Global Cybersecurity Incident Review: January – April 2025

Executive Summary
The first four months of 2025 witnessed an alarming escalation in the global cybersecurity threat landscape, characterized by an unprecedented surge in attack volume and sophistication. Cyber attacks per organization globally increased by 47% compared to Q1 2024, reaching an average of 1,925 weekly incidents.1 Ransomware attacks, in particular, experienced a dramatic spike, with various reports indicating historic highs in victim counts and incident frequency. Q1 2025 was marked as the worst quarter to date for ransomware victims, with one source tracking over 2,000 incidents, a 102% increase year-over-year.2 Another report noted a 126% global rise in reported ransomware incidents compared to Q1 2024.1
Several high-impact incidents underscored the severity of the threat environment. The cyberattack on Change Healthcare, a subsidiary of UnitedHealth Group, caused catastrophic disruption across the U.S. healthcare system, potentially compromising the data of up to 190 million individuals and inflicting severe financial strain on providers.4 The theft of over $1.46 billion in cryptocurrency from the Bybit exchange, allegedly by North Korea's Lazarus Group, highlighted the immense financial risk within the digital asset space.10 Major attacks also impacted media (Lee Enterprises 2), government entities globally (Palau, Yap, Union County PA, KLIA Airport, Italian and Moroccan government sites 13), and critical third-party service providers (DISA Global Solutions 11).
Analysis revealed that Healthcare, Education/Research, Government/Military, Manufacturing, and various Service sectors (Business, Consumer, Technology, Telecommunications) were among the most frequently targeted industries globally.1 Dominant trends included the evolution of ransomware tactics, such as double extortion and the fragmentation of major RaaS groups; the increasing sophistication of social engineering, amplified by AI-driven deepfakes and a surge in vishing 21; a rise in malware-free attacks leveraging legitimate system tools 21; persistent exploitation of software vulnerabilities 2; and the growing significance of supply chain risks.22
The response landscape remained dynamic. Organizations focused on enhancing resilience through improved technical controls, incident response planning, and employee training.3 Law enforcement agencies demonstrated increased international cooperation, targeting cybercrime infrastructure through operations like Endgame.31 Concurrently, the global regulatory environment continued to evolve, with major legislation like the EU's NIS2 Directive and Digital Operational Resilience Act (DORA) coming into force or effect in 2025, alongside updates to HIPAA in the U.S. and the proliferation of state-level privacy laws, creating a complex compliance challenge for global organizations.29
I. The Escalating Threat Landscape: Q1-Q2 2025 Overview
A. Unprecedented Surge in Global Attack Volume
The initial months of 2025 marked a significant intensification of the global cyber threat environment. Data compiled by cybersecurity researchers indicated a sharp and concerning rise in the frequency of attacks targeting organizations worldwide. Check Point Research, for instance, reported that the average number of cyber attacks experienced per organization each week surged to 1,925 in the first quarter of 2025. This figure represents a substantial 47% increase compared to the same period in 2024, underscoring the rapidly growing challenge organizations face in defending their digital assets.1
Ransomware remained a primary driver of this escalation, with multiple threat intelligence firms converging on the conclusion that Q1 2025 set new records for ransomware activity. BlackFog tracked 278 disclosed ransomware incidents in Q1, a 45% increase from Q1 2024, with March setting a monthly record.2 However, analyses encompassing non-disclosed victims painted an even starker picture. The GuidePoint Research and Intelligence Team (GRIT) identified 2,063 new ransomware victims posted on leak sites during Q1 2025, deeming it the worst quarter to date. This represented a staggering 102% increase compared to Q1 2024 and a 30.8% increase from the previous quarter (Q4 2024).2 Similarly, Check Point Research documented a 126% year-over-year increase in reported ransomware incidents globally for Q1 2025, totaling 2,289 incidents.1 Cyble also reported a record-breaking quarter, noting a peak of 886 new victims added to leak sites in February alone.2
This surge translates to a relentless pace of attacks. GRIT calculated that ransomware groups were claiming an average of 22.9 new victims per day during Q1 2025.2 Looking further ahead, Cybersecurity Ventures projected that the frequency of ransomware attacks could reach one every two seconds by 2031, illustrating the exponential acceleration of this threat.39
The dramatic increase in ransomware volume may be linked to evolving attacker economics. Reports suggest a growing reluctance among victims to pay ransoms, with data from Chainalysis 19 indicating a potential decline in overall ransom payments. Cyble analysts proposed that this dwindling return per attack could be incentivizing ransomware groups to significantly increase the volume of their attacks.2 If the probability of receiving payment from any single victim decreases, attackers may shift towards a higher-volume, lower-success-rate model to maintain revenue streams. This potential dynamic implies that while refusing ransom payments is a crucial deterrent, the resulting increase in attack frequency still imposes significant disruption, recovery costs, and data loss burdens on a larger pool of victims globally.
Furthermore, the significant disparity between the number of disclosed incidents (e.g., BlackFog's 278) and the number of tracked victims on leak sites (e.g., GRIT's 2,063) highlights a critical aspect of the threat landscape: the vast majority of ransomware incidents likely go unreported publicly.2 BlackFog focuses specifically on publicly acknowledged attacks, whereas GRIT monitors dark web leak sites where attackers post victim names, often including organizations that have not disclosed the breach. The substantial difference (~1,800 victims in Q1) strongly suggests that publicly available data represents only a fraction of the true scale of ransomware activity. Consequently, assessments of the economic impact and prevalence of ransomware based solely on public disclosures may significantly underestimate the actual threat level and the resources required to combat it effectively.
B. Geographic Hotspots and Regional Trends
While the surge in cyber attacks was a global phenomenon, certain regions experienced particularly intense activity in early 2025. The United States remained the primary target, especially for ransomware groups. GRIT reported that an unprecedented 59% of tracked ransomware victims in Q1 2025 were based in the U.S., the highest proportion observed to date.2 BlackFog's data corroborated this, showing the U.S. accounted for 52% of disclosed and 55% of undisclosed ransomware attacks.2 Check Point Research similarly found that North America represented 62% of all reported ransomware incidents globally.1 This concentration is likely driven by factors such as the high density of valuable targets and perhaps a perception among attackers that U.S. organizations are more likely or able to pay ransoms.19
However, other regions witnessed alarming growth rates in overall cyber attack activity. According to Check Point Research's Q1 2025 data, Latin America experienced the most dramatic year-over-year increase in average weekly attacks per organization, soaring by 108% to reach 2,640 attacks. Europe saw a 57% increase (1,612 weekly attacks), North America a 40% increase (1,357 weekly attacks), Africa a 39% increase (3,286 weekly attacks - the highest absolute average), and the Asia-Pacific (APAC) region a 38% increase (2,934 weekly attacks).1 The extreme growth observed in Latin America suggests this region may be emerging as a significant new focal point for cybercriminals. This could be attributed to the region's rapid digitalization and economic development potentially outpacing the maturity of its cybersecurity infrastructure and defenses, making it an attractive target for attackers seeking organizations with potentially high value but lower security postures compared to more established markets. Organizations operating or expanding within Latin America must therefore recognize this heightened risk and prioritize strengthening their regional cybersecurity capabilities.
The global nature of the threat was further evidenced by numerous specific incidents reported across diverse countries, including France, Canada, the Czech Republic, Italy, Japan, Brazil, Morocco, Switzerland, Germany, Belgium, Australia, the UK, India, Poland, Singapore, Taiwan, Argentina, and Austria.14
State-sponsored cyber activity also contributed significantly to the threat landscape, often with clear geopolitical motivations. Chinese-nexus groups, notably Salt Typhoon, were actively exploiting vulnerabilities in Cisco networking devices to target telecommunications providers and potentially government communications in the U.S., Taiwan, Italy, South Africa, and Thailand.4 CrowdStrike reported a 150% increase in observed China-nexus adversary activity overall.21 Russian-linked actors were implicated in attacks against Ukrainian critical infrastructure, Italian government systems, and diplomatic entities in Kazakhstan.15 A group potentially linked to Russia, Storm-237, targeted Microsoft 365 accounts across various critical sectors in Europe and the U.S. using sophisticated phishing techniques.10 North Korean actors, particularly the Lazarus Group (also known as APT38 or TraderTraitor), were allegedly behind the massive Bybit cryptocurrency theft and were observed using platforms like LinkedIn for espionage campaigns targeting organizations globally.10 This underscores the persistent threat posed by nation-state actors engaging in espionage, disruption, and financially motivated attacks often targeting critical infrastructure and sensitive data.
II. Major Global Cybersecurity Incidents (Jan-Apr 2025)
The first four months of 2025 were marked by numerous significant cybersecurity incidents affecting organizations across various sectors and geographic regions. Ransomware, data breaches, state-sponsored espionage, and large-scale cryptocurrency theft were prominent features of the threat landscape.
A. Overview Table: Significant Global Cyber Incidents (Jan-Apr 2025)
The following table provides a consolidated, non-exhaustive list of major publicly reported cyber incidents between January and April 2025, illustrating the breadth and diversity of threats during this period.
| Date (Reported/Occurred) | Victim | Sector | Country/Region | Attack Type | Brief Impact Summary | Source Snippet(s) |
| Jan 2025 | Kazakh Diplomatic Entities | Government | Kazakhstan | State-Sponsored (Suspected Russia) | Spearphishing for cyber espionage via malicious documents | |
| Jan 2025 | Italian Government Websites | Government | Italy | DDoS (Pro-Russian Group Claimed) | Disruption of ministries, public services, transport platforms | |
| Jan 2025 | TalkTalk (Claim) | Telecommunications | UK | Data Breach (Claimed by Hacker "b0nd") | Claimed sale of 18.8M user records (names, emails, IPs, phone#) from 3rd party; Investigation ongoing | |
| Jan 2025 | Gravy Analytics / Unacast | Data Broker | US / Norway | Data Breach (AWS Key Misappropriation) | Exposure of precise location data for millions, including sensitive locations | |
| Jan 2025 | PowerSchool | Education Technology | US / Canada | Data Breach (Credential Compromise) | Potential exposure of student/staff PII (names, SSNs, medical, grades) affecting 6,505 school districts | |
| Jan 2025 | Sichuan Juxinhe Network Technology Co. | Technology | China | State-Sponsored (Linked to Salt Typhoon) | US Sanctions imposed for role in cyber intrusions targeting US telecoms | |
| Jan 2025 | US Telecoms / Treasury (Salt Typhoon) | Telecom / Government | US | State-Sponsored (China - Salt Typhoon) | Breach of 9 US telecoms, access to communications; Theft of 3,000+ Treasury files | |
| Jan 2, 2025 (Discovered) | Community Health Center, Inc. (CHC) | Healthcare | US (CT) | Data Breach (Hacking) | Medical records & SSNs of 1M+ patients exposed; Breach persisted Oct 2024 - Jan 2025 | |
| Jan 14, 2025 (Update) | Change Healthcare (UHG) | Healthcare IT | US | Ransomware (ALPHV/BlackCat) / Data Breach | Data review "substantially complete" for Feb 2024 attack; Victim count increased to potential 190M | |
| Jan 18, 2025 (Reported) | AT&T (FBI Data Links) | Telecommunications | US | Data Breach | Compromise of FBI agent call/text logs (numbers, contacts); Linked to earlier 109M account breach | |
| Jan 20, 2025 (Reported) | Conduent | IT Services / BPO | US | Cyberattack (Suspected Ransomware) | Disruption to services (e.g., state payments) in multiple states; Server rebuilding required | |
| Jan 23, 2025 | Phemex Crypto Exchange | Finance (Crypto) | Global | Crypto Heist | Theft of $85M+ in cryptocurrency from hot wallet | |
| Jan 24, 2025 | Qilin Ransomware Group | Threat Actor | Global | Ransomware Campaign | Targeted Lee Enterprises (Media), Globelink Int'l (Logistics), 1st Health (Healthcare) | |
| Jan 25, 2025 (Reported) | NoOnes Crypto Platform | Finance (Crypto) | Global | Crypto Heist (Solana Bridge Exploit) | Loss of ~$8M in crypto assets due to exploit on Jan 1 | |
| Jan 27, 2025 (Update) | Globe Life / American Income Life Insurance | Finance (Insurance) | US | Data Breach | June 2024 breach impact revised to 850k individuals (names, DOB, SSNs) | |
| Jan/Feb 2025 | Cisco Routers (Salt Typhoon) | Technology / Telecom | Global (US focus) | State-Sponsored (China - Salt Typhoon) | Exploitation of IOS XE vulns (CVE-2023-20198, -20273) targeting 1000+ devices; Breached US telecoms | |
| Feb 2025 | Lee Enterprises | Media | US | Ransomware (Qilin) | Disruption to print/online operations (75+ papers); 350 GB data stolen claim; Ransom demanded | |
| Feb 2025 | DISA Global Solutions | Business Services | US | Data Breach | Affected 3.3M individuals; Potential compromise of PII/financial data for employees of client companies | |
| Feb 2025 | Orange (Romania/Global) | Telecommunications | Romania / Global | Data Breach (Claimed by Hacker) | Claimed breach of 600k customer records from Orange Romania + other divisions | |
| Feb 2025 | LANIT Group | IT Services | Russia | Cyberattack | Attack on major Russian IT system integrator, impacting financial services subsidiaries | |
| Feb 2025 | HCRG Care Group | Healthcare / Social Svcs | UK | Ransomware (Medusa) | Claimed theft of 2.275 TB data; $2M ransom demand | |
| Feb 2025 | Trimble Cityworks | Software (Gov/Infra) | US | Vulnerability Exploit (CVE-2025-0994) | Active exploitation of asset management tool used by local governments; Patch urged by CISA | |
| Feb 2025 | Palo Alto Networks Firewalls | Technology | Global | Vulnerability Exploit (CVE-2025-0108) | Active exploitation of PAN-OS auth bypass flaw, potentially chainable | |
| Feb 2025 | GrubHub | Food Delivery | US | Data Breach (Third Party) | Compromise of customer, merchant, driver PII (names, email, phone, partial payment card for some) | |
| Feb 12, 2025 | zkLend | Finance (DeFi) | Global | Crypto Heist (Smart Contract Flaw) | Theft of 3,600 ETH ($9.5M) via rounding error bug | |
| Feb 13, 2025 | Zacks Investment Research | Finance | US | Data Breach (Leaked by "Jurak") | Leak of 12M user account details (names, emails, addresses, phone#) from alleged June 2024 breach | |
| Feb 14, 2025 | Microsoft 365 Accounts | Cloud Services | Global (Eur/US) | Phishing (Storm-237 / Russia-linked) | Device code phishing targeting Gov, NGO, IT, Defense, Telecom, Health, Energy sectors | |
| Feb 17, 2025 | Palau Health Ministry | Healthcare | Palau | Ransomware (Qilin) | Attack allowed data theft; Ministry recovered from attack | |
| Feb 18, 2025 | Insight Partners | Finance (Venture Cap) | US (NY) | Cyberattack (Social Engineering) | Systems breached in January via social engineering | |
| Feb 18, 2025 | National Assembly of Ecuador | Government | Ecuador | Cyberattack (Attempted) | Two attacks aimed at disruption and accessing sensitive data | |
| Feb 21, 2025 | Bybit Crypto Exchange | Finance (Crypto) | Global | Crypto Heist (Alleged Lazarus Group) | Theft of $1.46B+ in ETH from cold wallet; Largest crypto hack recorded | |
| Feb 26, 2025 | Cleveland Municipal Court | Government (Judicial) | US (OH) | Cyber Incident | Shutdown for multiple days due to cybersecurity incident | |
| Feb 26, 2025 | Anne Arundel County Government | Government (Local) | US (MD) | Cyber Incident | Impacted public services and government buildings; Recovery ongoing | |
| Mar 1, 2025 | Palau Health Ministry (Update) | Healthcare | Palau | Ransomware (Qilin) | Confirmed recovery from Feb 17 attack | |
| Mar 3, 2025 | Rubrik | Technology (Data Sec) | US | Data Breach (Log Server) | Anomalous activity on log server; Rotated potentially leaked auth keys | |
| Mar 3, 2025 | Angel One | Finance (Stock Broker) | India | Data Breach (AWS Account) | Client information impacted; Shares dropped significantly | |
| Mar 5, 2025 | Toronto Zoo | Entertainment/Culture | Canada (ON) | Ransomware (Akira) / Data Breach | Visitor data (names, transaction info) 2000-Apr 2023 stolen in earlier attack (reported Jan 2024, impact ongoing) | |
| Mar 10, 2025 | Sunflower Medical Group | Healthcare | US (KS) | Ransomware (Rhysida) / Data Breach | ~221k patients affected by Dec 15 attack; Rhysida claimed credit Jan, threatened leak | |
| Mar 12, 2025 | Yap State Dept. of Health Services | Healthcare | Micronesia | Ransomware (Unknown) | Health system network taken offline, computers shut down | |
| Mar 13, 2025 (Discovered) | Union County, Pennsylvania | Government (Local) | US (PA) | Ransomware (Unknown) / Data Breach | Personal information of residents stolen during attack | |
| Mar 23, 2025 (Started) | Kuala Lumpur Int'l Airport (KLIA) | Transport (Airport) | Malaysia | Ransomware (Unknown) | Disruptions started Mar 23; Hackers demanded $10M ransom, rejected by government | |
| Apr 1, 2025 | CMC Technology Group | Technology | US | Ransomware (BianLian) | Data breach reported | |
| Apr 1, 2025 | Delta Life | Finance (Insurance) | US | Ransomware (Ransomhub) | Data breach reported | |
| Apr 1, 2025 | Goosehead Insurance | Finance (Insurance) | US | Ransomware (Chaos) | Data breach reported | |
| Apr 1, 2025 | Meridian Senior Living | Healthcare | US | Ransomware (BianLian) | Data breach reported | |
| Apr 8, 2025 | Petr Fiala (Czech PM) | Government | Czech Republic | Social Media Hack | PM's X account hacked with fake posts | |
| Apr 9, 2025 | Universidade de Brasília | Education (University) | Brazil | Cyberattack | University systems targeted | |
| Apr 12, 2025 | Moroccan Government Websites | Government | Morocco | DDoS Attacks | Massive cyber attack hitting government websites | |
| Apr 12, 2025 | DaVita | Healthcare | US (CO) | Ransomware | Major healthcare provider experienced ransomware attack | |
| Apr 15, 2025 | Radio Rhône / Rhône FM | Media (Radio) | Switzerland | Ransomware | Radio station systems impacted by ransomware | |
| Apr 16, 2025 | Polizia Locale di Roma Capitale (via IT Svc) | Government (Police) | Italy (Rome) | Cyberattack (via IT Service Provider) | Police systems affected, requiring manual processes (e.g., handwritten tickets) | |
| Apr 17, 2025 | Service public de Wallonie (SPW) | Government (Regional) | Belgium | Cyberattack | Wallonia public service administration targeted | |
| Apr 17, 2025 | Tokai University | Education (University) | Japan | Cyberattack | University systems targeted | |
| Apr 18, 2025 | 1st Health Inc. | Healthcare | US | Ransomware (Qilin) | Data breach reported | |
| Apr 18, 2025 | AccessSMT | Construction/Supply | Canada | Ransomware (Qilin) | Data breach reported |
B. In-Depth Case Studies (Selected High-Impact Incidents)
While the table above provides a broad overview, several incidents during this period warrant closer examination due to their scale, impact, or significance in illustrating key trends.
1. Change Healthcare (UHG Subsidiary) Cyberattack (Ongoing Impact):
Arguably the most impactful cyber incident with repercussions felt throughout early 2025 originated from an attack discovered on February 21, 2024. Change Healthcare, a critical technology provider processing approximately 15 billion healthcare transactions annually and touching one in three U.S. patient records, was crippled by a ransomware attack attributed to the ALPHV/BlackCat group.7 The attack, which involved data exfiltration between February 17-20 and subsequent encryption, incapacitated core functions like claims processing, payment systems, prescription fulfillment, and insurance verification.7
The consequences were devastating and widespread. Hospitals and physician practices across the U.S. faced severe financial distress due to interrupted cash flow; an American Hospital Association (AHA) survey found 94% of hospitals reported financial impacts, with a third reporting over half their revenue disrupted.7 Many smaller practices were forced to use personal funds to cover expenses.6 Patient care was directly affected, with 74% of hospitals reporting impacts, including delays in obtaining authorizations for necessary care.7 The scale of the data breach itself was immense. Initial estimates suggested 100 million individuals might be affected, but by January 2025, UnitedHealth Group (UHG), Change Healthcare's parent company, indicated the number could be closer to 190 million Americans, making it potentially the largest healthcare data breach ever recorded.4 Compromised data included health insurance information, medical records, and potentially financial details, though UHG stated Social Security numbers and financial/banking data were not impacted for the majority.4
The response involved immediate system shutdowns by Change Healthcare.45 UHG reportedly paid a $22 million ransom, although complexities arose when the affiliate who allegedly conducted the attack claimed they were not paid by the ALPHV group, potentially leading to further data leak threats involving another group, RansomHub.9 UHG provided significant financial assistance (around $9 billion) to affected providers.9 The recovery process was protracted, with normal operations taking weeks or months to resume for many providers.7 Change Healthcare offered notification assistance to affected covered entities and began mailing individual notices on a rolling basis, confirming its data review was "substantially complete" by January 14, 2025.5 Regulatory scrutiny followed, with the U.S. Department of Health and Human Services' Office for Civil Rights (OCR) launching investigations into Change Healthcare and UHG regarding potential HIPAA violations.47 Multiple lawsuits were filed, consolidated into multidistrict litigation, with motions to dismiss key claims scheduled for March 2025.9 The incident starkly highlighted the systemic risks inherent in the consolidation of critical healthcare infrastructure and the profound consequences of cyberattacks on essential third-party providers.6 The American Medical Association (AMA) continues to advocate for stronger resilience requirements for clearinghouses and health plans.6
2. Bybit Cryptocurrency Exchange Theft (February 2025):
The volatile cryptocurrency market faced another major security event in February 2025 with a record-breaking theft from the Bybit exchange. Threat actors successfully stole over $1.46 billion worth of Ethereum (ETH) from one of the exchange's cold wallets, making it the largest single cryptocurrency hack recorded to date.10 The exact method of attack was not disclosed by Bybit, described only as "sophisticated".42
The financial impact was immense, though Bybit assured users of its solvency and stated that all client assets were fully backed, implying the exchange could absorb the loss.12 Blockchain investigators tracked the movement of the stolen funds, noting the attacker quickly began splitting and moving the ETH across numerous addresses.12 The FBI publicly attributed the attack to North Korea's Lazarus Group (also known as APT38 or TraderTraitor), a notorious state-sponsored entity frequently linked to major cryptocurrency heists.10 This incident underscores the continued focus of sophisticated state actors on high-value cryptocurrency targets and the persistent security challenges faced by exchanges managing vast sums of digital assets.
3. Lee Enterprises Ransomware Attack (February 2025):
The media sector proved vulnerable when the Qilin ransomware group targeted Lee Enterprises, a major U.S. media conglomerate owning around 350 publications across 25 states.2 The attack, reported in February 2025, caused significant operational disruption, affecting both print and online functions for at least 75 local newspapers.11 Lee Enterprises confirmed that the incident involved file encryption and data exfiltration, consistent with a ransomware attack.11 The Qilin group claimed responsibility on their leak site, asserting they had stolen 350 GB of data, including sensitive investor information, financial transactions, and payment records, demanding a ransom by March 5th.2 BlackFog ranked this among the top five most significant ransomware attacks of Q1 2025 based on impact.2 The incident highlights the susceptibility of the media industry to disruptive attacks that can impede the flow of information and demonstrates the continued activity of potent ransomware groups like Qilin against prominent targets.
4. DISA Global Solutions Data Breach (Reported February 2025):
Illustrating the pervasive nature of supply chain risk, DISA Global Solutions, a provider of third-party employment screening services (including drug testing and background checks) for over 55,000 enterprises, reported a data breach impacting more than 3.3 million individuals.11 The breach potentially exposed highly sensitive personal information such as names, Social Security numbers, driver's license numbers, government ID numbers, and financial account details belonging to individuals screened on behalf of DISA's clients, which include a third of Fortune 500 companies.11 While DISA stated it had contained the incident, notified affected individuals, and found no evidence of data misuse at the time of reporting, the breach underscores the significant downstream risk posed by compromises at service providers holding large volumes of sensitive data for numerous organizations.11
5. Salt Typhoon Campaign (Ongoing, Reported Jan/Feb 2025):
State-sponsored espionage remained a major threat vector, exemplified by the ongoing campaign attributed to Salt Typhoon, a China-nexus group. Between December 2024 and January 2025, the group targeted over 1,000 Cisco network devices globally, exploiting critical vulnerabilities in Cisco IOS XE software (CVE-2023-20198 and CVE-2023-20273).10 This campaign successfully breached multiple U.S. telecommunications providers, potentially gaining access to sensitive communications, including those of government officials.4 Targets were also identified in Italy, South Africa, and Thailand.11 The U.S. government responded by identifying an alleged hacker involved and imposing sanctions on a related Chinese technology firm, Sichuan Juxinhe Network Technology Co..4 This campaign demonstrates the persistent efforts by nation-state actors to infiltrate critical infrastructure through widespread vulnerability exploitation for intelligence gathering purposes, highlighting the critical intersection of cybersecurity and geopolitics.
6. Other Notable Incidents:
Beyond these major cases, numerous other incidents contributed to the challenging landscape of early 2025. These included ransomware attacks crippling healthcare systems in Palau and the state of Yap in Micronesia 13, a rejected $10 million ransom demand following an attack on Malaysia's Kuala Lumpur International Airport 13, the leak of 12 million user records from Zacks Investment Research 10, sophisticated device code phishing attacks by the Russia-linked Storm-237 group against high-value targets using Microsoft 365 10, a claimed breach impacting 18.8 million TalkTalk customers via a third-party supplier 4, and another major healthcare breach at Community Health Center in Connecticut affecting over a million patients due to a third-party vendor vulnerability.17
III. Sector Vulnerability Analysis
The surge in cyber attacks during early 2025 did not impact all industries equally. Analysis of incident data and threat intelligence reports reveals distinct patterns of targeting, with certain sectors consistently appearing in the crosshairs of cybercriminals and state-sponsored actors.
A. Most Targeted Industries in Early 2025
Several industries repeatedly emerged as primary targets based on various metrics, including overall attack frequency and ransomware victimization rates:
- Healthcare: This sector remained a prime target, frequently ranking among the top three or four most attacked industries globally.1 The first quarter of 2025 saw 160 reported healthcare data breaches in the U.S. alone, compromising the records of 5.6 million patients.17 January contributed 70 of those breaches, affecting 2.7 million patients.18 Attackers target healthcare for its valuable Protected Health Information (PHI), which can be used for identity theft or fraud, and because disruption to critical operations creates significant leverage for ransom demands.19 The Change Healthcare incident serves as a stark example of the potential for systemic disruption.6 While healthcare providers were the most common initial point of compromise (75.6% of Q1 breaches), breaches involving third-party Business Associates often had a disproportionately large impact in terms of affected patient numbers (66% of patients affected in Q1 came from BA breaches).17
- Education/Research: This sector experienced the highest average number of weekly attacks per organization in Q1 2025, according to Check Point Research, with 4,484 attacks – a 73% increase year-over-year.1 Other sources confirmed its status as a highly targeted sector.26 The breach at PowerSchool, a major K-12 educational technology provider, affected numerous schools across the U.S. and Canada.4 Educational institutions are targeted for the large amounts of personal data they hold on students and staff, and are sometimes targeted by nation-state actors for research or intellectual property.27 GRIT noted a concerning 16% rise in education sector ransomware incidents in Q1.3
- Government/Military: Ranking second in weekly attack volume per Check Point (2,678 attacks/week, +51% YoY) 1, government entities at all levels (national, regional, local, judicial) were frequent targets. BlackFog also placed government among the top three sectors for disclosed ransomware attacks.2 Examples from early 2025 include attacks on the Palau Health Ministry 13, Yap State Health Services 13, Union County, Pennsylvania 13, Malaysia's KLIA Airport (state-owned) 13, the National Assembly of Ecuador 10, Cleveland Municipal Court 10, Anne Arundel County, Maryland 10, Italian and Moroccan government websites 14, and the Wallonia public service in Belgium.14 Motivations range from financial gain (ransomware) to operational disruption, espionage, and political influence.15
- Manufacturing: This sector emerged as a top target for ransomware groups. GRIT identified Manufacturing as the most attacked industry in Q1 2025.2 Check Point Research also ranked Industrial Manufacturing high among ransomware victims (9.1%).1 Other reports corroborate this, citing high attack rates and noting that 71% of ransomware attacks on industrial companies targeted manufacturers specifically.23 The sector's attractiveness stems from the increasing convergence of Information Technology (IT) and Operational Technology (OT) systems, the potential for highly disruptive impacts on production, the value of intellectual property, and a perception that its cybersecurity maturity may lag behind other sectors like finance.23
- Services (Business/Consumer/Technology): This broad category consistently ranked high in attack statistics. Check Point found Consumer Goods & Services (13.2%) and Business Services (9.8%) were the top two sectors targeted by ransomware globally in Q1.1 BlackFog included the Services sector in its top three for disclosed ransomware.2 GRIT ranked Business Services second for ransomware victimization.20 This category includes diverse organizations like IT service providers, consulting firms, screening services (like DISA Global 11), and outsourcing providers (like Conduent 40). Attacks on IT service providers are particularly concerning due to the potential for downstream impacts on their clients.19
- Finance/Insurance: While perhaps seeing slightly less ransomware activity compared to Manufacturing or Services in some Q1 reports 26, this sector remained a critical target, particularly for data breaches aimed at acquiring financial information and highly sophisticated phishing campaigns.24 Major incidents included massive crypto thefts (Bybit, Phemex, zkLend 10), large-scale data leaks from investment firms (Zacks Investment 10) and stock brokers (Angel One 13), and breaches at insurance companies (Globe Life 40, Goosehead 44, Delta Life 44). The sector faces intense regulatory scrutiny, exemplified by the EU's Digital Operational Resilience Act (DORA), which came into effect in January 2025.34
- Technology/Telecommunications: This sector experienced significant attack growth, with Check Point reporting a 94% year-over-year increase in weekly attacks against Telecommunications organizations.1 Telecom ranked third highest for weekly attack volume 1, and Technology was among the top three ransomware targets according to GRIT.2 Incidents involved state-sponsored exploitation of network hardware (Cisco routers 10), phishing campaigns against cloud services (Microsoft 365 10), breaches at security companies (Rubrik 13), exploitation of security appliances (Palo Alto firewalls 16), and attacks on major telecom providers (Orange 11, TalkTalk via supplier 4) and IT integrators (LANIT 11). Motivations include espionage, infrastructure disruption, and gaining access to downstream clients through compromised service providers.19
- Critical Infrastructure (Energy, Water, Transport): While perhaps less frequently named in top-level statistics compared to Healthcare or Manufacturing, attacks on critical infrastructure carry immense potential impact. Specific incidents included the ransomware attack on KLIA Airport 13 and disruptions potentially affecting state services via the Conduent attack.40 Targeting of critical infrastructure, especially by state-sponsored actors or ransomware groups seeking maximum leverage, remains a paramount concern.22 Regulatory frameworks like the EU's NIS2 Directive and the upcoming U.S. CIRCIA rules place a strong emphasis on protecting these vital sectors.36
B. Table: Q1 2025 Sector Attack Statistics Comparison
Comparing data from different threat intelligence reports provides a more nuanced understanding of sector targeting, highlighting areas of consensus and potential variations based on methodology (e.g., overall attacks vs. ransomware, disclosed vs. tracked victims).
| Sector | Check Point (Overall Attack Rank / YoY Change) | Check Point (Ransomware Rank / % Victims) | GRIT (Ransomware Rank) | BlackFog (Disclosed Ransomware Rank) | Healthcare Reports (Breach Volume/Impact) |
| Education/Research | #1 / +73% | #6 / 6.0% (Q2 2024 data) | High Target | #4 | N/A |
| Government/Military | #2 / +51% | Not Top 5 | High Target | #3 | N/A |
| Telecommunications | #3 / +94% | Not Top 5 | High Target | N/A | N/A |
| Healthcare | High Target | #4 / 7.2% | #4 | #1 | Very High (5.6M patients Q1) |
| Finance/Insurance | High Target | #8 / 7.0% (Q2 2024 data) | High Target | N/A | N/A |
| Manufacturing (Industrial) | High Target | #3 / 9.1% | #1 | High Target | N/A |
| Services (Consumer Goods &) | High Target | #1 / 13.2% | High Target | #2 (Services) | N/A |
| Services (Business) | High Target | #2 / 9.8% | #2 | #2 (Services) | N/A |
| Technology | High Target | Not Top 5 | #3 | High Target | N/A |
| Retail/Wholesale | High Target | Not Top 5 | #2 | High Target | N/A |
| Construction & Engineering | High Target | #5 / 6.5% | #4 | High Target | N/A |
(Note: Ranks and percentages may vary slightly between reports due to differing methodologies and timeframes within Q1/early Q2. Some data points reference slightly earlier periods where Q1 2025 data wasn't available in the snippet).
C. Analysis of Sector-Specific Risks and Impacts
The reasons behind the intense targeting of specific sectors are multifaceted. Healthcare organizations possess vast amounts of sensitive PHI, making them attractive targets for data theft, while the critical nature of their operations provides significant leverage for ransomware extortionists demanding payment to restore systems essential for patient care.19 Financial institutions are targeted for direct monetary gain through theft, fraud, or extortion, as well as for valuable customer financial data.24 The Manufacturing sector is increasingly vulnerable due to valuable intellectual property, the potential for significant financial losses from production downtime, and the growing attack surface created by IT/OT convergence.23 Government entities are targeted for espionage, disruption of services, political influence, or sometimes financial extortion.15 Technology and Telecommunications companies are targeted not only for their own data and operations but also as conduits to access their vast customer bases and critical infrastructure control.19
The impact of attacks also varies by sector. In Healthcare, beyond financial losses and data compromise, the primary concern is the potential impact on patient safety due to delayed treatments, inaccessible records, or malfunctioning medical devices.7 For Critical Infrastructure sectors like Energy and Water, successful attacks could have severe consequences for public safety and national security.22 Financial sector breaches erode customer trust and can lead to significant direct financial losses.24 Attacks on the Technology sector can have widespread downstream effects, as demonstrated by supply chain compromises.4
A significant factor amplifying risk, particularly in sectors like Manufacturing, Energy, and Utilities, is the increasing convergence of IT and Operational Technology (OT) systems.23 Historically, OT networks controlling physical processes (like factory machinery or power grid controls) were isolated from corporate IT networks. However, the drive for efficiency, remote monitoring, and data analytics has led to increased connectivity between these domains.25 This interconnectivity creates new pathways for cyber threats originating in the IT environment (which is typically more exposed to external threats) to propagate into sensitive OT environments.25 OT systems often have unique vulnerabilities: they may use legacy protocols, have longer lifecycles than IT equipment (making patching difficult), and were often designed without modern security considerations, assuming physical isolation provided sufficient protection. Consequently, threats like ransomware, once primarily data-theft or IT disruption tools, can now potentially cause physical disruption to industrial processes, halt manufacturing lines, or interfere with critical infrastructure operations, dramatically raising the stakes for organizations in these sectors.
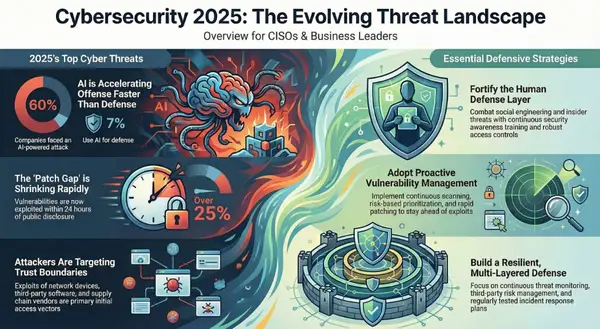
Another notable development is the increased targeting of sectors previously considered less prominent targets or potentially "off-limits" by some attackers, such as non-profit organizations and the education sector.3 GRIT's Q1 2025 report highlighted a 106% increase in attacks on non-profits and a 16% rise in education sector incidents, suggesting a possible "erosion of respect" for perceived boundaries.3 These sectors often hold significant amounts of personal data (students, donors) but may operate with tighter budget constraints, potentially leading to weaker cybersecurity postures compared to large commercial enterprises. This trend indicates that organizations in these sectors cannot rely on any assumed lower priority from attackers and must invest in robust security measures commensurate with the value of the data they hold and the potential impact of disruption.
IV. Evolving Threat Actor Tactics, Techniques, and Procedures (TTPs)
Cyber adversaries continuously refine their methods to bypass defenses and maximize impact. Early 2025 saw several key trends in attacker TTPs.
A. Dominant Attack Vectors and Methodologies
- Ransomware Evolution: The Ransomware-as-a-Service (RaaS) model, where developers lease their malware and infrastructure to affiliates who conduct attacks, remained the dominant operational structure.2 The tactic of "double extortion"—encrypting victim data and exfiltrating it with threats to leak it publicly if the ransom isn't paid—became standard practice, employed in an estimated 95% of attacks in Q1 2025.1 The ransomware landscape also experienced significant fragmentation following law enforcement actions against major groups like LockBit and ALPHV/BlackCat in 2024. This led to affiliates migrating to other groups and the emergence or increased prominence of numerous players. In early 2025, groups such as RansomHub (which rapidly gained dominance in late 2024 and Q1 2025), Clop (known for large-scale data exfiltration via zero-day exploits), Akira, Qilin, Lynx, Medusa, Rhysida, and DragonForce were particularly active.2 Average ransom demands remained high, with BlackFog calculating an average of $663,582 based on known demands in Q1.2
- Phishing & Social Engineering: Exploiting human psychology remained a primary method for gaining initial access.22 Attackers employed increasingly sophisticated tactics, leveraging AI and deepfake technology to create more convincing lures.21 Common variants included highly targeted spear phishing messages, voice phishing (vishing) – which saw a reported 442% surge in the second half of 2024 21, SMS-based phishing (smishing), baiting (e.g., leaving infected USB drives), and Business Email Compromise (BEC) scams designed to trick employees into making fraudulent payments or divulging sensitive information.23 The use of malicious QR codes embedded in emails also emerged as a technique.26 State-sponsored groups like Lazarus were observed using fake job offers on professional networking sites like LinkedIn to deliver malware and steal credentials.16
- Vulnerability Exploitation: Threat actors continued to aggressively scan for and exploit security flaws in software and hardware. This included both newly discovered zero-day vulnerabilities and older, unpatched known vulnerabilities (Common Vulnerabilities and Exposures - CVEs).2 Notable examples from early 2025 involved vulnerabilities in Cisco IOS XE network devices (exploited by Salt Typhoon 10), Fortinet security appliances 11, Palo Alto Networks' PAN-OS 16, Trimble Cityworks asset management software 16, and Ivanti Connect Secure VPNs.20 The Clop ransomware group specialized in exploiting vulnerabilities in file transfer solutions for mass data theft.2 The number of actively exploited vulnerabilities saw a significant increase, with GRIT reporting a 75% rise in Q1 2025 compared to Q1 2024 2, emphasizing the critical importance of timely patch management.
- Malware-Free / Living-off-the-Land (LotL): A significant trend involved attackers minimizing their use of custom malware to evade detection by traditional antivirus solutions. CrowdStrike reported that 79% of the detections made by its platform in 2024 were malware-free.21 Instead, attackers utilized legitimate tools and utilities already present on the target systems – such as PowerShell, Windows Management Instrumentation (WMI), and administrative tools like PsExec – to conduct reconnaissance, move laterally, escalate privileges, and exfiltrate data.50 This approach focuses heavily on compromising valid credentials (identity-based intrusions) and abusing trusted processes, making detection more challenging for security tools reliant on signature-based malware identification.21
- Other Vectors: Distributed Denial-of-Service (DDoS) attacks remained a prevalent threat, used to overwhelm websites or services and cause disruption, sometimes employed by hacktivists or as a smokescreen to cover other malicious activities.14 Cryptojacking, where attackers hijack system resources to mine cryptocurrency, continued to occur.27 Insider threats, stemming from malicious employees or partners, or accidental actions by negligent insiders, remained a significant risk vector.21 Misconfigurations in cloud environments also presented opportunities for attackers to gain unauthorized access or expose data.22
B. The Role of Emerging Technologies
Emerging technologies, particularly Artificial Intelligence (AI), are increasingly influencing the cybersecurity landscape, acting as both a tool for attackers and a potential asset for defenders.
- AI-Powered Attacks: Cybercriminals are actively leveraging AI, especially generative AI (GenAI), to enhance their operations.1 AI can automate the creation of more convincing and personalized phishing emails, social media profiles, and even websites, making social engineering attacks more effective and scalable.21 There is also concern that AI could be used to accelerate vulnerability discovery, develop polymorphic malware that evades signature detection, or optimize attack strategies. A survey indicated that 60% of U.S. IT professionals viewed AI-enhanced malware as the most concerning AI-generated threat.28 Nation-state actors like North Korea's FAMOUS CHOLLIMA were observed using GenAI to supercharge social engineering and insider threat operations.21
- Deepfakes: The ability of AI to generate highly realistic fake audio, video, and images (deepfakes) poses a growing threat. The volume of deepfakes surged dramatically in recent years (a reported 550% increase from 2019 to 2023), with hundreds of thousands shared online.28 This technology is being incorporated into sophisticated phishing and social engineering schemes, used for impersonation in BEC scams, or potentially for spreading disinformation.22 The trade in deepfake creation tools on dark web forums has also reportedly increased significantly.29
- Quantum Computing Threats: While still an emerging technology, quantum computing poses a long-term strategic threat to cybersecurity. Sufficiently powerful quantum computers could potentially break many of the cryptographic algorithms currently used to protect data and communications.22 Although large-scale, fault-tolerant quantum computers capable of this are not yet available, organizations are being advised to start monitoring developments and exploring post-quantum cryptography (PQC) standards to prepare for a future transition.22
C. Key Threat Actors: Profiles and Motivations
The threat landscape in early 2025 was populated by a diverse range of actors with varying motivations:
- Ransomware Groups (Financially Motivated): This remained arguably the most visible and disruptive category. The RaaS ecosystem thrived, with GRIT tracking 70 active groups in Q1 2025.2 Key players during this period included RansomHub, Clop, Akira, Qilin, Lynx, Medusa, Rhysida, DragonForce, BianLian, Chaos, and others identified via leak site postings and incident reports.2 Their primary motivation is financial gain, achieved through extorting ransom payments for data decryption and/or non-disclosure of stolen data. These groups often operate with a high degree of professionalism, resembling businesses ("enterprising adversaries") focused on maximizing profit and efficiency.21
- State-Sponsored Actors (Espionage, Disruption, Influence): Nation-states continued to leverage cyber capabilities to achieve strategic objectives. Notable activity involved actors linked to China (e.g., Salt Typhoon targeting telecommunications for espionage 4), Russia (e.g., attacks on Ukraine, European entities, Storm-237 phishing campaigns 10), and North Korea (e.g., Lazarus Group/APT38 targeting cryptocurrency exchanges and defense sectors, FAMOUS CHOLLIMA using GenAI 10). Their motivations typically include intelligence gathering, theft of intellectual property, disruption of critical infrastructure or government services, and exerting geopolitical influence.4 There is growing concern about the blurring lines and potential spillover of tools and techniques between state-sponsored groups and financially motivated cybercriminals.29
- Financially Motivated Cybercriminals (Non-Ransomware): Beyond ransomware operators, numerous other criminals focused on direct financial theft or monetization of stolen data. This includes groups specializing in large-scale cryptocurrency theft (like the Bybit and zkLend attackers 10), actors stealing and selling sensitive personal or financial data on dark web markets (like the alleged hacker "Jurak" leaking Zacks Investment data 10 or "b0nd" claiming TalkTalk data 4), and perpetrators of payment fraud and BEC scams.23
- Hacktivists: Actors motivated by political or social agendas continued to use cyber means, primarily DDoS attacks, to disrupt targets and draw attention to their causes. Examples include DDoS attacks targeting Moroccan government websites attributed to hacktivists.14
D. Supply Chain and Third-Party Risk Trends
Attacks targeting the software supply chain and third-party vendors remained a critical and growing concern in early 2025. This vector was identified as a leading cybersecurity risk and a major barrier to achieving organizational resilience.22 Instead of directly attacking a well-defended primary target, adversaries compromise a less secure supplier, vendor, or software component that the primary target trusts and utilizes.
Numerous incidents highlighted this risk: the TalkTalk data exposure was suspected to originate from a third-party subscription management platform 4; the massive Community Health Center breach stemmed from a vulnerability in a third-party vendor's system 18; the DISA Global Solutions breach impacted potentially millions of individuals whose data was held by DISA on behalf of its corporate clients 11; and the PowerSchool breach occurred via compromise of a support platform, potentially exposing data from thousands of school districts.4
The increasing complexity and opacity of modern supply chains exacerbate this risk.29 Organizations often lack sufficient visibility into the security practices of their direct suppliers, let alone fourth- and Nth-party vendors further down the chain. Vulnerabilities introduced in widely used open-source software components can also create significant supply chain risks, as demonstrated by incidents like the 3CX compromise in 2024.23
Recognizing this threat, regulators are placing greater emphasis on third-party risk management. Proposed updates to the U.S. HIPAA Security Rule include greater scrutiny of third-party vendors (Business Associates).17 The EU's DORA explicitly includes requirements for managing risks associated with ICT third-party providers in the financial sector.34 Similarly, the EU's NIS2 Directive mandates that covered entities address supply chain security risks, including assessing the security practices of their direct suppliers.37
The convergence of several factors—increasingly complex and globalized supply chains, sophisticated state-sponsored actors actively exploiting these chains, and a fragmented landscape of international regulations—creates a particularly challenging environment for multinational corporations.29 These organizations must secure their own operations while also managing the risks associated with potentially hundreds or thousands of suppliers, all while navigating a patchwork of differing cybersecurity and data privacy laws across multiple jurisdictions (e.g., NIS2/DORA in the EU, various U.S. state laws, India's DPDP Act). This complexity makes comprehensive supply chain risk management extremely difficult and resource-intensive, increasing the likelihood that vulnerabilities or compliance gaps within the extended ecosystem will be exploited by adversaries.
V. Global Responses and the Regulatory Environment
The escalating threat landscape prompted responses from affected organizations, law enforcement agencies, and regulators worldwide.
A. Organizational Incident Response and Mitigation Strategies
In the face of relentless attacks, organizations focused on bolstering their defenses and improving their ability to respond and recover. Key strategies observed and recommended included:
- Building Resilience: Emphasis shifted beyond prevention to encompass resilience – the ability to withstand and quickly recover from attacks. This involves robust business continuity and disaster recovery planning, alongside well-defined incident response protocols.3 Examples of recovery efforts were seen with the Palau Health Ministry 13 and Anne Arundel County.10 The Change Healthcare incident underscored the critical need for resilience, particularly for essential service providers.6
- Implementing Technical Controls: Foundational security measures remained crucial. Recommendations consistently included strong encryption for data at rest and in transit, ubiquitous multi-factor authentication (MFA), rigorous vulnerability management and timely patching (especially for actively exploited flaws), network segmentation to limit lateral movement, and adopting Zero Trust security architectures.3
- Leveraging Advanced Security Tools: Organizations increasingly rely on advanced tools for detection and response, such as Endpoint Detection and Response (EDR), Extended Detection and Response (XDR), and Security Information and Event Management (SIEM) systems, often enhanced with AI capabilities.21
- Conducting Regular Assessments: Proactive identification of weaknesses through regular security risk assessments, penetration testing, and audits was frequently advised.3
- Focusing on the Human Element: Recognizing that human error is often exploited, continuous cybersecurity awareness training for employees on topics like phishing identification, password hygiene, and reporting suspicious activity remained a critical component of defense strategies.3
- Managing Third-Party Risk: Organizations are placing greater emphasis on vetting the security posture of their vendors and suppliers, incorporating security requirements into contracts, and continuously monitoring third-party risk.17
- Exploring AI for Defense: While AI poses risks, organizations are also exploring its potential to enhance cybersecurity through improved threat detection, faster anomaly analysis, automated incident response, and predictive analytics.8
B. Law Enforcement Actions and International Cooperation
Law enforcement agencies globally intensified efforts to combat cybercrime through disruption operations and international collaboration.
- Major Disruption Operations: A notable example, though announced just prior to the 2025 period but highly relevant, was Operation Endgame. This multinational effort, involving the FBI, Europol, Eurojust, and law enforcement from the UK, Germany, France, Netherlands, Denmark, and others, targeted the infrastructure (servers, domains) underpinning several major malware droppers and loaders, including IcedID, Smokeloader, Pikabot, and Bumblebee. The operation involved arrests, searches, and over 100 server takedowns, aiming to dismantle the networks responsible for distributing ransomware and other malware to millions of computers worldwide.33
- Role of International Agencies:
- Europol: As the EU's law enforcement agency, Europol plays a central role in coordinating cross-border investigations and intelligence sharing related to serious and organized crime, including cybercrime.56 Its European Cybercrime Centre (EC3) provides operational support, technical expertise, and facilitates collaboration between member states and partners.32 EC3 hosts the Joint Cybercrime Action Taskforce (J-CAT), comprising liaison officers working on high-profile cybercrime cases.32 Europol publishes key threat assessments like the EU-SOCTA 2025, which highlighted cyber-attacks and online fraud as major threats.31 Recent Europol-supported actions in early 2025 included crackdowns on child sexual exploitation platforms (Kidflix), AI-generated CSAM, and arrests related to the Phobos and 8Base ransomware operations.32
- Interpol: With its global reach across 190+ member countries, Interpol facilitates international police cooperation, information sharing (via databases and notices like Red Notices), and capacity building.57 It runs specific programs and operations targeting cybercrime and collaborates closely with national agencies like the FBI.57
- FBI: As the primary U.S. federal agency investigating cybercrime, the FBI works domestically and internationally through its Legal Attaché (Legat) program, participating in joint operations and collaborating with Interpol and Europol.58 The FBI was a key player in Operation Endgame.33
- Strategic Shift: Operations like Endgame signal a potential strategic shift in law enforcement tactics. Rather than solely focusing on arresting individual cybercriminals (who can often be replaced within criminal organizations), agencies are increasingly targeting the core infrastructure and services—such as malware delivery platforms, RaaS portals, bulletproof hosting, and cryptocurrency mixing services—that enable large-scale cybercrime. Disrupting these foundational elements aims to have a broader, more lasting impact on the cybercrime ecosystem.32 This approach acknowledges the industrialized nature of modern cybercrime and seeks to undermine its operational capabilities more systematically.
- Challenges: Despite successes, international cooperation faces persistent challenges, including differing legal frameworks across jurisdictions, difficulties in attribution, the use of anonymity-enhancing technologies by criminals, and the volatile nature of digital evidence.59
C. Table: Key Cybersecurity Regulations Impacting 2025
The regulatory landscape governing cybersecurity and data privacy continued its rapid evolution in 2025, with significant new legislation coming into effect or being implemented across major jurisdictions.
| Regulation Name | Jurisdiction | Scope (Sectors/Entities Covered) | Key Requirements | Status/Effective Date(s) in 2025 | Source Snippet(s) |
| EU NIS2 Directive (Directive 2022/2555) | European Union | Expanded list of "Essential" & "Important" entities (Energy, Transport, Health, Finance, Digital Infra, Public Admin, Postal, Waste Mgmt, Mfg, Chem, Food, Research, Space, Digital Providers) | Min. security measures (risk mgmt, incident handling, supply chain sec, encryption, MFA), Strict incident reporting (24h warning, 72h notification), Mgmt liability, Fines | Transposition deadline Oct 17, 2024; Enforcement from Oct 18, 2024; Registration deadline Jan 17, 2025 (for some entities) | |
| EU DORA (Regulation 2022/2554) | European Union | Financial entities (banks, insurers, investment firms) & their critical ICT third-party providers | ICT risk management framework, Incident reporting, Digital operational resilience testing, Third-party risk management oversight | Entered into force Jan 2023; Applies from Jan 17, 2025 | |
| EU AI Act | European Union | Providers & deployers of AI systems, tiered by risk level | Transparency, Data governance, Risk management, Human oversight (esp. for high-risk AI), Prohibited practices | Entered into force Aug 2024; Phased enforcement: Transparency/Governance obligations expected during 2025, more in 2026 | |
| US HIPAA Security Rule Updates (Proposed) | United States | HIPAA Covered Entities & Business Associates | Proposed: Annual tech inventories, Mandatory MFA, Stricter encryption, Regular audits, Incident response plans, Enhanced vendor scrutiny | Proposed updates announced Jan 2025, aiming for implementation during 2025 | |
| US State Comprehensive Privacy Laws | US States | Businesses meeting thresholds (revenue, data processing volume) interacting with state residents | Consumer rights (access, delete, correct, opt-out of sale/sharing/profiling), Security requirements, Risk assessments | Effective in 2025: Delaware, Iowa, Minnesota, Nebraska, New Hampshire, New Jersey, Tennessee, Maryland. (11 more laws effective 2025/2026 total) | |
| US CIRCIA (Cyber Incident Reporting for Critical Infrastructure Act) | United States | Entities in critical infrastructure sectors | Mandatory reporting of significant cyber incidents & ransom payments to CISA | Enacted 2022; CISA NPRM Apr 2024; Final rule expected late 2025 | |
| US Federal Contractor Rules (EO 14144 / FAR Updates) | United States | Federal contractors (above threshold or managing federal systems) | Vulnerability Disclosure Programs (VDPs), Software security attestations (SBOMs), Enhanced identity mgmt, Encryption | EO 14144 issued Jan 2025; FAR Council to update regulations; H.R. 872 (Fed Contractor Cyber Vuln Reduction Act) passed House Mar 2025 | |
| India Digital Personal Data Protection Act (DPDPA) 2023 | India | Data Fiduciaries processing digital personal data in India | Consent requirements, Data Principal rights, Significant Data Fiduciary obligations, Data breach reporting, Penalties | Enacted Aug 2023; Phased implementation, additional provisions expected during 2025 | |
| Canada PIPEDA (Personal Information Protection and Electronic Documents Act) | Canada | Private sector organizations collecting/using/disclosing personal info in commercial activities | Consent, Accountability, Safeguards, Individual access | Existing law, ongoing relevance and potential updates |
D. Analysis of Regulatory Impact and Compliance Challenges
The global trend towards more stringent and comprehensive cybersecurity regulation clearly accelerated into 2025.30 Legislations like the EU's NIS2 and DORA impose significant new obligations on a wide range of organizations regarding risk management, incident reporting, supply chain security, and operational resilience.34 Similarly, updates to HIPAA, the proliferation of U.S. state privacy laws, and sector-specific rules like CIRCIA reflect a growing governmental focus on mandating baseline security standards and increasing transparency around incidents.17 These regulations aim to improve overall cybersecurity posture and protect consumers and critical infrastructure.29
However, this rapid expansion of regulatory requirements presents significant challenges for organizations, particularly those operating internationally. The sheer volume and complexity of new rules create a substantial compliance burden.29 Furthermore, the lack of global harmonization leads to a fragmented landscape where companies must navigate overlapping, and sometimes conflicting, requirements across different jurisdictions.29 Over 76% of CISOs surveyed at a World Economic Forum event reported that regulatory fragmentation significantly impacts their ability to maintain compliance.29 This complexity extends to managing third-party compliance within intricate supply chains.29
There exists a potential tension: while the intent of these regulations is to enhance security, the resources required merely to understand, interpret, and document compliance across multiple frameworks could potentially divert attention and budget away from implementing the most effective, risk-based security controls tailored to an organization's specific threat environment. The focus might inadvertently shift towards achieving auditable compliance ("checking the box") rather than optimizing actual security posture, potentially leading to "regulatory fatigue" and diminishing returns.29 The potential for political shifts, such as a possible move towards deregulation in the U.S. contrasting with the EU's more prescriptive approach, could further complicate the global landscape.35 Effectively navigating this environment requires organizations to adopt strategic compliance approaches, leveraging common frameworks where possible, while ensuring that compliance activities genuinely contribute to improved cyber resilience.
VI. Outlook and Strategic Recommendations
The first four months of 2025 have established a trajectory of heightened cyber risk likely to persist throughout the year and beyond. Organizations must prepare for a future shaped by several key trends and adapt their strategies accordingly.
A. Summary of Key Trends Shaping the Near Future
- Persistent High Threat Volume: The record-breaking attack volumes seen in Q1, particularly for ransomware, are unlikely to abate quickly. Financially motivated actors will continue to innovate, and state-sponsored activity will remain tied to geopolitical dynamics.
- AI as a Double-Edged Sword: AI will increasingly be integrated into both attack TTPs (making social engineering more potent, potentially automating exploits) and defensive tools (enhancing detection, response, and analysis). Managing AI-related risks while harnessing its benefits will be critical.
- Sophisticated Social Engineering: Attacks targeting human psychology will remain a primary initial access vector, becoming more personalized and convincing through the use of AI and deepfakes.
- Continuous Vulnerability Exploitation: Attackers will continue to capitalize on unpatched vulnerabilities in software, hardware, and cloud services. The speed at which newly disclosed vulnerabilities are exploited is likely to increase.
- Supply Chain as a Battleground: The interconnectedness of digital ecosystems means supply chain security will remain a major focus for both attackers and defenders/regulators. Compromises via third parties will continue to cause significant downstream impact.
- Intensifying Regulatory Pressure: Governments worldwide will continue to enact and enforce stricter cybersecurity and data privacy regulations, demanding greater organizational accountability, transparency, and resilience. Harmonization challenges will persist.
- Widening Skills Gap: The demand for skilled cybersecurity professionals will continue to outstrip supply, exacerbated by the need for expertise in new areas like AI security and OT security. This gap impacts organizations' ability to effectively manage risk.29
- Focus on Operational Resilience: Beyond data protection, ensuring business continuity and the ability to recover quickly from disruptive attacks (like ransomware) will be paramount.
B. Actionable Recommendations for Organizations
Navigating this complex and dynamic threat landscape requires a proactive, strategic, and multi-faceted approach. Organizations should prioritize the following actions:
- Enhance Foundational Cyber Resilience: Adopt a "prevention-first" mindset where possible, but assume breaches will occur.1 Implement robust technical controls as standard practice: enforce MFA universally, utilize strong encryption for data at rest and in transit, maintain rigorous patch management processes (prioritizing actively exploited vulnerabilities), segment networks effectively, and progress towards a Zero Trust architecture.17 Invest in modern security operations capabilities, including advanced endpoint protection (EDR/XDR) and security analytics (SIEM/NG-SIEM), potentially augmented by AI.21 Conduct regular, comprehensive risk assessments and penetration tests to identify and remediate weaknesses proactively.3
- Address AI Risks and Opportunities Strategically: Develop clear internal governance policies and frameworks for the safe and ethical procurement, development, and deployment of AI systems.30 Implement processes to assess the security implications of AI tools before integration.29 Educate employees about AI-driven threats, particularly sophisticated phishing and deepfake-based impersonation attempts.28 Simultaneously, evaluate how AI can be responsibly leveraged to augment defensive capabilities, such as threat detection, anomaly analysis, and automating response actions.8
- Strengthen Supply Chain Security Posture: Recognize that third-party risk is integral to overall security. Implement thorough due diligence processes for vetting the security practices of potential vendors and suppliers.22 Embed clear cybersecurity requirements, incident notification protocols, and audit rights into supplier contracts.61 Utilize tools and services for continuous monitoring of third-party risk exposure.30 Foster collaborative relationships with key suppliers to improve collective resilience.
- Navigate Compliance Efficiently and Effectively: Stay actively informed about the evolving regulatory landscape applicable to the organization's operations and jurisdictions (e.g., NIS2, DORA, CCPA/CPRA and other state laws, HIPAA, CIRCIA, DPDP Act).30 Where feasible, map security controls to recognized frameworks (like NIST CSF, ISO 27001) that can satisfy requirements across multiple regulations, reducing redundant effort.48 Treat regulatory compliance as a baseline standard of security hygiene, not the ultimate goal; focus on implementing controls that genuinely reduce risk, rather than solely meeting audit requirements.
- Mature Incident Preparedness and Response: Develop, maintain, and regularly test a comprehensive incident response plan that outlines roles, responsibilities, communication strategies, and technical procedures for various attack scenarios.17 Conduct tabletop exercises or simulations to ensure the plan is practical and understood by relevant personnel. Establish relationships with external resources, such as legal counsel and incident response firms (potentially via retainers), in advance.3
- Invest in the Human Element: Implement continuous, engaging cybersecurity awareness training tailored to the organization's specific risks and employee roles.3 Foster a strong security culture where employees feel empowered to report suspicious activity without fear of blame. Address the cybersecurity skills gap through internal training and upskilling programs, recruitment efforts focused on diverse talent pipelines (potentially leveraging initiatives like the Cyber PIVOTT Act 69), and strategic partnerships with managed security service providers (MSSPs) or virtual CISO services where appropriate.3
- Embrace Collaboration and Information Sharing: Participate actively in relevant industry-specific Information Sharing and Analysis Centers (ISACs) or Organizations (ISAOs) to gain access to timely threat intelligence and best practices. Explore secure platforms for collaboration with peers and law enforcement, such as Europol's SPACE network for cybercrime experts 32 or initiatives supported under frameworks like the U.S. Cybersecurity Information Sharing Act (CISA 2015).70 Sharing anonymized threat indicators and defensive strategies benefits the entire ecosystem.
By implementing these recommendations, organizations can enhance their ability to anticipate, withstand, and respond to the complex and escalating cybersecurity threats characterizing the global landscape in 2025 and beyond.
Works cited
- Q1 2025 Global Cyber Attack Report from Check Point Software: An ..., accessed April 21, 2025, https://blog.checkpoint.com/research/q1-2025-global-cyber-attack-report-from-check-point-software-an-almost-50-surge-in-cyber-threats-worldwide-with-a-rise-of-126-in-ransomware-attacks/
- Cybersecurity Firms Report Record-Breaking Quarter for ..., accessed April 21, 2025, https://www.hipaajournal.com/q1-2025-ransomware-report/
- GRIT 2025 Q1 Ransomware & Cyber Threat Report | GuidePoint ..., accessed April 21, 2025, https://www.guidepointsecurity.com/resources/grit-2025-q1-ransomware-and-cyber-threat-report/
- Top Data Breaches of January 2025 - Strobes Security, accessed April 21, 2025, https://strobes.co/blog/top-data-breaches-of-january-2025/
- www.hipaajournal.com, accessed April 21, 2025, https://www.hipaajournal.com/change-healthcare-responding-to-cyberattack/#:~:text=It%20has%20been%20almost%2011,data%20is%20%E2%80%9Csubstantially%20complete.%E2%80%9D
- Hard lessons learned from Change Healthcare breach | American Medical Association, accessed April 21, 2025, https://www.ama-assn.org/about/leadership/hard-lessons-learned-change-healthcare-breach
- Change Healthcare Cyberattack Underscores Urgent Need to Strengthen Cyber Preparedness for Individual Health Care Organizations and as a Field | AHA, accessed April 21, 2025, https://www.aha.org/change-healthcare-cyberattack-underscores-urgent-need-strengthen-cyber-preparedness-individual-health-care-organizations-and
- Healthcare industry must brace itself for deluge of cyberattacks in 2025 | Viewpoint, accessed April 21, 2025, https://www.chiefhealthcareexecutive.com/view/healthcare-industry-must-brace-itself-for-deluge-of-cyberattacks-in-2025-viewpoint
- UnitedHealth Adopts Aggressive Approach to Recover Ransomware Attack Loans, accessed April 21, 2025, https://www.hipaajournal.com/change-healthcare-responding-to-cyberattack/
- February 2025: Major Cyber Attacks, Ransomware Attacks & Data Breaches, accessed April 21, 2025, https://www.cm-alliance.com/cybersecurity-blog/february-2025-major-cyber-attacks-ransomware-attacks-data-breaches
- Major Cyber Attacks in Review: February 2025 - SOCRadar® Cyber ..., accessed April 21, 2025, https://socradar.io/major-cyber-attacks-in-review-february-2025/
- Hacker steals record $1.46 billion from Bybit ETH cold wallet, accessed April 21, 2025, https://www.bleepingcomputer.com/news/security/hacker-steals-record-146-billion-from-bybit-eth-cold-wallet/
- Biggest Cyber Attacks, Ransomware Attacks, Data Breaches of March 2025, accessed April 21, 2025, https://www.cm-alliance.com/cybersecurity-blog/biggest-cyber-attacks-ransomware-attacks-data-breaches-of-march-2025
- The list of cyber attacks worldwide 2025 today - KonBriefing.com, accessed April 21, 2025, https://konbriefing.com/en-topics/cyber-attacks.html
- Significant Cyber Incidents | Strategic Technologies Program - CSIS, accessed April 21, 2025, https://www.csis.org/programs/strategic-technologies-program/significant-cyber-incidents
- 9 major cyber attacks & data breaches in February 2025, accessed April 21, 2025, https://www.cshub.com/attacks/articles/cyber-attacks-data-breaches-february-2025
- Q1 2025 Healthcare Data Breach Wrap-Up: 5.6 Million Patient Records Exposed, accessed April 21, 2025, https://compliancy-group.com/q1-2025-healthcare-data-breach-wrap-up/
- January 2025 Healthcare Breaches Impact 2.7 Million Patients, accessed April 21, 2025, https://compliancy-group.com/january-2025-healthcare-breaches/
- Ransomware Attack Surge Continues in 2025 - The HIPAA Journal, accessed April 21, 2025, https://www.hipaajournal.com/ransomware-attack-surge-continues-in-2025/
- 2025 Ransomware: Business as Usual, Business is Booming | Rapid7 Blog, accessed April 21, 2025, https://www.rapid7.com/blog/post/2025/04/08/2025-ransomware-business-as-usual-business-is-booming/
- 2025 Global Threat Report | Latest Cybersecurity Trends & Insights ..., accessed April 21, 2025, https://www.crowdstrike.com/en-us/global-threat-report/
- The Emerging Cybersecurity Threats in 2025 - What You Can Do To Stay Ahead, accessed April 21, 2025, https://cloudsecurityalliance.org/blog/2025/01/14/the-emerging-cybersecurity-threats-in-2025-what-you-can-do-to-stay-ahead
- Top 5 Cyber Threats Manufacturers Face in 2025 - Eye Security, accessed April 21, 2025, https://www.eye.security/blog/top-cyber-threats-manufacturers-face-in-2025
- Must-know cyber attack statistics and trends 2025 - Embroker, accessed April 21, 2025, https://www.embroker.com/blog/cyber-attack-statistics/
- Industrial Cybersecurity Market Outlook 2025: Focus on quantifying risk, embracing AI, building operational resilience, accessed April 21, 2025, https://industrialcyber.co/features/industrial-cybersecurity-market-outlook-2025-focus-on-quantifying-risk-embracing-ai-building-operational-resilience/
- Top Cybersecurity Statistics for 2025 - Cobalt, accessed April 21, 2025, https://www.cobalt.io/blog/top-cybersecurity-statistics-2025
- Cyber Attack Statistics for 2025: What They Mean for Your Business - Parachute, accessed April 21, 2025, https://parachute.cloud/cyber-attack-statistics-data-and-trends/
- Top Cybersecurity Threats [2025] - University of San Diego Online Degrees, accessed April 21, 2025, https://onlinedegrees.sandiego.edu/top-cyber-security-threats/
- Global Cybersecurity Outlook 2025 | World Economic Forum, accessed April 21, 2025, https://reports.weforum.org/docs/WEF_Global_Cybersecurity_Outlook_2025.pdf
- Cybersecurity Compliance in 2025: Preparing for New Regulations - Ntiva, accessed April 21, 2025, https://www.ntiva.com/blog/cybersecurity-compliance-in-2025
- The DNA of organised crime is changing – and so is the threat to Europe - Europol, accessed April 21, 2025, https://www.europol.europa.eu/media-press/newsroom/news/dna-of-organised-crime-changing-and-so-threat-to-europe
- European Cybercrime Centre - EC3 - Europol, accessed April 21, 2025, https://www.europol.europa.eu/about-europol/european-cybercrime-centre-ec3
- Operation Endgame: Coordinated Worldwide Law Enforcement Action Against Network of Cybercriminals - FBI, accessed April 21, 2025, https://www.fbi.gov/news/press-releases/operation-endgame-coordinated-worldwide-law-enforcement-action-against-network-of-cybercriminals
- Cyber resilience legislation: Global policy shifts in 2025 - Redstor, accessed April 21, 2025, https://www.redstor.com/resource-hub/cyber-resilience-legislation-global-policy-shifts-in-2025/
- How will rules and regulations affect cybersecurity and AI in 2025? | SC Media, accessed April 21, 2025, https://www.scworld.com/feature/how-will-rules-and-regulations-affect-cybersecurity-and-ai-in-2025
- Cyber Insights 2025: Cybersecurity Regulatory Mayhem - SecurityWeek, accessed April 21, 2025, https://www.securityweek.com/cyber-insights-2025-cybersecurity-regulatory-mayhem/
- Navigating NIS2 2025: How the New EU Cybersecurity Directive Affects Your Business, accessed April 21, 2025, https://leaf-it.com/navigating-nis2-2025-new-eu-cybersecurity-directive-affects-business/
- The NIS 2 Directive | Updates, Compliance, Training, accessed April 21, 2025, https://www.nis-2-directive.com/
- Global Ransomware Damage Costs Predicted To Exceed $275 Billion By 2031, accessed April 21, 2025, https://cybersecurityventures.com/global-ransomware-damage-costs-predicted-to-reach-250-billion-usd-by-2031/
- Data Breach Report: January 2025 Edition - PKWARE®, accessed April 21, 2025, https://www.pkware.com/blog/data-breach-report-january-2025-edition
- The State of Ransomware 2025 - BlackFog, accessed April 21, 2025, https://www.blackfog.com/the-state-of-ransomware-2025/
- January 2025 Data Breaches [LIST] - Pomerium, accessed April 21, 2025, https://www.pomerium.com/blog/january-2025-data-breaches-list
- The Most Recent Data Breaches in 2025 - Breachsense, accessed April 21, 2025, https://www.breachsense.com/breaches/
- Data breaches in April 2025 - Breachsense, accessed April 21, 2025, https://www.breachsense.com/breaches/2025/april/
- HIPAA Website Substitute Notice - Change Healthcare, accessed April 21, 2025, https://www.changehealthcare.com/hipaa-substitute-notice.html
- Change Healthcare Consumer support page - UnitedHealth Group, accessed April 21, 2025, https://www.unitedhealthgroup.com/ns/health-data-breach.html
- Change Healthcare Cybersecurity Incident Frequently Asked Questions - HHS.gov, accessed April 21, 2025, https://www.hhs.gov/hipaa/for-professionals/special-topics/change-healthcare-cybersecurity-incident-frequently-asked-questions/index.html
- Every Major Cybersecurity Compliance Standard To Know in 2025 - Fractional CISO, accessed April 21, 2025, https://fractionalciso.com/cybersecurity-compliance-standards/
- NIS2 Directive: new rules on cybersecurity of network and information systems, accessed April 21, 2025, https://digital-strategy.ec.europa.eu/en/policies/nis2-directive
- Last Year in Ransomware: Threat Trends and Outlook for 2025 - Halcyon, accessed April 21, 2025, https://www.halcyon.ai/blog/last-year-in-ransomware-threat-trends-and-outlook-for-2025
- Ransomware 2025: Attacks Keep Rising as Threat Shows its Resilience, accessed April 21, 2025, https://www.security.com/threat-intelligence/ransomware-trends-2025
- Cybersecurity threatscape: Q4 2024 – Q1 2025 - Positive Technologies, accessed April 21, 2025, https://global.ptsecurity.com/analytics/cybersecurity-threatscape-q4-2024-q1-2025
- 2025 Ransomware Report: What Q1 Trends Reveal About the Year Ahead, accessed April 21, 2025, https://www.bankinfosecurity.com/whitepapers/2025-ransomware-report-what-q1-trends-reveal-about-year-ahead-w-14970
- NIS2 Directive Is on the Edge of Enforcement: What Now for EU/U.S. Companies?, accessed April 21, 2025, https://www.crowell.com/en/insights/publications/nis2-directive-is-on-the-edge-of-enforcement-what-now-for-euus-companies
- Trend 2025 Cyber Risk Report | Trend Micro (US), accessed April 21, 2025, https://www.trendmicro.com/vinfo/us/security/news/threat-landscape/trend-2025-cyber-risk-report
- Europol - Wikipedia, accessed April 21, 2025, https://en.wikipedia.org/wiki/Europol
- INTERPOL | The International Criminal Police Organization, accessed April 21, 2025, https://www.interpol.int/
- Difference between INTERPOL and FBI, accessed April 21, 2025, https://interpol-stop.com/en/faq-en/difference-between-interpol-and-fbi/
- Cybercrime - Interpol, accessed April 21, 2025, https://www.interpol.int/Crimes/Cybercrime
- International Operations - FBI, accessed April 21, 2025, https://www.fbi.gov/about/leadership-and-structure/international-operations
- 2025 European Supply Chain Cybersecurity: NIS2 & more - BitSight Technologies, accessed April 21, 2025, https://www.bitsight.com/blog/nis2-and-european-supply-chain-security
- NIS2 Directive Transposition Tracker - ECSO - European Cyber Security Organisation, accessed April 21, 2025, https://ecs-org.eu/activities/nis2-directive-transposition-tracker/
- NIS2 across the EU - Fieldfisher, accessed April 21, 2025, https://www.fieldfisher.com/en/insights/nis2-across-the-eu
- NIS2 Directive Explained: Strengthening Network Security | RUCKUS Networks, accessed April 21, 2025, https://www.ruckusnetworks.com/blog/2025/nis2-explained/understanding_nis2_framework_for_network_security
- Cybersecurity Laws and Regulations to Know About (2025) - Office1, accessed April 21, 2025, https://www.office1.com/blog/cybersecurity-laws-and-regulations
- U.S. Cybersecurity and Data Privacy Review and Outlook – 2025 - Gibson Dunn, accessed April 21, 2025, https://www.gibsondunn.com/us-cybersecurity-and-data-privacy-review-and-outlook-2025/
- H.R.872 - 119th Congress (2025-2026): Federal Contractor Cybersecurity Vulnerability Reduction Act of 2025, accessed April 21, 2025, https://www.congress.gov/bill/119th-congress/house-bill/872
- January and February 2025 Cybersecurity Developments Under the Biden and Trump Administrations | Inside Government Contracts, accessed April 21, 2025, https://www.insidegovernmentcontracts.com/2025/03/january-and-february-2025-cybersecurity-developments-under-the-biden-and-trump-administrations/
- Committee Advances “Cyber PIVOTT Act,” Adopts 119th Congress Oversight Plan, accessed April 21, 2025, https://homeland.house.gov/2025/02/26/committee-advances-cyber-pivott-act-adopts-119th-congress-oversight-plan/
- America's Critical Infrastructure Sectors Urge Congress to Reauthorize Cybersecurity Information-Sharing Law - Bank Policy Institute, accessed April 21, 2025, https://bpi.com/americas-critical-infrastructure-sectors-urge-congress-to-reauthorize-cybersecurity-information-sharing-law/