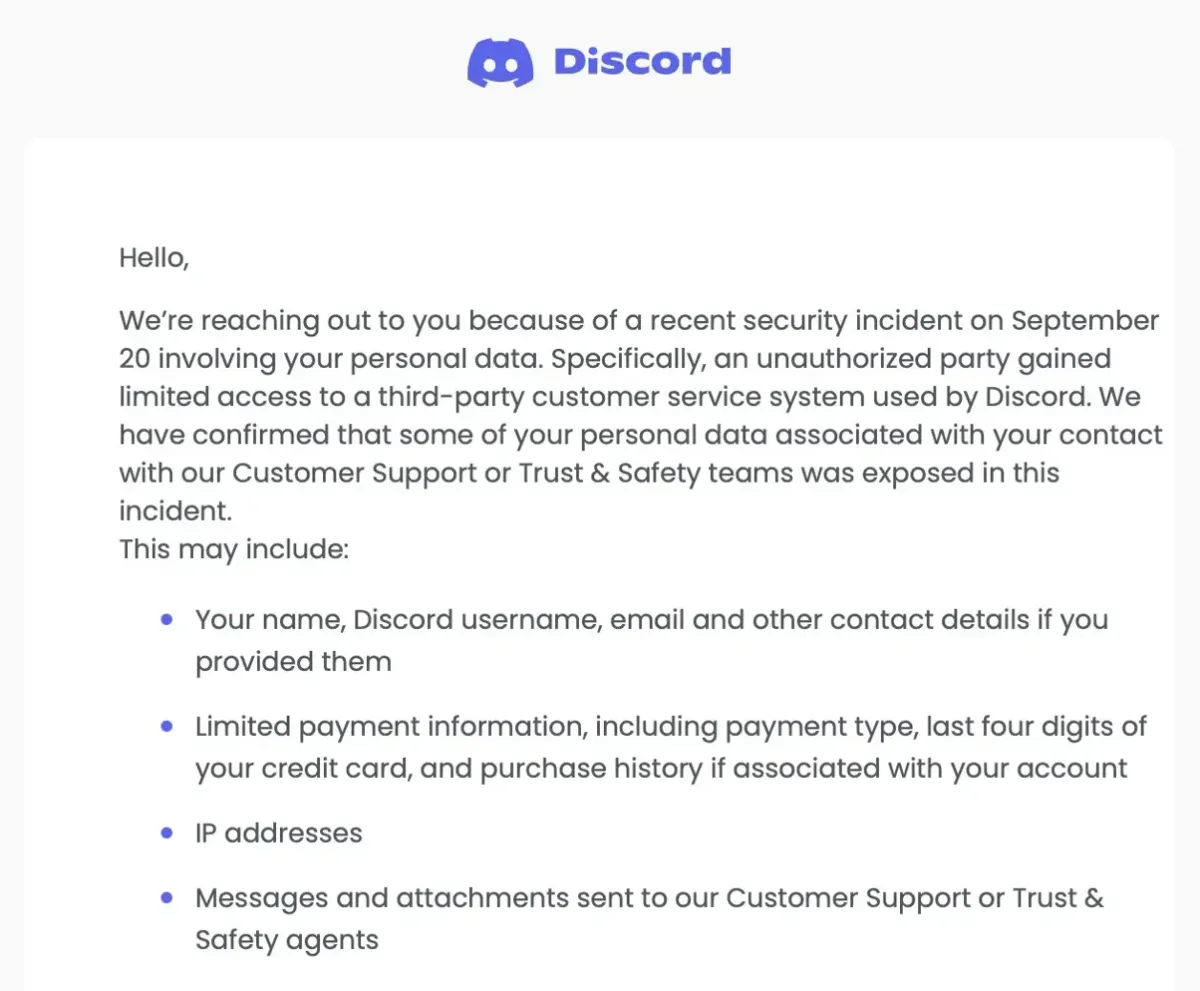
Discord has disclosed a significant security incident involving unauthorized access to user data through a compromised third-party customer service provider. The breach, which occurred on September 20, 2025, exposed sensitive personal information including government-issued IDs, billing details, and support communications for users who had contacted Discord's Customer Support or Trust & Safety teams. The attackers attempted to extort a financial ransom from Discord in exchange for not releasing the stolen data.
The Breach: What Happened
On September 20, 2025, cybercriminals successfully compromised one of Discord's third-party customer service providers, gaining unauthorized access to the company's support ticketing system. Discord discovered the incident shortly after and immediately took action to contain the breach.
The attack was financially motivated, with threat actors specifically targeting the customer service infrastructure to exfiltrate user data and leverage it for extortion purposes. Security researchers, including the VX-Underground group, noted that the compromised data represents "literally people's entire identity," highlighting the severity of the exposure.
Importantly, Discord itself was not directly breached. The attackers exploited vulnerabilities or credentials within the third-party vendor's systems to access Discord's customer support data.
Compromised Data
The breach impacted a limited number of Discord users who had previously interacted with the platform's Customer Support or Trust & Safety teams. The following types of data were potentially exposed:
Personal Information
- Full names
- Discord usernames
- Email addresses
- Contact details provided to support teams
- IP addresses
Financial Data
- Payment types
- Last four digits of credit card numbers
- Purchase history associated with accounts
Support Communications
- Complete messages and attachments sent to customer service agents
- Support ticket histories
Government-Issued IDs
A small number of users who had submitted government identification documents for age verification appeals had their scanned IDs exposed. This includes:
- Driver's licenses
- Passports
- Other state-issued identification documents
Internal Corporate Data
Limited internal Discord materials were also accessed, including:
- Training materials
- Internal presentations
What Was NOT Compromised
Discord confirmed that several critical categories of data remained secure:
- Full credit card numbers
- CVV security codes
- Passwords or authentication credentials
- User messages or activity on Discord outside of support interactions
- Physical addresses
Discord's Response
Upon discovering the breach, Discord took immediate action:
- Immediate Containment: Revoked the compromised provider's access to the ticketing system
- Investigation: Launched an internal investigation and engaged a leading computer forensics firm
- Law Enforcement: Contacted law enforcement agencies to investigate the attack
- User Notification: Began sending emails to affected users from [email protected]
- Regulatory Compliance: Notified relevant data protection authorities
- Security Review: Reviewed threat detection systems and security controls for third-party providers
The company emphasized that it will continue to frequently audit third-party systems to ensure they meet Discord's security and privacy standards.
The Broader Third-Party Risk Problem
This incident is part of a disturbing pattern of third-party vendor compromises affecting major platforms. Recent similar incidents include:
- ShinyHunters' Salesforce Campaign: The extortion group compromised hundreds of companies through stolen OAuth tokens, claiming to have stolen 1.5 billion Salesforce records from 760 companies
- Ongoing Supply Chain Attacks: Third-party customer service and support platforms have become prime targets for cybercriminals seeking access to user data across multiple organizations
The Discord breach highlights a critical vulnerability in modern digital ecosystems: companies are only as secure as their weakest third-party vendor.
The Age Verification Controversy
This breach has reignited debate over mandatory age verification requirements and government ID submission to online platforms. With Discord recently implementing stricter age verification measures in compliance with regulations like the UK's Online Safety Act, critics argue that this incident demonstrates the inherent risks of centralized ID databases.
Security experts have long warned that requiring platforms to collect and store government-issued identification creates attractive targets for cybercriminals. When these databases are compromised—whether through direct platform breaches or third-party vendor compromises—users face significant identity theft risks.
Implications for Affected Users
Users whose government IDs were exposed face elevated risks:
- Identity Theft: Compromised IDs can be used to open fraudulent accounts, apply for loans, or commit other identity-related crimes
- Synthetic Identity Fraud: Attackers can combine legitimate ID information with fabricated details to create synthetic identities
- Social Engineering: Detailed personal information enables sophisticated phishing and social engineering attacks
- Credential Stuffing: Email addresses and usernames can be used in automated attacks across multiple platforms
What Users Should Do
If you received a notification from Discord about this breach:
- Verify the Email: Ensure notifications come from [email protected]. Discord will NOT contact you by phone about this incident
- Monitor Financial Accounts: Watch for unauthorized transactions using the payment methods associated with your Discord account
- Enable MFA: Activate multi-factor authentication on Discord and other critical accounts
- Credit Monitoring: If your government ID was exposed, consider enrolling in credit monitoring services
- Fraud Alerts: Place fraud alerts with credit bureaus if your ID was compromised
- Stay Vigilant: Be alert for phishing attempts and social engineering attacks leveraging your exposed information
- Review Support Tickets: Consider what information you've shared with Discord support and assess your risk accordingly
Discord's Security Track Record
This breach is not Discord's first security challenge in 2025:
- July 2025: Threat actors impersonated Discord to distribute Epsilon Red ransomware
- August 2025: Malware campaign leveraged Discord's Content Delivery Network (CDN) for distribution
- September 2025: This third-party customer service provider breach
While these incidents demonstrate different attack vectors, they collectively highlight Discord's ongoing struggle to secure its vast ecosystem, which serves over 200 million monthly active users with a 90%+ market share in gaming communications.
Industry Perspective
Cybersecurity experts have weighed in on the significance of this breach. Alon Gal, Chief Technology Officer at threat intelligence firm Hudson Rock, noted that if the stolen Discord data is released publicly, it could provide crucial information for tracking cryptocurrency scammers and solving crypto-related hacks, as many scammers fail to use proper operational security when using Discord.
The incident also underscores the importance of vendor risk management and supply chain security assessments. Organizations must extend security audits beyond their own infrastructure to include rigorous evaluation of third-party vendors with access to sensitive data.
Recommendations for Platforms
This incident offers important lessons for digital platforms:
- Vendor Security Audits: Implement continuous security assessments of third-party providers, not just initial due diligence
- Data Minimization: Limit the amount of sensitive data shared with third-party vendors
- Access Controls: Implement strict least-privilege access controls for vendor systems
- Monitoring and Detection: Deploy robust threat detection systems that monitor third-party access patterns
- Incident Response Plans: Maintain clear protocols for vendor-related security incidents
- Contractual Obligations: Ensure vendor contracts include specific security requirements and breach notification timelines
- Alternative Solutions: Evaluate whether collecting government IDs is necessary or if alternative verification methods can reduce risk
Looking Forward
As of this publication, several key questions remain unanswered:
- The specific identity of the compromised third-party provider has not been disclosed
- The exact number of affected users has not been publicly confirmed
- The attack vector used to compromise the vendor remains unclear
- Whether the stolen data has been or will be released publicly is unknown
Discord states that its investigation is ongoing and that it continues to work with law enforcement to identify and prosecute those responsible.
Conclusion
The Discord third-party breach serves as a stark reminder that in our interconnected digital ecosystem, security is only as strong as the weakest link in the supply chain. For platforms handling hundreds of millions of users' data, the compromise of a single vendor can expose sensitive information at scale.
As regulatory requirements increasingly mandate age verification and identity confirmation, platforms must carefully weigh the security implications of collecting and storing government-issued IDs. This incident demonstrates that even when platforms don't directly suffer breaches, their reliance on third-party infrastructure creates significant risk exposure.
Users should remain vigilant, monitor their accounts for suspicious activity, and think carefully about what information they share with customer support teams. In the age of sophisticated cyber threats, every piece of personal information shared online represents a potential vulnerability.
About This Breach
- Date of Incident: September 20, 2025
- Date of Discovery: Late September 2025
- Date of Public Disclosure: October 3, 2025
- Attack Type: Third-party vendor compromise, extortion attempt
- Affected Platform: Discord (via customer service provider)
- Users Impacted: Limited number who contacted Customer Support/Trust & Safety
- Data Types: PII, government IDs, billing info, support communications
- Ransom Demanded: Yes (amount undisclosed)
- Data Released: Not confirmed at time of publication
Sources: Discord official press release, BleepingComputer, Tom's Hardware, Engadget, PC Gamer, CyberInsider, HackRead, VX-Underground
This article will be updated as new information becomes available about the Discord data breach.





