France's La Poste and La Banque Postale Crippled by Massive Christmas DDoS Attack
Critical postal and banking services knocked offline just 72 hours before Christmas as France faces unprecedented wave of cyberattacks targeting government and critical infrastructure
Executive Summary
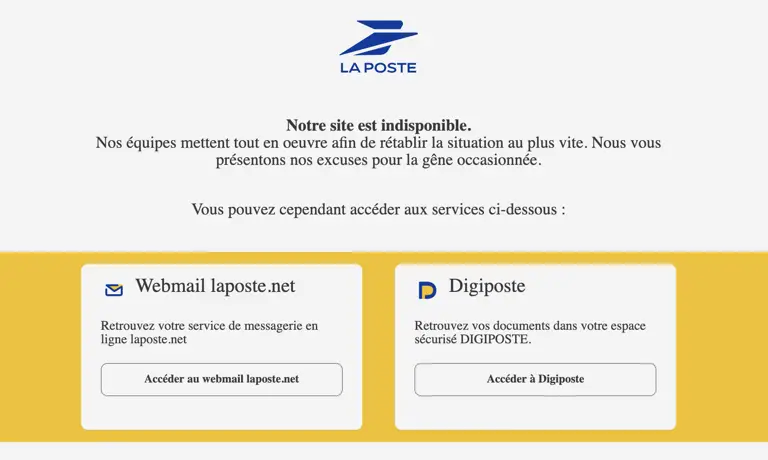
France's national postal service La Poste and its banking subsidiary La Banque Postale suffered a devastating distributed denial-of-service (DDoS) attack on Monday, December 22, 2025, rendering online services inaccessible during the critical Christmas delivery period. The attack disrupted package deliveries, online banking, and digital services for millions of French citizens, with no visibility on when services would return to normal.
This incident represents the latest in a series of high-profile cyberattacks targeting French government and critical infrastructure in December 2025, including a significant breach of the Interior Ministry's email servers and the discovery of remote access malware aboard a passenger ferry—all occurring within a single week.
The Attack: What Happened
At approximately 6:15 AM local time on Monday, December 22, 2025, La Poste's digital infrastructure began collapsing under a massive DDoS attack targeting its DNS servers. The attack flooded the postal service's systems with illegitimate connection requests, overwhelming the infrastructure and making legitimate access impossible.
Services Impacted
The attack affected virtually every digital service in the La Poste ecosystem:
- La Poste websites and mobile applications – completely inaccessible
- Colissimo parcel tracking and shipping services – unable to process new shipments or provide tracking
- La Banque Postale online banking and mobile app – customers locked out of accounts
- Digiposte digital vault – users unable to access stored documents including pay slips and invoices
- La Poste Mobile – telecommunications services disrupted
- France's Digital Identity service – authentication systems offline
Customer Impact
At Paris post offices decorated with Christmas garlands, frustrated customers lined up to send or collect last-minute parcels were turned away by staff. The timing could not have been worse—La Poste typically sorts and delivers more than 2 million items in the immediate run-up to Christmas.
La Banque Postale serves over 10.8 million active retail customers and maintains the largest branch network in France with over 17,000 contact points and 7,700 post offices. As the only bank in France charged with implementing universal banking accessibility services, the outage particularly affected vulnerable populations who depend on its services.
What Still Worked
La Poste confirmed that while digital services were down, some operations continued:
- Physical bank card payments at point-of-sale terminals
- ATM withdrawals
- WERO payment transfers
- Manual package deliveries (though significantly slowed)
- Text message authentication for online payments (as a backup measure)
Timeline of Events
| Date | Event |
|---|---|
| Saturday, December 20 | Initial DDoS attack disrupts La Poste services for several hours |
| Monday, December 22, 6:15 AM | Major DDoS attack begins, taking down all digital services |
| Monday, December 22, afternoon | La Poste confirms cyberattack, states no customer data compromised |
| Monday, December 22 | BPCE group (Banque Populaire, Caisse d'Épargne) experiences separate IT issues, resolved by midday |
| As of publication | Services remain disrupted with no restoration timeline |
Technical Analysis
Attack Vector
The attack specifically targeted La Poste's DNS servers, rendering domain names inaccessible and preventing users from reaching any of the company's web-based services. This is a classic DDoS technique that maximizes disruption while avoiding direct intrusion into systems containing sensitive data.
La Poste confirmed that customer data remained secure throughout the attack—a key distinction from data breach incidents. However, some cybersecurity experts expressed skepticism about the "simple DDoS" characterization, suggesting the attack may have been more sophisticated than initially disclosed.
Attack Attribution
As of publication, no group has claimed responsibility for the attack. The incident follows a pattern of DDoS attacks that have targeted French critical infrastructure throughout 2025, many attributed to pro-Russian hacktivist groups conducting operations in retaliation for France's support of Ukraine.
According to cybersecurity firm Cyble, France experienced 845 mentions of targeting activities in underground communications channels in just the first three months of 2025, with DDoS attacks accounting for 73% of incidents.
Context: France Under Siege
The La Poste attack caps an extraordinary week of cyber incidents targeting French institutions, highlighting the escalating threat environment facing the nation's critical infrastructure.
Interior Ministry Breach (December 11-17, 2025)
Just one week before the La Poste attack, France's Interior Ministry confirmed that hackers breached its internal email servers in an attack detected overnight between December 11-12, 2025.
Interior Minister Laurent Nuñez disclosed that attackers:
- Accessed professional email inboxes and recovered access codes
- Consulted sensitive files including the Criminal Records Processing System (TAJ) and Wanted Persons File (FPR)
- Potentially extracted several dozen confidential files
A 22-year-old suspect, identified by the alias "SSRQM," was arrested on December 17, 2025, near Limoges. The suspect, who had prior convictions for cybercrime offenses in 2025, faces up to 10 years in prison for unauthorized access to state data systems.
The attack was claimed by administrators of BreachForums, who alleged it was conducted in revenge for the 2025 arrests of forum moderators including individuals using the aliases "ShinyHunters," "Hollow," "Noct," "Depressed," and "IntelBroker." The attackers claimed to have accessed data on 16.4 million French citizens, though authorities dispute this figure.
Related Reading: French Interior Ministry Email Servers Breached in Latest Government Cyberattack
Ferry Malware Plot (December 12-17, 2025)
In a parallel investigation, France's counterespionage agency (DGSI) discovered Remote Access Trojan (RAT) malware aboard the GNV Fantastic, an Italian passenger ferry docked at the Mediterranean port of Sète.
The malware was capable of remotely controlling the vessel's operating systems, potentially including navigation components. A Latvian crew member was arrested and charged with:
- Conspiring to infiltrate computer systems on behalf of a foreign power
- Attempted intrusion into automated data systems
- Possession of devices capable of interfering with navigation systems
Interior Minister Nuñez strongly hinted at Russian involvement, stating "foreign interference very often comes from the same country." The investigation is being led by the DGSI in cooperation with Italian authorities and Eurojust.
Pattern of Russian Hybrid Warfare
France has formally attributed multiple cyberattacks to Russia's GRU military intelligence service throughout 2025. In April 2025, France's National Cybersecurity Agency (ANSSI) published a detailed report on APT28 (Fancy Bear) operations targeting French entities since 2021.
The EU has condemned Russia's "persistent hybrid campaigns" which include:
- Cyberattacks on government and critical infrastructure
- Acts of sabotage and physical attacks
- Disinformation and information manipulation
- Covert operations targeting democratic institutions
Related Reading: France vs. Russia: Unmasking APT28's Cyber Espionage Campaign
The Growing DDoS Threat to Financial Services
The La Banque Postale attack reflects a broader trend of escalating DDoS attacks against global financial institutions. According to a June 2025 report by FS-ISAC and Akamai, the financial services sector is now the top target for volumetric DDoS attacks worldwide.
Key Statistics
- DDoS attacks on financial services increased disproportionately compared to other industries in 2024-2025
- API attacks targeting financial institutions increased 58% between 2023 and 2024
- One coordinated DDoS campaign in 2024 caused multi-day service disruptions across several banks
- The widespread use of DDoS-for-Hire services has made attacks cheaper and more accessible
2025: The Year of Record-Breaking DDoS
The scale of DDoS attacks has reached unprecedented levels in 2025:
- September 2025: Cloudflare mitigated an 11.5 Tbps attack
- Three weeks later: A 22.2 Tbps attack shattered the previous record
- Q1 2025: Cloudflare blocked 20.5 million DDoS attacks—96% of all attacks mitigated in 2024
Related Reading: The DDoS Arms Race: How 2025 Became the Year of Record-Breaking Cyber Assaults
Impact on French Citizens
Banking Disruptions
La Banque Postale plays a unique role in France's financial system. It is the only bank legally mandated to provide universal banking accessibility through Livret A accounts, serving approximately 1.5 million customers who would otherwise be excluded from traditional banking services.
The bank also supports 1.6 million customers identified as "financially vulnerable" by the Observatory of Banking Inclusion—individuals below the poverty line, those experiencing over-indebtedness, or those banned from traditional banking services.
For these populations, losing access to online banking during the holiday period represents more than inconvenience—it can mean inability to:
- Check account balances before making purchases
- Authorize urgent payments
- Access emergency funds
- Verify incoming deposits
Postal Disruptions
With Christmas just days away, the attack threatens to delay or prevent delivery of countless holiday packages and cards. While La Poste confirmed that physical deliveries were "being maintained at this stage," the inability to track packages, generate shipping labels, or process new shipments creates significant disruption.
The attack also impacts businesses relying on Colissimo services for e-commerce fulfillment during the peak holiday shopping period.
Response and Mitigation
La Poste's Response
In an official statement, La Poste confirmed:
"A distributed denial of service incident rendered its online services inaccessible. Customer data was safe, but mail distribution, including parcels, had been slowed."
The company's teams are "mobilized to resolve the situation quickly," though no restoration timeline has been provided.
La Banque Postale's Response
The bank redirected payment authorizations to SMS-based authentication as a temporary measure and confirmed that in-store card payments and ATM services remained operational.
Questions About Preparedness
The success of the attack in taking down services for an extended period raises questions about DDoS mitigation capabilities at one of France's largest banking and postal institutions. Modern DDoS protection solutions typically claim to detect and mitigate attacks in real-time using advanced traffic filtering, rate limiting, and cloud-based scrubbing centers.
The fact that Saturday's initial attack was followed by an even more devastating assault on Monday suggests attackers may have been probing defenses and adapting their tactics—a common pattern in sophisticated DDoS campaigns.
Implications for Critical Infrastructure Security
The Convergence of Threats
France's December 2025 cyber incidents illustrate how multiple attack vectors can converge to create compounding security challenges:
- State-sponsored espionage (Interior Ministry breach)
- Critical infrastructure sabotage (ferry malware)
- Service disruption attacks (La Poste DDoS)
This combination of data theft, potential physical sabotage, and service denial represents the full spectrum of cyber threats facing modern nation-states.
Recommendations for Organizations
Based on the 2025 threat landscape, organizations—particularly those in critical infrastructure and financial services—should:
- Implement robust DDoS mitigation with cloud-based scrubbing and automatic detection
- Maintain offline operational capabilities for essential services
- Conduct regular red team exercises to identify vulnerabilities before attackers do
- Develop incident response plans that account for extended outages
- Share threat intelligence with industry peers and government agencies
- Address insider threats through proper vetting and access controls
- Segment networks to prevent lateral movement from compromised systems
Related Reading: The Evolution of DDoS Attacks: From Mirai to Hyper-Volumetric Threats
Looking Ahead
The La Poste attack represents a significant escalation in the ongoing campaign of cyber operations targeting French institutions. With no claim of responsibility and services still disrupted, many questions remain unanswered:
- Was this attack coordinated with other recent incidents?
- What group or nation-state is behind the campaign?
- Will French authorities identify and apprehend those responsible?
- How will La Poste strengthen its defenses to prevent future incidents?
What is clear is that France—like many Western nations supporting Ukraine—faces an elevated and sustained cyber threat from state-aligned actors willing to target critical civilian infrastructure.
For the millions of French citizens waiting for packages and struggling to access their bank accounts during the Christmas holiday, this attack serves as a stark reminder that cybersecurity is not merely a technical concern but a matter of national resilience.
Related Articles
- French Interior Ministry Email Servers Breached in Latest Government Cyberattack
- France vs. Russia: Unmasking APT28's Cyber Espionage Campaign
- The DDoS Arms Race: How 2025 Became the Year of Record-Breaking Cyber Assaults
- The Evolution of DDoS Attacks: From Mirai to Hyper-Volumetric Threats
- Germany Accuses Russia of Air Traffic Control Attack as Aviation Cybersecurity Crisis Deepens
- Global Cybersecurity Incident Review: January – April 2025
- Briefing on the 2025 Cybersecurity Landscape: Key Threats, Trends, and Incidents