Navigating the Digital Frontier: Protecting Patients from Medical Device Cyber Threats, Including the Mind Itself

In an era defined by hyper-connectivity, our healthcare systems are undergoing a profound transformation. Medical devices, once standalone instruments, are now increasingly connected—from Bluetooth-enabled pacemakers and insulin pumps to sophisticated patient monitors and advanced neurotechnologies. This "Internet of Medical Things" (IoMT) offers immense benefits, such as real-time monitoring and improved patient care, but it simultaneously introduces a complex web of cybersecurity risks that pose a direct threat to patient safety, data integrity, and even the fundamental aspects of human autonomy.
The landscape of healthcare cybersecurity has shifted from primarily an IT concern to a patient safety imperative, profoundly influencing procurement decisions and operational strategies within healthcare organizations.
The Evolving Threat Landscape: More Than Just Data Breaches
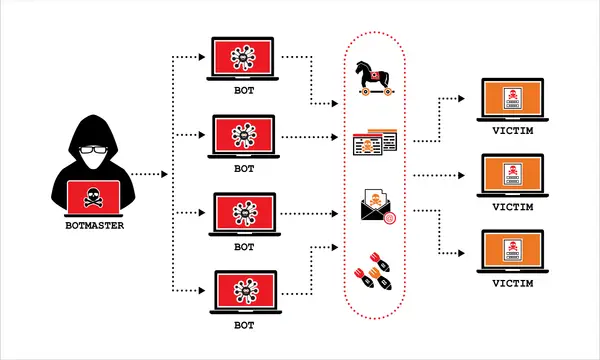
Cyber threats in healthcare are no longer theoretical; they are a daily reality. Hospitals and healthcare delivery organizations face a barrage of risks to connected medical devices and critical Operational Technology (OT) systems. Operational Technology (OT) systems, which include medical devices, are now identified as the biggest cybersecurity concern for 35% of organizations, surpassing traditional IT systems. Attacks can range from ransomware rendering hospital networks inoperable to malware impacting patient monitors and even directly controlling life-sustaining implanted devices.
For instance, a 2017 FDA advisory highlighted vulnerabilities in over 500,000 pacemakers, susceptible to cyber-attacks that could allow remote control or even administer unnecessary shocks to a patient's heart. Similarly, an insulin pump was famously hacked in 2011 to deliver a lethal dose. Patient monitors like the Contec CMS8000 have been found with embedded backdoors and the ability to transmit private patient data externally undetected, posing risks of unauthorized data transmission, remote control, and potential network compromise. These incidents underscore how vulnerabilities in interconnected devices can lead to direct patient harm through clinical hazards like delayed diagnoses or treatment.
Emerging Ethical and Security Frontiers: Neurotechnology and Biohacking
Beyond traditional medical devices, the rapid advancements in neurotechnology are opening unprecedented ethical and security frontiers. Brain-computer interfaces (BCIs) and neuroimaging technologies (EEG, fMRI) are creating new opportunities for cognitive enhancement and even brainwave-based authentication, a method touted as superior to traditional passwords or fingerprints. However, this progress introduces profound ethical dilemmas and privacy concerns:

- Cognitive Privacy: Neural data is "qualitatively different" and "deeper and more sensitive" than other personal data, capable of revealing a person’s thoughts, feelings, plans, emotional states, and even mental illnesses. Unauthorized access or monitoring of this data violates the "psychological sphere of human existence".
- Brainjacking: This alarming threat involves unauthorized control over brain implants or neurostimulators. Attackers could manipulate neural signals to cause undesirable movements, thoughts, or dysphoria, as demonstrated by a 2021 case study. This applies not only to medical devices like deep brain stimulators for Parkinson's but also to BCIs used for cognitive optimization in military or high-security applications.
- Data Sovereignty and Consent: Individuals often don't fully understand the implications of sharing their brain activity data, making true informed consent challenging. The reusability of neural data over time further complicates consent, and existing cybersecurity and privacy frameworks do not adequately address the ownership, access, or sharing of this sensitive information. The leaking of unencrypted neural data from a neuroimaging firm in 2022 highlighted the risk of identity theft and manipulation using neural profiles.
- Cognitive Manipulation: Neurotechnology can be exploited in social engineering attacks, where attackers use discreet neural signals to elicit trust or confusion, making targets more vulnerable to revealing sensitive data. The concept of "Malicious Mind Hacking" has even made an explosive entry into the 2022 World Economic Forum's Global Risks Report due to its high likelihood and impact.
The weaponization of neurosciences, though explored in fictional scenarios, points to a future where technologies like NBIC (Nanotechnology, Biotechnology, Information Technology, and Cognitive Sciences) could be used to target the human mind as a "domain of operations," influencing perceptions and behaviors.
Regulatory Imperatives and Industry Response
Recognizing these escalating risks, regulatory bodies like the FDA are implementing stricter requirements. For "cyber devices" – those with software, internet connectivity, and vulnerability to cyber threats – providing a Software Bill of Materials (SBOM) in premarket submissions is now mandatory. An SBOM is a formal inventory of software components and their dependencies, helping to manage cybersecurity risks throughout the software stack and identify devices affected by vulnerabilities.

The FDA recommends that SBOMs adhere to the minimum elements identified by the National Telecommunications and Information Administration (NTIA) and include additional details like the software component’s level of support and end-of-support date. Manufacturers are also encouraged to:
- Maintain and regularly update SBOMs as part of device configuration management.
- Identify known vulnerabilities, including those in CISA’s Known Exploited Vulnerabilities Catalog, and provide safety and security risk assessments for each, along with risk controls.
- Implement a Secure Product Development Framework (SPDF), a set of processes to reduce vulnerabilities throughout the device lifecycle, from design to decommissioning.
- Ensure cybersecurity transparency through device labeling, communicating essential security information, and establishing robust vulnerability management plans.
Industry reports also reflect this growing urgency:
- 83% of healthcare organizations now integrate cybersecurity standards directly into their medical device RFPs, with 46% declining purchases due to cybersecurity concerns.
- 73% report that new FDA cybersecurity guidance and EU cybersecurity regulations are influencing procurement decisions.
- 79% of executives are willing to pay a premium for devices with advanced runtime protection or built-in exploit prevention, with 41% willing to pay up to 15% more.
- 78% of providers consider SBOMs essential or important in procurement decisions.
Challenges for Healthcare Providers and the Path Forward
Despite increasing budgets for medical device and OT security (75% of organizations increased budgets in the last year), only 17% feel extremely confident in their ability to detect and contain attacks on medical devices. Resource-constrained providers, especially rural hospitals and small practices, face disproportionate challenges due to limited staff, IT infrastructure, and funding. Many rely on outdated legacy systems that are no longer supported, complicating cybersecurity efforts and requiring costly workarounds.

Addressing these complex challenges requires a multi-faceted approach and shared responsibility among all stakeholders:
- Secure by Design: Manufacturers must integrate security controls throughout the entire device lifecycle, ensuring devices are designed with cybersecurity in mind, not as an afterthought.
- Robust Testing: Comprehensive cybersecurity testing, including vulnerability testing, penetration testing, and software composition analysis, is crucial to identify and mitigate risks before and after market release.
- Transparency and Information Sharing: SBOMs, clear labeling, and coordinated vulnerability disclosure processes are vital for enabling users to manage risks effectively. Healthcare providers must collaborate to exchange threat intelligence.
- Workforce Development and Support: Addressing the cybersecurity skills shortage through training, external support from managed security service providers (MSSPs), and government incentives is paramount, especially for resource-constrained organizations.
- Continuous Vigilance: Cybersecurity is an ongoing process. Devices need regular firmware and software updates, intrusion detection systems, and continuous monitoring for abnormal traffic.
The convergence of medical technology and the human mind demands an unprecedented level of ethical consideration and robust security measures. As our health and very cognition become increasingly intertwined with digital systems, safeguarding these connected critical assets is not just a technical challenge, but a societal imperative. It requires collective action to ensure that the innovations designed to improve health do not inadvertently become new vectors for harm.