DoorDash Data Breach Exposes Customer Information After Employee Falls for Social Engineering Attack
Just in: DoorDash breached…
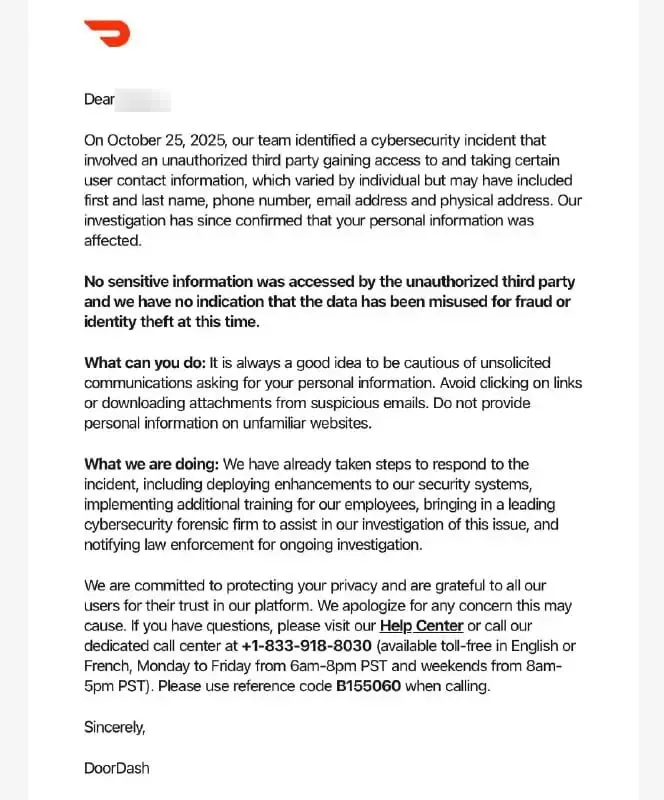
On November 13, 2025, DoorDash began notifying users of a security incident that occurred on October 25, 2025, involving "an unauthorized third party gaining access to and taking certain user contact information." According to the company's disclosure, the compromised data "may have included first and last name, phone number, email address and physical address."
But here's the puzzling contradiction that has cybersecurity experts raising eyebrows: In the same notification, DoorDash insisted that "No sensitive information was accessed."
This marks the third major security incident for the food delivery giant, raising serious questions about the company's security culture, employee training, and why a multi-billion-dollar platform continues to fall victim to social engineering attacks that security professionals have been warning about for years.
The Breach: What We Know
Timeline of Events
- October 25, 2025: Unauthorized access detected; breach occurs
- October 25, 2025: DoorDash's incident response team shuts down unauthorized access
- November 13, 2025: DoorDash begins sending breach notification emails to affected users
- November 14-15, 2025: News of the breach becomes public through cybersecurity media
How It Happened: Social Engineering Strikes Again
The breach was caused by a DoorDash employee falling victim to a social engineering scam. The compromised employee unwittingly provided credentials that allowed unauthorized access to customer data repositories.
While DoorDash has not disclosed the specific social engineering technique used, common methods employed against corporate employees include:
- Phishing emails impersonating IT support or management
- Vishing (voice phishing) where attackers call employees pretending to be tech support
- SMS phishing (smishing) with urgent requests to verify credentials
- Business email compromise (BEC) mimicking executives or vendors
- Credential harvesting through fake login portals
This attack method is particularly concerning because it exploits the human element—the weakest link in any cybersecurity defense. No matter how sophisticated a company's technical security controls are, a single employee falling for a convincing scam can compromise the entire system.
What Data Was Exposed
According to DoorDash's notification, the breach affected a mix of consumers, Dashers (delivery drivers), and merchants. The exposed information varied by individual but may have included:
- First and last names
- Phone numbers
- Email addresses
- Physical addresses (delivery/billing addresses)
What Was NOT Exposed (According to DoorDash)
DoorDash emphasized that the following information was not accessed in the breach:
- Social Security numbers
- Government-issued identification numbers
- Driver's license information
- Bank account information
- Payment card information (credit/debit card numbers)
- Passwords
The "No Sensitive Information" Contradiction
DoorDash's claim that "no sensitive information was accessed" deserves scrutiny. While the company correctly notes that financial data and government IDs were not compromised, names, phone numbers, email addresses, and physical addresses are absolutely sensitive information.
Why This Data Matters
This combination of personal information is exactly what criminals need for:
1. Targeted Phishing Attacks
With names, phone numbers, and email addresses, scammers can craft highly convincing phishing messages that appear to come from DoorDash or related services. These messages can reference your actual delivery history or account details to appear legitimate.
2. Identity Theft Foundation
While this data alone may not enable full identity theft, it provides critical building blocks that, when combined with data from other breaches, can be used to impersonate victims.
3. SIM Swapping Attacks
Phone numbers combined with personal information can be used in SIM swapping attacks, where criminals convince mobile carriers to transfer your phone number to a SIM card they control, enabling them to bypass two-factor authentication.
4. Physical Security Risks
Physical addresses combined with names can enable:
- Targeted burglary (knowing when residents are likely away based on delivery patterns)
- Mail theft
- Physical stalking
- "Brushing" scams where unwanted packages are sent
5. Spear Phishing and Social Engineering
Attackers can use this information to target individuals with personalized scams, including:
- Fake delivery notifications
- Account verification requests
- "Refund" scams
- Credit card fraud attempts
6. Database Enrichment
Cybercriminals maintain massive databases of personal information compiled from multiple breaches. This DoorDash data enriches those databases, making future attacks against victims more effective.
The reality: There's no such thing as "non-sensitive" personal information in the hands of criminals. DoorDash's characterization minimizes the real risk to affected users.
How Many Users Were Affected?
DoorDash has not disclosed the total number of affected users. The company only stated that notifications were sent to those impacted by the incident.
Based on reports from affected users, DoorDash Canada customers appear to have been the primary recipients of breach notification emails, though the company's undated security advisory suggests the incident may extend beyond Canada.
DoorDash's Scale Makes This Significant
To understand the potential scope:
- DoorDash operates in over 7,000 cities across the United States, Canada, Australia, Japan, and several European countries
- The company serves millions of active users
- Even a "limited" breach at DoorDash's scale could affect hundreds of thousands or millions of people
The lack of transparency about the number of affected users is troubling and prevents individuals from understanding the true scope of the risk.
DoorDash's Response
Upon discovering the breach on October 25, 2025, DoorDash says it took the following actions:
Immediate Response
- Shut down unauthorized access to the compromised systems
- Launched an internal investigation with the incident response team
- Referred the matter to law enforcement for criminal investigation
User Notification
- Began sending emails on November 13, 2025 (19 days after discovery)
- Posted a security advisory on the DoorDash website (undated)
- Provided recommendations for affected users
DoorDash's Recommended Actions for Affected Users
DoorDash advised affected individuals to:
- Be vigilant for phishing attempts via email, phone, or text claiming to be from DoorDash
- Never provide personal information in response to unsolicited communications
- Monitor financial accounts for suspicious activity
- Be cautious of communications that create urgency or request immediate action
DoorDash's Troubling Security History
This October 2025 breach is not DoorDash's first security incident. In fact, it's the third notable breach for the food delivery platform, revealing a pattern of security vulnerabilities that should concern every user.
2019: The Big One
In 2019, DoorDash suffered a massive data breach that exposed information of approximately 4.9 million customers, Dashers (delivery drivers), and merchants.
That breach, which occurred in May 2019 but wasn't disclosed until September 2019, compromised:
- Names
- Email addresses
- Delivery addresses
- Order histories
- Phone numbers
- Hashed, salted passwords (for users who created accounts before April 5, 2018)
- Last four digits of payment cards (for some Dashers and merchants)
- Bank account numbers (for some Dashers and merchants)
DoorDash claimed the breach was discovered during routine security monitoring and affected data from the period on or before April 5, 2018.
Previous Security Concerns
Beyond confirmed breaches, DoorDash has faced scrutiny for:
- Third-party vendor security risks (highlighted in previous incidents)
- Driver background check controversies raising questions about security vetting
- App security vulnerabilities reported by researchers
The Pattern: Social Engineering as a Persistent Threat
The 2025 breach's root cause—an employee falling for social engineering—is particularly concerning because:
- This attack vector has been known for decades yet continues to succeed
- DoorDash has experienced breaches before and should have enhanced training
- The food delivery industry is a known target for these attacks
- Competitors have faced similar incidents, providing lessons DoorDash should have learned
Why Food Delivery Platforms Are Prime Targets
DoorDash is far from the only food delivery platform to suffer breaches, but the industry's characteristics make it particularly attractive to attackers:
Rich Data Repositories
Food delivery platforms possess:
- Personal information: Names, addresses, phone numbers
- Financial data: Payment card information, transaction histories
- Behavioral data: Eating habits, ordering patterns, location data
- Business information: Restaurant partnerships, merchant data
High-Value Targets
- Large user bases: Millions of active customers
- Frequent transactions: Regular payment processing
- Mobile-first design: Potential app vulnerabilities
- Third-party integrations: Restaurants, drivers, payment processors create expanded attack surface
Operational Complexity
- Gig economy workforce: Thousands of drivers with varying security awareness
- Restaurant partnerships: Multiple business connections increase risk
- Real-time operations: Pressure to maintain service can compromise security decisions
The Social Engineering Problem: Why Employees Keep Falling For It
Social engineering attacks succeed because they exploit fundamental human psychology, not technical vulnerabilities. Understanding why these attacks work is crucial to preventing them.
The Psychological Triggers
Attackers exploit:
1. Authority: Impersonating bosses, IT support, or executives
2. Urgency: Creating artificial time pressure ("Your account will be locked in 30 minutes")
3. Fear: Threatening consequences ("Your system is compromised")
4. Trust: Leveraging familiarity with brands or internal processes
5. Helpfulness: Exploiting employees' desire to be cooperative and solve problems
Why Corporate Training Often Fails
Despite widespread security awareness training, employees continue to fall victim because:
- Training is too infrequent (annual sessions don't create lasting habits)
- Simulated phishing is too obvious (doesn't prepare for sophisticated attacks)
- No consequences for failures (or penalties that discourage reporting)
- Lack of real-world context (generic training doesn't address specific threats)
- Conflicting priorities (productivity pressures override security caution)
The Human Firewall Needs Constant Maintenance
Security experts emphasize that preventing social engineering requires:
- Continuous training with realistic, evolving scenarios
- Cultural change that prioritizes security without punishment
- Technical controls that reduce reliance on human judgment (e.g., phishing-resistant MFA)
- Clear escalation procedures so employees know how to verify suspicious requests
- Regular testing with sophisticated simulations
- Leadership commitment demonstrating that security is everyone's responsibility
What This Means for the Gig Economy
DoorDash's breach highlights broader security challenges facing gig economy platforms:
Distributed Workforce Vulnerabilities
- Dashers (delivery drivers) use personal devices that may lack enterprise security
- Variable security awareness among thousands of independent contractors
- High turnover makes consistent training difficult
- Access to customer data creates multiple potential compromise points
The Third-Party Risk
Modern platforms rely on extensive third-party integrations:
- Payment processors
- Mapping and routing services
- Restaurant POS systems
- Cloud infrastructure providers
- Marketing and analytics tools
Each integration represents a potential vulnerability, and securing them requires:
- Vendor security assessments
- Limited data access
- Continuous monitoring
- Incident response coordination
Regulatory Implications
The gig economy's security challenges are attracting regulatory attention:
- Data protection laws (GDPR, CCPA, etc.) impose strict breach notification requirements
- Labor regulations may increasingly address gig worker data protection
- Consumer protection agencies are scrutinizing how platforms safeguard user data
Immediate Actions for DoorDash Users
If you received a breach notification from DoorDash, or if you're a DoorDash user concerned about this incident, take these steps immediately:
1. Assume Your Information Is Compromised
Even if you didn't receive a notification, the lack of transparency about affected user numbers means you should assume risk if you've used DoorDash.
2. Watch for DoorDash-Themed Phishing
Expect an increase in phishing attempts that:
- Reference your DoorDash account or orders
- Claim there's a problem with a delivery
- Offer refunds or credits
- Request account verification
- Ask you to update payment information
Remember: DoorDash will never ask for your password, payment information, or Social Security number via email, text, or unsolicited phone calls.
3. Enable Two-Factor Authentication (2FA)
If you haven't already:
- Enable 2FA on your DoorDash account
- Use an authenticator app (Google Authenticator, Authy) rather than SMS if possible
- Enable 2FA on your email account (critical for account recovery)
4. Review Your Account Activity
Log into your DoorDash account and:
- Check your order history for unauthorized orders
- Review delivery addresses on file
- Verify payment methods listed
- Check for any account changes you didn't make
5. Monitor Financial Accounts
While DoorDash says payment information wasn't accessed:
- Review credit/debit card statements for DoorDash charges you don't recognize
- Set up transaction alerts with your bank
- Watch for small "test" charges that precede larger fraud
6. Update Your Password
Even though DoorDash says passwords weren't compromised:
- Change your DoorDash password to a strong, unique password
- Use a password manager to generate and store complex passwords
- Never reuse passwords across multiple accounts
7. Beware of Phone Scams
Your exposed phone number could be used for:
- Vishing (voice phishing) attempts
- Smishing (SMS phishing) messages
- SIM swapping attacks
Action: Contact your mobile carrier about adding additional security measures to prevent unauthorized SIM changes.
8. Protect Your Physical Address
Be cautious of:
- Unexpected packages (brushing scams)
- Requests for package re-delivery requiring payment
- QR codes attached to unexpected deliveries
9. Consider Freezing Your Credit
If you're concerned about identity theft:
- Place a credit freeze with Equifax, Experian, and TransUnion
- Credit freezes are free and prevent new accounts from being opened in your name
- You can temporarily lift the freeze when you need to apply for credit
10. Document Everything
- Save the breach notification email from DoorDash
- Take screenshots of any suspicious communications
- Keep records of any fraudulent charges or identity theft attempts
- This documentation may be valuable if you need to dispute charges or file complaints
Long-Term Protective Measures
Beyond immediate actions, consider these ongoing security practices:
Email Security
- Use a dedicated email address for food delivery services (separate from banking/critical accounts)
- Enable advanced spam filtering
- Never click links in unsolicited emails—go directly to the website
Phone Number Protection
- Consider using a Google Voice or similar secondary number for delivery services
- This creates a buffer between your primary contact number and service accounts
Payment Security
- Use virtual credit card numbers (offered by many card issuers)
- Consider using privacy-focused services like Privacy.com for online transactions
- Set low spending limits on virtual cards used for delivery services
Privacy Practices
- Minimize the personal information you provide to delivery services
- Use delivery instructions that don't reveal security vulnerabilities (e.g., "Leave at door" rather than "No one home until 6pm")
- Regularly review and delete old addresses from your account
Questions DoorDash Needs to Answer
The company's disclosure leaves many critical questions unanswered:
Transparency Gaps
- How many users were actually affected? The lack of a specific number raises concerns about the scope.
- What specific social engineering technique was used? Knowing this could help prevent future incidents.
- Why did it take 19 days to notify users? The breach occurred October 25, but notifications didn't begin until November 13.
- What security measures failed? What allowed an employee's compromised credentials to access customer databases?
- What additional security measures have been implemented? What's being done to prevent recurrence?
- Were any third-party vendors involved? Was the compromised employee a direct DoorDash employee or a contractor?
- Has the data appeared on dark web forums? Is there evidence of the stolen data being sold or distributed?
- Were international users affected? The breach appears to have primarily impacted Canadian users, but was this limited to one region?
- What employee training improvements are being made? What's changing to address the social engineering vulnerability?
- Will affected users receive any compensation or credit monitoring? Many companies offer these services following breaches.
The Broader Implications
The DoorDash breach represents more than just another data exposure—it's a symptom of larger cybersecurity challenges facing the digital economy.
The Social Engineering Epidemic
According to recent cybersecurity research:
- 90% of data breaches involve some form of social engineering
- Phishing attacks increased 61% year-over-year in 2024
- Business email compromise (BEC) cost organizations over $2.9 billion in 2024
- AI-powered phishing is making attacks more sophisticated and harder to detect
The human element remains the weakest link, and as DoorDash's breach demonstrates, even major corporations with substantial security budgets remain vulnerable.
The Third-Party Ecosystem Risk
Modern digital platforms rely on complex ecosystems of:
- Cloud providers
- Payment processors
- Analytics services
- Marketing platforms
- Customer relationship management tools
Each integration represents a potential attack vector. Security is only as strong as the weakest link in this chain.
Consumer Data: Everyone's Responsibility
The DoorDash breach underscores that protecting personal information requires vigilance from both companies and consumers:
Companies must:
- Invest in continuous security training
- Implement defense-in-depth strategies
- Conduct regular security assessments
- Maintain transparency about incidents
- Face meaningful consequences for security failures
Consumers must:
- Practice good password hygiene
- Enable multi-factor authentication
- Remain skeptical of unsolicited communications
- Monitor accounts regularly
- Understand that convenience often comes with privacy trade-offs
Regulatory and Legal Considerations
DoorDash's breach may trigger various regulatory and legal consequences:
Data Protection Compliance
The breach likely triggers notification requirements under:
- Personal Information Protection and Electronic Documents Act (PIPEDA) in Canada
- California Consumer Privacy Act (CCPA) for California users
- Various state breach notification laws across the US
- General Data Protection Regulation (GDPR) if any EU citizens were affected
Potential Regulatory Actions
Regulators may investigate:
- Whether DoorDash's security measures were adequate
- Whether notification timing complied with legal requirements
- Whether the company minimized data collection as required
- What steps are being taken to prevent recurrence
Class Action Lawsuits
DoorDash may face class action litigation, as is common following data breaches. Previous food delivery breaches have resulted in settlements, though these often provide minimal compensation to individual class members.
FTC Scrutiny
The Federal Trade Commission has increased enforcement of data security requirements. Companies found to have inadequate security practices may face:
- Consent decrees requiring security improvements
- Regular security audits for 20 years
- Potential civil penalties
What Other Food Delivery Platforms Can Learn
DoorDash competitors like Uber Eats, Grubhub, Postmates, and Instacart should treat this breach as a warning and opportunity:
Security Best Practices
- Implement phishing-resistant multi-factor authentication (e.g., FIDO2 security keys) for employees
- Conduct continuous security awareness training with realistic simulations
- Limit access to customer data based on the principle of least privilege
- Deploy endpoint detection and response (EDR) solutions on all corporate devices
- Establish clear verification procedures for sensitive requests
- Create a security-first culture where reporting suspicious activity is rewarded, not punished
Technical Controls
- Zero-trust architecture that assumes no user or system is trusted by default
- Data loss prevention (DLP) tools to detect unusual data access patterns
- Behavioral analytics to identify compromised accounts
- Network segmentation to limit lateral movement if credentials are compromised
- Immutable audit logs to track all access to sensitive data
Vendor Management
- Regular security assessments of all third-party vendors
- Contractual security requirements with meaningful penalties
- Limited data sharing to only what's absolutely necessary
- Continuous monitoring of vendor security posture
The Future of Food Delivery Security
As the food delivery industry continues to grow, security must evolve to match:
Emerging Threats
AI-Powered Social Engineering: Deepfake audio and video will make impersonation attacks even more convincing.
Supply Chain Attacks: Targeting restaurant POS systems and other integration points.
Ransomware: Attacks that encrypt operational systems, disrupting service and demanding payment.
IoT Vulnerabilities: As delivery services experiment with drones and autonomous vehicles, new attack surfaces emerge.
Security Innovations
Biometric Authentication: Fingerprint or facial recognition for high-value transactions.
Blockchain for Data Integrity: Immutable records of data access and modifications.
AI-Powered Threat Detection: Machine learning to identify anomalous behavior patterns.
Privacy-Preserving Technologies: Homomorphic encryption and other techniques that allow data processing without exposing raw information.
Regulatory Evolution
Expect increased regulation of data security practices:
- Mandatory security standards for food delivery platforms
- Breach notification requirements with stricter timelines
- Potential liability frameworks holding companies accountable
- International data protection cooperation
Conclusion: A Wake-Up Call for the Industry
The November 2025 DoorDash data breach serves as yet another reminder that security is not a solved problem—it's an ongoing challenge requiring constant vigilance, investment, and cultural commitment.
For DoorDash, this third security incident raises serious questions about whether the company has learned from past failures. Social engineering attacks are preventable with proper training, technical controls, and security culture, yet DoorDash employees continue to fall victim.
For users, this breach underscores the importance of defensive digital hygiene: unique passwords, multi-factor authentication, healthy skepticism about unsolicited communications, and regular monitoring of accounts.
For the industry, it's a call to action. Food delivery platforms handle massive amounts of personal, financial, and behavioral data. With that privilege comes responsibility—a responsibility that requires more than reassuring press releases claiming "no sensitive information was accessed" when names, addresses, phone numbers, and email addresses clearly are sensitive.
The question isn't whether there will be another breach—history suggests there will be. The question is whether companies like DoorDash will invest in the people, processes, and technology needed to minimize that risk and protect the millions of users who trust them with their personal information.
For DoorDash users, the message is clear: Stay vigilant, protect your information, and remember that the only data truly safe from a breach is data you never provided in the first place.
Key Takeaways
✅ DoorDash suffered a data breach on October 25, 2025, disclosed November 13, 2025
✅ Caused by an employee falling for social engineering, providing credentials to attackers
✅ Exposed names, phone numbers, email addresses, and physical addresses for customers, Dashers, and merchants
✅ Third major security incident for DoorDash (previous breach in 2019 affected 4.9 million users)
✅ Number of affected users not disclosed, raising transparency concerns
✅ DoorDash's claim of "no sensitive information" is misleading—exposed data enables phishing, identity theft building blocks, and other attacks
✅ Social engineering remains the #1 cause of data breaches across industries
✅ Users should enable 2FA, change passwords, and watch for phishing attempts
✅ Food delivery platforms are prime targets due to rich data repositories and operational complexity
✅ The gig economy model creates unique security challenges with distributed workforces and third-party integrations
Stay informed about the latest data breaches and cybersecurity threats. Follow Breached for breaking news, analysis, and practical security guidance.
Have you received a DoorDash breach notification? Share your experience and any suspicious activity you've noticed in the comments below.