Federal Grand Jury Indicts 54 in Massive $40.7M ATM Jackpotting Scheme Linked to Venezuelan Terror Group
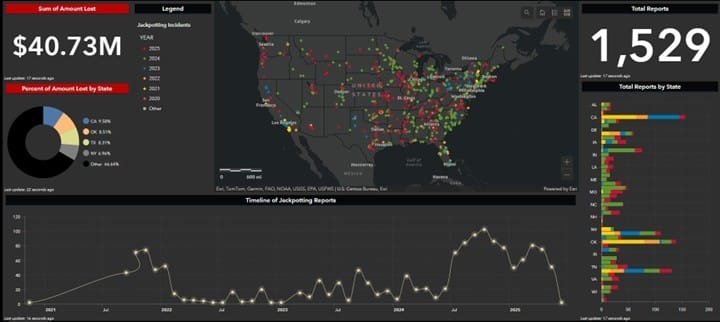
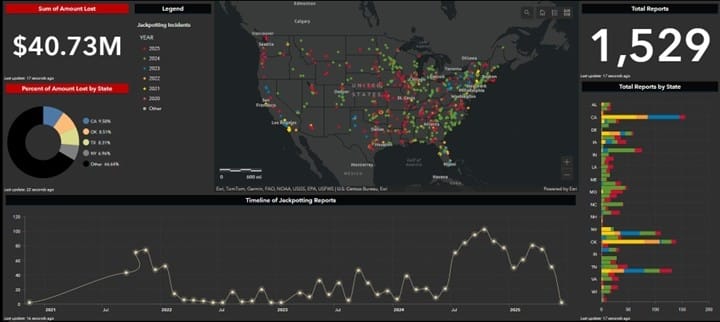
December 19, 2025 - In one of the most significant financial cybercrime cases to date, federal prosecutors have charged 54 individuals connected to Tren de Aragua (TdA), a designated foreign terrorist organization, with orchestrating a sophisticated nationwide ATM jackpotting operation that netted over $40.73 million as of August 2025.
The Indictments: A Two-Pronged Legal Assault
The U.S. Attorney's Office for the District of Nebraska announced two sweeping indictments:
December 9, 2025 Indictment:
- 22 defendants charged
- Charges include conspiracy to provide material support to terrorists, bank fraud, bank burglary, computer fraud, and money laundering
- Alleges TdA used jackpotting proceeds to fund terrorist activities
October 21, 2025 Indictment:
- 32 defendants charged
- 56 total counts including bank fraud, bank burglary, and computer damage
- Faces maximum sentences ranging from 20 to 335 years imprisonment

High-Profile Defendants and International Connections
Among those indicted is Jimena Romina Araya Navarro, also known as "Rosita," a Venezuelan entertainer and alleged TdA leader who was previously sanctioned by the U.S. Department of Treasury's Office of Foreign Assets Control (OFAC). According to Treasury documents, Araya Navarro allegedly helped TdA leader Hector Rusthenford Guerrero Flores (known as "Niño Guerrero") escape from Venezuela's Tocorón prison in 2012 and has been photographed at social events with him.
The indictment also names Anibal Alexander Canelon Aguirre, alias "Prometheus," believed to be the malware engineer behind the operation. Aguirre is currently assessed to be in Venezuela.
The Technical Operation: Ploutus Malware Deployment
The conspiracy relied on a sophisticated variant of Ploutus malware, one of the most advanced ATM malware families discovered. First identified in Mexico in 2013, Ploutus has evolved through multiple iterations and can now run on machines from 41 different ATM vendors across 80 countries.
The Attack Methodology
According to court documents, the operation followed a methodical three-phase approach:
Phase 1: Reconnaissance
- Criminal teams traveled in groups using multiple vehicles
- Conducted surveillance of targeted banks and credit unions
- Documented external security features
- Tested alarm systems by opening ATM hoods and monitoring for law enforcement response
Phase 2: Malware Installation Attackers deployed Ploutus through three primary methods:
- Hard drive replacement - Removing the existing drive and installing one pre-loaded with malware
- Direct installation - Removing the hard drive, installing malware directly, and reinstalling
- External device deployment - Connecting USB drives or other devices to deploy the malware
Phase 3: Cash Extraction
- Ploutus malware issued unauthorized commands to the ATM's Cash Dispensing Module
- Forced rapid withdrawal of all stored currency
- Malware deleted evidence and created false impressions to deceive bank employees
- Proceeds were split among conspirators in predetermined portions
Technical Sophistication
The Ploutus malware demonstrated several advanced capabilities:
- Anti-detection features: Designed to delete evidence and mislead financial institution employees
- XFS middleware targeting: Communicated directly with Extensions for Financial Services (XFS) APIs
- Remote activation: Could be triggered via SMS or keyboard commands
- Multi-vendor compatibility: Capable of attacking diverse ATM hardware
- Obfuscation: Protected by commercial obfuscators like .NET Reactor to hinder analysis
National Scope of the Operation
The scheme affected financial institutions across the United States, with documented incidents in:
- Nebraska (multiple locations)
- Texas
- Pacific Northwest states
- Southeast region
- Multiple other states nationwide
Visual representations released by the U.S. Attorney's Office show the geographic spread of attacks and associated losses, demonstrating the truly nationwide nature of this criminal enterprise.
The Terrorist Connection: Tren de Aragua
This case represents a critical intersection of cybercrime and terrorism financing. Tren de Aragua originated as a prison gang in Venezuela's Tocorón prison in the mid-2000s but has since evolved into a transnational criminal organization with presence throughout the Western Hemisphere.
TdA's Criminal Portfolio
The organization engages in:
- Drug trafficking
- Firearms trafficking
- Commercial sex trafficking
- Kidnapping and extortion
- Murder and violent assault
- Financial crimes targeting U.S. institutions
- Money laundering operations
Formal Terrorist Designation
On February 20, 2025, the U.S. Department of State officially designated Tren de Aragua as a Foreign Terrorist Organization (FTO) and Specially Designated Global Terrorist (SDGT). This designation:
- Blocks all property and interests in property within U.S. jurisdiction
- Prohibits U.S. persons from transacting with the organization
- Enables enhanced law enforcement coordination
- Carries significant legal consequences for material support
Since January 20, 2025, the Department of Justice has federally indicted over 260 TdA members. In 2025 alone, the District of Nebraska charged 67 TdA members and leaders with offenses ranging from material support to terrorism to sex trafficking of minors.
Law Enforcement Response
Acting Assistant Attorney General Matthew R. Galeotti of the Criminal Division stated: "These defendants employed methodical surveillance and burglary techniques to install malware into ATM machines, and then steal and launder money from the machines, in part to fund terrorism and the other far-reaching criminal activities of TDA."
U.S. Attorney Lesley Woods emphasized the collaborative nature of the investigation: "A tirelessly dedicated team of Nebraska law enforcement agents and officers banded together to identify this vast international criminal network and to follow the money trail of this devastating financial crime back to its terroristic roots in Venezuela."
Unprecedented Interagency Collaboration
The investigation involved an extraordinary coalition of federal, state, and local agencies:
Federal Agencies:
- FBI Omaha Field Office and multiple field offices nationwide
- Homeland Security Investigations (HSI)
- U.S. Secret Service
- U.S. Marshals Service
- Customs and Border Patrol
- Immigration and Customs Enforcement
- Multiple U.S. Attorney's Offices
State and Local Partners: Over 50 police departments and sheriff's offices across 15+ states participated in the investigation, demonstrating unprecedented law enforcement cooperation.
Homeland Security Task Force Initiative
This operation is part of the Homeland Security Task Force (HSTF) established by Executive Order 14159, "Protecting the American People Against Invasion." The HSTF represents a whole-of-government partnership dedicated to eliminating:
- Criminal cartels
- Foreign gangs
- Transnational criminal organizations
- Human smuggling and trafficking rings
The task force places special emphasis on crimes involving children and utilizes all available tools to prosecute and remove violent criminal aliens from the United States.
Joint Task Force Vulcan
Originally created in 2019 to eradicate MS-13, Joint Task Force Vulcan has expanded to target Tren de Aragua. The task force comprises:
- Multiple U.S. Attorney's Offices nationwide
- DOJ's National Security Division
- DOJ's Criminal Division
- FBI, DEA, HSI, ATF, USMS, and Federal Bureau of Prisons
- International coordination through DOJ's Office of International Affairs
Implications for Financial Institutions
This case highlights several critical vulnerabilities in ATM security:
Physical Security Gaps
- Standalone ATMs in retail locations present higher risk
- Physical access controls remain the first line of defense
- Tamper detection systems require consistent monitoring
- Regular physical inspections are essential
Technical Vulnerabilities
- Windows-based ATM operating systems create attack surfaces
- XFS middleware can be exploited by sophisticated malware
- Antivirus solutions must be specifically configured for ATM environments
- Hard drive security and access controls are critical
Recommended Countermeasures
Financial institutions should implement:
- Enhanced Physical Security
- Tamper-evident seals and locks
- Video surveillance with AI-powered anomaly detection
- Regular physical inspections for signs of tampering
- Secure enclosures with improved access controls
- Technical Protections
- Application whitelisting to prevent unauthorized code execution
- Device control policies to block unauthorized USB devices
- Network segmentation and monitoring
- Regular security patching and updates
- Encrypted hard drives with secure boot processes
- Operational Controls
- 24/7 monitoring of ATM networks
- Rapid incident response procedures
- Staff training on physical security indicators
- Collaboration with law enforcement
- Detection Capabilities
- Behavioral analytics to identify unusual cash dispensing patterns
- Log analysis for malware indicators
- Regular integrity checks of ATM software
- Network traffic analysis for command-and-control communications
The Broader Terrorism Financing Threat
This case exemplifies a disturbing trend: sophisticated cyber operations funding terrorist activities. The use of ATM jackpotting as a revenue stream demonstrates:
- Technical sophistication: Foreign terrorist organizations are developing or acquiring advanced cyber capabilities
- Financial motivation: Traditional funding sources are supplemented by financial crime
- Transnational reach: Operations span multiple countries with coordinated execution
- Money laundering integration: Stolen funds are systematically laundered through complex networks
Current Status and Ongoing Investigations
The defendants face charges that carry maximum sentences of 20 to 335 years imprisonment. However, as with all criminal cases, defendants are presumed innocent until proven guilty beyond a reasonable doubt.
The investigation remains ongoing, with law enforcement officials indicating this represents only a portion of TdA's criminal enterprise. The U.S. Department of State is offering rewards of up to $5 million for information leading to the arrest and conviction of TdA leader Hector Rusthenford Guerrero Flores.
Conclusion
The indictment of 54 individuals in this ATM jackpotting conspiracy represents a significant victory in the fight against both cybercrime and terrorism financing. However, it also serves as a stark reminder of the evolving threat landscape facing financial institutions.
As Acting Assistant Attorney General Galeotti stated, "The Criminal Division will not tolerate networks of thieves who breach the security of our financial system, including for the nefarious purpose of providing material support to terrorists."
For financial institutions, this case underscores the critical importance of defense-in-depth security strategies that address both physical and cyber threats. The convergence of organized crime, terrorism, and sophisticated cyber capabilities demands heightened vigilance and proactive security measures.
Key Takeaways for Security Professionals
- Physical security remains fundamental - Even sophisticated cyber operations require physical access to ATMs
- Malware detection must be ATM-specific - Generic antivirus solutions may not protect against specialized ATM malware
- Monitoring is essential - Unusual cash dispensing patterns can indicate compromise
- Interagency cooperation works - This case demonstrates the power of coordinated law enforcement
- Terrorism financing evolves - Organizations are diversifying revenue streams to include financial cybercrime
Additional Resources
For the complete Department of Justice press release and visual evidence, visit: https://www.justice.gov/usao-ne/pr/tren-de-aragua-members-and-leaders-indicted-multi-million-dollar-atm-jackpotting-scheme
This analysis is based on publicly available court documents and Department of Justice press releases. The charges described in the indictments are allegations, and all defendants are presumed innocent unless and until proven guilty in a court of law.





