Major Supply Chain Attack: Palo Alto Networks and Zscaler Hit by Salesloft Drift Breach

Two cybersecurity giants fall victim to sophisticated OAuth token theft campaign targeting hundreds of organizations worldwide
September 2, 2025 — In a stunning turn of events that has sent shockwaves through the cybersecurity industry, both Palo Alto Networks and Zscaler have confirmed they were victims of a massive supply chain attack that compromised customer data through stolen OAuth tokens from Salesloft's Drift integration with Salesforce.

Executive Summary
Between August 8-18, 2025, threat actors orchestrated one of the year's most significant supply chain attacks by compromising Salesloft Drift's OAuth tokens to gain unauthorized access to hundreds of Salesforce environments. The campaign, tracked by Google's Threat Intelligence Group as UNC6395 and attributed to the ShinyHunters extortion group, has impacted over 700 organizations globally, including two of the world's leading cybersecurity companies.
Key Impact Numbers:
- 700+ organizations affected worldwide
- Hundreds of Salesforce instances compromised
- Multiple cybersecurity vendors breached, including industry leaders
- 10-day attack window during which threat actors operated undetected

The Attack Vector: OAuth Token Theft
The sophistication of this supply chain attack lies in its exploitation of legitimate third-party integrations. Salesloft Drift, an AI-powered chat agent that integrates with Salesforce for sales workflow automation, became the unwitting gateway for mass data exfiltration.
How the Attack Worked
- Initial Compromise: Threat actors breached Salesloft's systems and stole OAuth and refresh tokens associated with the Drift application's Salesforce integrations
- Token Abuse: Using these stolen tokens, attackers could impersonate the legitimate Drift application and access connected Salesforce environments without triggering traditional authentication alerts
- Mass Data Exfiltration: The attackers systematically queried Salesforce databases, extracting sensitive information from Account, Contact, Case, and Opportunity objects
- Credential Harvesting: Post-exfiltration, the threat actors actively scanned stolen data for additional credentials, including AWS access keys, Snowflake tokens, passwords, and other cloud secrets
Palo Alto Networks: A Cybersecurity Giant Falls
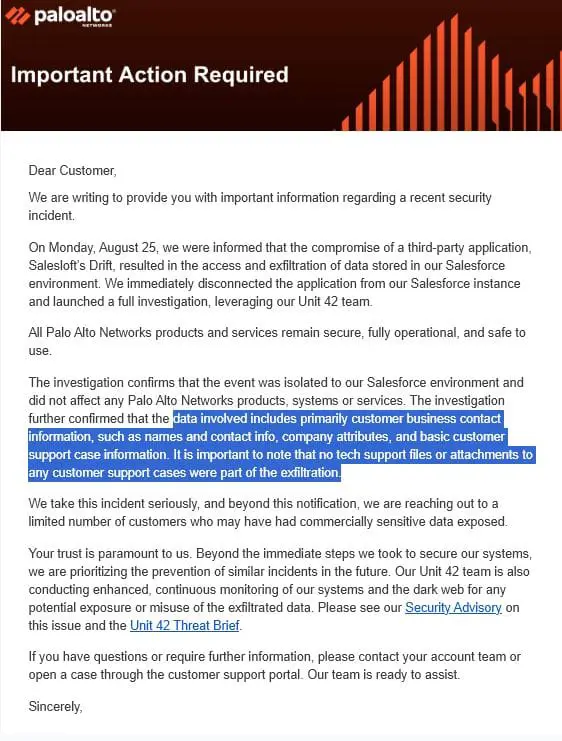
Palo Alto Networks' disclosure on September 2, 2025, confirmed the company was among hundreds affected by the supply chain attack. The breach exposed customer support case data and business contact information, though the company emphasized that its core products and services remained secure.
What Was Compromised at Palo Alto Networks:
- Business contact information and account details
- Internal sales records
- Basic support case data (contact info and text comments)
- No technical support files or attachments were accessed
"We quickly contained the incident and disabled the application from our Salesforce environment," Palo Alto Networks stated. "Our Unit 42 investigation confirms that this situation did not affect any Palo Alto Networks products, systems, or services."
The company's Unit 42 threat intelligence team provided crucial insights into the attack methodology, revealing that threat actors used automated Python tools with specific user-agent strings:
python-requests/2.32.4Python/3.11 aiohttp/3.12.15Salesforce-Multi-Org-Fetcher/1.0Salesforce-CLI/1.0
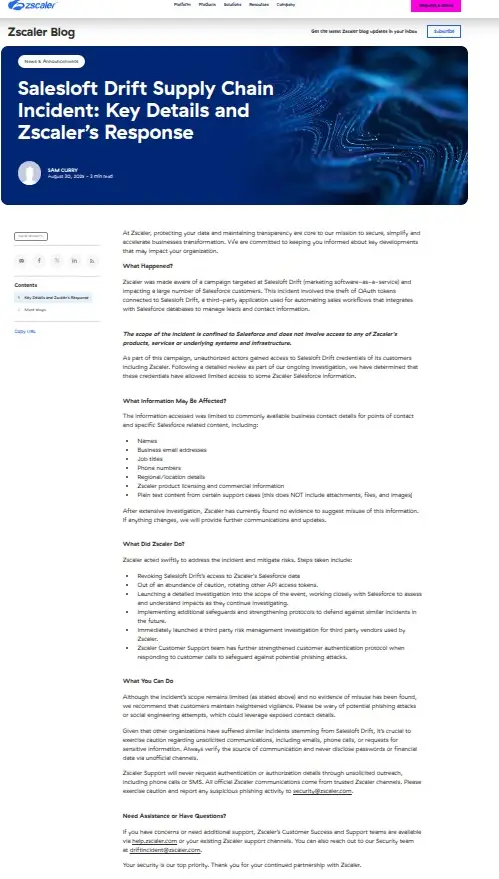
Zscaler: Cloud Security Leader Breached
Zscaler's disclosure followed shortly after, confirming that threat actors gained "limited access" to its Salesforce environment through the compromised Drift credentials. The cloud security company emphasized that its core infrastructure and security services were not impacted.
Zscaler's Compromised Data:
- Customer names and business email addresses
- Phone numbers and job titles
- Company locations and regional details
- Zscaler product licensing information
- Content from certain support cases
"Although the incident's scope remains limited and no evidence of misuse has been found, we recommend that customers maintain heightened vigilance," Zscaler advised in its security advisory.
Technical Analysis: Advanced Threat Actor Techniques
Google's Threat Intelligence Group and Mandiant researchers have provided detailed analysis of the UNC6395 threat actor's sophisticated operational techniques:
Automated Data Extraction
The attackers leveraged Python's asynchronous capabilities with libraries like aiohttp to perform high-volume, rapid data exfiltration through Salesforce's Bulk API. This approach minimized their time on target while maximizing data collection.
Anti-Forensics Measures
- Query Deletion: Attackers systematically deleted query jobs to hide evidence of their activities
- Tor Usage: Infrastructure was obfuscated using Tor exit nodes and cloud hosting providers (AWS, DigitalOcean)
- Log Evasion: While query jobs were deleted, audit logs remained intact for forensic analysis
Targeted Credential Harvesting
The threat actors specifically searched for high-value credentials using automated scanning for:
- AWS access keys (AKIA identifiers)
- Snowflake tokens and credentials
- Generic keywords: "password," "secret," "key"
- VPN and SSO login strings
- Organization-specific authentication URLs

Industry-Wide Impact and Response
The supply chain attack's scope extends far beyond cybersecurity companies. The campaign has affected organizations across multiple sectors, with technology and software companies representing the majority of victims.
Coordinated Response Efforts
- Salesloft immediately revoked all active OAuth and refresh tokens for Drift applications
- Salesforce removed the Drift application from its AppExchange marketplace
- Google disabled Drift integrations for affected Workspace accounts
- Mandiant was engaged to conduct forensic investigation
Previous Salesforce Attack Campaign
This supply chain attack represents an evolution in tactics from the ongoing Salesforce breach campaign that has plagued organizations throughout 2025. Previous attacks by the ShinyHunters group relied on social engineering and voice phishing (vishing) to trick employees into authorizing malicious OAuth applications.
Notable victims of the broader Salesforce campaign include:
- Cisco
- Farmers Insurance
- Workday
- Adidas
- Qantas
- Allianz Life
- LVMH subsidiaries (Louis Vuitton, Dior, Tiffany & Co.)

Implications for the Cybersecurity Industry
The successful targeting of two major cybersecurity vendors raises critical questions about supply chain security and third-party risk management across the industry.
Trust and Reputation Impact
Having cybersecurity leaders fall victim to supply chain attacks creates a paradox of confidence in an industry built on protecting others. Both companies have been transparent about the incidents, but the reputational implications are significant.

Supply Chain Security Lessons
- Third-party Integration Risks: Even legitimate, widely-used integrations can become attack vectors
- OAuth Token Security: The persistent nature of OAuth tokens makes them high-value targets for threat actors
- Monitoring Gaps: The 10-day attack window suggests detection capabilities need enhancement
- Credential Management: Support case systems often contain sensitive credentials that require better protection
Mitigation and Response Recommendations
Immediate Actions for Organizations
- Audit Third-party Integrations: Review all SaaS application connections and OAuth permissions
- Rotate Credentials: Proactively rotate any credentials that may have been exposed in support cases
- Monitor for Social Engineering: Increase vigilance against phishing attempts using exposed contact information
- Review Access Logs: Examine Salesforce and identity provider logs for suspicious activity
Long-term Security Improvements
- Zero Trust Implementation: Apply conditional access policies and least-privilege principles
- Automated Credential Scanning: Deploy tools like Trufflehog and Gitleaks to identify exposed secrets
- Enhanced Monitoring: Implement robust logging and detection for unusual API activity
- Supply Chain Risk Assessment: Conduct thorough security evaluations of third-party integrations
The Broader Threat Landscape
This supply chain attack exemplifies the evolving threat landscape where cybercriminals increasingly target legitimate business tools and integrations. The ShinyHunters group's evolution from direct social engineering to supply chain exploitation demonstrates the adaptability and sophistication of modern threat actors.
ShinyHunters Group Evolution
The threat actors behind this campaign have claimed to be associated with both ShinyHunters and Scattered Spider, suggesting potential collaboration between major cybercriminal groups. Their evolution from the Snowflake data theft campaign to Salesforce attacks shows a pattern of targeting cloud infrastructure and SaaS platforms.
Looking Forward: Industry Response and Prevention
The cybersecurity industry must collectively address the supply chain vulnerabilities exposed by this attack. Key areas for improvement include:
Enhanced OAuth Security
- Implementing stricter token rotation policies
- Developing better monitoring for OAuth token usage
- Creating industry standards for third-party integration security
Supply Chain Security Frameworks
- Establishing comprehensive vendor risk assessment processes
- Developing real-time monitoring capabilities for third-party integrations
- Creating incident response playbooks specific to supply chain attacks
Information Sharing and Collaboration
The rapid disclosure and information sharing between affected companies, security researchers, and platform providers demonstrates the importance of collaborative defense against supply chain attacks.
Conclusion
The Salesloft Drift supply chain attack represents a watershed moment for cybersecurity, demonstrating that even industry leaders are vulnerable to sophisticated supply chain compromises. The targeting of Palo Alto Networks and Zscaler sends a clear message that no organization is immune to these evolving threats.
The incident underscores the critical importance of:
- Comprehensive third-party risk management
- Robust monitoring of OAuth token usage
- Proactive credential rotation and management
- Enhanced detection capabilities for supply chain attacks
As the investigation continues and more organizations potentially come forward, the full scope of this supply chain attack may reveal even broader implications for enterprise security and the SaaS ecosystem as a whole.
The cybersecurity industry's response to this incident will likely shape supply chain security practices for years to come, making it a defining moment in the evolution of enterprise security defenses.
This developing story will be updated as more information becomes available about the ongoing investigation and potential additional victims.