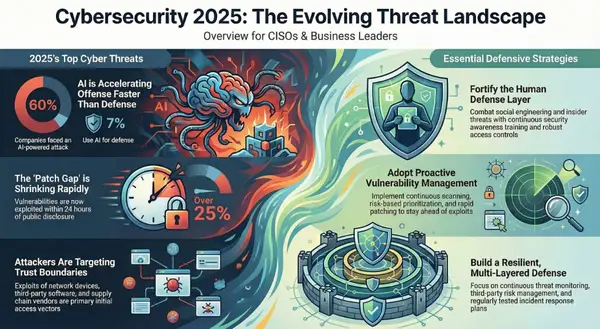
Europe Cyber Threat Briefing: November 2025 Analysis
Executive Summary
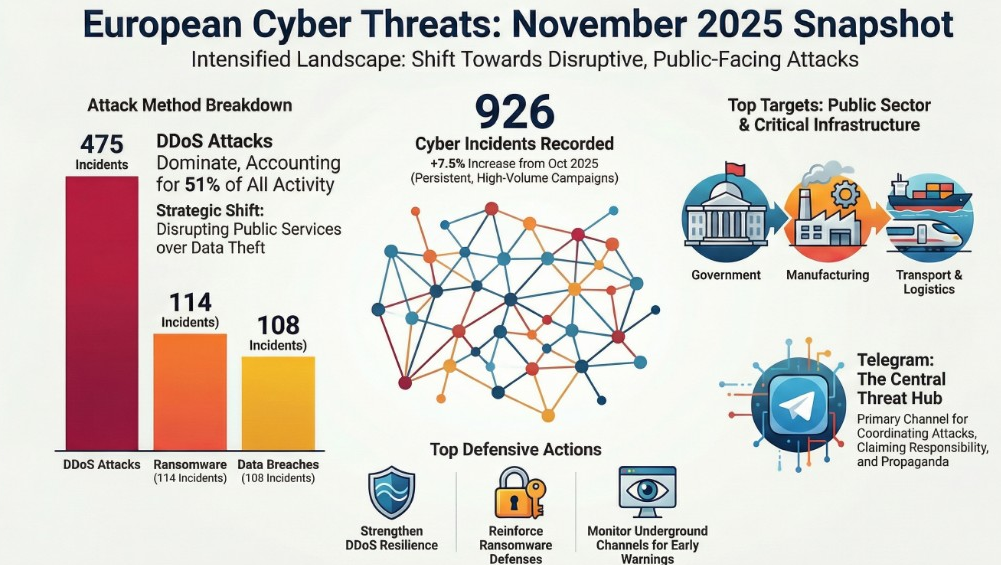
In November 2025, Europe's cybersecurity landscape underwent a significant tactical shift, moving from clandestine breaches toward overt, sustained disruption. The region recorded 926 cyber incidents, a 7.5% increase from the 861 incidents in October. This escalation was not a series of isolated events but a persistent, high-volume campaign characterized by a strategic preference for visibility and interruption of public services.
Distributed Denial of Service (DDoS) attacks were the dominant threat vector, accounting for over 51% of all activity. This highlights a coordinated effort by threat actors to disrupt public-facing systems. Concurrently, a robust cybercriminal economy continued to operate at scale, with significant activity in ransomware, data breaches, and the sale of initial network access. This establishes a hybrid threat model where hacktivist pressure and criminal monetization work in parallel.
Government bodies, critical infrastructure, and transport-linked organizations were the primary targets, absorbing the heaviest pressure. Geographically, Spain and Denmark experienced particularly elevated activity, while Ukraine remained a focus of sustained geopolitical targeting. The communication platform Telegram has been confirmed as the central command-and-control and propaganda channel for threat actors operating against European targets.
Detailed Analysis of the Threat Landscape
Incident Volume and Trends
The month-over-month increase in cyber incidents points to an active and extended campaign rather than a temporary or reactive spike. The pressure was consistently applied across the month.
- October 2025 Incidents: 861
- November 2025 Incidents: 926
- Month-over-Month Growth: 7.5%
The primary drivers behind this sustained activity include:
- Escalated DDoS Campaigns: Coordinated attacks focused on government and transport systems.
- Steady Ransomware Operations: Consistent extortion activity without dramatic peaks.
- Persistent Access Brokerage: Ongoing sale of network access and data exposure, fueling future attacks.
Category-Wise Threat Landscape
The threat profile for November 2025 was defined by a clear strategic focus on service disruption, complemented by a strong undercurrent of data extortion and theft. DDoS attacks alone constituted more than half of all recorded incidents.
Threat Category | Incident Count | Percentage of Total |
DDoS Attacks | 475 | 51.3% |
Ransomware | 114 | 12.3% |
Data Breaches | 108 | 11.7% |
Initial Access Listings | 87 | 9.4% |
Data Leaks | 67 | 7.2% |
Defacement | 47 | 5.1% |
Cyber Attack Alerts | 28 | 3.0% |
Geographic Distribution of Attacks
Campaigns were concentrated in Southern and Western Europe, though activity was recorded across the continent. The data indicates focused disruption campaigns against specific nations, alongside continued geopolitical targeting.
Country | Incident Count |
Spain | 155 |
Denmark | 119 |
Ukraine | 103 |
France | 78 |
Belgium | 77 |
United Kingdom | 70 |
Italy | 67 |
Germany | 50 |
Sweden | 39 |
Romania | 29 |
Additional significant activity was noted in Switzerland (21), Poland (20), Austria (18), the Netherlands (17), Finland (10), Greece (9), and Portugal (7).
Sector-Specific Impact
Threat actors employed a dual targeting strategy, tailoring their attacks based on the victim's sector. Public-facing and critical infrastructure sectors were targeted for disruption, while sectors vulnerable to operational downtime were targeted for extortion.
Industry | Incident Count |
Government & Public Sector | 242 |
Manufacturing & Industrial | 100 |
Transport & Logistics | 94 |
Technology & IT Services | 82 |
Telecom | 39 |
Consumer Services & Goods | 37 |
Financial Services | 37 |
Energy & Utilities | 29 |
Building & Construction | 28 |
Business & Professional Services | 25 |
Education | 25 |
Other affected industries included Media, Arts, & Entertainment (19), Wholesale & Retail (15), Healthcare (13), Social Organization (12), and Science and Research (5).
Deep Dive into Criminal Ecosystems
Underground Platform Activity
The coordination, amplification, and monetization of attacks were overwhelmingly routed through specific underground platforms, with Telegram emerging as the primary hub.
- Telegram's Role: The report identifies Telegram as the "central nervous system" for threat actor operations, used for coordinating attacks, claiming responsibility, and disseminating propaganda.
- Monetization Platforms: Data Leak Sites (DLS) were used to sustain extortion pressure from ransomware attacks, while Dark Forums and Exploit Forums served as marketplaces for access sales and vulnerability trading.
Platform Type | Incident Count |
Telegram | 568 |
Data Leak Sites | 123 |
Dark Forums | 105 |
Exploit Forums | 51 |
LeakBase | 32 |
Defacer ID | 22 |
Ransomware Landscape
The ransomware ecosystem in Europe remains highly fragmented and competitive, driven by numerous affiliate-based groups rather than a single dominant actor.
Most Active Ransomware Groups:
- Qilin: 26 incidents
- INC RANSOM: 14 incidents
- CL0P: 10 incidents
- Warlock: 8 incidents
- RansomHouse: 6 incidents
- Payouts King: 5 incidents
- Mid-Tier Groups: Benzona, DragonForce, Everest, and Nova each recorded 4 incidents.
Top Ransomware-Affected Countries:
- United Kingdom: 17 incidents
- Germany: 14 incidents
- Italy: 12 incidents
- Spain: 12 incidents
- Austria: 10 incidents
- Switzerland: 10 incidents
Top Ransomware-Affected Industries: Attackers continued to favor industries where "downtime equals leverage."
- Manufacturing & Industrial: 31 incidents
- Building & Construction: 16 incidents
- Business & Professional Services: 14 incidents
- Consumer Services & Goods: 9 incidents
- Transport & Logistics: 6 incidents
Key Observations and Strategic Recommendations
Summary of Key Observations
- DDoS Dominance: DDoS attacks represented over 50% of all recorded incidents, signaling a strategic focus on disruption.
- Targeted Pressure: Government and transport sectors faced sustained and coordinated campaigns.
- Decentralized Ransomware: The ransomware threat remains active and potent but is spread across a fragmented landscape of operators.
- Telegram as Operational Hub: The platform has become the primary channel for threat actor coordination and communication.
- Access Brokerage: The sale of initial network access continues to be a critical enabler for downstream attacks like ransomware.
Actionable Recommendations
- Strengthen DDoS Resilience: Implement and refine defenses through scrubbing services, Web Application Firewall (WAF) tuning, and coordination with Internet Service Providers (ISPs).
- Prioritize Critical Infrastructure Protection: Focus defensive resources on government, transport, energy, and telecom systems.
- Reinforce Ransomware Defenses: Ensure robust, immutable backups and deploy advanced Endpoint Detection and Response (EDR) solutions.
- Monitor the Underground: Establish real-time monitoring of Telegram, Data Leak Sites, and Exploit Forums to gain early warnings of impending attacks.
- Apply Sector-Specific Controls: Develop and implement security controls tailored to the unique risks faced by high-target industries like manufacturing and logistics.
Conclusion
The cyber threat landscape in Europe during November 2025 is defined by a blended model where sustained, disruptive campaigns are supported by parallel criminal operations for monetization. The combination of DDoS attacks, ransomware extortion, and access brokerage creates multifaceted pressure on public trust, economic stability, and national resilience. In this environment, a reactive security posture is insufficient. The report concludes that only proactive, intelligence-driven defense, grounded in deep visibility of the cyber underground and tailored with sector-specific readiness, can effectively counter this escalating and evolving threat.