Measuring What Matters: Why Incident Response Maturity Is Your Organization's Hidden Security Metric
In today's rapidly evolving threat landscape, the question isn't if your organization will experience a security incident, but when. Security breaches have become an inevitable aspect of business operations, with the average cost of a data breach reaching $4.45 million in 2023, according to IBM's Cost of a Data Breach Report.

Yet many organizations continue to focus primarily on prevention while underinvesting in incident response (IR) capabilities. This imbalance creates a dangerous security gap – one that can be addressed through systematic IR maturity assessment.
The Critical Gap in Security Programs
Security leaders across industries face a common challenge: demonstrating the value of security investments while ensuring their organizations can effectively respond when preventative controls fail. Consider these sobering statistics:
- 83% of organizations experienced more than one data breach in the past year
- The average time to identify and contain a breach is 277 days
- Organizations with an IR team and tested IR plan reduce breach costs by up to $3.1 million
These numbers tell a compelling story: incident response capabilities directly impact your bottom line. But how do you know if your IR program is actually effective?
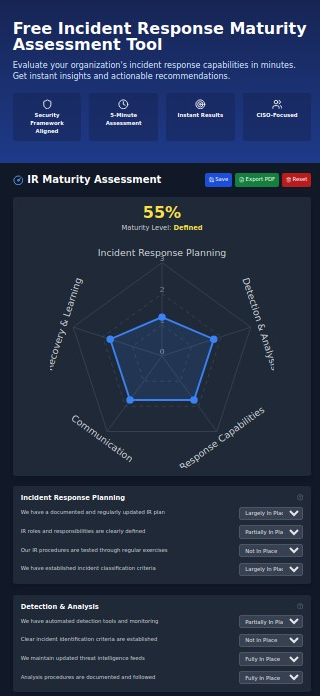
Enter the IR Maturity Assessment
A comprehensive IR maturity assessment evaluates your organization's ability to detect, respond to, and recover from security incidents across multiple dimensions. Unlike point-in-time security audits or technical penetration tests, maturity assessments measure the operational effectiveness of your security program.
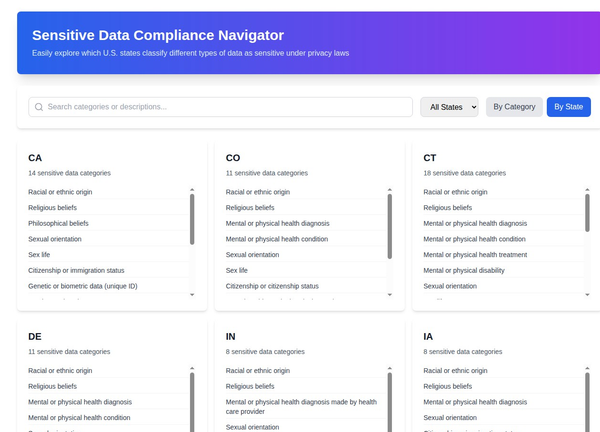
IRMaturityAssessment.com offers a free, framework-based tool that measures five critical dimensions of IR maturity:
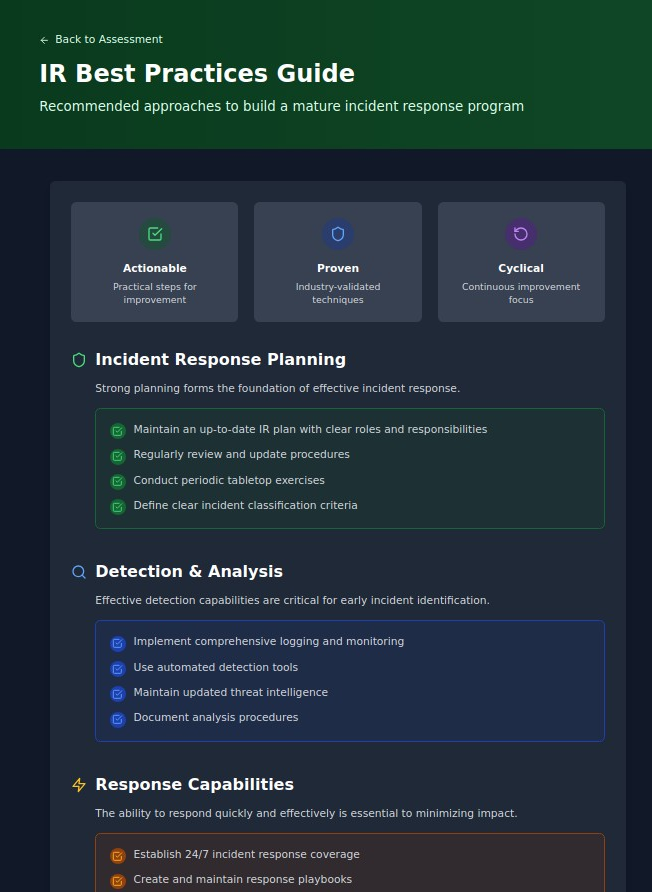
1. Incident Response Planning
The foundation of effective response, this dimension evaluates your documented procedures, roles and responsibilities, testing cadence, and classification criteria. Without proper planning, incident response becomes chaotic and ineffective, often leading to increased damage and costs.
2. Detection & Analysis
This dimension assesses your ability to identify and analyze potential security incidents, including monitoring capabilities, analysis procedures, threat intelligence integration, and tooling effectiveness. Organizations with mature detection capabilities identify breaches 74 days sooner than those without.
3. Response Capabilities
Beyond planning, this dimension examines your actual ability to contain and eradicate threats, including response coverage, containment procedures, external support relationships, and response playbooks for common scenarios.
4. Communication
Often overlooked but critically important, communication measures how effectively you disseminate information during incidents, including protocols, stakeholder management, status updates, and documentation processes.
5. Recovery & Learning
The most mature organizations continuously improve their IR capabilities through structured recovery procedures, lessons learned processes, metrics tracking, and program enhancements.
The Maturity Spectrum: Where Do You Stand?
IR maturity exists on a spectrum, with most organizations falling somewhere between initial ad-hoc processes and optimized, continuously improving programs:
- Initial (0-20%): Reactive with minimal documentation and informal procedures
- Developing (21-40%): Basic processes established but inconsistent
- Defined (41-60%): Standardized and documented processes with regular testing
- Managed (61-80%): Measured, controlled processes with continuous improvement
- Optimized (81-100%): Automated, enhanced processes focused on continuous improvement
According to recent industry surveys, approximately 65% of organizations fall in the "Developing" to "Defined" range, indicating significant room for improvement across the board.
Real-World Impact: The Case of Company X
Consider the experience of a mid-sized financial services company we'll call Company X. After suffering a ransomware attack that resulted in 72 hours of system downtime and $1.2 million in recovery costs, they conducted a thorough IR maturity assessment.
The assessment revealed:
- Well-documented IR plans (score: 75%)
- Adequate detection capabilities (score: 68%)
- Weak response capabilities (score: 42%)
- Poor communication processes (score: 35%)
- Limited recovery and learning procedures (score: 30%)
These findings helped Company X prioritize investments in response playbooks, communication templates, and post-incident review processes. Six months later, when facing another attempted ransomware attack, they contained the threat within 4 hours with minimal business impact.
Beyond Compliance: The Business Value of Mature IR
While many organizations conduct IR assessments for compliance reasons, the true value extends far beyond regulatory checkboxes:
- Financial Protection: Organizations with mature IR capabilities experience 54% lower costs when breaches occur
- Operational Resilience: Reducing incident impact and recovery time maintains business continuity
- Customer Trust: Effective communication during incidents preserves reputation and customer confidence
- Competitive Advantage: Security maturity increasingly factors into business decisions and partnerships
- Continuous Improvement: Systematic measurement drives ongoing program enhancement
Five Steps to Improve Your IR Maturity
Based on data from hundreds of IR maturity assessments, these five steps consistently deliver the greatest improvement in overall maturity:
1. Document and Test Your Plan
Start by creating a comprehensive IR plan document that clearly defines roles, responsibilities, and procedures. Test this plan through regular tabletop exercises involving both technical and non-technical stakeholders.
2. Implement Detection Metrics
You can't improve what you don't measure. Establish baseline metrics for detection capabilities, including mean time to detect (MTTD), false positive rates, and coverage across critical systems.
3. Develop Playbooks for Common Scenarios
Create detailed response playbooks for your top 5-10 most likely incident types. These should include step-by-step procedures, decision trees, and clearly defined escalation paths.
4. Establish Communication Templates
Prepare pre-approved communication templates for different stakeholder groups and incident severities. These save critical time during incidents and ensure consistent messaging.
5. Conduct Meaningful Post-Mortems
After each incident or exercise, conduct thorough reviews focused on actionable improvements. Document lessons learned and track the implementation of recommendations.
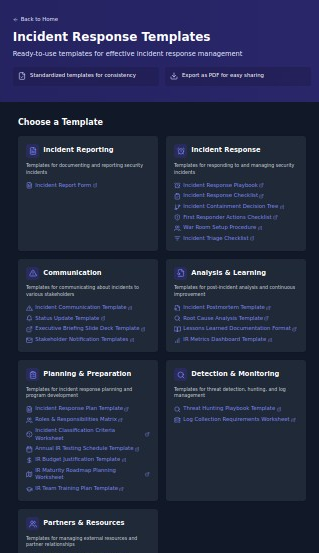
Leveraging IRMaturityAssessment.com for Continuous Improvement
The free assessment tool at IRMaturityAssessment.com provides security leaders with:
- Comprehensive evaluation across 5 critical dimensions
- Visual representation of maturity through an interactive radar chart
- Overall maturity score and classification
- Targeted recommendations based on your specific results
- Access to customizable templates for each maturity dimension
By conducting regular assessments (we recommend quarterly), you can track progress over time and demonstrate the value of your security investments to executive leadership.
Beyond the Assessment: Building a Culture of Readiness
While tools and processes form the backbone of mature IR programs, truly resilient organizations foster a culture of security awareness and incident readiness. This includes:
- Regular training across all staff levels
- Executive-level involvement in IR exercises
- Recognition for reporting potential incidents
- Transparent communication about security events
- Integration of IR considerations into business decisions
Conclusion: Measure, Improve, Repeat
In today's threat landscape, robust incident response capabilities are no longer optional—they're essential to organizational resilience. By systematically assessing your IR maturity, you gain visibility into critical gaps, prioritize improvements, and demonstrate the value of security investments.
The journey toward IR maturity is continuous rather than a destination. Each assessment provides an opportunity to identify the next most valuable improvements, creating a virtuous cycle of enhancement that strengthens your security posture over time.
Start your IR maturity journey today with a free assessment at IRMaturityAssessment.com and transform the question from "Are we secure?" to the more actionable "How effectively can we respond when security incidents occur?"
About Breached.Company: We provide actionable security insights and tools for organizations seeking to enhance their security posture. Our team of experienced security professionals specializes in incident response, threat intelligence, and security program development.