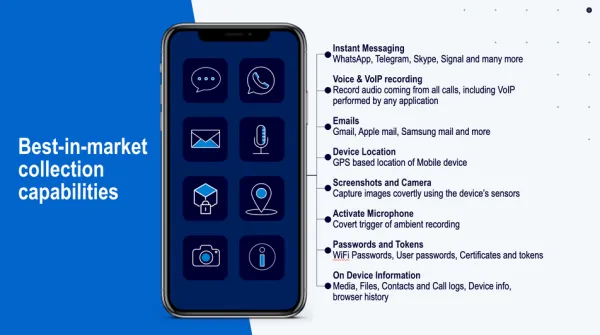
Major Cyber Attacks 2025: A Comprehensive Analysis of the Year's Most Devastating Data Breaches and Ransomware Incidents

Executive Summary: 2025 has witnessed an unprecedented surge in sophisticated cyber attacks, with ransomware attacks rising by 126% globally and the average number of attacks per organization reaching 1,925 per week. From geopolitical cyber warfare between India and Pakistan to massive retail breaches affecting millions of customers across the UK, the cyber threat landscape has evolved dramatically, with attackers leveraging AI, social engineering, and advanced persistent threat (APT) techniques to devastating effect.
Table of Contents
- Pakistan-India Cyber Warfare: APT36 and Digital Battlegrounds
- UK Retail Ransomware Wave: Scattered Spider's Million-Dollar Attacks
- Grove City Data Breach: Municipal Systems Under Siege
- Adidas Customer Data Compromise: Third-Party Security Failures
- Global Cyber Attack Trends and Statistics 2025
- Industry-Specific Attack Patterns and Vulnerabilities
- Advanced Threat Actor Analysis: APT Groups and Ransomware Collectives
- Financial Impact and Recovery Costs
- Emerging Attack Vectors and Techniques
- Mitigation Strategies and Best Practices
- Future Outlook and Predictions
Pakistan-India Cyber Warfare: APT36 and Digital Battlegrounds
The Pahalgam Terror Attack and Immediate Cyber Response
On 7 May 2025, exercising its "right to respond", Indian armed forces launched Operation Sindoor, under which they carried out precision strikes to destroy a network of terror camps in Pakistan and Pakistan-Occupied Kashmir following a devastating terror attack in Pahalgam that claimed 26 civilian lives. However, the physical conflict immediately spilled into cyberspace, marking one of the most significant state-sponsored cyber warfare campaigns of 2025.
Pakistani-affiliated hacker groups conducted a range of cyber attacks against Indian targets, even though none of them created any significant disruption. The attacks began immediately after the Pahalgam incident and escalated dramatically following India's military response.
APT36: The Primary Threat Actor
APT36 (Transparent Tribe) emerged as the primary threat actor in this cyber campaign. APT36 or Transparent Tribe, a threat group attributed to Pakistan, has been active since 2013, and has primarily targeted Indian defence, government and diplomatic entities.
Key Technical Details:
- Primary Malware: APT36 is known for its reliance on Crimson RAT, a remote access trojan used for data exfiltration and espionage
- Attack Methods: It frequently mimics Indian government websites to distribute malware
- Campaign Scope: Following the Pahalgam attack, APT36 launched a cyber attack campaign spoofing India's Ministry of Defence and "Pahalgam Terror Attack" themed documents to distribute malware
Scale of the Digital Assault
The scope of the Pakistani cyber offensive was massive:
- Indian agencies identified seven APT groups operating against India that were also responsible for over 15 lakh cyber attacks
- Most of these attacks reportedly originated from Pakistan, Bangladesh and the West Asian region
- Attack vectors included web defacement, DDoS attacks, malware distribution, and information warfare campaigns
India's Cyber Defense Response
India's response demonstrated the country's growing cyber defense capabilities:
Government Response:
- The Department of Telecommunications (DoT) has been evaluating measures to enhance infrastructure
- The Indian Computer Emergency Response Team (CERT-In) has issued advisories pertaining to risks to banks and financial institutions
- An advisory outlining the essential measures that need to be undertaken to secure MSMEs was issued on 10 May, followed by one for large industries
Disinformation Campaign Countermeasures:
A manual count shows that the Press Information Bureau (PIB) issued more than 60 fact-checks over five days to counter this tsunami of misinformation. The campaign included false claims about shot-down aircraft and captured pilots.
The Ministry of Electronics and Information Technology issued orders to social media platform X to block 8,000 accounts spreading misinformation.
Implications for Global Cyber Warfare
This incident highlights several critical trends:
- Immediate Cyber Response: Cyber attacks now begin within hours of physical conflicts
- Multi-Domain Warfare: Modern conflicts seamlessly integrate conventional and cyber operations
- Information Warfare: Social media platforms were flooded with misinformation in a deliberate attempt to undermine public trust in Indian operations
- GPS Spoofing: Reports are pointing out that threat actors are still targeting Indian government websites. The attack envelope is also expanding with reports of GPS spoofing
UK Retail Ransomware Wave: Scattered Spider's Million-Dollar Attacks
The Coordinated Assault on British Retail Giants
The spring of 2025 witnessed an unprecedented wave of sophisticated ransomware attacks targeting Britain's most prestigious retail brands. British retail giant Marks & Spencer (M&S) and the iconic Knightsbridge department store, Harrods, have become the latest to be hit by cyberattacks in the UK, along with the Co-operative Group, in what experts believe were coordinated strikes.
Financial Impact: Hundreds of Millions in Losses
The financial devastation was immediate and severe:
- Marks & Spencer: Marks and Spencer lost more than 700 million pounds ($930m) in its market value following the cyberattack
- M&S Profit Impact: The attacks disrupted online purchases and impacted some store inventories
- Operational Disruption: Around 200 warehouse workers told to stay home as the company responds to the attack
Scattered Spider: The Unconventional Threat Collective
What Makes Scattered Spider Unique:
Scattered Spider, also known as 0ktapus, Starfraud, UNC3944, Scatter Swine, Octo Tempest, and Muddled Libra, is a classification of threat actors that are adept at using social engineering attacks, phishing, multi-factor authentication (MFA) bombing (targeted MFA fatigue), and SIM swapping to gain initial network access on large organizations.
This is a loose network of mostly young, English-speaking hackers, making them distinct from traditional cybercrime groups typically based in Russia or Eastern Europe.
Attack Methodology:
Security researchers believe the recent wave of attacks was carried out using a Ransomware-as-a-Service (RaaS) platform known as DragonForce, with strong indications that the perpetrators are linked to the loosely organized threat collective Scattered Spider.
Individual Retailer Impact Analysis
Marks & Spencer: The Primary Target
Timeline and Attack Vector:
- The threat actors are believed to have first breached M&S as early as February, when they reportedly stole the Windows domain's NTDS.dit file
- April 21: Customers begin reporting issues making contactless payments and booking click-and-collect services
- April 25: M&S suspends all online orders and pulls its more than 200 [stores offline]
Customer Data Impact:
The company said the stolen customer information could include basic contact details, dates of birth and online order histories, though the information does not include "usable payment or card details," which it does not store on its own systems, nor any password information.
Harrods: The Luxury Target
Luxury retailer Harrods confirmed on May 1 that it experienced attempts to gain unauthorized access to some of its systems, leading it to take some of its systems offline as a proactive response step. The iconic Knightsbridge department store maintained operations while addressing the security incident.
Co-op: The Cooperative Under Siege
Co-op's Chief Digital Information Officer Rob Elsey confirmed the shut down of VPN access to stem the attack's spread. The incident affected:
- Back-office systems
- Call center operations
- Remote access capabilities
"We would ask for your patience as we take some additional pre-emptive actions on remote access to continue to keep our Co-op safe," the memo said.
DragonForce Ransomware: The Weapon of Choice
Technical Analysis:
DragonForce originated as a pro-Palestine hacktivist group allegedly based in Malaysia (under the name DragonForce Malaysia) that has been active since August 202 [2023]. The group has evolved significantly:
- In April 2024, threat actors associated with DragonForce were observed using a ransomware binary based on a leaked builder of LockBit Black ransomware, also known as LockBit 3.0
- In March 2025, the group also claimed to have taken over RasomHub's RaaS tooling after the group ceased its operations
- RansomBay Service: DragonForce took its model further by launching "RansomBay," a white-label service that lets affiliates rebrand the ransomware under a different name. Affiliates pay a 20% cut of any ransom haul and keep the rest
Government and Law Enforcement Response
National Cyber Security Centre (NCSC) Intervention:
Richard Horne, CEO at the GCHQ cybersec offshoot, confirmed the organization was assisting all three retailers on Thursday, and said the ongoing saga should serve as a wake-up call to all other or[ganizations].
Investigation Status:
Both the Metropolitan Police and the National Cyber Security Centre (NCSC) are investigating the cyber attacks, with the National Crime Agency (NCA) also involved in the M&S investigation.
Broader Implications for UK Retail Security
This coordinated attack exposed systemic vulnerabilities:
- Shared Infrastructure Risks: analysts suspect a shared architectural or supply chain vulnerability among the affected retailers
- VPN Vulnerabilities: Multiple retailers suffered breaches through compromised remote access systems
- Supply Chain Exposure: The rapid succession of attacks suggests common third-party dependencies
Grove City Data Breach: Municipal Systems Under Siege
Incident Overview and Timeline
Grove City offices suffered a cyber-attack on their internal computer network, which affected certain current and former Grove residents and employees. According to a letter sent out by city leaders on May 15, the internal computer server was breached on March 24.
Scope of Data Compromised
The breach exposed highly sensitive personal information:
- The database included names, addresses, social security numbers, and financial information
- Impact on both current and former city residents
- Exposure of city employee data
Municipal Response and Recovery Efforts
Immediate Response:
City staff contacted third-party IT specialists to isolate and remediate the attack, followed by hiring outside forensic specialists to investigate.
Customer Protection Measures:
As a safeguard, the city has arranged for customers to enroll at no cost in an online identity credit monitoring service for one year.
Implications for Municipal Cybersecurity
This incident highlights the vulnerability of local government systems:
- Resource Constraints: Municipal governments often lack adequate cybersecurity budgets
- Legacy Systems: Older infrastructure provides numerous attack vectors
- Sensitive Data Holdings: Cities maintain extensive databases of citizen information
- Limited IT Expertise: Smaller municipalities may lack specialized cybersecurity staff
Adidas Customer Data Compromise: Third-Party Security Failures
Breach Details and Impact
Sportswear brand Adidas has admitted it has been hit by a cyberattack in which customer data has been compromised. The German company said criminals had accessed certain consumer data through a third-party customer service provider.
Data Types Compromised
What Was Stolen:
- The breached data mainly consisted of contact information from consumers who had contacted its customer service help desk in the past
What Was Protected:
Adidas confirmed no passwords or credit card data was taken.
Company Response
"We immediately took steps to contain the incident and launched a comprehensive investigation, collaborating with leading information security experts," the company said in a statement.
"Adidas is in the process of informing potentially affected consumers," it said.
Third-Party Risk Management Crisis
This incident exemplifies growing concerns about supply chain security:
- Vendor Security Gaps: Third-party providers often have weaker security controls
- Data Flow Visibility: Companies may lack full visibility into how vendors handle their data
- Shared Responsibility Models: Unclear boundaries between company and vendor security responsibilities
Connection to Broader UK Retail Attack Pattern
The breach on Adidas is the latest in a string of cyberattacks on companies, demonstrating how cybercriminals are systematically targeting retail and consumer-facing businesses.
Related Retail Attacks:
- A recent cyberattack on Marks & Spencer will cost the retailer around £300 million after it was targeted over the Easter weekend
- A hack on Co-op earlier this month also caused significant disruption across its retail chain and led to bare shelves in many of its shops, while luxury shop Harrods has also been affected
Investigation Status:
The National Crime Agency said it is investigating the attacks on M&S and Co-op individually but is "mindful they may be linked".
Global Cyber Attack Trends and Statistics 2025
Unprecedented Growth in Attack Volume and Sophistication
The cyber threat landscape in 2025 has reached alarming new heights. The first quarter of 2025 saw cyber attacks around the global up sharply, with businesses experiencing more frequent – and more sophisticated – attacks. The average number of cyber attacks per organization reached 1,925 per week, marking a 47% rise compared to the same period in 2024.
Ransomware: The Dominant Threat Vector
Explosive Growth Statistics:
- Ransomware attacks rose by 126%, with North America accounting for 62% of global incidents
- The average ransom payment rose from $400,000 in 2023 to $2 million in 2024 -- an increase of 500%
- The average ransomware payout has increased dramatically from $812,380 in 2022 to $1,542,333 in 2023
Attack Frequency:
- According to a report by the United Nations Office on Drugs and Crime (UNODC), these attacks are happening at an alarming rate, with a new incident occurring approximately every 11 seconds
- Cybersecurity Ventures estimates that global ransomware trends for damage will experience 30% year-over-year growth over the next decade. The damages are estimated to exceed $265 billion annually by 2031, with a new attack happening every two seconds
Financial Impact: The $10.5 Trillion Crisis
Global Economic Impact:
According to Cybersecurity Ventures, the cost of cybercrime is expected to continue rising, potentially reaching $10.5 trillion annually by 2025.
Specific Cost Breakdowns:
- In 2024, data breaches continue to be an expensive challenge for organizations globally. According to IBM's 2024 Cost of a Data Breach Report, the average cost of a breach increased by 12% from the previous year, reaching $4.62 million
- The healthcare industry remains the hardest hit, with breach costs averaging $10.93 million per incident due to the sensitive nature of the data involved
- In 2024, the average ransomware insurance claim increased by 68% to an average loss of $353,000
Sector-Specific Attack Patterns
Most Targeted Industries:
The consumer goods & services sector was the most targeted by ransomware, making up 13.2% of reported attacks globally. Business services and industrial manufacturing sectors followed closely, accounting for 9.8% and 9.1%, respectively.
Critical Infrastructure Under Siege:
The Cybersecurity and Infrastructure Security Agency reported ransomware attacks against 14 of the 16 U.S. critical infrastructure sectors, including the food and agriculture, emergency services, government facilities, defense, and IT industries.
Industry-Specific Attack Patterns and Vulnerabilities
Healthcare: The Most Expensive Target
Healthcare organizations face the highest financial impact from cyber attacks:
- The healthcare sector remains particularly vulnerable, with the IBM 2024 Cost of a Data Breach Report showing that ransomware breaches in healthcare cost an average of $10.93 million per incident
- From 2020 to 2025, healthcare will spend $125 billion to defend against breaches
Downtime Impact:
ransomware-induced downtime leads to significant financial losses, with businesses losing an average of $8,500 per hour due to disrupted operations, according to Egnyte.
Education: Universities Under Attack
The education sector faces unique vulnerabilities:
Attack Statistics:
- Attacks on lower education (56%) and higher education (64%) increased
- Since 2020, 1,681 higher education facilities have been affected by 84 ransomware attacks
- 66 percent of universities lack basic email security configurations
Recovery Challenges:
- It costs, on average, $1.58 million for lower education to recover and $1.42 million for higher education to recover. The process sometimes takes months
- While nearly half of those attacked paid the ransom to recover their data, just 2% got all the data back
Financial Services: The High-Value Target
Attack Prevalence:
- Banking ranks as the No. 1 industry for detected ransomware attacks in 2023
- The rate of ransomware attacks in financial services increased from 55 percent in 2022 to 64 percent
Financial Impact:
In 2023, the average cost of a data breach in the financial industry was $5.90 million.
Government and Municipal Targets
Attack Statistics:
- 45% of government organizations hit by ransomware, paid to regain access to files
- Recorded Future cataloged 169 ransomware incidents in local and state governments since 2013
Insurance Coverage Gaps:
Only 78% of education organizations have cyber insurance coverage against ransomware compared with the global average of 83%.
Advanced Threat Actor Analysis: APT Groups and Ransomware Collectives
State-Sponsored APT Groups
APT36 (Transparent Tribe) - Pakistan
Operational Characteristics:
- APT36 or Transparent Tribe, a threat group attributed to Pakistan, has been active since 2013, and has primarily targeted Indian defence, government and diplomatic entities
- Primary Malware: Crimson RAT for data exfiltration and espionage
- Techniques: Website spoofing, themed malicious documents
Chinese APT Operations
The 2025 threat landscape also includes continued Chinese state-sponsored activities, with groups like APT31 (covered in our Czech Republic analysis) maintaining persistent campaigns against Western targets.
Ransomware-as-a-Service (RaaS) Evolution
Scattered Spider: The English-Speaking Anomaly
Unique Characteristics:
Scattered Spider is not a conventional cybercrime gang but rather an amorphous network of financially motivated threat actors. Members coordinate and share resources across Telegram, Discord, and dark web forums, making the group both resilient and difficult to dismantle.
Social Engineering Mastery:
- SIM swapping attacks
- Multi-factor authentication bombing
- Sophisticated phishing campaigns
- Vishing (voice phishing) operations
DragonForce: From Hacktivism to RaaS
Evolution Timeline:
- August 2023: Origin as pro-Palestine hacktivist group
- April 2024: threat actors associated with DragonForce were observed using a ransomware binary based on a leaked builder of LockBit Black ransomware
- March 2025: the group also claimed to have taken over RasomHub's RaaS tooling after the group ceased its operations
Business Model Innovation:
DragonForce took its model further by launching "RansomBay," a white-label service that lets affiliates rebrand the ransomware under a different name. Affiliates pay a 20% cut of any ransom haul and keep the rest, while DragonForce handles the underlying infrastructure, technical support and leak-site hosting.
Emerging Threat Actor Trends
AI-Enhanced Social Engineering
From fictitious profiles to AI-generated emails and websites, adversaries like FAMOUS CHOLLIMA are using genAI to supercharge insider threats and social engineering. With AI-powered deception becoming more convincing, organizations must evolve their defenses.
Malware-Free Attacks
79% of detections were malware-free, indicating a shift toward living-off-the-land techniques and legitimate tool abuse.
Fastest Breakout Times:
51 sec — the fastest recorded eCrime breakout time, demonstrating the speed at which modern attackers can move laterally through compromised networks.
Financial Impact and Recovery Costs
Direct Financial Losses
Ransom Payment Trends
Payment Statistics:
- According to research from blockchain analysis company Chainalysis, approximately $813.55 million was spent on ransomware payments in 2024
- A survey conducted with 1,263 companies found 80 percent of victims who submitted a ransom payment experienced another attack soon after, and 46 percent got access to their data but most of it was corrupted
Insurance Coverage Gaps:
42 percent of companies with cyber insurance policies in place indicated that insurance only covered a small part of the damages resulting from a ransomware attack.
Business Disruption Costs
Operational Impact:
In our 2025 Unit 42 Global Incident Response Report, we found that 86% of incidents involved business disruption, spanning operational downtime, reputational damage or both.
Revenue and Brand Impact:
60 percent of survey respondents experienced revenue loss and 53 percent stated their brands were damaged as a result of ransomware attacks.
Industry-Specific Financial Impact
Retail Sector Losses
The UK retail attacks of 2025 demonstrate massive financial impact:
- M&S Market Value Loss: Marks and Spencer lost more than 700 million pounds ($930m) in its market value following the cyberattack
- Operational Disruption: Weeks of suspended online ordering and warehouse shutdowns
Healthcare Financial Devastation
The healthcare industry remains the hardest hit, with breach costs averaging $10.93 million per incident due to the sensitive nature of the data involved.
Municipal Government Costs
Local governments face particular challenges:
- Limited IT budgets for recovery
- Costs of forensic investigations
- Extended downtime affecting citizen services
- Credit monitoring services for affected residents
Long-Term Economic Impact
Projected Growth in Cybercrime Costs:
Worldwide, cybercrime costs companies an estimated $8 trillion in 2023, a staggering number that is expected to rise to nearly $24 trillion by 2027.
Decade-Long Damage Projections:
Cybersecurity Ventures estimates that global ransomware trends for damage will experience 30% year-over-year growth over the next decade. The damages are estimated to exceed $265 billion annually by 2031.
Emerging Attack Vectors and Techniques
AI-Powered Cyber Attacks
Generative AI in Social Engineering
Almost three-quarters of organizations report rising cyber risks, with generative AI fuelling more sophisticated social engineering and ransomware attacks; 42% saw an uptick in phishing incidents.
Specific AI Applications:
- Deepfake audio for CEO fraud
- AI-generated phishing emails
- Automated vulnerability discovery
- Enhanced password cracking
AI Adoption Risks
Despite growing reliance on AI for cybersecurity, many organizations lack processes to properly assess the security of AI tools before deployment, creating a gap in managing associated risks.
While 66% of organizations see AI as the biggest cybersecurity game-changer this year, only 37% have safeguards to assess AI tools before use.
Supply Chain Attack Evolution
Third-Party Risk Amplification
Supply chain attacks are seen by 60% of C-Suite executives as the most likely type of cyber threat that would affect their business.
Managed Service Provider (MSP) Targeting:
Ransomware groups have been shifting their focus to managed service providers (MSPs), a platform that serves many clients at once. This means that if a hacker gains access to one MSP, it could also reach the clients it's serving as well.
Risk Assessment Integration
By 2025, it is estimated that 60% of organisations will use cyber security risk as a key factor when determining transactions and business engagements with third parties.
Cloud and Remote Work Vulnerabilities
Unsecured Remote Access
59 percent of employers allow their employees to access company applications from unmanaged personal devices, creating significant security gaps.
Remote Access Exploitation:
One of the primary attack vectors was remote access exploitation, which accounted for 20% of incidents. Many breaches resulted from insecure remote access, including default credentials, unpatched VPNs, and exposed RDP sessions.
Advanced Evasion Techniques
Living-Off-The-Land Attacks
Modern attackers increasingly rely on legitimate tools and system features:
- PowerShell script abuse
- WMI (Windows Management Instrumentation) exploitation
- Legitimate remote administration tools
- Credential dumping with built-in utilities
Zero-Day and N-Day Exploitation
Vulnerability Disclosure Trends:
New research reveals that more than 30,000 vulnerabilities were disclosed last year, a 17 percent increase from previous figures, reflecting the steady rise in cyber risks.
Mitigation Strategies and Best Practices
Zero Trust Architecture Implementation
Core Principles
Adopt a Zero Trust Architecture: Eliminate implicit trust. The traditional VPN is now one of the most targeted entry points in modern attacks.
Key Components:
- Identity Verification: Continuous authentication and authorization
- Least Privilege Access: Minimal necessary permissions
- Network Segmentation: Microsegmentation to prevent lateral movement
- Continuous Monitoring: Real-time threat detection and response
Practical Implementation
Implement Secure Remote Access: Protect remote access channels with Zero Trust Access solutions that do more than just authenticate—they continuously assess risk and granularly enforce least-privilege policies in real-time.
Advanced Authentication Measures
Multi-Factor Authentication (MFA) Enhancement
Deploy Phishing-resistant MFA: Use FIDO2-based authentication methods that remain effective even in disconnected or offline environments—critical in ransomware scenarios where systems may be taken down.
Device-Specific MFA:
Per Device MFA: The NCSC has emphasized the importance of enabling 2FA across all systems—especially for remote and privileged access.
Network Security and Segmentation
Microsegmentation Strategy
Apply Adaptive Microsegmentation: Prevent lateral movement by enforcing microsegmentation – granular access controls between users and systems as well as between systems. Allow system interaction based only on identity, need, and time of access using principles of least privilege.
Privilege Management
Remove Standing Privileges: Use just-in-time privileged access with ephemeral credentials that disappear once a task is complete.
Incident Response and Recovery
Backup Strategy Evolution
Modern Backup Requirements:
- Immutable backups to prevent encryption
- Offline backup copies disconnected from networks
- Regular backup testing and validation
- Rapid recovery procedures with defined RTOs
Crisis Communication Planning
Lessons from the UK retail attacks demonstrate the importance of:
- Immediate customer notification procedures
- Clear communication channels with stakeholders
- Coordinated response with law enforcement
- Public relations management during incidents
Employee Training and Awareness
Social Engineering Defense
Employee Training and Awareness: Regular training sessions can educate employees about the latest cyber threats and phishing tactics, fostering a culture of vigilance.
Training Focus Areas:
- Recognition of AI-generated content
- Verification procedures for unusual requests
- Secure remote work practices
- Incident reporting procedures
Supply Chain Security
Vendor Risk Management
Assessment Criteria:
- Third-party security certifications
- Regular penetration testing
- Incident response capabilities
- Data handling procedures
Continuous Monitoring
Advanced Threat Prevention: Utilize technologies such as sandboxing and anti-ransomware tools to detect and block sophisticated attacks.
Future Outlook and Predictions
Threat Landscape Evolution
AI Arms Race Acceleration
The cybersecurity landscape is entering an AI-driven arms race where both attackers and defenders leverage artificial intelligence. With AI-powered deception becoming more convincing, organizations must evolve their defenses.
Predicted Developments:
- Fully automated attack campaigns
- AI-generated zero-day exploits
- Dynamic evasion techniques
- Personalized social engineering at scale
Geopolitical Cyber Warfare
The Pakistan-India cyber conflict represents a preview of future state-sponsored campaigns:
- Immediate cyber responses to physical conflicts
- Multi-domain warfare integration
- Information warfare as a primary weapon
- Critical infrastructure targeting
Economic Impact Projections
Escalating Financial Damage
The damages are estimated to exceed $265 billion annually by 2031, with a new attack happening every two seconds.
Key Drivers:
- Increased attack sophistication
- Greater digital dependency
- Expanding attack surfaces
- Higher ransom demands
Regulatory and Policy Changes
Mandatory Reporting Expansion
Switzerland has enacted a new mandate requiring operators of critical infrastructure to report cyber-attacks to national authorities, and will take effect on April 1, 2025.
Global Trend:
With this mandate, Switzerland joins nations such as Australia, the EU, Japan, Singapore, South Korea, the UK, and the US, which have implemented similar reporting mandates for critical infrastructure operators.
Ransomware Payment Regulation
The percentage of states that enact laws regulating ransomware payments, fines, and negotiations will increase from less than 1% in 2021 to 30% by the end of 2025.
Technological Defense Evolution
Next-Generation Security Technologies
Emerging Solutions:
- Quantum-resistant cryptography
- Behavioral analytics and AI detection
- Automated incident response
- Predictive threat intelligence
Zero Trust Maturity
Organizations are moving beyond basic Zero Trust implementation toward comprehensive security architectures that assume breach and focus on limiting damage.
Industry-Specific Predictions
Retail Sector Transformation
The UK retail attacks will likely drive:
- Industry-wide security standards
- Shared threat intelligence platforms
- Coordinated incident response procedures
- Enhanced customer data protection
Critical Infrastructure Hardening
Government agencies are prioritizing critical infrastructure protection:
- Mandatory security standards
- Regular penetration testing requirements
- Incident response coordination
- Public-private partnership enhancement
Risk Assessment Evolution
Business Risk Integration
By 2025, it is estimated that 60% of organisations will use cyber security risk as a key factor when determining transactions and business engagements with third parties.
This integration will drive:
- Enhanced due diligence procedures
- Continuous vendor monitoring
- Risk-based pricing models
- Insurance requirement evolution
Conclusion: Navigating the 2025 Cyber Threat Landscape
The cyber attacks of 2025 have demonstrated unprecedented sophistication, scale, and impact across all sectors and geographies. From the geopolitical cyber warfare between Pakistan and India to the coordinated retail attacks in the UK, attackers have shown remarkable adaptability and persistence.
Key Takeaways
- Scale and Speed: The average number of cyber attacks per organization reached 1,925 per week, marking a 47% rise compared to the same period in 2024
- Financial Impact: the cost of cybercrime is expected to continue rising, potentially reaching $10.5 trillion annually by 2025
- Attack Evolution: Modern threats combine state-sponsored techniques with criminal motivations, leveraging AI and social engineering at unprecedented levels
- Systemic Vulnerabilities: Supply chain attacks and third-party breaches represent growing risks that traditional security models struggle to address
Strategic Imperatives
Organizations must adapt their cybersecurity strategies to address these evolving threats:
- Implement Zero Trust Architecture with continuous verification and least-privilege access
- Enhance Employee Training to combat AI-powered social engineering
- Strengthen Supply Chain Security through rigorous vendor risk management
- Prepare for Inevitable Breaches with robust incident response and recovery capabilities
- Integrate Cyber Risk into business decision-making processes
Looking Forward
As we progress through 2025, the cyber threat landscape will continue evolving rapidly. Organizations that proactively adapt their security postures, invest in advanced technologies, and foster a security-conscious culture will be best positioned to defend against increasingly sophisticated threats.
The incidents analyzed in this report serve as crucial learning opportunities for the global cybersecurity community. By understanding attack patterns, sharing threat intelligence, and implementing comprehensive defense strategies, organizations can build resilience against the next wave of cyber threats.
The message is clear: cybersecurity is no longer just an IT concern but a fundamental business imperative that requires board-level attention, adequate investment, and continuous adaptation to emerging threats.
This analysis is based on comprehensive research of publicly available threat intelligence, incident reports, and cybersecurity research. Organizations should consult with cybersecurity professionals to develop customized defense strategies appropriate for their specific risk profiles and operational requirements.