Justice Department Disrupts Major Malware Operation: The LummaC2 Takedown
A Coordinated Strike Against Cybercrime Infrastructure
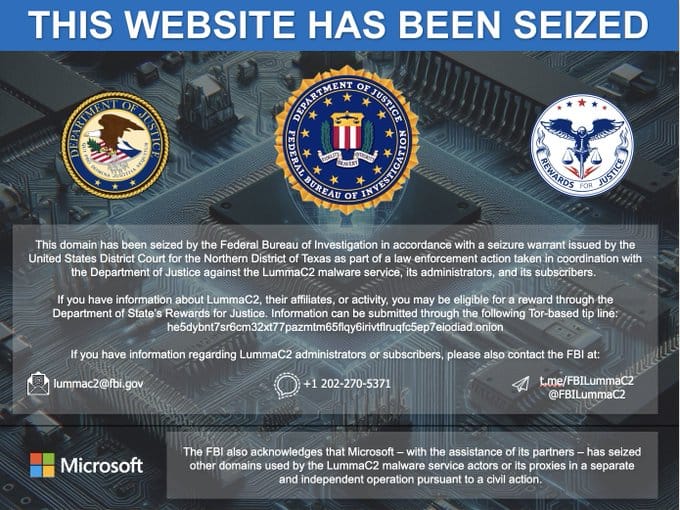
On May 21, 2025, the U.S. Department of Justice announced a significant victory in the ongoing battle against cybercrime: the successful disruption of LummaC2, one of the most prolific information-stealing malware operations targeting millions of victims worldwide. Through a coordinated effort involving federal law enforcement and private sector partnerships, authorities seized five critical internet domains and effectively dismantled the infrastructure that enabled this sophisticated criminal enterprise.

Understanding the LummaC2 Threat
LummaC2 represents a particularly dangerous category of malware known as "infostealers" – malicious software designed specifically to harvest sensitive personal and financial information from infected computers. Unlike ransomware that locks systems for money, infostealers operate more insidiously, silently extracting valuable data that can be sold on criminal marketplaces or used directly for fraud.
The malware's primary targets include:
Browser Data and Credentials: LummaC2 systematically harvests saved passwords, autofill information, and login credentials stored in web browsers. This includes access to email accounts, social media platforms, and critically, online banking services.
Financial Information: Beyond traditional banking credentials, the malware specifically targets cryptocurrency-related data, including seed phrases and wallet information. In an era where digital assets represent significant wealth, this capability makes LummaC2 particularly lucrative for cybercriminals.
Personal Information: The malware collects comprehensive personal data that can be used for identity theft, social engineering attacks, or sold to other criminal actors.
The Scale of the Operation
The scope of LummaC2's impact is staggering. According to FBI affidavits filed in support of the seizure warrants, investigators identified at least 1.7 million instances where the malware successfully stole victim information. This figure likely represents only a fraction of the actual damage, as it reflects documented cases where the malware successfully exfiltrated data.
The operation functioned as a "malware-as-a-service" (MaaS) model, where the LummaC2 administrators provided the malware and supporting infrastructure to affiliated cybercriminals. This business model has become increasingly common in the cybercrime ecosystem, allowing technical experts to focus on developing sophisticated malware while enabling less technically skilled criminals to deploy it at scale.
The Technical Takedown
The Justice Department's operation targeted the critical infrastructure that made LummaC2 functional. The seized domains served as "user panels" – essentially the control centers where criminals could:
- Access and deploy the malware
- Monitor infection campaigns
- Retrieve stolen data
- Manage their criminal operations
The seizure occurred in two phases, demonstrating the adaptability required in modern cybercrime investigations:
Phase 1 (May 19, 2025): Authorities seized two initial domains used by the operation.
Phase 2 (May 21, 2025): When LummaC2 administrators quickly established three replacement domains and informed their users, law enforcement was ready. Within 24 hours, these new domains were also seized, effectively cutting off the criminals' ability to operate.
This rapid response capability highlights the sophisticated intelligence gathering and coordination required for successful cybercrime disruption operations.
Public-Private Partnership in Action
The LummaC2 takedown exemplifies the evolving model of cybersecurity cooperation between government and private sector entities. Concurrent with the Justice Department's action, Microsoft announced its own independent civil action targeting an additional 2,300 internet domains associated with the LummaC2 operation.
This parallel approach leverages the unique capabilities of both sectors:
Government Authority: The Justice Department's seizure warrants provide legal authority to disrupt criminal infrastructure and gather evidence for potential prosecutions.
Private Sector Agility: Microsoft's civil action allows for broader domain takedowns that might not meet the threshold for criminal warrants but still serve to disrupt criminal operations.
Sue J. Bai, head of the Justice Department's National Security Division, emphasized this collaborative approach: "Today's disruption is another instance where our prosecutors, agents, and private sector partners came together to protect us from the persistent cybersecurity threats targeting our country."
Broader Implications for Cybersecurity
The LummaC2 takedown represents more than just the disruption of a single criminal operation. It signals several important developments in the cybersecurity landscape:
Operational Sophistication: The rapid response to the criminals' attempt to establish new domains demonstrates that law enforcement has developed the intelligence capabilities and operational flexibility needed to counter adaptive cybercriminal organizations.
International Cooperation: While the press release doesn't detail international partnerships, operations of this scale typically require coordination with foreign law enforcement agencies, suggesting continued development of international cybercrime cooperation frameworks.
Deterrent Effect: Public announcements of successful takedowns serve as important deterrents to other cybercriminals, demonstrating that law enforcement can and will disrupt even sophisticated operations.
The Ongoing Challenge
Despite this success, the LummaC2 takedown also highlights the persistent nature of the cybercrime threat. Information-stealing malware remains one of the most significant threats to individual and organizational cybersecurity for several reasons:
Low Barrier to Entry: The malware-as-a-service model means that individuals with limited technical skills can still deploy sophisticated malware.
High Profitability: Stolen credentials and financial information command high prices on criminal marketplaces, making these operations extremely lucrative.
Difficult Detection: Unlike ransomware, infostealers operate silently, often going undetected for extended periods while continuously harvesting data.
Rewards and Reporting
The Justice Department has announced substantial rewards for information leading to the identification of cybercriminals. The State Department's Rewards for Justice program offers up to $10 million for information on foreign government-linked individuals participating in malicious cyber activities against U.S. critical infrastructure.
For victims who believe their computers may be compromised, the FBI recommends reporting to the Internet Crime Complaint Center (IC3) or contacting local FBI field offices directly.
Looking Forward
The LummaC2 takedown represents a significant victory in the ongoing battle against cybercrime, but it's important to recognize it as one battle in a larger war. Assistant Director Bryan Vorndran of the FBI's Cyber Division captured this perspective: "Together, we are making it harder, and more painful, for cyber criminals to operate."
As cybercriminals continue to evolve their tactics, law enforcement and private sector partners must maintain their collaborative approach, combining legal authority, technical expertise, and operational agility to protect individuals and organizations from these persistent threats.
The success of this operation provides a blueprint for future cybercrime disruption efforts and demonstrates that even the most sophisticated criminal operations can be effectively countered through coordinated action and public-private partnerships.
This operation was conducted by the FBI's Dallas Field Office in coordination with the U.S. Attorney's Office for the Northern District of Texas, the National Security Division's National Security Cyber Section, and the Criminal Division's Computer Crime and Intellectual Property Section.