Massive Chinese Espionage Campaign Targets Global Network Infrastructure
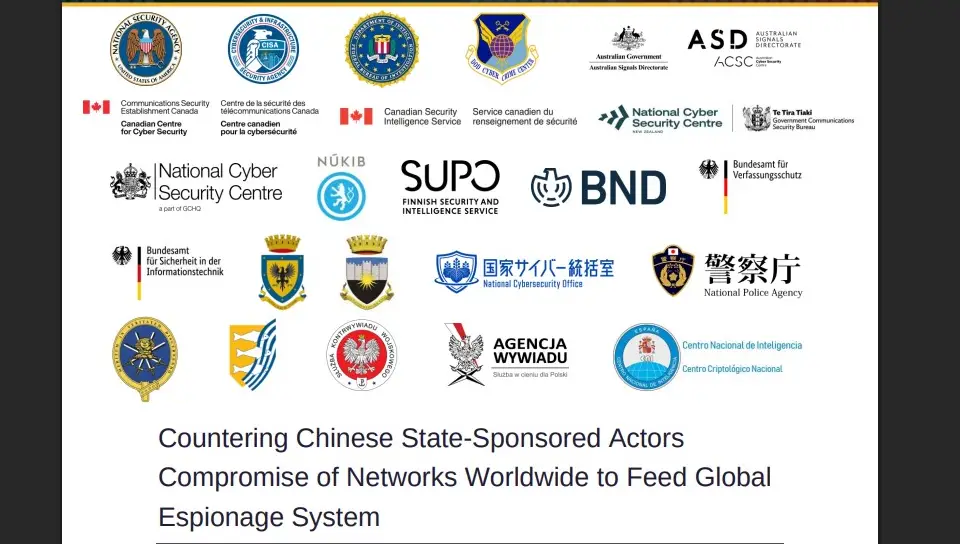
A new joint cybersecurity advisory from 23 international agencies reveals the scope of an ongoing Chinese state-sponsored cyber campaign that has been quietly compromising critical network infrastructure worldwide since 2021. The coordinated effort, involving agencies from the United States, United Kingdom, Australia, Canada, and 10 other nations, exposes sophisticated attacks against telecommunications providers, government networks, and critical infrastructure across multiple continents.

The Scale of the Campaign
The threat actors—tracked under various names including Salt Typhoon, OPERATOR PANDA, and RedMike—have demonstrated remarkable persistence and technical sophistication. Rather than targeting individual endpoints, these groups have focused on the backbone of the internet itself: routers, switches, and network infrastructure that carries global communications.
Key targets include:
- Telecommunications and Internet service providers (ISPs)
- Government networks
- Transportation systems
- Hospitality infrastructure
- Military networks
The campaign's ultimate goal appears to be establishing a global surveillance network capable of monitoring and intercepting communications as they flow through compromised infrastructure.
Chinese Companies Behind the Attacks
The advisory directly links this activity to Chinese entities providing cyber services to China's intelligence apparatus, including:
- Sichuan Juxinhe Network Technology Co. Ltd.
- Beijing Huanyu Tianqiong Information Technology Co., Ltd.
- Sichuan Zhixin Ruijie Network Technology Co., Ltd.
These companies allegedly support "multiple units in the People's Liberation Army and Ministry of State Security," transforming stolen data into intelligence capabilities for tracking targets' "communications and movements around the world."
Tactics and Techniques
Exploiting Known Vulnerabilities
Unlike many advanced persistent threat (APT) groups that rely on zero-day exploits, these actors have found remarkable success using publicly known vulnerabilities. They've particularly focused on:
- CVE-2023-20198/20273: Cisco IOS XE authentication bypass and privilege escalation vulnerabilities
- CVE-2024-3400: Palo Alto Networks GlobalProtect remote code execution
- CVE-2024-21887: Ivanti Connect Secure command injection
- CVE-2018-0171: Cisco Smart Install vulnerability
The reliance on known CVEs highlights a critical issue: many organizations aren't patching network infrastructure devices quickly enough, leaving them vulnerable to sophisticated actors.

Advanced Persistence Methods
Once inside networks, the attackers employ numerous techniques to maintain long-term access:
Router Modifications:
- Creating unauthorized administrative accounts
- Modifying Access Control Lists (ACLs) to permit traffic from attacker-controlled IPs
- Enabling SSH services on non-standard ports (often using patterns like 22x22 or xxx22)
- Setting up HTTP/HTTPS management servers on unusual high ports
Traffic Collection:
- Using native packet capture capabilities to intercept TACACS+ authentication traffic
- Configuring traffic mirroring (SPAN/RSPAN/ERSPAN) to copy network traffic
- Modifying router configurations to redirect authentication servers to attacker infrastructure
Tunneling and Exfiltration:
- Creating GRE and IPsec tunnels for covert data transmission
- Leveraging compromised routers as pivot points for lateral movement
- Using legitimate network protocols to blend malicious traffic with normal operations
The Guest Shell Technique
One particularly sophisticated technique involves abusing Cisco's Guest Shell feature—a legitimate Linux container environment available on many Cisco devices. Attackers use this to:
- Run Python scripts and custom tools directly on network devices
- Process and stage collected data locally
- Evade detection by keeping malicious activities within the container
- Execute reconnaissance and lateral movement from within trusted network infrastructure
Real-World Impact
A case study in the advisory reveals how attackers collected network packet captures specifically targeting TACACS+ traffic on TCP port 49. Since TACACS+ is used for network device authentication, compromising this traffic provides access to administrative credentials for additional network equipment.
The attackers demonstrated particular interest in:
- Subscriber information from telecommunications providers
- Network diagrams and device inventories
- Customer records and metadata
- Authentication credentials and passwords
Immediate Actions for Organizations
Prioritize Patching
Organizations must immediately patch the identified vulnerabilities, especially:
- CVE-2023-20198/20273 (Cisco IOS XE)
- CVE-2024-3400 (Palo Alto GlobalProtect)
- CVE-2024-21887 (Ivanti Connect Secure/Policy Secure)
Network Monitoring
Implement comprehensive monitoring for:
- Unusual SSH access on non-standard ports
- Unexpected packet capture or traffic mirroring configurations
- TACACS+/RADIUS traffic to unauthorized servers
- New tunnel interfaces or routing changes
- Guest Shell or container activity on network devices
Configuration Management
- Regularly audit all network device configurations
- Monitor for unauthorized changes to ACLs, user accounts, and routing tables
- Implement robust change management processes
- Disable unnecessary services like Guest Shell if not operationally required
Network Segmentation
- Isolate management interfaces using dedicated VRFs or out-of-band networks
- Restrict management plane access to authorized IP addresses only
- Implement control-plane policing (CoPP) to rate-limit management protocols

The Bigger Picture
This campaign represents more than just another APT group—it's evidence of a coordinated effort to compromise the fundamental infrastructure of global communications. By targeting the routers and switches that carry internet traffic, these actors have positioned themselves to monitor communications at scale.
The international scope of the advisory, involving 23 agencies from multiple continents, underscores the global nature of this threat. It also represents an unprecedented level of cooperation in sharing threat intelligence and attribution.
Looking Forward
The sophistication and persistence of this campaign highlight several critical needs:
- Faster Patching: Network infrastructure requires the same urgent attention to patching as traditional IT systems
- Enhanced Monitoring: Organizations need visibility into network device activities, not just endpoint security
- International Cooperation: Threats of this scale require coordinated international response
- Zero Trust Networks: Traditional network security models may be insufficient against actors who can compromise core infrastructure
This advisory serves as a stark reminder that nation-state actors are not just targeting data—they're targeting the very infrastructure that carries our digital communications. Organizations must recognize that network security is national security, and act accordingly.
For technical details, indicators of compromise, and specific mitigation guidance, organizations should review the full joint advisory and implement the recommended security measures immediately. The threat is ongoing, sophisticated, and requires urgent attention from network defenders worldwide.

The full joint cybersecurity advisory AA25-239A is available from CISA and partner agencies. Organizations should also report any suspected compromise to their national cybersecurity agencies.