Operation SIMCARTEL: Europe Dismantles Massive Cybercrime-as-a-Service Network

Seven arrests, 49 million fake accounts, and €4.9 million in losses: How European law enforcement took down a sophisticated SIM box fraud operation
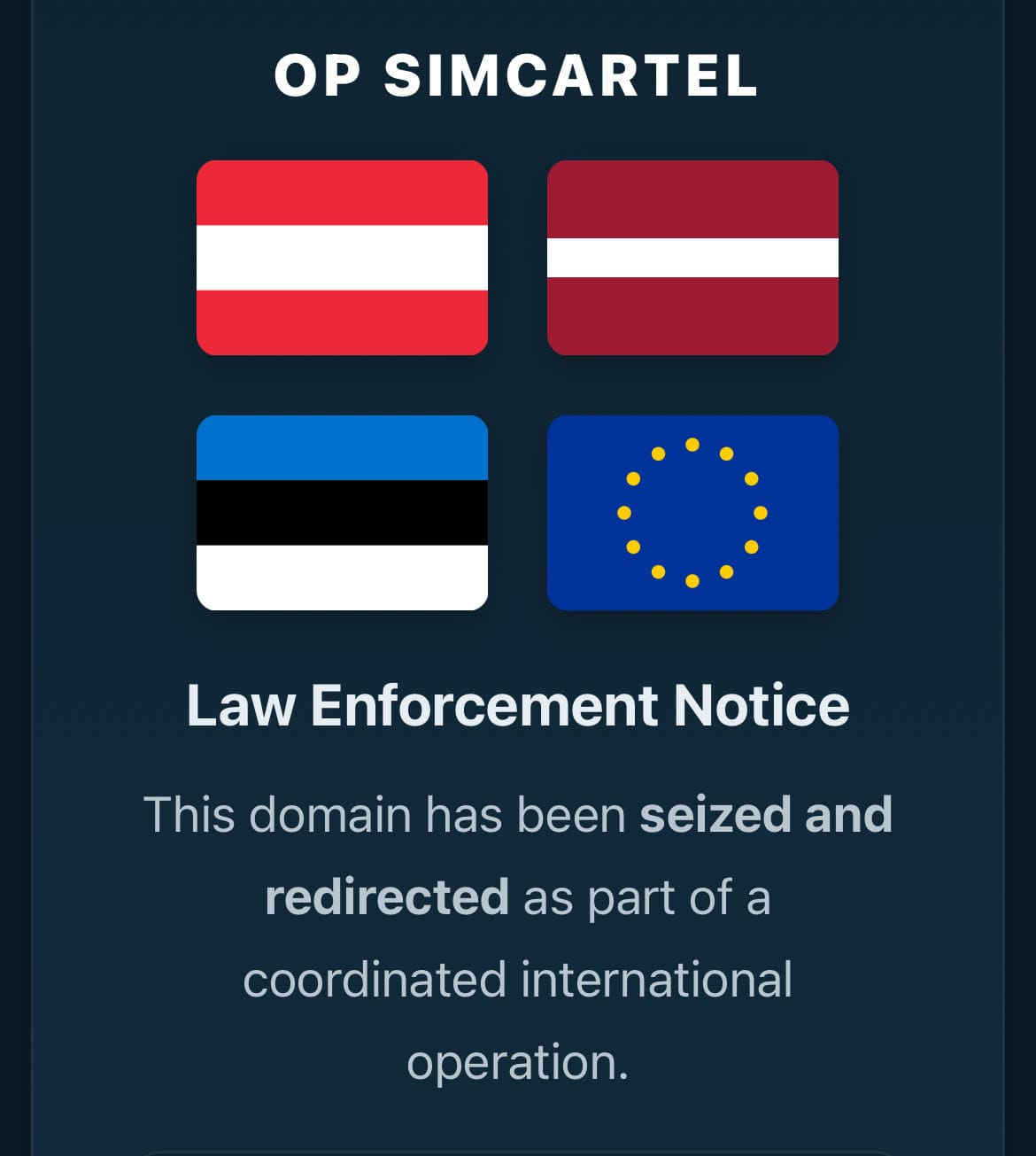
In one of the most significant cybercrime takedowns of 2025, European law enforcement agencies have dismantled a sophisticated criminal network that provided the technical infrastructure for thousands of online frauds across the continent. Operation SIMCARTEL, which culminated on October 10, resulted in seven arrests and the seizure of an extensive illegal telecommunications operation that enabled criminals to hide their identities while perpetrating a wide range of cybercrimes.

The Scale of the Operation
The numbers tell a staggering story. Coordinated raids across Latvia, Austria, Estonia, and Finland uncovered:
- 1,200 SIM box devices operating simultaneously with 40,000 active SIM cards
- Five servers hosting the criminal infrastructure
- Two websites (gogetsms.com and apisim.com) offering cybercrime services
- 49 million fake online accounts created through the service
- Over 3,200 fraud cases linked directly to the operation
- €4.9 million in confirmed financial losses (€4.5 million in Austria alone, €420,000 in Latvia)
Authorities also froze €431,000 and $333,000 in bank and cryptocurrency accounts, and seized four luxury vehicles from the suspects.
Understanding SIM Box Fraud
At the heart of this operation was what's known as a "SIM box" or "SIM farm" — a sophisticated telecommunications device that houses hundreds or thousands of SIM cards. While SIM boxes have legitimate uses in the telecommunications industry, cybercriminals have weaponized this technology to create a lucrative cybercrime-as-a-service business model.





How It Works
The criminal operation functioned through a deceptively simple but highly effective system:
- Infrastructure Setup: The suspects maintained approximately 1,200 SIM box devices across multiple locations, each loaded with dozens of SIM cards from different mobile operators in over 80 countries.
- Service Offering: Through their websites, gogetsms.com and apisim.com, the group rented out phone numbers to criminals worldwide. These numbers appeared to be legitimate local phone numbers from various countries.
- Account Creation: Criminals used these temporary phone numbers to verify and create accounts on social media platforms, messaging services, financial platforms, and e-commerce sites — all while hiding their true identity and location.
- Scale of Operation: The system was designed for automation, allowing the creation of millions of accounts rapidly. Investigators discovered the infrastructure had been used to create approximately 49 million fake online accounts.

The Cybercrime-as-a-Service Model
What made this operation particularly dangerous was its business model. Rather than committing fraud directly, the suspects provided essential infrastructure that enabled other criminals to operate. This "cybercrime-as-a-service" approach has become increasingly common, lowering the technical barriers for aspiring cybercriminals.
The service allowed customers to:
- Create anonymous accounts without revealing their actual location
- Bypass security measures that require phone verification
- Operate at massive scale without maintaining their own infrastructure
- Avoid detection by constantly rotating through different phone numbers
The Crimes It Enabled
The fake accounts and phone numbers provided by this service were linked to a disturbing range of criminal activities:
- Phishing and smishing campaigns targeting unsuspecting victims
- Investment fraud schemes promising unrealistic returns
- "Daughter-son" scams where criminals impersonated family members in distress
- Fake online shops and banking sites designed to steal credentials
- Police impersonation to intimidate and extort victims
- Marketplace fraud on legitimate e-commerce platforms
- Extortion schemes
- Migrant smuggling operations
- Distribution of child sexual abuse material
The Takedown
International Cooperation
Operation SIMCARTEL exemplified international law enforcement cooperation at its finest. The operation involved:
- Europol (European Union Agency for Law Enforcement Cooperation) coordinating the overall effort
- Eurojust (European Union Agency for Criminal Justice Cooperation) facilitating legal cooperation
- Austrian law enforcement investigating over 1,700 fraud cases
- Latvian State Police Cybercrime Combating Directorate and the elite Counterterrorism Unit "Omega"
- Estonian authorities tracking cross-border criminal activity
- Finnish police contributing to the investigation
- Shadowserver Foundation assisting with the digital infrastructure takedown
The Raids
On October 10, 2025, law enforcement conducted 26 coordinated searches across multiple locations in Latvia. The Latvian State Police's Counterterrorism Unit "Omega" led the dramatic raids, which were captured on video showing heavily armed officers breaching doors of suspected locations.

The Suspects
Seven individuals were arrested during the operation:
- Five Latvian nationals were detained in Latvia, including the suspected organizer of the operation (born 1977) and technical staff members (born 1982, 1987, and 1970)
- Two additional suspects were apprehended as the investigation expanded
- One of those detained had been previously declared internationally wanted by Estonian authorities for other serious crimes
Three suspects were subjected to non-custodial security measures, while one (born 1982) was remanded in custody. All suspects face charges related to enabling cybercrime on a massive scale.
The Technical Infrastructure
The sophistication of the operation was evident in its technical setup. The 1,200 SIM box devices were strategically distributed to provide phone numbers from more than 80 different countries, allowing criminals to appear as though they were operating from virtually anywhere in the world.
The seized servers contained comprehensive records of the operation, which forensic analysts are now examining to identify customers of the illegal service. This could lead to a secondary wave of investigations targeting those who purchased and used the criminal infrastructure.
The websites gogetsms.com and apisim.com have been seized and now display law enforcement banners, a common practice in cybercrime takedowns to notify would-be customers that the service has been shut down and is under investigation.
Financial Impact
The direct financial losses documented by investigators tell only part of the story:
- Austria: €4.5 million in losses from approximately 1,700 fraud cases
- Latvia: €420,000 in losses from 1,500 fraud cases
- Total documented: Nearly €5 million, though authorities believe the actual global impact is significantly higher
Beyond direct theft, the operation cost:
- Legitimate businesses money through chargebacks and fraud prevention
- Platform operators resources fighting fake accounts and abuse
- Governments tax revenue that was diverted through criminal channels
- Victims emotional trauma and time resolving identity theft issues
The Broader Implications
The Cybercrime Supply Chain
Operation SIMCARTEL reveals the industrialized nature of modern cybercrime. Just as legitimate businesses rely on service providers and suppliers, cybercriminals have developed a robust supply chain where specialists provide infrastructure, tools, and services to those who lack technical capabilities.
This "crime-as-a-service" model has several troubling characteristics:
- Lower Barriers to Entry: Criminals no longer need technical expertise to commit sophisticated cybercrimes
- Scalability: Service providers can serve thousands of customers simultaneously
- Resilience: When one service is shut down, criminals simply move to another provider
- Specialization: Different groups focus on their expertise, making operations more efficient
The SIM Box Problem
SIM box fraud has become a significant challenge for the global telecommunications industry. The Communications Fraud Control Association estimates that interconnect bypass fraud (which includes SIM box fraud) costs the industry approximately $3.11 billion annually, representing 7.8% of total telecom fraud losses.
The problem is particularly acute in regions with:
- High international call termination rates
- Weak SIM card registration requirements
- Limited know-your-customer (KYC) enforcement
- Insufficient fraud detection systems
Privacy and Security Concerns
The operation also highlighted serious privacy and security implications. When criminals can create millions of fake accounts using hijacked or fraudulently obtained SIM cards, it:
- Undermines platform trust and safety measures
- Makes it harder to trace criminal activity
- Puts legitimate SIM card holders at risk
- Compromises national security by enabling unmonitored communications
- Facilitates identity theft on a massive scale
What Happens Next
Ongoing Investigations
Europol has emphasized that the full scale of the criminal network is still under investigation. With 49 million fake accounts traced to this operation, investigators face the daunting task of:
- Analyzing seized servers to identify customers of the service
- Tracing financial flows through cryptocurrency and traditional banking
- Working with platform providers to identify and remove fake accounts
- Building cases against secondary suspects who used the service
- Determining the full extent of criminal activity enabled by the infrastructure
The Whack-a-Mole Challenge
Law enforcement officials have cautioned that while Operation SIMCARTEL was successful, cybercriminals are already seeking new infrastructure. The nature of the internet means that similar services can potentially resurface elsewhere, requiring constant vigilance from both law enforcement and the private sector.
Authorities have encouraged:
- Platform providers to strengthen verification processes and monitoring
- Telecommunications companies to implement better fraud detection
- Financial institutions to watch for patterns associated with this type of fraud
- Private sector partners to report suspicious activity
- International cooperation to continue and expand
Prevention and Detection
For telecommunications operators, detecting SIM box fraud requires:
- Call pattern analysis to identify unusual activity
- Location monitoring to flag stationary SIM cards
- Voice fingerprinting to detect unauthorized routing
- User behavior profiling to spot anomalies
- International data sharing to track cross-border operations
For individuals and businesses, awareness is key:
- Be skeptical of unsolicited communications, even from seemingly local numbers
- Verify unexpected requests through alternative channels
- Report suspicious messages and calls to authorities
- Use multi-factor authentication beyond just SMS
- Monitor accounts regularly for unauthorized access
Conclusion
Operation SIMCARTEL represents both a significant victory for law enforcement and a sobering reminder of the sophisticated infrastructure supporting modern cybercrime. The arrest of seven suspects and the dismantling of a network that created 49 million fake accounts demonstrates what's possible when international agencies coordinate effectively.
However, the operation also reveals the challenges ahead. As long as there's demand for anonymous online accounts and criminal services, entrepreneurs in the cybercrime economy will seek to provide supply. The cybercrime-as-a-service model has proven too lucrative and too resilient to disappear with any single takedown.
The success of Operation SIMCARTEL relied on several factors that must be replicated in future efforts:
- Strong international cooperation
- Technical expertise in cybercrime investigation
- Coordination between multiple agencies and jurisdictions
- Support from private sector partners
- Adequate legal frameworks for cross-border prosecution
As investigators continue to analyze the seized infrastructure and build cases against customers of the service, the operation may yield additional arrests and provide valuable intelligence about the broader cybercrime ecosystem. For now, it stands as a reminder that behind many of the scams and frauds people encounter online is a professional, industrialized criminal infrastructure — and that taking down that infrastructure requires equally professional and coordinated law enforcement response.
The message from Operation SIMCARTEL is clear: cybercrime-as-a-service operations may seem untouchable, operating across borders and behind layers of technical obfuscation, but with determination and international cooperation, they can be dismantled. The seven suspects now in custody, the millions in assets frozen, and the infrastructure seized represent not just one operation's end, but a warning to others operating in the cybercrime supply chain.
Key Takeaways:
- Operation SIMCARTEL dismantled a major cybercrime infrastructure operation
- 7 arrested, 49 million fake accounts linked to the service
- €4.9 million in documented losses from over 3,200 fraud cases
- International cooperation was key to the operation's success
- The cybercrime-as-a-service model remains a significant threat
- Continued vigilance and cooperation needed to prevent similar operations from emerging
For More Information:
- Europol: www.europol.europa.eu
- Report cybercrime: Your local law enforcement or national cybercrime center
- Protect yourself: Use strong authentication, verify unexpected requests, report suspicious activity








