Operation PowerOff: A Global Crackdown on Criminal DDoS Services

Executive Summary
Operation PowerOff represents one of the most comprehensive and sustained international law enforcement efforts against cybercrime infrastructure in recent history. Since its inception in 2018, this ongoing joint operation by the FBI, EUROPOL, the Dutch National Police Corps, German Federal Criminal Police Office, Poland Cybercrime Police and the UK National Crime Agency has successfully dismantled dozens of "booter/stresser" services offering DDoS attack services for hire. The operation has fundamentally disrupted the criminal ecosystem surrounding Distributed Denial of Service (DDoS) attacks, resulting in over 75 domain seizures, numerous arrests, and significant deterrence efforts against cybercriminals worldwide.
Understanding DDoS-for-Hire Services
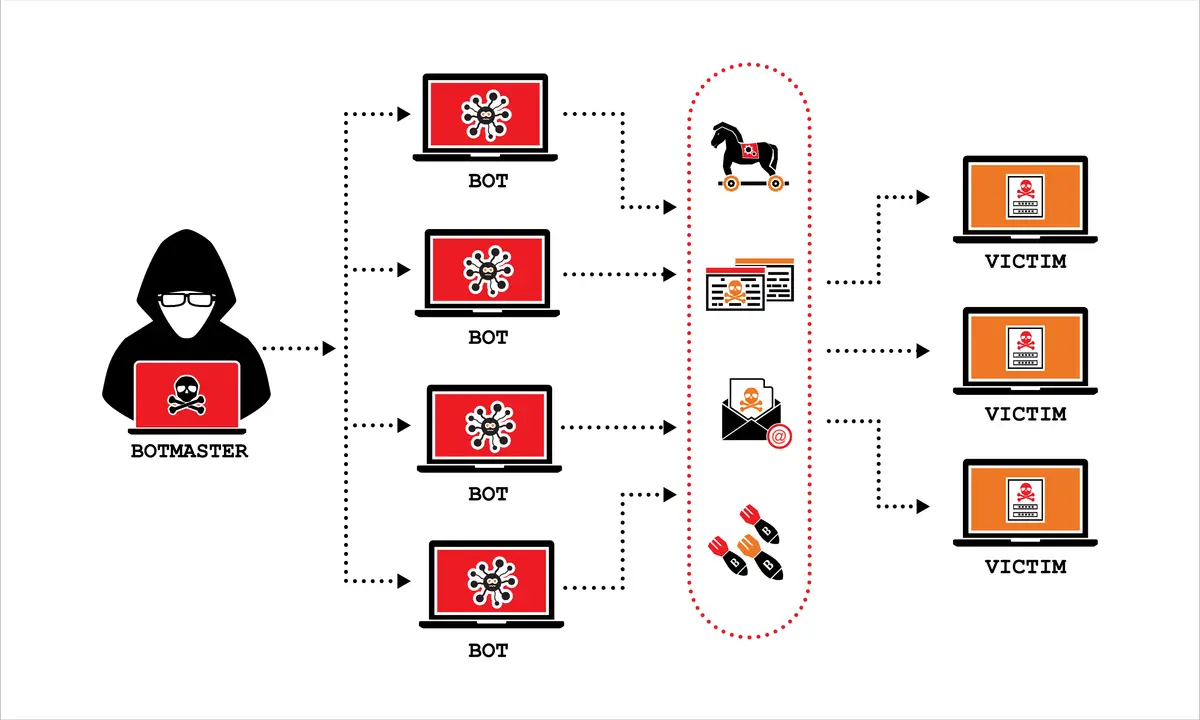
DDoS-for-hire services, commonly known as "booters" or "stressers," represent a significant threat to internet infrastructure and digital commerce. These services are obtained through a monetary transaction, usually in the form of online payment services or virtual currency, and have no legitimate use; they are designed to overwhelm server resources or to exceed bandwidth capacities.

These platforms let cybercriminals and hacktivists overwhelm target websites and web-based services with traffic and render them inaccessible. The services typically operate with user-friendly interfaces that require no technical expertise, allowing individuals to input target IP addresses, select attack types and duration, and pay fees as low as 10 euros for sophisticated attacks.
DDoS attacks can act as a smokescreen, masking other cybercriminal attempts to compromise systems, potentially leading to data breaches or the exploitation of vulnerabilities. The economic impact is substantial, with downtime costs estimated to average around $40,000 USD per hour.
Operation Timeline and Major Milestones
Phase 1: Initial Takedowns (2018)
In 2018, the FBI closed down 15 DDoS websites with the Dutch National Police Corps. This initial phase established the foundation for international cooperation and demonstrated the viability of coordinated cross-border enforcement actions against DDoS services.

Phase 2: Major Expansion (2022)
The operation significantly expanded in December 2022, marking a new level of international coordination. On December 14, 2022, resuming this collaboration, the FBI and Department of Justice announced that they had closed multiple websites offering DDoS-for-hire services. This phase saw the seizure of 48 domains and resulted in six arrests across multiple U.S. states. The same was said about Quantum, one of the platforms shuttered as part of the FBI's 50-domain PowerOff seizures in 2022, which also led to six arrests.
Phase 3: Sustained Operations (2023-2024)
Throughout 2023 and 2024, Operation PowerOff maintained consistent pressure on DDoS-for-hire services. Notable actions included the takedown of major platforms such as DigitalStress in July 2024 and Dstat.cc, described as one of the largest platforms of its kind.

Phase 4: Holiday Crackdown (December 2024)
This multifaceted operation, coordinated by Europol and involving 15 countries, targeted all levels of those engaged in this crime ahead of annual Christmas attacks. Law enforcement agencies from 15 countries have taken 27 DDoS-for-hire services offline, also known as "booters" or "stressers," arrested three administrators, and identified 300 customers of the platforms.
Phase 5: Continued Enforcement (2025)
The Justice Department today announced the court-authorized seizure of nine internet domains associated with some of the world's leading DDoS-for-hire services. Poland's Central Cybercrime Bureau simultaneously announced the arrests of four administrators of such services. More than 75 domains associated with such services have been seized.
International Coordination and Participating Agencies
Operation PowerOff exemplifies modern international law enforcement cooperation. The operation has involved agencies from multiple countries including:
- United States: FBI, Department of Justice, Defense Criminal Investigative Service (DCIS), Homeland Security Investigations
- Europe: EUROPOL coordination, German Federal Criminal Police Office (BKA), Dutch National Police Corps, UK National Crime Agency
- Other Nations: Australia, Canada, Japan, and the US got in on the act too, making it a truly international effort.
Beteiligt an dieser Kooperation sind Polizeibehörden aus der ganzen Welt. (Participating in this cooperation are police authorities from around the world.)
Operational Methodology and Legal Framework
Technical Approaches
Law enforcement agencies have employed sophisticated investigative techniques, including crypto-tracing, forensic analysis of seized servers, and infiltration of criminal networks. Europol says the takedowns and arrests were made possible by its analytical support, crypto-tracing information, and various forms of forensic investigation assistance provided by its specialists at the Joint Cybercrime Action Taskforce (J-CAT).

Legal Consequences
The use of booter and stresser services to conduct a DDoS attack is punishable under the Computer Fraud and Abuse Act (18 U.S.C. § 1030). Penalties can include significant prison sentences and substantial financial penalties.
Prevention and Deterrence
Beyond enforcement actions, Operation PowerOff has implemented innovative deterrence strategies. In conjunction with the website seizures, Homeland Security Investigations, DCIS, and the Netherlands Police have launched an advertising campaign using targeted placement ads in search engines, which are triggered by keywords associated with DDoS activities.
Those who search for DDoS-for-hire tools on Google will be served the ads, and those who look for YouTube tutorials on how to use them will likewise receive similar messaging.

Impact Assessment and Results
Quantitative Impact
The numbers demonstrate the operation's significant scope:
- Over 75 domains seized across multiple phases
- Hundreds of arrests and investigations initiated
- Over 300 users of the platforms have been identified in the latest phase alone
- The FBI claimed that these websites offered services designed to slow down websites relating to gaming. The FBI also noted that these services had heavy use, claiming that "Quantum", one of the seized services, was used to launch 50,000 attacks.

Victim Protection
Booter services such as those named in this action allegedly attacked a wide array of victims in the United States and abroad, including schools, government agencies, gaming platforms, and millions of people. The operation has directly protected critical infrastructure, educational institutions, and commercial enterprises from ongoing attacks.
Industry Collaboration and Private Sector Partnership
Private sector involvement has been crucial to the operation's success. Multiple companies, including Cloudflare, PayPal, and DigitalOcean provided information to the FBI to assist in the seizure. Flashpoint is proud to have contributed to this investigation as part of an alliance of government agencies and private sector partners.

Challenges and Criminal Adaptation
Despite the operation's successes, cybercriminals continue to adapt. However, the question of whether such takedowns are 'working' is more complex. Historically, efforts like these do disrupt criminal operations temporarily and send a strong signal that these activities won't be tolerated. Yet, they don't always lead to a lasting reduction in the underlying issue.
Cybercriminals often adapt quickly, setting up new services or switching tactics. For instance, decentralized platforms or private networks might emerge as replacements. This reality necessitates the ongoing nature of Operation PowerOff.
Current Status and Future Outlook
As of November 2024, Operation PowerOFF activities were still ongoing, with further websites being seized and prosecutions continuing. The operation maintains an official website at operation-poweroff.com, where it states: "On this domain we keep track of the ongoing actions and share relevant updates. Operation PowerOFF continues."
Educational and Deterrence Efforts
Beyond enforcement, the operation emphasizes education and deterrence. In addition to these digital interventions, other methods such as knock-and-talks, more than 250 warning letters, and over 2,000 emails will be used to reach users of illegal services.
"We know that Booter services are an attractive entry-level cyber crime, and users can go on to even more serious offending." This recognition drives comprehensive intervention strategies targeting users at all levels.
Conclusion
Operation PowerOff represents a paradigm shift in international cybercrime enforcement, demonstrating that sustained, coordinated efforts can significantly disrupt criminal infrastructure. While challenges remain in the constantly evolving cybercrime landscape, the operation has established important precedents for international cooperation and comprehensive approaches to digital crime prevention.
"Booter services facilitate cyberattacks that harm victims and compromise everyone's ability to access the internet," as noted by United States Attorney Bill Essayli. "This week's sweeping law enforcement activity is a major step in our ongoing efforts to eradicate criminal conduct that threatens the internet's infrastructure and our ability to function in a digital world."
The success of Operation PowerOff underscores the critical importance of international cooperation in combating transnational cybercrime and protecting global digital infrastructure. As the operation continues, it serves as both a deterrent to would-be cybercriminals and a model for future international law enforcement initiatives in cyberspace.
For more information about DDoS attacks or to report cybercrime, the FBI encourages victims to contact their local FBI field office or file a complaint with the Internet Crime Complaint Center (IC3) at www.ic3.gov.














