North Korean Hackers Tricked by Fake Remote-Work Laptops: Inside the Lazarus Group Honeypot Operation

First-Time Capture: Researchers Watch Chollima Operators Live in Sophisticated Sandbox Trap
In a groundbreaking cybersecurity operation, researchers successfully infiltrated North Korea's notorious Lazarus Group hiring pipeline and watched their operators work in real-time—believing they had access to genuine developer laptops. Instead, the Famous Chollima division walked directly into a sophisticated honeypot designed to expose their tactics, tools, and infrastructure.
The joint investigation, led by Mauro Eldritch (founder of BCA LTD), threat intelligence initiative NorthScan, and interactive malware analysis platform ANY.RUN, represents the first documented case of North Korean APT operators being filmed conducting actual attack preparation activities.
The Setup: Becoming the Target
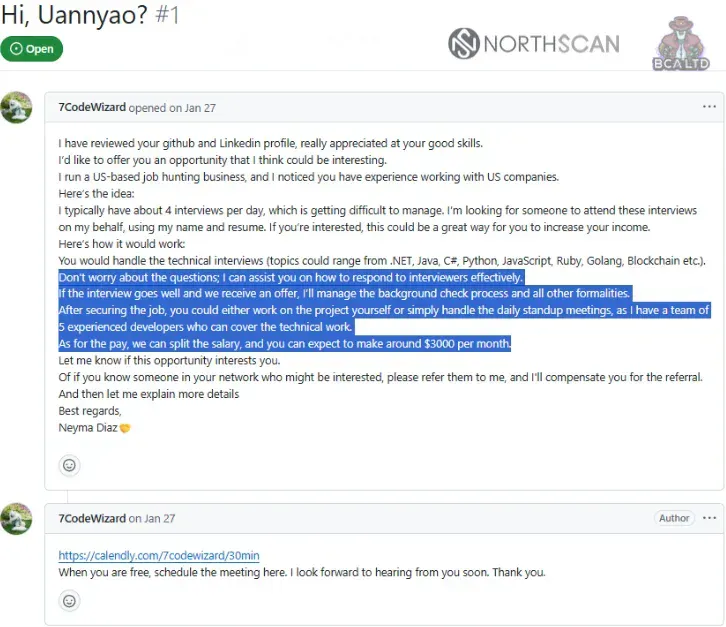
The operation began when Heiner García from NorthScan assumed the identity of "Andy Jones," a U.S.-based developer who had been targeted by a Lazarus recruiter operating under the alias "Aaron" (also known as "Blaze").
🔥 After months inside #Lazarus’ fake hiring pipeline, we achieved something never seen before: the full Famous Chollima attack cycle captured on video, including their tools, tactics and targets.
— BCA LTD (@BirminghamCyber) December 2, 2025
🤝 This wouldn’t have been possible without our friends at ANY RUN (@anyrun_app)… pic.twitter.com/mDivdZdHfn
The recruitment pitch followed a well-established pattern that has been used to infiltrate hundreds of Western companies: Blaze posed as a legitimate job-placement business, offering García 35% of a developer's salary in exchange for full access to his laptop, credentials, and identity documents.
The scheme's mechanics are straightforward but effective:
- Steal or borrow a legitimate identity
- Pass technical interviews using AI tools and coordinated answer-sharing
- Work remotely via the victim's laptop with 24/7 access
- Funnel salary payments back to the DPRK regime
García created a fabricated GitHub profile mimicking Andy Jones, complete with realistic repositories and development history. When Blaze requested complete access—including Social Security Number, identification documents, LinkedIn credentials, Gmail account, and persistent laptop availability—the research team moved to phase two.


The Trap: A Virtual "Laptop Farm"
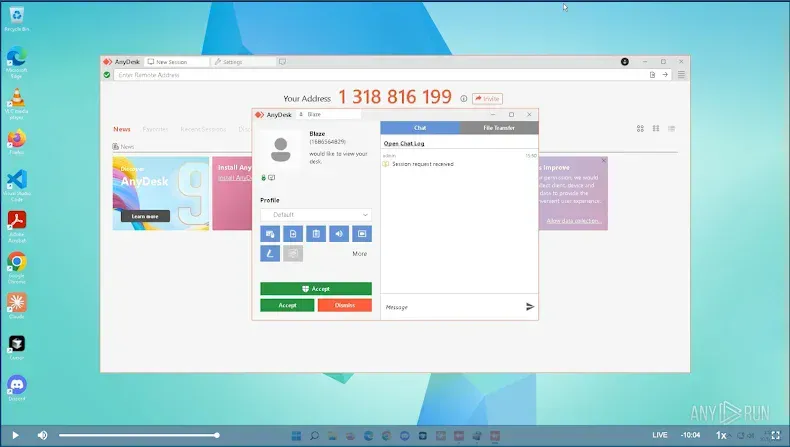
Rather than providing access to real hardware, Mauro Eldritch deployed ANY.RUN's Interactive Sandbox—highly sophisticated virtual machines configured to resemble fully active personal workstations. Each sandbox included:
- Realistic browsing history and developer tools
- U.S.-based residential proxy routing for authentic IP geolocation
- Complete usage patterns mimicking a working developer
- Full recording capabilities capturing every action
- The ability to simulate system crashes and throttle connectivity
The operators remained completely unaware they were working inside a controlled environment. Every keystroke, every tool deployment, every connection attempt—all captured for analysis.
What They Found: The Chollima Toolkit Exposed
The sandbox sessions revealed a lean but highly effective toolkit focused on identity takeover and persistent remote access rather than traditional malware deployment. Once the operators synced their Chrome browser profiles, researchers observed:
AI-Powered Job Automation
- Simplify Copilot: Automated job application submissions
- AiApply: Generated customized cover letters and responses
- Final Round AI: Produced interview answers in real-time
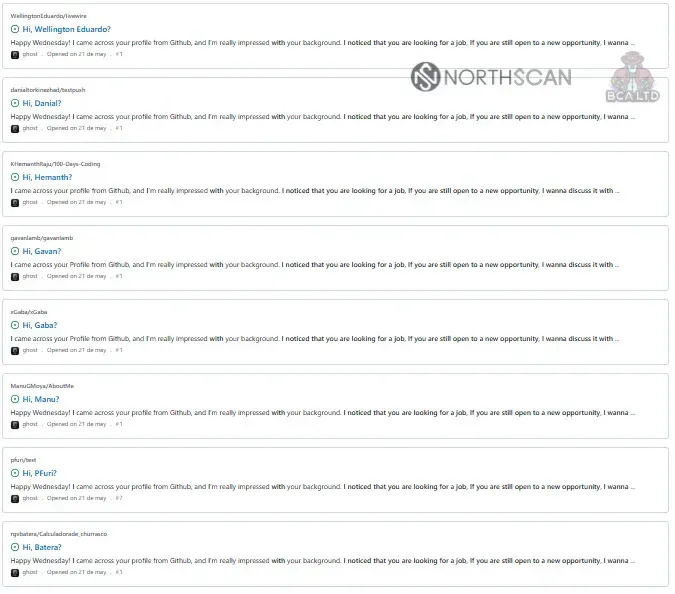
These tools enable North Korean IT workers to maintain multiple simultaneous job applications and interviews—some operators manage six to seven positions concurrently.
Two-Factor Authentication Bypass
Browser-based OTP generators (OTP.ee and Authenticator.cc) allowed operators to handle victims' multi-factor authentication once identity documents were collected, effectively bypassing one of the most common security controls.
Persistent Remote Access
Google Remote Desktop was configured via PowerShell scripts using a fixed PIN, providing continuous control of the host machine without requiring malware installation. This legitimate tool usage helps operators avoid detection by traditional security solutions.
System Reconnaissance
Standard Windows commands (dxdiag, systeminfo, whoami) were used to validate hardware specifications and environmental details—likely verifying the sandbox appeared legitimate before proceeding.
Infrastructure Patterns
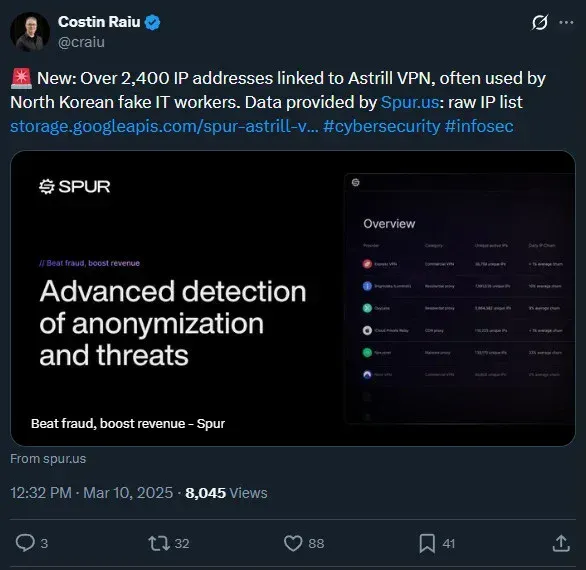
All connections consistently routed through Astrill VPN, a service repeatedly linked to previous Lazarus infrastructure in open-source intelligence reporting.
Perhaps most revealing: operators left a Notepad message requesting the "developer" upload identification documents, Social Security Number, and banking details—confirming the operation's ultimate goal of complete identity and workstation takeover without deploying a single piece of traditional malware.
The Scale of the Threat: A Global Epidemic
This operation exposed just one thread in a massive infiltration network. As we've previously documented in our analysis of North Korea's global cybercrime empire, the DPRK has evolved from conducting basic cyberattacks to operating the world's most sophisticated state-sponsored cybercrime enterprise. Recent statistics paint an alarming picture:
By the Numbers (2024-2025):
- Over 300 U.S. companies unknowingly employed North Korean IT workers between 2020-2022
- 320+ companies infiltrated in the past 12 months alone—a 220% increase year-over-year
- Several Fortune 500 companies compromised, with some estimates suggesting "nearly every major company" has been targeted
- $88 million generated over six years by a single 14-person operation
- $866,255 in revenue from just 10 of 64 infiltrated U.S. companies by one indicted group
- 64+ U.S. companies infiltrated by one five-person team
- 8,400 personnel working in North Korea's cyber divisions as of 2024 (up from 6,800 in 2022)
- Individual IT workers can earn $300,000 annually, with the DPRK regime retaining up to 90% of earnings
Geographic Expansion:
What began as a U.S.-focused operation has rapidly expanded globally. Researchers have identified active operations throughout:
- Europe: United Kingdom, Germany, Portugal, with increased targeting of defense industrial base companies
- Asia: South Korea, Vietnam, India, UAE
- Latin America: Costa Rica
- Middle East: Turkey, Dubai
The Famous Chollima division alone was linked to 304 incidents in 2024, with activity ramping up significantly in the latter half of the year.
Beyond IT worker infiltration, the Lazarus Group continues to conduct massive cryptocurrency heists. As documented in our comprehensive review of early 2025 cybersecurity incidents, North Korean actors allegedly stole over $1.46 billion in cryptocurrency from the Bybit exchange, highlighting the immense financial risk within the digital asset space.
The Famous Chollima Organization
The research identified a six-member team for this specific operation using the names Mateo, Julián, Aaron, Jesús, Sebastián, and Alfredo. However, multiple competing North Korean teams run simultaneous Famous Chollima operations—some with up to ten members—actively poaching potential victims from one another.
Famous Chollima (also tracked as WageMole) operates as part of the larger Lazarus Group umbrella, itself affiliated with North Korea's Reconnaissance General Bureau. The operation is run out of Department 53, which oversees the regime's cyber warfare capabilities.
Recruits come from elite institutions including Kim Chaek University of Technology and the University of Sciences in Pyongyang, trained in hacking techniques, foreign languages, and social engineering. They're deployed primarily to China, Russia, Cambodia, Nigeria, and the UAE, working under strict operational security protocols.
The Famous Chollima operation is part of a broader ecosystem. As detailed in our analysis of the global cybercrime empire, North Korea's cyber operations have become integrated into a sophisticated international network where state-sponsored operations and criminal enterprises converge.
Evolution of Tactics: AI as Force Multiplier
The schemes have evolved dramatically since their emergence during the COVID-19 pandemic's remote work expansion:
2024-2025 Tactical Innovations:
- Deepfake technology for video interviews and identity document manipulation
- Voice-changing software to mask accents and alter gender presentation
- AI-enhanced photographs making North Korean workers appear more professional
- Automated scripts allowing single operators to maintain multiple simultaneous positions
- BYOD exploitation: Increasingly targeting bring-your-own-device environments
- Virtualized infrastructure operations: Working within corporate virtual environments
- Escalating extortion: Recently terminated workers threatening to release proprietary source code or provide it to competitors
- "Laptop farms": As detailed in our investigation of North Korea's laptop farm remote job scam, U.S.-based locations where witting or unwitting Americans host laptops for remote North Korean workers
Beyond Financial Theft: Strategic Objectives
While revenue generation remains primary, researchers have identified three distinct operational goals:
1. Financial Revenue
Collecting multiple paychecks simultaneously to fund the regime's weapons programs, particularly nuclear and missile development.
2. Intelligence Collection
Gaining prolonged access to sensitive corporate data, intellectual property, and in some cases, U.S. military technology under export control regulations.
3. Extortion and Ransomware
Stealing source code and proprietary data, then demanding payment to prevent public release or sale to competitors. This tactic has intensified following increased U.S. law enforcement actions. Notably, Microsoft's threat intelligence revealed that Moonstone Sleet, a North Korean state-sponsored threat actor, has been observed deploying Qilin ransomware, representing a dangerous convergence of financially motivated cybercrime and state-sponsored operations.
Warning Signs: Detection Indicators
Organizations should watch for these red flags during hiring and onboarding:
Interview Stage:
- Reluctance to appear on video camera
- AI-generated or suspiciously professional headshots
- References that seem coordinated or use similar language patterns
- Technical knowledge that seems scripted or relies heavily on prepared answers
- Multiple candidates with similar backgrounds from the same recruiting source
Employment Stage:
- Request for company hardware to be shipped to unfamiliar addresses
- Use of "laptop farms" or proxy shipping addresses
- Unusual VPN usage patterns, especially Astrill VPN
- Access requests immediately upon hiring, particularly to sensitive systems
- Working hours inconsistent with stated timezone
- Multiple devices or IP addresses used to access company resources
- Installation of remote desktop tools like Google Remote Desktop
Identity Verification:
- Inconsistencies in identification documents
- Social Security Numbers that fail validation checks
- LinkedIn profiles with limited connection history or recent creation dates
- GitHub repositories that appear copied or have suspicious commit patterns
- Banking information that doesn't match the employee's stated location
What This Means for Your Organization
The BCA LTD-NorthScan-ANY.RUN operation demonstrates that awareness alone is insufficient. North Korean IT workers are highly sophisticated, well-funded, and continuously evolving their tactics.
Recommended Actions:
1. Enhanced Identity Verification
- Implement specialized identity document verification services
- Cross-reference multiple data sources during background checks
- Verify educational credentials directly with institutions
- Conduct behavioral interviews that can't be easily scripted
2. Technical Controls
- Monitor for unauthorized remote access tool installations
- Implement robust endpoint detection and response solutions
- Track VPN usage patterns and flag uncommon services
- Restrict immediate access to sensitive systems for new hires
- Deploy data loss prevention solutions
3. Security Awareness
- Train hiring managers and recruiters on common tactics
- Establish clear escalation procedures for suspicious activity
- Create safe channels for employees to report unusual recruitment approaches
- Conduct regular "insider threat" tabletop exercises
4. Organizational Policies
- Implement progressive access controls (not full access on day one)
- Require hardware return tracking with verified addresses
- Establish clear protocols for remote employee device management
- Consider additional scrutiny for fully remote positions requiring sensitive access
5. Incident Response Planning
- Develop specific playbooks for suspected North Korean IT worker infiltration
- Establish relationships with federal law enforcement (FBI, Department of Justice)
- Plan for potential data exfiltration scenarios
- Prepare communications strategies for disclosure if compromised
Government Response and Legal Implications
The U.S. government has dramatically increased enforcement actions:
Recent Actions (2024-2025):
- December 2024: DOJ indicted 14 North Koreans for generating $88 million over six years
- January 2025: DOJ indicted two Americans operating a scheme placing operatives in 60+ U.S. companies
- June 2025: Sweeping enforcement including searches of 29 "laptop farms" across 16 states, seizure of 29 financial accounts, and 21 fraudulent websites
- November 2025: Four guilty pleas and over $15 million in civil forfeitures
- Multiple 2025 OFAC sanctions: Targeting facilitators in Russia, China, India, and Burma
Legal exposure for companies includes:
- International sanctions violations (OFAC penalties)
- Export control violations if sensitive technology was accessed
- Data breach notification requirements
- Shareholder lawsuits for inadequate security controls
- Reputational damage and customer loss
The Road Ahead
The Lazarus Group has a long history of devastating cyberattacks. As documented in our analysis of the 15 most devastating data breaches in history, the North Korea-linked Lazarus Group used the EternalBlue exploit to launch the WannaCry ransomware attack that crippled NHS hospitals and caused over $4 billion in global damages—highlighting the group's capability for both targeted infiltration and mass disruption.
CrowdStrike predicts Famous Chollima will continue and potentially accelerate operations through 2025 given:
- Limited impact from federal prosecutions on operational capability
- Financial success of the scheme (hundreds of millions generated)
- Expansion into new geographic markets with less awareness
- Continuous tactical evolution leveraging AI and automation
- Increased desperation as sanctions tighten on the DPRK regime
The ANY.RUN sandbox footage—set for public release December 4th—will provide unprecedented insight into North Korean cyber operations. It represents not just a technical achievement, but a warning: these aren't distant state-sponsored hackers launching remote exploits. They're applying for jobs at your company, passing your interviews, and gaining access to your most sensitive systems.
The most effective defense isn't a single technical control or policy change. It's a comprehensive, cross-functional approach combining enhanced verification, technical monitoring, security awareness, and incident response planning.
Remote hiring has become a quiet but reliable entry point for identity-based threats. An infiltrator can access internal dashboards, sensitive business data, and manager-level accounts that carry real operational impact. The difference between stopping an approach early and dealing with a full-blown internal compromise often comes down to awareness and having safe channels to verify suspicious activity.
Key Takeaways
✓ First-Ever Live Capture: BCA LTD, NorthScan, and ANY.RUN documented complete Famous Chollima attack cycle in real-time using sophisticated honeypot sandboxes
✓ Massive Scale: 320+ companies infiltrated in past 12 months with 220% year-over-year growth; nearly every Fortune 500 targeted
✓ Tool Evolution: Operators use AI-powered job automation, deepfake identity documents, voice modification, and legitimate remote access tools instead of malware
✓ Triple Threat: Beyond revenue generation, operations include intelligence collection and escalating extortion/ransomware tactics
✓ Global Expansion: Operations expanding from U.S. focus into Europe, Asia, and targeting defense industrial base companies
✓ Detection Challenges: Legitimate tool usage, sophisticated social engineering, and continuous tactical evolution make traditional security controls insufficient
✓ Legal Exposure: Companies face sanctions violations, export control penalties, breach notifications, and reputational damage
✓ Required Response: Multi-layered defense combining enhanced identity verification, technical monitoring, security awareness training, and incident response planning
Additional Resources
- FBI Public Service Announcements: May 2024 and January 2025 warnings on North Korean IT workers
- Unit 42 Threat Research Report: Comprehensive DPRK IT worker risk matrix and detection strategies
- Microsoft Threat Intelligence: Detailed analysis of evolving TTPs including AI-enhanced operations
- Google Cloud Threat Intelligence: DPRK IT worker expansion tracking and mitigation recommendations
- ANY.RUN Blog: Full video release of Famous Chollima operations (December 4th, 2025)
This investigation demonstrates why cybersecurity requires constant vigilance and collaboration across the industry. As threat actors become more sophisticated, so too must our defensive strategies—and our willingness to share intelligence that protects the entire community.
About This Research
This article synthesizes reporting from the groundbreaking BCA LTD-NorthScan-ANY.RUN investigation alongside public data from the U.S. Department of Justice, FBI, Microsoft Threat Intelligence, Google Cloud, CrowdStrike, Palo Alto Networks Unit 42, Mandiant, and other industry sources. The operation represents months of embedded research within Lazarus Group's hiring pipeline, resulting in unprecedented documentation of Famous Chollima's complete attack cycle.
🇰🇵 Meet Aaron AKA Blaze, a #Lazarus recruiter.
— Mauro Eldritch 🏴☠️ (@MauroEldritch) December 2, 2025
💵 He offered 35% of a salary if we let his operators use our laptops "to work in" (infiltrate) Western companies.
▶️ We gave him ANYRUN sandboxes, recording everything they did.
⬇️ Full article below. Full disclosure on Dec 4. pic.twitter.com/iOjBVbBpWi
🎥 After months tracking #DPRK IT worker fake hiring operations, we had the chance to collaborate on something rare: the full Famous Chollima attack cycle captured on video – tools, tactics, and targets, end-to-end.
— BlockOSINT (@0xfigo) December 2, 2025
🙏 Huge thanks to @MauroEldritch and the ANY RUN team… https://t.co/5ZFag5RcfV
For organizations concerned about potential North Korean IT worker infiltration, consult with qualified cybersecurity professionals and consider engaging federal law enforcement through FBI field offices or the Internet Crime Complaint Center (IC3).





