Laptop in the River: Inside Coupang's $1.1B Data Breach Response

When a Former Employee Steals 33 Million Customer Records, Panics, and Tries to Destroy the Evidence—And Why the Stock Actually Went Up
The cybersecurity world loves a good drama, and South Korea just delivered one for the ages. Coupang—the country's dominant e-commerce platform and often called "the Amazon of Korea"—has been navigating what authorities describe as South Korea's worst-ever data breach. The story involves a former employee, stolen authentication keys, 33.7 million compromised accounts, a laptop weighted with bricks and thrown into a river, and a compensation package worth over $1 billion.
Oh, and Coupang's stock price? It went up.
The Breach: An Insider with the Keys to the Kingdom
The breach traces back to a former Coupang employee—reportedly a Chinese national who worked on the company's authentication management systems before leaving in 2024. The critical failure? He allegedly retained an active internal security key even after his contract ended.
Using that retained access, the individual accessed basic user data from approximately 33 million customer accounts between June and November 2025—a five-month window that went entirely undetected by Coupang's security systems. The compromised data included names, email addresses, phone numbers, home addresses, partial order histories, and 2,609 building entrance access codes.
Critically, Coupang maintains that no payment data, login credentials, or personal customs clearance numbers were accessed. The company also claims the perpetrator only retained detailed data from roughly 3,000 accounts despite accessing 33 million.

The Cover-Up: Bricks, a Canvas Bag, and a River
Here's where the story gets cinematic.
When news of the breach hit Korean media in late November, the perpetrator allegedly panicked. According to sworn testimony Coupang obtained during its investigation, he physically smashed his MacBook Air, stuffed it into a canvas Coupang bag along with bricks for weight, and threw it into a nearby river.
The laptop was his primary tool for the attack—along with a desktop PC where investigators later found the script used to extract the data.
But the evidence didn't stay underwater. Coupang, working under government direction, used maps and descriptions provided by the perpetrator to send divers into the river. They recovered the laptop exactly as described: in the branded canvas bag, weighted with bricks. The serial number matched his iCloud account.
The perpetrator had already fled South Korea by the time the investigation progressed.
Coupang's Response: A Masterclass in Breach Management?
This is where cybersecurity professionals should pay close attention.
Within weeks of confirming the breach's scope, Coupang:
- Engaged three top-tier forensic firms: Mandiant, Palo Alto Networks, and Ernst & Young conducted parallel investigations
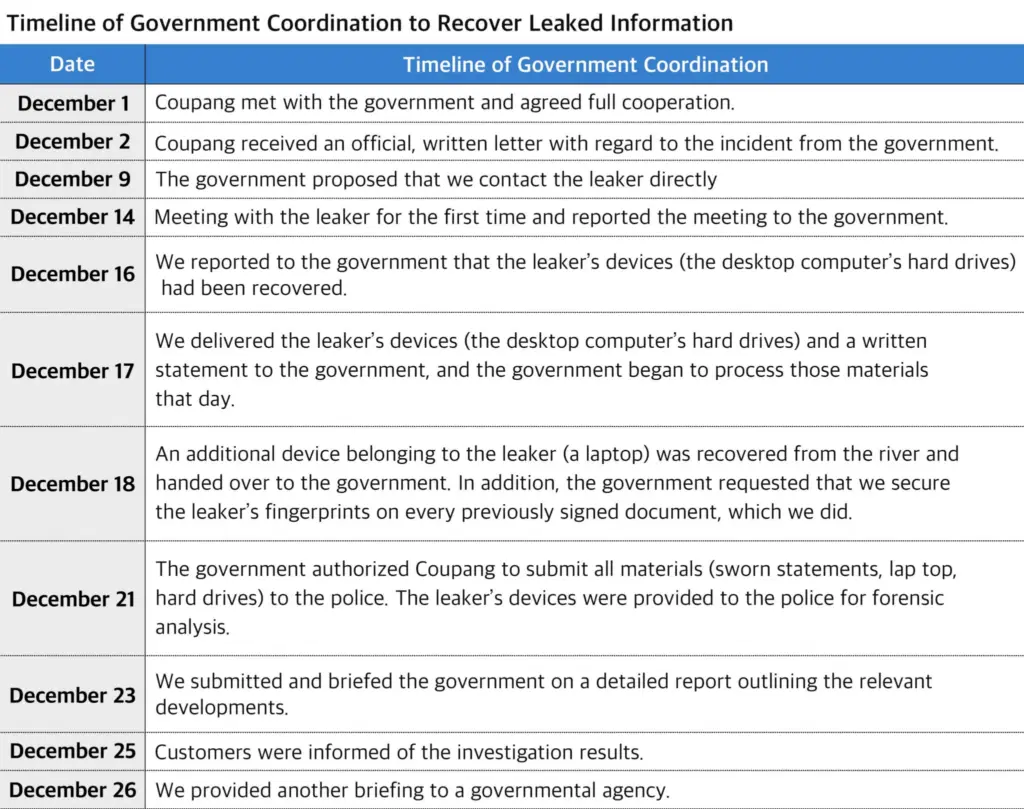
- Coordinated daily with government authorities: Contrary to criticism that Coupang conducted a "self-investigation," the company released a detailed timeline showing near-daily coordination with Korean government agencies starting December 1
- Recovered all devices: The perpetrator's desktop, four hard drives, and the river-recovered MacBook were all secured and submitted to authorities
- Obtained a full confession: The perpetrator provided sworn, fingerprinted declarations detailing exactly how the breach occurred
- Accepted executive accountability: CEO Park Dae-jun resigned on December 10, taking full responsibility for both the breach and the company's response
And then came the compensation announcement that turned heads across the industry.
The $1.1 Billion Apology
On December 29, Coupang announced a compensation package worth approximately 1.685 trillion won—over $1.1 billion USD—to be distributed to all 33.7 million affected customers.
Each customer receives 50,000 won (~$35) in purchase vouchers:
- 5,000 won for all Coupang products (Rocket Delivery, marketplace items)
- 5,000 won for Coupang Eats (food delivery)
- 20,000 won for Coupang Travel
- 20,000 won for R.LUX (luxury beauty platform)
Distribution begins January 15, 2026, via the Coupang app.
The compensation approach has drawn mixed reactions. Critics, including National Assembly committee chair Choi Min-hee, accused Coupang of attempting to "turn the crisis into a business opportunity" since the vouchers only work on Coupang's own platforms. But from a pure incident response perspective, the speed and scale of the commitment is remarkable.

The Market's Surprising Response
Here's the twist that confounds conventional wisdom about breach fallout: after Coupang released its December 25 investigation update confirming the limited scope of retained data and device recovery, the stock rose approximately 6%.
Several factors explain this counterintuitive market behavior:
Contained damage narrative: Coupang's claim that only ~3,000 accounts had data actually retained (versus merely accessed), combined with no payment data exposure, positioned this as a "near miss" rather than a catastrophic leak.
Decisive leadership action: The CEO's resignation signaled accountability. The interim appointment of Harold Rogers, chief administrative officer from the U.S. parent company, brought in senior leadership perceived as capable of crisis management.
Proactive compensation: Announcing a billion-dollar compensation plan before regulatory penalties were even finalized demonstrated Coupang was getting ahead of the crisis rather than being dragged by it.
Forensic transparency: Publishing the detailed coordination timeline with government, complete with specific dates and actions, countered the "cover-up" narrative that typically tanks stock prices.
Morgan Stanley and Nomura both lowered price targets—to $31 and $30 respectively—citing increased cybersecurity costs, but both maintained buy/overweight ratings based on Coupang's fundamental business strength.
The Legal Storm Still Brewing
The stock bounce doesn't mean Coupang is out of the woods. Multiple class action lawsuits are proceeding in U.S. federal courts, and Korean law firm Daeryun is pursuing parallel litigation domestically.
The company faces potential fines up to 1 trillion won (~$681 million) under Korean law. The Ministry of Science and ICT has publicly rebuked Coupang for unilaterally disclosing investigation findings before the joint public-private investigation team verified them.
And founder Bom Kim was summoned to testify before the National Assembly—with lawmakers warning of consequences if the billionaire failed to appear.
Lessons for Security Leaders
This breach offers several critical takeaways:
Offboarding is your biggest blind spot. A former employee retained active authentication credentials for months after departure. How many organizations can honestly say their deprovisioning processes would catch this?
Insider threats require different detection. The access was carried out using legitimate credentials over five months. Traditional perimeter security is irrelevant when the threat has valid keys.
Speed of response matters more than perfection. Coupang's compensation announcement came before investigations concluded. They took the reputational hit of admitting fault early rather than fighting a losing PR battle.
Executive accountability signals organizational seriousness. The CEO resigned within two weeks of the breach becoming public. That's rare—and investors noticed.
Forensic transparency can rebuild trust. By releasing granular timelines and engaging elite forensic firms publicly, Coupang shifted the narrative from "what are they hiding?" to "what did they find?"
The Insider Threat Wake-Up Call
South Korea has now experienced breaches affecting SK Telecom (27 million users), Lotte Card (3 million), and Coupang (33.7 million) within a single year. President Lee Jae Myung called the Coupang breach "truly astonishing" and demanded tougher corporate penalties.
The presidential office described current enforcement as "not functioning."
For cybersecurity professionals globally, this is the pattern we keep seeing: the perimeter is hardened, the firewalls are enterprise-grade, the SOC is staffed 24/7—and then someone who used to work there walks out with an authentication key nobody revoked.
Coupang's response may have been impressive. But the breach itself was entirely preventable.
The investigation continues. Coupang has pledged full cooperation with Korean authorities and promised additional security measures to prevent recurrence.

Sources: Coupang official statements, Bloomberg, The Korea Herald, Reuters, The Record, CNBC, Cybernews, eSecurity Planet, Fortune