INC Ransom: The Ransomware Group That Abandoned All Ethical Boundaries
Executive Summary
INC Ransom has emerged as one of the most aggressive and prolific ransomware-as-a-service (RaaS) operations since its appearance in July 2023. Unlike traditional ransomware groups that claim to avoid healthcare, education, and government targets, INC Ransom has systematically attacked precisely these sectors, demonstrating a complete abandonment of the informal "rules" that once governed cybercriminal behavior.
With over 200 victims posted to their leak sites in 2025 alone, and major attacks against critical infrastructure including emergency notification systems, healthcare networks serving millions, and government agencies, INC Ransom represents a new breed of financially-motivated cybercriminals for whom no target is off-limits.
Origins and Evolution
Initial Emergence (July 2023)
INC Ransom was first observed by security researchers in early August 2023, though the group likely began operations in July of that year. From the outset, the group positioned itself as a "service" to victims, claiming that by revealing their attack methods in exchange for ransom payment, they were actually improving their victims' security posture.
This cynical framing—presenting extortion as a security service—represents a new level of psychological manipulation in ransomware operations.
Rapid Growth and Expansion
By September 2023, just two months after emergence, INC Ransom had publicly announced the successful infiltration of 12 victims on their TOR-based blog. This number has since grown dramatically:
- End of 2023: Most active in December with 124 attack attempts detected by Trend Micro
- 2024: Continued aggressive expansion with major attacks on healthcare, government, and manufacturing
- 2025: Over 200 victims posted to leak sites, becoming one of the top 10 most active ransomware groups
The group's victim count represents only organizations that refused to pay ransoms—the actual number of successfully compromised organizations is likely significantly higher.

Geographic Focus
INC Ransom primarily targets organizations in:
- United States (most heavily targeted)
- United Kingdom
- Canada
- Australia
- France
- Germany
The concentration on Western countries, particularly English-speaking nations, reflects both the economic value of these targets and the operational capabilities of the group's affiliates.
Business Model: Ransomware-as-a-Service
How the RaaS Model Works
INC Ransom operates as a ransomware-as-a-service platform, where:
Core Team provides:
- Ransomware malware and encryption tools
- Leak site infrastructure and management
- Negotiation platforms and communication systems
- Technical support and operational guidance
- Payment processing infrastructure
Affiliates handle:
- Initial network compromise
- Reconnaissance and lateral movement
- Data exfiltration
- Ransomware deployment
- Direct victim negotiations
Profit Sharing: Affiliates typically receive 70-80% of ransom payments, with the core INC Ransom team taking 20-30%.

Infrastructure and Operations
INC Ransom maintains sophisticated infrastructure including:
Dual Leak Sites:
- Private Site: Requires login credentials provided to victims, serves as negotiation platform
- Public Site: Accessible to anyone, displays leaked data from victims who refused to pay
This two-tier approach maximizes pressure on victims while providing a communication channel that law enforcement cannot easily monitor.
Multiple Communication Channels:
- TOR-based negotiation portals
- Unique victim IDs assigned in ransom notes
- Direct email contact (in some cases)
- Public Twitter/X account (historically)
Target Industries and Victim Profile
Primary Targets
Unlike traditional ransomware groups that claimed to avoid certain sectors, INC Ransom aggressively targets precisely those industries previously considered "off-limits":
Healthcare (Highest priority):
- Hospitals and health systems
- Cancer treatment centers
- Medical device manufacturers
- Healthcare insurance providers
Education:
- K-12 school districts
- Universities and colleges
- Educational technology providers
Government:
- State attorney general offices
- County governments
- Federal contractors
- Emergency services infrastructure
Other Sectors:
- Manufacturing (particularly automotive)
- Financial services
- Professional services
- Technology companies
- Non-profit organizations
Why These Targets?
According to cybersecurity analyst Brian Baker: "Formerly it was considered taboo for a ransomware organization to attack and encrypt healthcare organizations. What we've seen a lot in the last year is a gradual erosion of those norms."
INC Ransom's targeting strategy reflects several factors:
- High-Value Data: Healthcare and government hold extremely sensitive personal and medical information
- Critical Operations: Downtime is extremely costly and dangerous, creating pressure to pay quickly
- Weakened Defenses: Recent law enforcement actions against major groups like LockBit shifted how some affiliates viewed targets
- Retaliation Mindset: Some researchers suggest attacks on traditionally protected sectors represent retaliation for law enforcement disruptions
Victim Selection Criteria
INC Ransom primarily focuses on:
- Small to medium enterprises (less robust security)
- Organizations with revenue of $10M+ (ability to pay significant ransoms)
- Entities with valuable data (maximum leverage for double extortion)
- Time-sensitive operations (healthcare, emergency services)
Notable Attacks and Victims
McLaren Health Care (July-August 2024)
Impact: 743,000 patients affected
Scope: 13 Michigan hospitals, Karmanos Cancer Institute
Damage:
- Three-week IT and phone system outage
- Electronic health records offline
- Cancer treatments delayed/rescheduled
- Ambulances diverted to other facilities
- Patients asked to bring physical medical records
Significance: This was McLaren's second major ransomware attack in a year (previously hit by BlackCat/ALPHV in 2023), suggesting either incomplete remediation or sophisticated re-compromise techniques.
The attack exemplifies INC Ransom's willingness to target life-critical healthcare operations. Patients undergoing cancer treatment, including chemotherapy and radiation, had appointments cancelled because doctors couldn't safely deliver therapies without comprehensive medical histories.
Pennsylvania Attorney General's Office (August 2025)
Data Stolen: 5.7 TB of files
Impact: Personal and medical information of state residents
Operational Disruption:
- Website offline
- Email systems disrupted
- Phone services interrupted
- Criminal and civil cases delayed
Bold Claims: INC Ransom claimed the breach provided access to an FBI internal network, though this has not been independently verified.
Response: Pennsylvania AG Dave Sunday confirmed the attack was ransomware and publicly stated the office would not pay the ransom. Subsequently, INC Ransom began publishing stolen documents on their leak site.
OnSolve CodeRED Emergency Alert System (November 2025)
Scale: 10,000+ municipalities nationwide
Impact:
- Two-week outage of emergency notification system
- Complete platform decommissioning required
- Potential exposure of millions of residents' contact information
- Loss of tornado warnings, evacuation orders, AMBER alerts
Significance: This represents one of the most serious attacks on public safety infrastructure in U.S. history, leaving thousands of communities unable to send emergency notifications during a critical two-week period.
Other Major Victims
Healthcare:
- NHS Scotland: Major breach of UK healthcare system
- Ahold Delhaize: Food retail giant with healthcare operations
- Multiple smaller clinics and medical practices across North America
Manufacturing:
- Yamaha Motor Philippines: 37GB of data including employee information, corporate files
- Xerox Business Solutions (XBS): U.S. division compromised
Education & Non-Profits:
- Multiple school districts
- Universities
- Charitable organizations
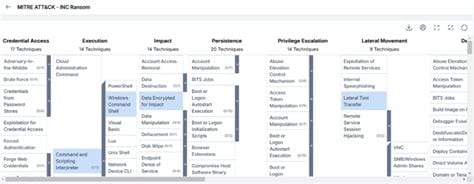
Technical Capabilities and Tactics
Initial Access Methods
INC Ransom affiliates employ multiple attack vectors:
1. Vulnerability Exploitation
Most significant: CVE-2023-3519 (Citrix NetScaler)
- Critical vulnerability in Citrix NetScaler ADC and Gateway
- Allows unauthenticated remote code execution
- Heavily exploited by INC Ransom throughout late 2023
Other exploited vulnerabilities:
- CVE-2023-48788: Fortinet EMS SQL injection
- CVE-2024-57726/57727/57728: SimpleHelp RMM vulnerabilities
- CVE-2025-5777: Citrix Bleed 2 (suspected in Pennsylvania AG breach)
2. Credential-Based Attacks
- Purchase of valid credentials from Initial Access Brokers (IABs)
- Exploitation of weak or default passwords on RDP services
- Compromise of VPN credentials
- Password reuse attacks
3. Spear-Phishing Campaigns
- Targeted emails to executives and employees
- Malicious attachments delivering credential stealers
- Links to fake login pages capturing credentials
Post-Compromise Tactics
Once inside victim networks, INC Ransom follows a methodical approach:
Reconnaissance (Hours 1-24):
- Network scanning using NETSCAN.EXE and Advanced IP Scanner
- Domain enumeration and mapping
- Identification of critical systems and data repositories
- Document inspection to verify data value
Credential Harvesting:
- Lsassy for extracting credentials from LSASS
- HackTool.PS1.VeeamCreds for Veeam backup credentials
- Native Windows tools like ESENTUTL.EXE for database access
Defense Evasion:
- HackTool.Win32.ProcTerminator.A to terminate security processes
- ProcessHacker to disable antivirus and EDR tools
- Specific targeting of TrendMicro processes and services
Lateral Movement:
- RDP (Remote Desktop Protocol) for moving between systems
- SMB file shares for propagation
- Exploitation of trust relationships between systems
Data Exfiltration (Days 1-7):
- MEGASync desktop application for cloud synchronization
- Rclone for efficient cloud storage transfers
- Staging with 7-Zip or WinRAR before exfiltration
- Typical volume: 37GB to 5.7TB per victim
Ransomware Deployment (Day 7-14):
- Multi-threaded encryption for speed
- Partial encryption strategy (faster than full file encryption)
- Deletion of Volume Shadow Copies to prevent recovery
- Termination of databases, backup services, email applications
Encryption Technology
Windows Variant:
- Algorithm: AES-128 in CTR (Counter) mode
- Key Exchange: Curve25519 Donna
- File Extension:
.inc - Ransom Notes:
INC-README.TXTandINC-README.HTML
Linux/ESXi Variant:
- Released December 2023
- Targets virtualized environments
- Scripts to terminate virtual machines before encryption
Technical Innovation:
- Multi-threading approach for rapid encryption
- Partial file encryption (encrypts portions of files for speed)
- Command-line arguments for customization
- Ability to target specific directories or network shares
Ransom Note Delivery
INC Ransom deploys ransom notes through multiple channels:
- Files in every encrypted directory
- Desktop wallpaper replacement
- Automatic printing to connected printers and fax machines
- Email notifications (in some cases)
This multi-pronged approach ensures victims cannot miss the ransom demand.
The Lynx Connection: Source Code Sale and Rebranding
The $300,000 Sale (May 2024)
In May 2024, a dramatic development emerged when a cybercriminal using the handle "salfetka" advertised the INC Ransom source code for sale on Exploit and XSS hacking forums for $300,000.
What Was Offered:
- Complete Windows ransomware source code
- Linux/ESXi variants
- Limited to only three buyers
- Technical specifications matched known INC Ransom samples
Legitimacy Indicators:
- Technical details (AES-128 CTR, Curve25519) aligned with public analysis
- "salfetka" included both old and new INC Ransom leak site URLs in forum signature
- Account had been active since March 2024, building credibility
- Previous history of seeking to purchase network access
Alternative Theory: Security researcher 3xp0rt identified "salfetka" as potentially operating under previous aliases including "rinc" and "farnetwork," suggesting a long history in ransomware operations.
Lynx Ransomware Emerges (July 2024)
Just two months after the source code sale, Lynx ransomware appeared with striking similarities to INC Ransom:
Code Overlap:
- 48% overall code similarity between Lynx and INC
- 70.8% similarity in specific shared functions
- Windows variants: Substantial overlap in encryption routines
- Linux/ESXi variants: Even greater similarity, approaching 91%
Operational Similarities:
- Nearly identical leak site design and structure
- Both operate on clear web AND TOR (rare among ransomware groups)
- Similar victim targeting patterns
- Comparable ransom demand structures
- Same technical capabilities (multi-platform support)
Key Differences:
- Lynx claims to avoid hospitals, governments, non-profits (INC makes no such claims)
- Lynx uses
.lynxfile extension (INC uses.inc) - Lynx operates more structured affiliate program with 80/20 split
- More professional branding and "ethical" positioning
Theories on the Relationship
Theory 1: Rebranding INC Ransom rebranded as Lynx to distance itself from law enforcement attention while continuing operations under a new name.
Theory 2: Sold Source Code Lynx operators purchased the INC source code and created their own variant, explaining the high code overlap.
Theory 3: Internal Split The INC operation fractured, with some members continuing as INC while others launched Lynx with modifications to the codebase.
Current Status:
- INC Ransom continues posting new victims as of November 2025
- Lynx has claimed approximately 300 victims since mid-2024
- Both groups remain actively operational
The source code sale created a proliferation risk—security researchers expect multiple new ransomware variants based on INC's code to emerge over the coming years.
Ransom Demands and Payment
Demand Structure
INC Ransom scales ransom demands based on multiple factors:
Victim Analysis:
- Annual revenue (primary factor)
- Number of employees
- Industry criticality
- Data sensitivity
- Geographic location
Typical Range: $50,000 to $5,000,000+
Payment Process:
- Victim receives ransom note with unique ID
- Accesses TOR-based payment portal
- Creates account using provided ID
- Negotiates with attackers via encrypted chat
- Pays in cryptocurrency (typically Bitcoin or Monero)
The False "Security Service" Pitch
INC Ransom's ransom notes contain a cynical twist—they frame payment as purchasing a security service:
"By paying the ransom, you'll save your reputation and we'll show you how we got in, making your environment more secure."
This positioning attempts to:
- Reframe extortion as a legitimate transaction
- Appeal to executives' desire to prevent future breaches
- Create psychological justification for paying
Reality: Paying ransoms:
- Funds continued criminal operations
- Provides no guarantee of file recovery
- Often results in re-victimization (as McLaren Health Care experienced)
- Leaves backdoors for future exploitation
Do They Keep Their Word?
On Decryption: Generally yes. Like most established ransomware groups, INC Ransom typically provides working decryption tools if paid. Not doing so would destroy their business model, as word would spread that payment doesn't result in recovery.
On Data Deletion: Much less reliable. Even after payment:
- Data may remain on threat actor systems
- Affiliates may retain copies
- Data could be sold to other criminals
- No way to verify complete deletion
Detection and Incident Response
Indicators of Compromise (IOCs)
File System:
- Files with
.incextension INC-README.TXTandINC-README.HTMLin directories- Desktop wallpaper changed to ransom note
Network Activity:
- Connections to known INC Ransom C2 servers
- Large data transfers to cloud services (MEGA, Rclone destinations)
- RDP connections from unusual sources
- SMB enumeration traffic
Process Indicators:
NETSCAN.EXEexecutionMEGAsyncSetup64.EXEinstallationProcessHackerorProcTerminatorrunning- Unusual PowerShell scripts accessing Veeam
- Mass file encryption operations
Registry Modifications:
- Changes to backup service configurations
- Disabled Windows Defender settings
- Modified boot configurations
Early Warning Signs
Organizations should watch for:
Days 1-3 (Initial Compromise):
- Failed login attempts on VPN/RDP
- New user accounts created
- Anomalous authentication from foreign IPs
- Privileged escalation attempts
Days 3-7 (Reconnaissance):
- Network scanning activity
- Access to sensitive file shares
- Database queries from unusual accounts
- Backup system access
Days 7-14 (Exfiltration):
- Large outbound data transfers
- Cloud storage tool installations
- After-hours administrative activity
- Compression of large file collections
Day 14+ (Ransomware Deployment):
- Mass file modifications
- Service terminations
- Shadow copy deletions
- Desktop wallpaper changes
- Printer activity (ransom note printing)
Defense and Mitigation Strategies
Prevention
1. Patch Management
- Prioritize patches for known INC-exploited vulnerabilities
- Implement automated patch testing and deployment
- Maintain asset inventory to ensure nothing is missed
- Pay special attention to internet-facing systems
Critical Patches:
- CVE-2023-3519 (Citrix NetScaler)
- CVE-2023-48788 (Fortinet EMS)
- CVE-2024-57727 (SimpleHelp RMM)
- CVE-2025-5777 (Citrix Bleed 2)
2. Access Control
- Multi-factor authentication (MFA) on ALL external services
- Conditional access policies based on location/device
- Privileged Access Management (PAM) solutions
- Regular credential rotation
- Password managers to prevent reuse
3. Network Segmentation
- Isolate critical systems from general network
- Separate backup infrastructure
- Restrict lateral movement pathways
- Implement zero-trust architecture principles
4. Backup Strategy
- 3-2-1 rule: 3 copies, 2 different media, 1 offsite
- Air-gapped backups that attackers cannot access
- Immutable backups that cannot be deleted/encrypted
- Regular backup testing and restoration drills
- Separate credentials for backup systems
5. Email Security
- Advanced phishing detection
- Link/attachment sandboxing
- DMARC/DKIM/SPF implementation
- Security awareness training
- Phishing simulation exercises
Detection
Endpoint Detection and Response (EDR):
- Deploy on all endpoints including servers
- Configure to detect credential dumping
- Alert on suspicious PowerShell execution
- Monitor for known INC Ransom tools
Network Detection:
- Monitor for lateral RDP connections
- Alert on large data transfers
- Detect MEGASync, Rclone installations
- Log and analyze SMB traffic
SIEM Implementation:
- Centralized log aggregation
- Correlation rules for ransomware IOCs
- Anomaly detection for user behavior
- Automated threat hunting
Specific Detection Rules:
- File system monitoring for mass encryption
- Registry changes to security software
- Volume Shadow Copy deletions
- Unusual backup system access
Response
Immediate Actions (Minutes):
- Isolate infected systems from network
- Preserve evidence (don't reboot or power off)
- Assess scope of compromise
- Notify leadership and legal counsel
- Engage incident response team
Short-term Actions (Hours):
- Identify patient zero and attack vector
- Contain spread by segmenting networks
- Eradicate attacker access and tools
- Inventory encrypted systems and data
- Evaluate backup integrity and recoverability
Recovery Actions (Days):
- Rebuild systems from clean images
- Restore data from backups
- Change all credentials
- Patch exploited vulnerabilities
- Monitor for re-infection attempts
DON'T:
- Pay ransom without exhausting all alternatives
- Delete logs or evidence
- Communicate about incident on compromised systems
- Assume attackers are gone after ransomware deployment
The Bigger Picture: What INC Ransom Represents
The Erosion of Cybercriminal "Ethics"
For years, major ransomware groups like LockBit and BlackCat/ALPHV publicly claimed they prohibited affiliates from attacking:
- Hospitals and healthcare facilities
- Schools and educational institutions
- Government agencies
- Non-profit organizations
- Critical infrastructure
These groups would occasionally "punish" affiliates who violated these rules, kick them out of affiliate programs, or even provide free decryption keys to affected organizations.
INC Ransom changed the calculus.
The group demonstrated that:
- There are no consequences for attacking "protected" targets
- Healthcare and government often pay quickly due to operational criticality
- Law enforcement disruptions of major groups created opportunities for more aggressive operators
- The financial incentives vastly outweigh any ethical considerations
As security researcher Brian Baker noted: "Recent disruptions really ticked off a lot of the big players — whether it be Operation Cronos with LockBit, or AlphV taking the bag and running with their exit scam. It really shifted how some people looked at victims."
Impact on Critical Infrastructure
INC Ransom's attacks demonstrate the fragility of critical infrastructure:
Healthcare:
- 743,000 McLaren Health Care patients affected
- Cancer treatments delayed
- Emergency room diversions
- Patient safety compromised
Emergency Services:
- 10,000+ municipalities lost emergency notifications
- Two-week outage during severe weather season
- No AMBER alerts, tornado warnings, evacuation orders
Government:
- State operations disrupted for weeks
- Criminal and civil cases delayed
- Public services interrupted
- Sensitive data exposed
The Ransomware-as-a-Service Economy
INC Ransom exemplifies the professionalization of cybercrime:
Specialized Roles:
- Core development teams
- Affiliate operators
- Initial access brokers
- Negotiation specialists
- Money laundering services
Professional Infrastructure:
- Customer support for victims
- Encrypted communication platforms
- Sophisticated leak sites
- Payment processing systems
Market Dynamics:
- Source code sales ($300K for INC)
- Network access marketplace ($7K+ per access)
- Profit sharing agreements (70-80% to affiliates)
- "Re-victimization" of previously compromised organizations
Law Enforcement Challenges
INC Ransom operates in ways that frustrate law enforcement:
Geographic Distribution:
- Core team likely in Russia/Eastern Europe
- Affiliates worldwide
- Cryptocurrency payment obscures money trail
- TOR/encrypted communications
Operational Security:
- No physical infrastructure to seize
- Encrypted communications
- Compartmentalized operations
- Rapid adaptation to disruptions
Legal Challenges:
- Jurisdictional issues
- Attribution difficulties
- Lack of international cooperation
- Minimal consequences in some countries
Future Outlook
Short-Term Predictions (6-12 Months)
- Continued Proliferation: The source code sale will likely spawn multiple new INC-based ransomware variants
- Increased Healthcare Targeting: Success against McLaren and other healthcare entities will encourage more attacks
- Critical Infrastructure Focus: Groups will increasingly target emergency services, utilities, transportation
- Sophistication Increases: Integration of AI, improved evasion techniques, faster encryption
Medium-Term Trends (1-3 Years)
- Consolidation: Some smaller groups will merge or be absorbed by larger operations
- Specialization: Groups may focus on specific industries or attack types
- Law Enforcement Pressure: Increased disruptions like Operation Cronos against LockBit
- Defensive Improvements: Better EDR, mandatory ransomware insurance requirements, improved backup strategies
Long-Term Concerns (3-5 Years)
- AI-Enhanced Attacks: Automated reconnaissance, adaptive evasion, AI-generated phishing
- Supply Chain Focus: More attacks targeting IT service providers and software vendors
- OT/ICS Targeting: Operational technology in manufacturing, utilities, critical infrastructure
- Legislative Response: Potential ransom payment bans, mandatory reporting, stricter regulations
Conclusion
INC Ransom represents a disturbing evolution in ransomware operations—a group that has completely abandoned any pretense of ethical boundaries, systematically targets the most vulnerable sectors of society, and demonstrates sophisticated technical capabilities combined with ruthless business acumen.
Their attacks on healthcare facilities endanger patients receiving life-critical care. Their compromise of emergency notification systems leaves millions without warnings of tornadoes, evacuations, or AMBER alerts. Their breaches of government agencies expose sensitive data and disrupt essential public services.
The group's success, measured by hundreds of victims and millions in ransom payments, sends a clear signal to other cybercriminal organizations: there are no consequences for attacking previously "protected" targets, and the financial rewards for doing so are substantial.
Key Takeaways for Organizations:
- No Sector Is Safe: If your organization has valuable data or critical operations, you are a potential target
- Healthcare Is Primary Target: Medical facilities face the highest risk and should implement maximum security measures
- Vulnerability Exploitation Is Primary Vector: Patching internet-facing systems is absolutely critical
- Backup Security Is Essential: Attackers specifically target backup systems—air-gapped, immutable backups are mandatory
- Detection Matters: Early detection during reconnaissance phase (days 1-7) is key to preventing ransomware deployment
- Incident Response Plans: Test your plans regularly; when ransomware hits, every minute counts
For Policymakers and Law Enforcement:
- Increased Resources: Ransomware investigations require specialized expertise and international cooperation
- Swift Action: The window between compromise and encryption is often less than two weeks
- Collaboration: Public-private partnerships are essential for threat intelligence sharing
- Consequences: Host countries must face diplomatic pressure for harboring ransomware operators
The Bottom Line
INC Ransom will not be the last ransomware group to abandon ethical boundaries in pursuit of profit. As long as ransomware remains highly profitable and consequences remain minimal, organizations must assume they will be targeted and prepare accordingly.
The question is no longer "if" your organization will face a ransomware attack, but "when"—and whether you'll be prepared to respond effectively without paying criminals who fund their operations by attacking hospitals, emergency services, and other critical infrastructure.
Indicators of Compromise (IOCs)
File Extensions
.inc(encrypted files)
Ransom Note Files
INC-README.TXTINC-README.HTML
Known Tools Used
NETSCAN.EXEMEGAsyncSetup64.EXEESENTUTL.EXEHackTool.Win32.ProcTerminator.AHackTool.PS1.VeeamCredsProcessHackerlsassy7-Zip/WinRARRclone
Email Addresses (Historical)
- gansbronz[at]gmail[.]com (also used by Lynx)
Exploited Vulnerabilities
- CVE-2023-3519 (Citrix NetScaler)
- CVE-2023-48788 (Fortinet EMS)
- CVE-2024-57726/57727/57728 (SimpleHelp RMM)
- CVE-2025-5777 (Citrix Bleed 2)
Resources and Further Reading
Threat Intelligence Reports:
- MITRE ATT&CK: INC Ransom (Group G1032)
- Trend Micro: Ransomware Spotlight INC
- Cybereason: Threat Alert INC Ransomware
- Palo Alto Unit 42: Lynx Ransomware Rebrand Analysis
- MOXFIVE: Threat Actor Spotlight INC Ransom
Related Articles:
- America's 911 Systems Under Siege: The Growing Cyber Threat to Emergency Services
- Nationwide CodeRED Emergency Alert System Compromised: INC Ransom Attack
- The Cyber Siege: How Ransomware is Crippling America's Cities and Towns
Cybersecurity Frameworks:
- NIST Cybersecurity Framework
- CIS Critical Security Controls
- MITRE ATT&CK Framework
- CISA Ransomware Guide
Disclosure: This analysis is provided for informational and educational purposes only. It does not constitute legal, regulatory, or professional advice. Organizations facing ransomware incidents should immediately engage qualified cybersecurity professionals and legal counsel. The author does not endorse or recommend paying ransoms to criminal organizations.







