Israeli Defense Contractor Maya Suffers Devastating Breach: 18 Months of Surveillance Exposed

Critical Infrastructure Alert: Iranian-linked threat actors demonstrate unprecedented access to sensitive defense systems
Executive Summary
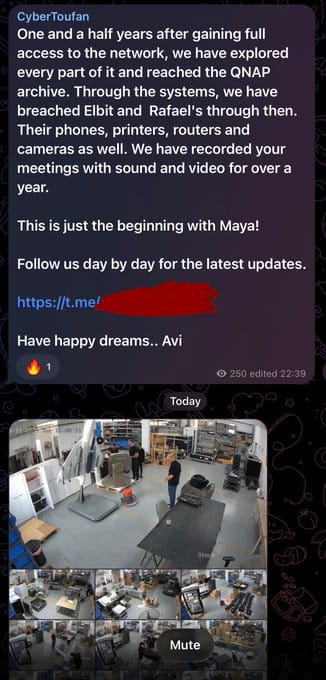
A sophisticated cyber operation targeting Israeli defense contractor Maya has exposed classified weapons development programs, including surveillance camera footage from meeting rooms and workshops captured over an 18-month period. The breach, attributed to the Cyber Support Front (al-Jabha al-Isnad al-Sayberaniyah), has compromised highly sensitive data on advanced defense systems including the Iron Beam laser defense system, David's Sling missile interceptors, and multiple drone and missile programs.
The incident represents one of the most significant defense industrial base compromises in recent years, combining physical surveillance, network infiltration, and supply chain compromise to devastating effect. This breach occurs amid a 126% surge in ransomware incidents and unprecedented cyber threats throughout 2025, with nation-state actors increasingly targeting critical infrastructure and defense sectors.








Attack Overview
Initial Compromise and Persistence
According to threat actor statements, they gained full network access to Maya approximately 18 months ago and systematically explored every component of the infrastructure before reaching the QNAP archive system. The extended dwell time allowed the attackers to:
- Map the complete network topology
- Identify high-value data repositories
- Compromise connected security infrastructure
- Establish persistent surveillance capabilities
- Exfiltrate massive volumes of sensitive data
Surveillance Infrastructure Compromise
The most alarming aspect of this breach involves the complete compromise of Maya's physical security systems. The threat actors released security camera footage from internal facilities, including meeting rooms and workshops, capturing confidential discussions and weapons assembly processes.
The leaked footage reportedly shows:
- Meeting Room Surveillance: Hours of recordings capturing confidential discussions about defense projects, specifications, and strategic planning
- Workshop Operations: Detailed visual documentation of weapons prototypes and assembly processes
- Weapons Systems: Clear imagery of drone components, missile systems, tracking equipment, and launching mechanisms
- 3D Printing Operations: Manufacturing processes for specialized components
Among the compromised projects was David's Sling, an Israel Defense Forces missile defense system jointly developed by Rafael Advanced Defense Systems and Raytheon, which became operational in 2017 and is designed to intercept tactical ballistic missiles, medium-to-long-range rockets, and cruise missiles at ranges from 40 to 300 km.
🚨‼️ Israeli defense contractor breached
— International Cyber Digest (@IntCyberDigest) October 30, 2025
Cyber Toufan, allegedly an Iranian state actor, just released security cam footage of defense contractor Maya. The cameras seem located in a meeting room (!) and a workshop.
There are hours of footage of confidential conversations in the… pic.twitter.com/aoDNJT8axz
Compromised Systems and Data
Critical Defense Programs Exposed
The breach exposed classified information on multiple high-profile Israeli weapons systems including the Iron Beam laser air defense system, Skylark reconnaissance drone, Spyder air defense system, and Ice Breaker stealth cruise missile.
Iron Beam Laser Defense System: Advanced directed-energy weapon designed to intercept short-range threats
David's Sling: Mid-tier missile defense system with 40-300km interception range
Hermes-900 UAV: Multi-purpose reconnaissance and strike drone platform
Spike Missile System: Precision-guided anti-tank missile with multiple variants
Skylark Reconnaissance Drone: Tactical surveillance platform
Spyder Air Defense System: Mobile surface-to-air missile system
Ice Breaker Stealth Cruise Missile: Advanced precision strike weapon
M-113 APC Upgrades: Enhanced armored personnel carrier modifications
Supply Chain Implications
Maya serves as a research and development contractor for major Israeli defense industries including Elbit Systems and Rafael Advanced Defense Systems. The threat actors claim to have breached Elbit and Rafael networks through Maya's compromised systems, accessing:
- Corporate phones and communication systems
- Network printers and attached storage
- Routers and network infrastructure
- Internal security cameras across multiple facilities
The leaked materials included images of joint defense contracts between Israel and partners in Australia and several European countries, potentially compromising international defense cooperation arrangements.
Technical Attack Methodology
QNAP Network Storage Exploitation
The attackers specifically mention accessing the "QNAP archive" as a critical milestone in their operation. QNAP network-attached storage devices have been plagued by numerous vulnerabilities throughout 2024-2025, with multiple critical security flaws allowing unauthenticated access and remote code execution.
Critical vulnerabilities in QNAP systems include CVE-2024-21899, an improper authentication issue with a CVSS score of 9.8 that could allow users to compromise the security of the system via a network. Organizations using QNAP devices for archival storage of sensitive defense data face significant risks if systems are not properly secured and patched.
Security Camera Infrastructure Vulnerabilities
Surveillance cameras have increasingly become targets for Iranian cyber operations, with Israeli officials confirming that CCTV systems are being exploited to gather intelligence. Exposed IP cameras allow threat actors to view live feeds, record footage for reconnaissance, and potentially use compromised cameras as pivot points to penetrate connected networks.
Previous incidents involved Iranian groups like Moses Staff publishing footage from Israeli security cameras, including images from Rafael defense contractor facilities and Jerusalem terror attacks, with Israeli authorities aware of the compromise for over a year before taking action.
Threat Actor Attribution
Cyber Support Front / Cyber Toufan Connection
The operation is claimed by both "Cyber Support Front" and references "Cyber Toufan," suggesting coordination between Iranian-linked threat groups. Cybersecurity researchers assess Cyber Toufan as a sophisticated, potentially state-sponsored entity, with rapid rise and effective execution of complex cyberattacks suggesting support and resources not typically available to independent hacker collectives.
Check Point identified Cyber Toufan as an Iranian threat actor, while cybersecurity companies noted the group's tactics and scale bear hallmarks of state sponsorship, with Iranian-affiliated groups like CyberAv3ngers and Cyber Toufan adopting strategies of dual retaliation against both Israel and U.S. entities.
Operational Patterns and TTPs
Security researchers identify Cyber Toufan as operating under IRGC contractor Emennet Pasargad, which has used various personas including Yare Gomnam Cyber Team and al Toufan Team. These "faketivists" adopt hacktivist aesthetics and rhetoric while conducting sophisticated intelligence operations aligned with Iranian state interests.
Unlike financially-motivated threat actors, the group is driven by ideological and political motives, with operations designed to destabilize targeted organizations, erode public trust, and inflict reputational and operational harm. Their campaigns typically culminate in public data releases via Telegram channels timed to maximize media attention and strategic impact.
Cyber Toufan emerged in November 2023, claiming to have destroyed over 1,000 servers and critical databases. The group initially compromised hosting company Signature-IT to gain access to dozens of high-profile Israeli organizations, releasing large SQL database files containing millions of user records.
Impact Assessment
National Security Implications
The breadth and depth of this compromise creates multiple severe consequences:
Weapons System Compromise: Detailed technical specifications and blueprints for active defense systems are now potentially in adversary hands, enabling development of countermeasures and identification of system vulnerabilities.
Operational Security Failure: 18 months of meeting recordings expose strategic planning, procurement decisions, capability assessments, and operational limitations.
Personnel Exposure: The Cyber Support Front published personal details of Maya employees who have access to secret military projects, with the group suggesting Israeli forces might resort to Operation Hannibal protocols in response to the exposure. This breach follows Microsoft's controversial termination of Azure access for Israeli military intelligence Unit 8200 over mass surveillance concerns, highlighting broader scrutiny of Israeli intelligence operations.
International Cooperation Risk: Exposure of joint development programs with Australia and European partners may damage trust in Israeli defense cooperation and information security.
Supply Chain Contamination: Compromise of Maya enabled lateral movement into Rafael and Elbit Systems, demonstrating cascading effects throughout the defense industrial base.
Economic and Strategic Costs
Competitive Intelligence Loss: Years of research and development investment compromised, potentially benefiting competitor nations and reducing technological advantages.
Contract Implications: International partners may reconsider procurement decisions based on demonstrated security vulnerabilities in Israeli defense supply chains.
Remediation Expenses: Complete network rebuilds, security infrastructure replacement, and enhanced monitoring will require massive investment across multiple organizations.
Historical Context: Escalating Cyber Operations
This incident follows previous Iranian operations where Moses Staff hacked Israeli CCTV cameras at defense facilities and published footage of terror attacks, with Israeli security establishment aware of the breaches for over a year but failing to take preventive action.
Following the October 7, 2023 attacks, Iranian-affiliated groups intensified operations against Israeli targets, with Check Point noting an 18% rise in cyberattacks and groups like CyberAv3ngers and Cyber Toufan targeting both Israeli infrastructure and U.S. entities using Israeli technology. This breach represents the latest chapter in an ongoing cyber proxy war between Israel and Iran, where dozens of hacktivist groups serve as digital proxies for both nations.
Iranian cyber actors have demonstrated persistent targeting of critical infrastructure networks across multiple sectors globally, employing brute force attacks, password spraying, and MFA push bombing techniques to penetrate organizations. The National Security Agency has issued multiple warnings about Iranian threat actor operations throughout 2024-2025.
The escalation demonstrates increasingly sophisticated Iranian cyber capabilities, moving from website defacements and DDoS attacks to sustained espionage operations with devastating intelligence collection outcomes. Iran has also faced significant cyber retaliation, with coordinated attacks disrupting Iran's maritime shadow fleet operations that generate an estimated $70 billion annually in oil revenues.
Security Recommendations
For Defense Industrial Base Organizations
Network Segmentation: Implement strict network isolation between operational technology, business systems, and security infrastructure to prevent lateral movement.
Security Camera Isolation: Place all IP-based surveillance systems on dedicated VLANs with no direct internet exposure and strict access controls. Regularly audit camera firmware and disable unnecessary network features.
NAS Security Hardening:
- Disable default credentials and enforce strong authentication
- Implement network-level access controls restricting NAS access to authorized systems only
- Enable comprehensive logging with off-device retention
- Deploy intrusion detection signatures specifically monitoring for NAS exploitation
- Maintain aggressive patch management for storage appliances
Physical Security Integration: Recognize that physical security systems (cameras, access controls, sensors) are now high-value cyber targets requiring equivalent cybersecurity rigor as IT infrastructure.
Supply Chain Security: Implement vendor security requirements and continuous monitoring for third-party access to sensitive systems and data.
For Organizations Using QNAP Devices
Given QNAP's history of critical vulnerabilities including CVE-2024-27130 and CVE-2024-21899, organizations should immediately audit all QNAP deployments, ensure current firmware, implement network access controls, and consider migration to enterprise storage solutions with stronger security postures.
Immediate Actions:
- Inventory all QNAP devices and verify firmware versions
- Disable external access and implement VPN-only connectivity
- Enable multi-factor authentication for all accounts
- Review and restrict file sharing configurations
- Implement comprehensive monitoring and alerting
- Conduct security assessments on stored data sensitivity
Detection and Monitoring
Indicators of Compromise:
- Unauthorized access to security camera management interfaces
- Anomalous network traffic from surveillance systems
- Unexpected authentication attempts against NAS devices
- Large data transfers from archive systems
- Access to QNAP systems from unusual geographic locations
- Modified security camera configurations or firmware
Continuous Monitoring Requirements:
- Centralized logging from all security infrastructure
- Network traffic analysis for unusual patterns
- User behavior analytics to detect credential compromise
- Regular review of access logs from sensitive systems
- Threat intelligence integration for known Iranian TTPs
Ongoing Threat
The threat actors stated: "This is just the beginning with Maya! Follow us day by day for the latest updates." This suggests additional data releases are planned, potentially including more sensitive operational details, additional surveillance footage, or information on connected organizations.
The group has demonstrated a pattern of sustained campaigns, with Cyber Toufan stating that "as long as our brothers keep striking the occupying forces on the ground, we'll continue targeting them and their interests in the cyber domain, whether publicly or without a trace".
Organizations within the Israeli defense industrial base and international partners should anticipate continued targeting and additional disclosures from this operation.
Conclusion
The Maya defense contractor breach represents a catastrophic failure of cybersecurity across multiple dimensions: network security, physical security system protection, supply chain risk management, and third-party vendor oversight. The 18-month dwell time enabled comprehensive intelligence collection that will have lasting impacts on Israeli defense capabilities and strategic planning.
This incident serves as a stark warning to defense contractors globally: security camera systems, network storage devices, and interconnected facilities represent critical attack surfaces that require the same rigorous security controls as traditional IT infrastructure. The days of treating physical security systems as isolated operational technology are over—these systems must be secured as critical cyber assets.
For organizations in the defense industrial base, the lessons are clear: implement defense-in-depth, continuously monitor for compromise indicators, maintain aggressive vulnerability management, and recognize that nation-state adversaries are investing heavily in long-term intelligence operations targeting every aspect of defense infrastructure.
Additional Resources
QNAP Security Advisories: https://www.qnap.com/en-us/security-advisories
CISA Security Camera Guidance: Review federal guidance on securing IP-based surveillance systems
Supply Chain Risk Management: NIST SP 800-161 for cybersecurity supply chain risk management
Israeli INCD Alerts: Monitor Israel National Cyber Directorate for defense sector advisories
This analysis is based on publicly available information, information released from the threat actor on telegram, and open-source intelligence. Organizations should conduct their own security assessments and not rely solely on threat actor claims when evaluating exposure.
Published by breached.company - Your source for breach intelligence and cybersecurity analysis





