Inside Microsoft's Global Operation to Disrupt Lumma Stealer's 2,300-Domain Malware Network

Bottom Line Up Front: Microsoft's Digital Crimes Unit led a groundbreaking international operation that seized 2,300 malicious domains and disrupted one of the world's largest infostealer malware operations, protecting nearly 400,000 victims and demonstrating how creative legal strategies combined with global partnerships can effectively combat cybercrime-as-a-service.
In a recent episode of the Microsoft Threat Intelligence Podcast, host Sherrod DeGrippo sat down with Richard Boscovich and Derek Richardson from Microsoft's Digital Crimes Unit (DCU) to unpack one of the most significant cybercrime takedowns of 2025: the disruption of Lumma Stealer, a malware-as-a-service operation that had infected hundreds of thousands of computers worldwide.
The Threat: Lumma Stealer's Global Impact
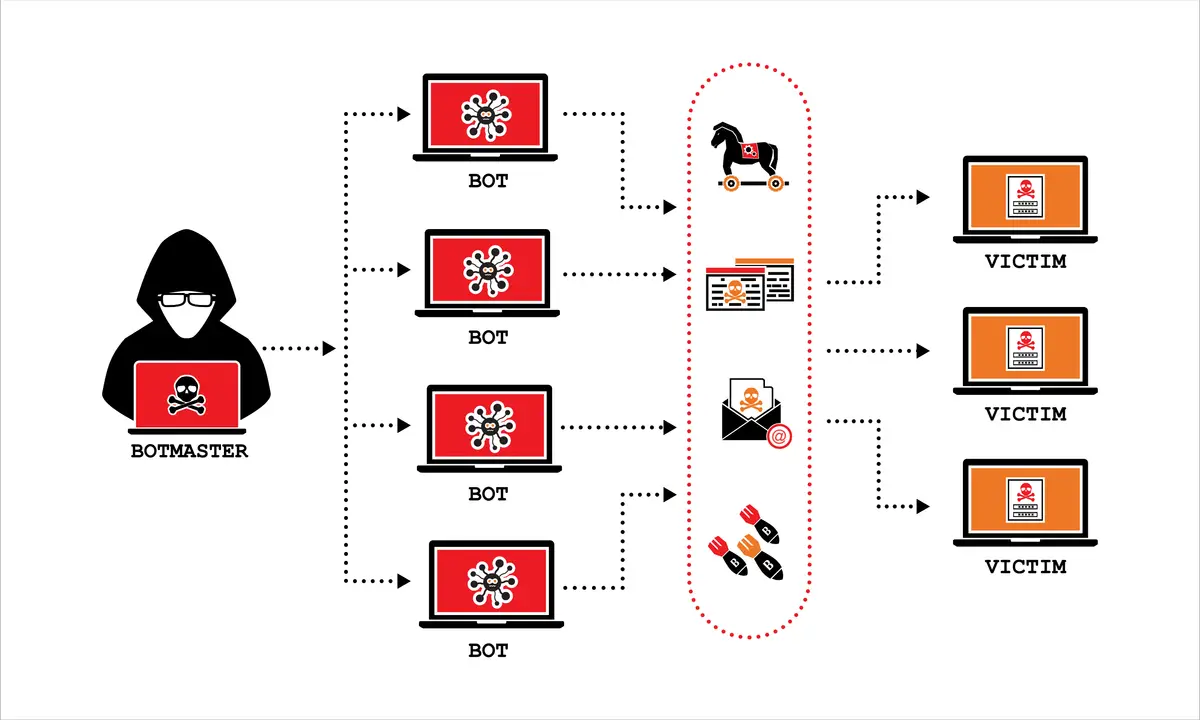
Lumma Stealer, also known as LummaC2, emerged as one of the most prolific infostealer malware families, operating under a malware-as-a-service model that made it accessible to hundreds of cybercriminals worldwide. Between March 16 and May 16, 2025, Microsoft identified more than 394,000 Windows computers infected with Lumma, while the FBI estimates that Lumma has been involved in around 10 million infections globally.
The malware's sophistication and ease of use made it "a go-to tool for cybercriminals and online threat actors, including prolific ransomware actors such as Octo Tempest (Scattered Spider)". Lumma Stealer leverages a broad and evolving set of delivery vectors, including phishing emails, malvertising, abuse of trusted platforms, and traffic distribution systems.

Real-World Impact
The podcast revealed the devastating real-world consequences of Lumma's operations. Lumma steals passwords, credit cards, bank accounts, and cryptocurrency wallets and has enabled criminals to hold schools for ransom, empty bank accounts, and disrupt critical services. The malware was particularly effective because it could impersonate trusted brands, including Microsoft, and is deployed via spear-phishing emails and malvertising.
One example highlighted in the research was a March 2025 phishing campaign where Microsoft Threat Intelligence identified a campaign impersonating online travel agency Booking.com, using multiple credential-stealing malware, including Lumma, to conduct financial fraud and theft.
The Operation: Creative Legal Strategies Meet Global Cooperation
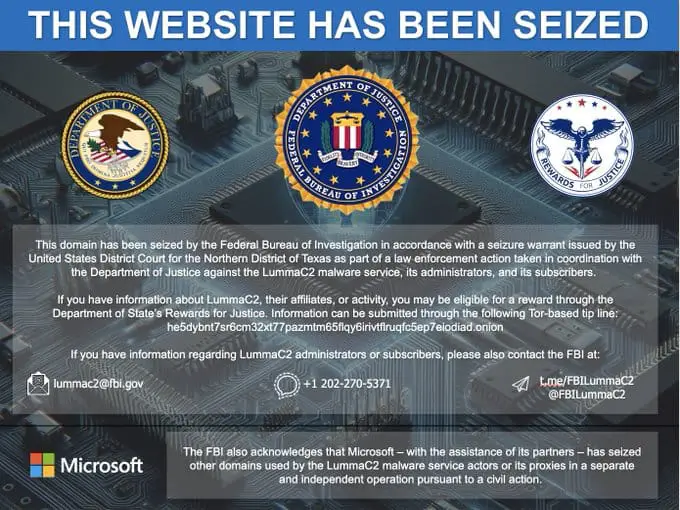
The takedown operation, announced on May 21, 2025, showcased the DCU's innovative approach to combating cybercrime. Via a court order granted in the United States District Court of the Northern District of Georgia, Microsoft's DCU seized and facilitated the takedown, suspension, and blocking of approximately 2,300 malicious domains that formed the backbone of Lumma's infrastructure.
Legal Innovation: From RICO to Centuries-Old Trespass Laws
As discussed in the podcast, the DCU employed creative legal tools that push the boundaries of traditional cybercrime prosecution. The DCU uses "trespass to chattel," a legal concept rooted in old English common law where chattel referred to cattle, one of the most valuable forms of property centuries ago. Today, computers and data are considered chattel, making malware intrusion a form of trespass.
Microsoft has also leveraged the Racketeer Influenced and Corrupt Organizations Act (RICO), the Computer Fraud and Abuse Act, and the Digital Millennium Copyright Act in their legal actions against cybercriminals. As Richard Boscovich noted in previous interviews, "They were basic, common law principles – well, maybe one or two modern laws – used in a totally unique way to address a 21st century problem".
Global Partnership Network
The operation demonstrated unprecedented international cooperation. The Department of Justice (DOJ) simultaneously seized the central command structure for Lumma and disrupted the marketplaces where the tool was sold to other cybercriminals. Europol's European Cybercrime Center and Japan's Cybercrime Control Center worked to suspend locally based infrastructure, while cybersecurity and tech companies ESET, Bitsight, Lumen, Cloudflare, CleanDNS and GMO Registry assisted with the takedown effort.
Technical Innovation: Sinkholing and Intelligence Gathering
The DCU's technical approach was equally sophisticated. Hundreds of the nearly 2,300 seized Lumma domains will be redirected back to "sinkholes" so the infrastructure can be further studied. By redirecting the seized domains to Microsoft-controlled sinkholes, investigators can now monitor ongoing attacks and provide intelligence to help defend against similar threats in the future.
This approach serves multiple purposes: Civil court orders allow us to sever or disrupt malware communication, redirecting infected devices to our Cyber Threat Intelligence Program (CTIP) sinkhole service. This service shares cyber intelligence with Computer Emergency Response Teams (CERTs), Internet Service Providers (ISPs), and Critical Infrastructure Information Sharing and Analysis Centers (ISACs).

The Adversary: Understanding the Criminal Enterprise
The podcast provided insights into the criminal enterprise behind Lumma. The primary developer of Lumma is based in Russia and goes by the internet alias 'Shamel'. Shamel markets different tiers of service for Lumma via Telegram and other Russian-language chat forums. In an interview conducted in November 2023, Shamel claimed he had "about 400 active clients".
Demonstrating the evolution of cybercrime to incorporate established business practices, he effectively created a Lumma brand, using a distinctive logo of a bird to market his product, calling it a symbol of "peace, lightness, and tranquility," and adding the slogan "making money with us is just as easy".
The Shift Toward Persistent Disruption
One of the key themes explored in the podcast was the DCU's evolution toward sustained campaigns rather than one-time takedowns. The DCU's enforcement actions are not one-time takedowns—they are often sustained campaigns. By securing court-appointed monitors and automated monitoring and detection, the DCU continuously tracks and disrupts reemerging threats.
As anticipated, investigators have already observed the threat actor attempt to rebuild their infrastructure. However, with a court order and because of close coordination with partners, they're able to immediately dismantle new infrastructure as it is established.
Cost-Imposing Strategy
The podcast emphasized how the operation was designed to impose significant costs on cybercriminals. "This joint action is designed to slow the speed at which these actors can launch their attacks, minimize the effectiveness of their campaigns, and hinder their illicit profits by cutting a major revenue stream," said Steven Masada, assistant general counsel in Microsoft's Digital Crimes Unit.
Disrupting the tools cybercriminals frequently use can create a significant and lasting impact on cybercrime, as rebuilding malicious infrastructure and sourcing new exploit tools takes time and costs money.
The Broader DCU Mission
The Lumma takedown represents just one example of the DCU's comprehensive approach to cybercrime. Over the course of our history the DCU has disrupted 30 malware families, nation-state threat actors, and distributors of malicious tools through civil actions, rescuing over 500 million victim devices. Our collaboration with law enforcement has led to over 780 arrests since 2014.
In 2024, we seized 453 domains used by cybercriminals and nation-state threat actors for malicious purposes and contributed to 85 arrests globally.

Lessons for Defenders
The podcast highlighted several key takeaways for cybersecurity professionals:
Multi-layered Defense: Microsoft Threat Intelligence recommends strengthening Microsoft Defender for Endpoint configuration, ensuring tamper protection is enabled, enabling network protection, turning on web protection, and running endpoint detection and response (EDR) in block mode.
User Education: Microsoft says computer users should protect themselves from malware like Lumma by turning on multi-factor authentication, keeping antivirus software up to date, and being careful with email links and attachments.
Industry Collaboration: The operation demonstrated that even with the Lumma infrastructure disrupted, the threat of information stealers remains very real and evolving, requiring continued cooperation between private industry, law enforcement, and international partners.
Looking Forward: The Future of Cybercrime Disruption
As discussed in the podcast, the DCU is increasingly leveraging new technologies to stay ahead of evolving threats. The DCU is continually evolving to address emerging threats, adapting our expertise and our tools to combat ever evolving malware and ransomware variants, state-affiliated actors, cryptocurrency-related crimes, digital fraud, and AI abuse. Increasingly we are leveraging new technologies like AI to enhance our investigations and proactively identify new threats and vulnerabilities.
The Lumma Stealer takedown represents a significant milestone in the fight against cybercrime-as-a-service, demonstrating how creative legal strategies, international cooperation, and technical innovation can effectively disrupt even the most sophisticated criminal enterprises. As cybercriminals continue to evolve their tactics, operations like this provide a blueprint for defenders to impose meaningful costs and consequences on those who would exploit our digital infrastructure.
Key Takeaway: The success of the Lumma Stealer disruption shows that persistent, coordinated action by public-private partnerships can significantly impact cybercrime operations, but requires sustained effort and continued innovation to stay ahead of adaptable adversaries.













