Massive Intellexa Leak Exposes Predator Spyware's Dark Evolution: Ad-Based Zero-Click Attacks and Vendor Backdoor Access
Major investigation reveals commercial spyware vendor maintained secret access to government surveillance systems while developing invisible infection vectors through digital advertising
A damning new investigation into mercenary spyware vendor Intellexa has exposed operational details that should alarm every CISO: the company behind the notorious Predator spyware not only developed zero-click infection methods through digital advertising but also maintained secret remote access to customer surveillance systems deployed at government facilities worldwide.
The "Intellexa Leaks" investigation, published jointly by Inside Story, Haaretz, WAV Research Collective, and Amnesty International, draws on leaked internal documents, training videos, and marketing materials that reveal the sophisticated—and deeply troubling—operations of one of the world's most notorious commercial surveillance vendors.
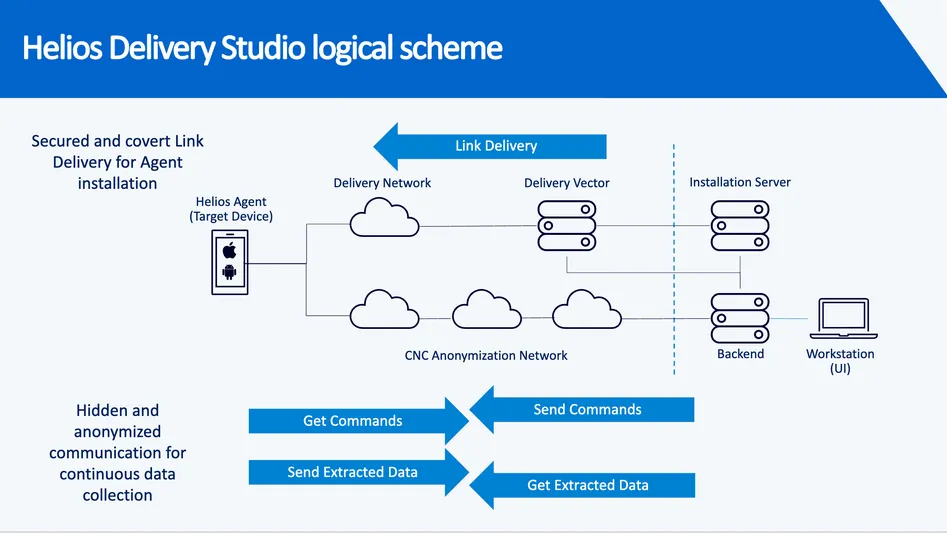
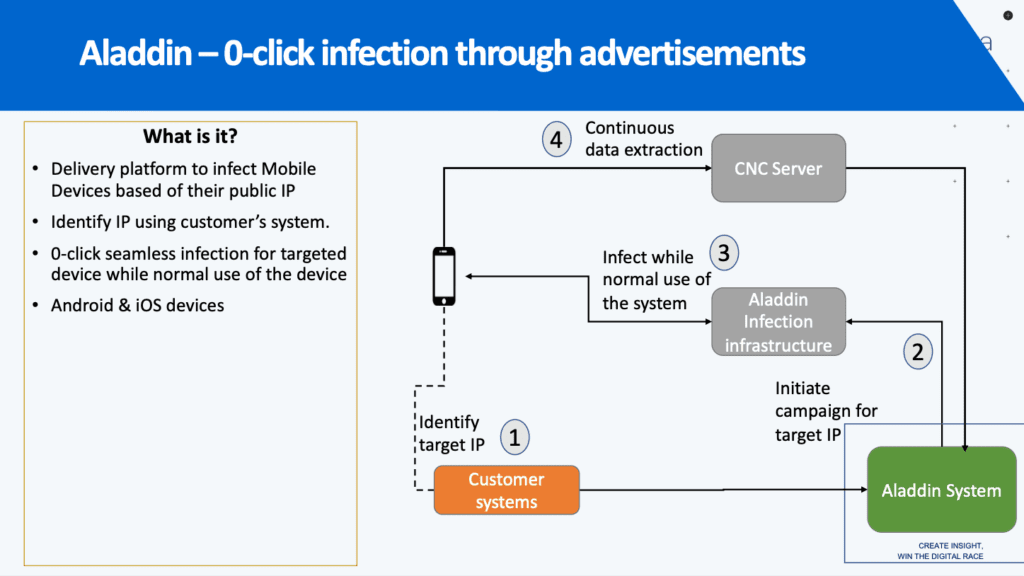
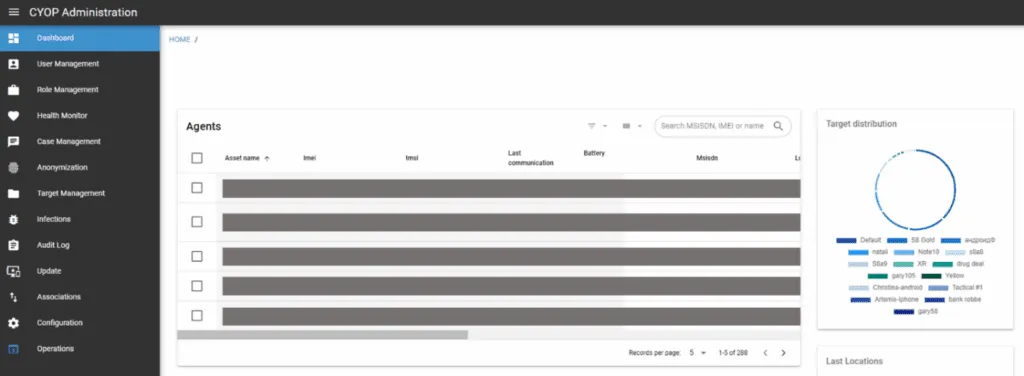
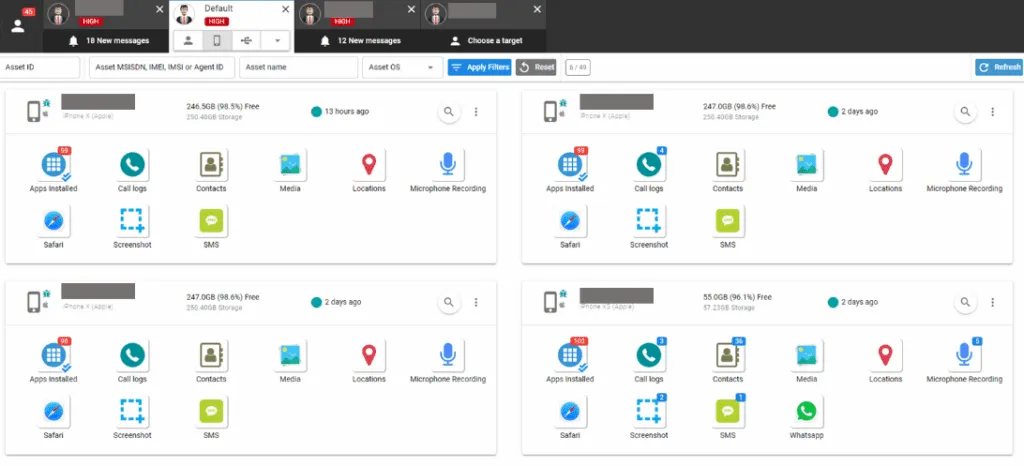
The Headline Threat: Zero-Click Infections Through Digital Ads
Perhaps the most alarming technical revelation is Intellexa's "Aladdin" system, which weaponizes the global digital advertising ecosystem to deliver spyware infections without any user interaction.
The system infects target phones by forcing a malicious advertisement to be shown on the target's device, with internal company materials explaining that simply viewing the advertisement is enough to trigger the infection—no click required.
This isn't theoretical. Amnesty International believes the Aladdin vector was supported in active Predator deployments in 2024, with additional research indicating Intellexa continues to actively develop their advertising-based infection vector into 2025.
For enterprise security teams, the implications are stark: your users could be compromised while browsing legitimate news websites or using trusted mobile apps. Traditional security awareness training about "not clicking suspicious links" becomes irrelevant when the infection requires no user action whatsoever.
The Vendor Trust Problem: Remote Access to "Air-Gapped" Systems
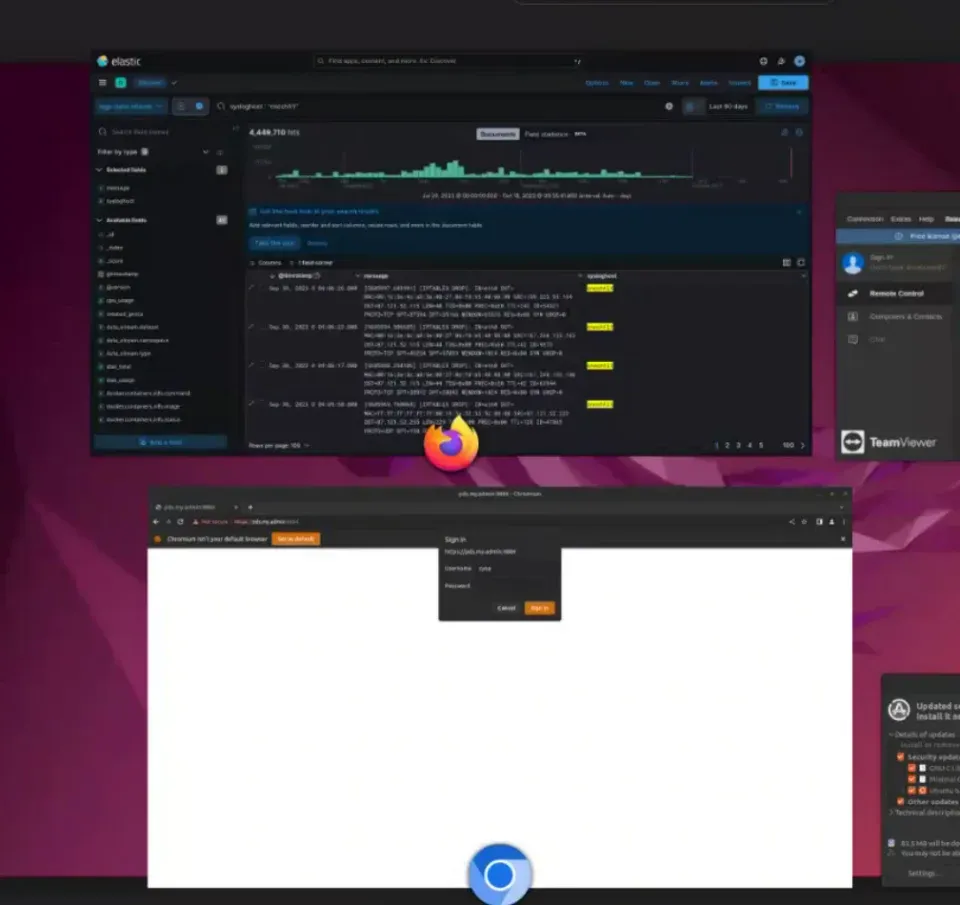
The investigation uncovered something that fundamentally challenges assumptions about commercial surveillance tools: Intellexa retained the capability to remotely access Predator customer systems, even those physically located on the premises of its governmental customers.
Leaked training videos show Intellexa staff using commercial TeamViewer software to connect directly to live customer surveillance systems—without apparent oversight or approval mechanisms. The video reveals:
- Access to at least 10 different customer systems (codenamed Dragon, Eagle, Falcon, Flamingo, Fox, Glen, Lion, Loco, Phoenix, and Rhino)
- Live visibility into infection attempts, including target IP addresses and device information
- Network access to systems containing collected surveillance data
- Pre-authenticated login credentials to customer Predator dashboards
Companies that sell spyware to government agencies have long maintained that they never have access to the data of their customers' targets, nor their customers' systems. This investigation proves otherwise—at least for Intellexa.
For CISOs evaluating third-party security tools: this raises critical questions about vendor access, oversight mechanisms, and whether "on-premises" deployments provide the isolation customers believe they're getting.
Active Exploitation: Still Burning Zero-Days Despite Sanctions
Despite being sanctioned by the U.S. government, Intellexa continues aggressive zero-day exploitation. Google's Threat Intelligence Group identified Intellexa as one of the most prolific spyware vendors exploiting zero-day vulnerabilities against mobile browsers, responsible for 15 out of 70 cases TAG discovered since 2021.
Recent CVEs linked to Intellexa include:
- CVE-2025-6554 (Chrome V8 type confusion - June 2025, Saudi Arabia)
- CVE-2023-41993 (Safari RCE)
- CVE-2023-4762, CVE-2023-3079, CVE-2023-2033 (Chrome V8 vulnerabilities)
The company's exploitation framework is sophisticated, with exploits high in sophistication compared to the less sophisticated spyware stager, supporting the assessment that exploits were likely acquired from another party. In other words: Intellexa is buying zero-days on the exploit market and weaponizing them at scale.
Infection Vectors: From Tactical to Strategic
The leaked documents reveal Intellexa's comprehensive approach to device compromise:
Tactical Vectors (requiring proximity):
- Triton: Samsung Exynos baseband exploits via fake 2G base stations
- Thor and Oberon: Additional local attacks (details unclear)
Strategic Vectors (remote):
- Mars/Jupiter: Network injection requiring ISP/telecom cooperation
- Aladdin: Zero-click via malicious advertising (as detailed above)
According to Recorded Future, two companies called Pulse Advertise and MorningStar TEC appear to be operating in the advertising sector and are likely tied to the Aladdin infection vector.
Real-World Impact: Pakistan, Kazakhstan, and Beyond
In summer 2025, a human rights lawyer from Pakistan's Balochistan province received a malicious link over WhatsApp from an unknown number, representing the first reported evidence of Predator spyware being used in the country.
Google announced notifications to several hundred accounts across various countries, including Pakistan, Kazakhstan, Angola, Egypt, Uzbekistan, Saudi Arabia and Tajikistan.
The investigation also forensically confirmed Predator's use in attacks on Greek journalist Thanasis Koukakis and Egyptian political activist Ayman Nour, with leaked internal documentation matching indicators of compromise found on victim devices.
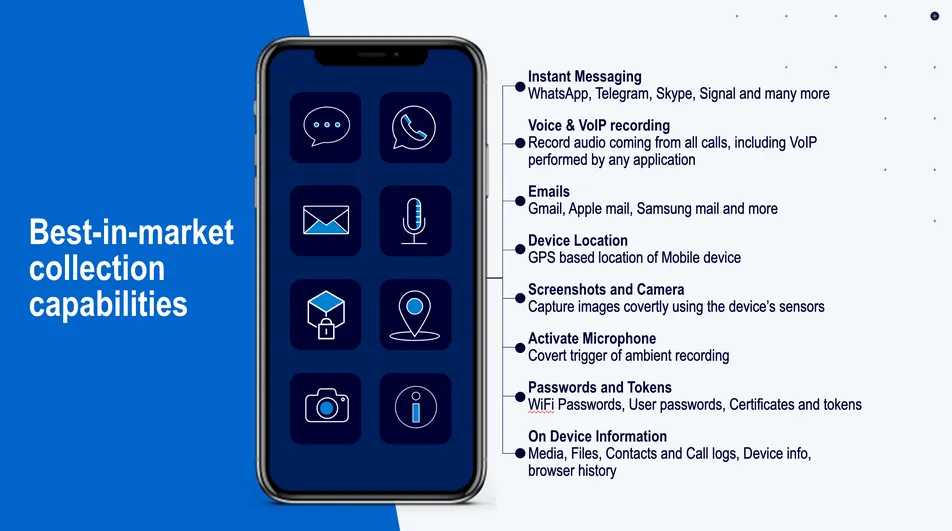
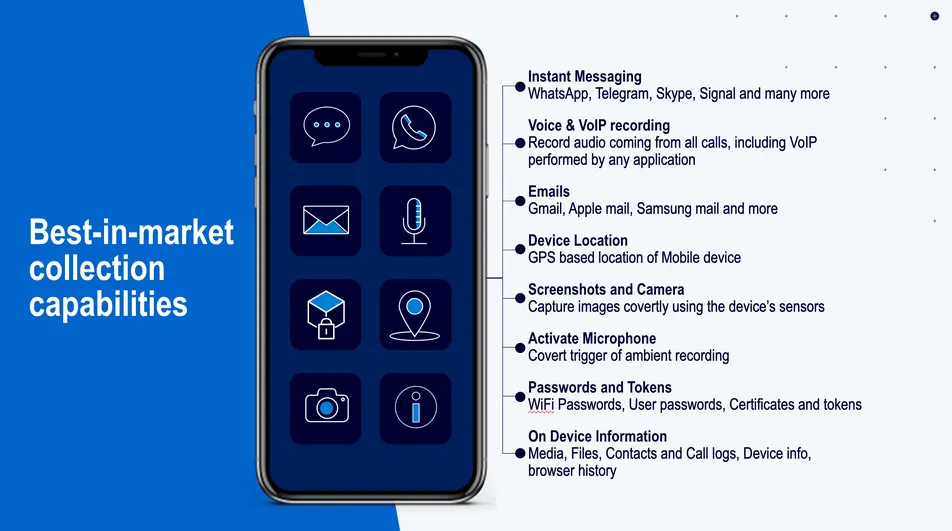
Capabilities: Complete Device Takeover
Once installed, Predator provides comprehensive surveillance capabilities:
- Access to encrypted messaging (Signal, WhatsApp, Telegram)
- Audio recordings and microphone activation
- Camera access and screenshots
- Stored passwords, emails, contacts, call logs
- Real-time location tracking
- Keylogging capabilities
What CISOs Need to Do
Immediate Actions:
- Enable Advanced Protections: Deploy Lockdown Mode (iOS) or Advanced Protection (Android) for high-risk users
- Review Third-Party Access: Audit all vendor remote access capabilities, especially for "on-premises" security tools
- Monitor Ad Traffic: Consider additional scrutiny of advertising SDKs in mobile applications
- Update Policies: Ensure critical personnel understand zero-click threats go beyond traditional phishing
Strategic Considerations:
- The advertising ecosystem is now a viable attack vector for nation-state level threats
- Commercial spyware vendors may maintain undisclosed access to deployed systems
- Mobile device security requires defense-in-depth beyond traditional MDM
- Zero-day exploitation remains economically viable for commercial vendors
The Bigger Picture
Despite repeated public exposure, criminal investigations, and financial sanctions directed at the company and its senior executives, Predator spyware continues to be used to unlawfully surveil activists, journalists and human rights defenders around the world.
The Intellexa leaks demonstrate that commercial surveillance vendors are not only technically sophisticated but also willing to maintain operational capabilities that directly contradict their public statements about customer independence and data separation.
For enterprise security leaders, this investigation serves as a stark reminder: third-party security tools require the same scrutiny as third-party applications, vendor access needs robust oversight mechanisms, and the threat landscape continues to evolve in directions that render traditional security controls increasingly inadequate.
Learn More
For complete technical details, forensic evidence, and analysis, see Amnesty International's comprehensive technical briefing: To Catch a Predator: Leak exposes the internal operations of Intellexa's mercenary spyware
About the Investigation: The "Intellexa Leaks" investigation represents a months-long collaboration between Inside Story, Haaretz, WAV Research Collective, and Amnesty International's Security Lab, with corroborating technical analysis from Google's Threat Intelligence Group and Recorded Future.

This article synthesizes findings from multiple sources investigating the Intellexa leaks. Security teams should review the source technical briefing for detailed indicators of compromise and forensic evidence.