Overview of Phobos and 8Base Ransomware - The Shakedown

Phobos ransomware, first identified in 2019, emerged as an evolution of the Dharma/CrySiS ransomware family[2][14]. Operating under a Ransomware-as-a-Service (RaaS) model, it allowed affiliates to license its malware for attacks targeting small-to-medium businesses (SMBs), government agencies, healthcare, and critical infrastructure[2][12]. Phobos typically infiltrated networks via compromised Remote Desktop Protocol (RDP) connections, phishing emails, or brute-force attacks[2][7]. Its encryption process combines AES-256 and RSA-1024 algorithms, rendering files inaccessible without a decryption key[7][23].





8Base, active since 2022, gained notoriety in 2023 for its aggressive double-extortion tactics: encrypting data and threatening to leak stolen files[6][9]. While initially linked to RansomHouse due to ransom note similarities[15][38], 8Base primarily used a customized variant of Phobos ransomware (version 2.9.1), appending the .8base extension to encrypted files[15][38]. The group targeted SMBs in the U.S., Brazil, and the U.K., focusing on industries like finance, manufacturing, and healthcare[6][13].


Key Tactics and Techniques
- Initial Access:
- Phobos: Exploited exposed RDP services and phishing campaigns[2][12].
- 8Base: Leveraged phishing emails, initial access brokers, and tools like SmokeLoader for payload delivery[6][38].
- Evasion and Persistence:
- Both groups disabled security tools (e.g., Windows Defender), deleted backups, and modified registry entries to maintain access[6][12].
- 8Base used SystemBC, a proxy/RAT tool, to mask command-and-control traffic[15][39].
- Encryption and Extortion:
- Phobos encrypted local and network drives, using hardcoded keys for offline encryption[2][23].
- 8Base employed AES-256 in CBC mode for rapid encryption and modified firewall rules to evade detection[11][13].
- Monetization:
- Phobos affiliates demanded ransoms averaging $18,755[7].
- 8Base escalated demands through public shaming on their leak site, "Space Bears," and negotiated payments via email or Telegram[9][36].
The 2025 Takedown Operation
On February 10, 2025, a coordinated international law enforcement operation led to:
- Arrests: Four Russian nationals linked to 8Base were arrested in Phuket, Thailand, following Interpol warrants issued by Swiss and U.S. authorities[35][36]. They allegedly stole $16 million from 1,000+ victims globally[35].
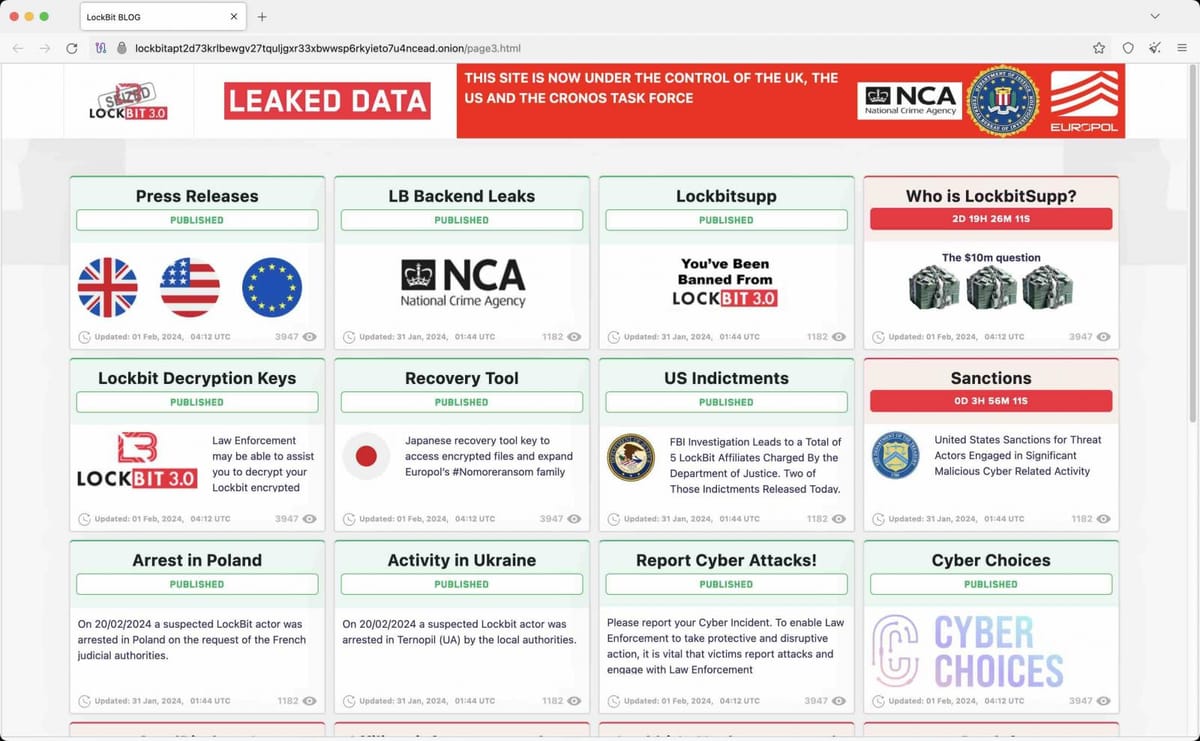
- Infrastructure Seizure: The 8Base leak site was seized by German authorities, replaced with a takedown notice from Europol, the FBI, and 14 other agencies[18][35].
- Disruption: Over 400 companies were warned of impending attacks, and Phobos/8Base operations saw a sharp decline post-operation[35][36].

Timeline of Phobos Ransomware Events
- 2019 (Early): Phobos ransomware is first identified as a variant of the CrySis/Dharma ransomware family. It begins operations, evolving into a prolific ransomware strain. It operates under a Ransomware-as-a-Service (RaaS) model, allowing other cybercriminals to distribute the malware.
- May 2019: Phobos ransomware incidents impacting state, local, tribal, and territorial (SLTT) governments are regularly reported to the MS-ISAC. These incidents target municipal and county governments, emergency services, education, public healthcare, and other critical infrastructure entities.
- 2019 Onward: Phobos variants such as Backmydata, Devos, Eight, Elking, and Faust emerge, targeting various sectors worldwide, including government, healthcare, education, and critical infrastructure.
- 2019 - Present: Phobos uses a hardcoded RSA public key across variants, making decryption without the attacker's private key nearly impossible.
- June 2021: Medusa ransomware group becomes active.
- September - November 2023: FBI and CISA investigations uncover IOCs (Indicators of Compromise) related to Phobos ransomware attacks.
- October 2023: Phobos actors' file hashes are observed
- November 2023: Qualys Threat Research identifies Phobos ransomware impersonating VX-Underground.
- November 2023: Phobos actors' file hashes from open source are identified.
- February 29, 2024: The FBI, CISA, and MS-ISAC release a joint Cybersecurity Advisory (CSA) AA24-060A to disseminate known TTPs (Tactics, Techniques, and Procedures) and IOCs (Indicators of Compromise) associated with Phobos ransomware.
- March 27, 2024: Avertium publishes a resource on Phobos ransomware, detailing tactics, techniques, and protective measures.
- August 21-27, 2024: During this week, ransomware activity shows alarming trends, with 97 victims across various industries and countries.
- February 7, 2025: The Japanese Cabinet approved a draft legislation introducing "active cyber defense" measures to bolster the nation's cybersecurity framework.
- February 10, 2025: Breached Company publishes an overview of Phobos and 8Base Ransomware.
- February 11, 2025: Key figures behind Phobos and 8Base ransomware are arrested in an international cybercrime crackdown.
- 2020–2025: Analysis of breaches from this time period reveals common methods attackers use to exploit vulnerabilities.
Connections Between Phobos and 8Base
- Shared Codebase: 8Base utilized Phobos’ encryption mechanisms and RaaS infrastructure, customizing it for double extortion[15][38].
- Affiliate Overlap: Both groups relied on initial access brokers and shared Jabber/XMPP channels for communication (e.g., "phobos777@exploit.im")[4][9].
- Parallel Declines: Activity drops in mid-2024 for both groups suggested shared infrastructure or affiliates impacted by earlier law enforcement actions[4][35].
Impact and Significance
- Financial Losses: Phobos and 8Base collectively extorted millions from SMBs, with 8Base responsible for 15% of global ransomware attacks in May 2023[13][37].
- Operational Resilience: The takedown highlights the effectiveness of cross-border collaboration, following similar successes against LockBit and AlphV[32][36].
- Mitigation Lessons: Organizations are urged to secure RDP, enforce multi-factor authentication, and maintain offline backups[12][21].
Earlier today we made a post regarding the arrest of 8base ransomware group. We have deleted that post due to misinformation. This is a correction post.
— vx-underground (@vxunderground) February 11, 2025
Note: Our original source of the 8base ransomware group takedown was incorrect. Thank you to "Deleted Account" (their name,… pic.twitter.com/nQgiR3dFQ4
The following authorities took part in the investigation:
- Belgium: Federal Police (Federale Politie / Police Fédérale)
- Czechia: Police of the Czech Republic (Policie České republiky)
- France: Paris Cybercrime Unit (Brigade de lutte contre la cybercriminalité de Paris - BL2C), Court of Paris - National Jurisdiction Against Organised Crime (Juridiction Nationale de Lutte contre la Criminalité Organisée – JUNALCO)
- Germany: Bavarian State Criminal Police Office (Bayerisches Landeskriminalamt – LKA Bayern), Bavarian Central Office for the Prosecution of Cybercrime (Generalstaatsanwaltschaft Bamberg – Zentralstelle Cybecrime Bayern)
- Japan: National Police Agency (警察庁)
- Poland: Central Cybercrime Bureau (Centralne Biuro Zwalczania Cyberprzestępczości)
- Romania: Romanian Police (Poliția Română)
- Singapore: Singapore Police Force CyberCrime Command
- Spain: Guardia Civil
- Sweden: Swedish Police Authority (Polisen)
- Switzerland: Office of the Attorney General of Switzerland (OAG), Federal Police (fedpol)
- Thailand: Cyber Crime Investigation Bureau (CCIB)
- United Kingdom: National Crime Agency (NCA)
- United States: US Department of Justice (US DOJ), Federal Bureau of Investigation (FBI – Baltimore Field Office), US Department of Defense Cyber Crime Center (DC3)
New ransomware group CryptBB is 8Base.
— Dominic Alvieri (@AlvieriD) September 16, 2023
New leak site /crypuglu….
Same backend, same victims with the exact posts and dates, leak site template, copy, bro even the same colors…
This is such a bad attempt @vxunderground @malwrhunterteam pic.twitter.com/UO8ZVib3Yc

How does Phobos ransomware evade detection by cybersecurity measures
Phobos ransomware employs a multifaceted strategy to bypass cybersecurity defenses, combining technical subterfuge with abuse of legitimate system tools. Here’s a breakdown of its key evasion tactics:
1. Disabling Security Tools
- Firewall Deactivation:Phobos usestext
netshcommands to disable Windows Firewall, preventing network-based defenses from blocking malicious traffic:bashnetsh advfirewall setcurrentprofile state offnetsh firewall set opmode mode=disable
This allows unrestricted command-and-control (C2) communication and payload delivery713. - Antivirus Tampering:The ransomware terminates security-related processes (e.g., Windows Defender) and manipulates Windows Management Instrumentation (WMIC) to delete antivirus services112.
2. Evading Behavioral Analysis
- Smokeloader Integration:Phobos leverages Smokeloader, a modular malware loader, to decrypt payloads in memory. It manipulates API functions to obfuscate network traffic and evade intrusion detection systems (IDS)313.
- UAC Bypass:Embedded code can bypass User Account Control (UAC) to execute with elevated privileges, though this is often unnecessary post-compromise due to prior credential theft10.
- Anti-Analysis Tools:Phobos actors use tools like Universal Virus Sniffer, Process Hacker, and PowerTool to terminate analysis utilities and evade sandboxed environments1314.
3. Abuse of Legitimate System Tools (Living-off-the-Land)
- Backup Destruction:Deletes Volume Shadow Copies usingtext
vssadmin.exe delete shadowsand WMIC to erase backups, crippling recovery options213.bashvssadmin.exe delete shadows /all /quiet - Legitimate Utilities for Persistence:Usestext
schtasksfor scheduled tasks and modifies registry keys (e.g.,textHKCU\Software\Microsoft\Windows\CurrentVersion\Run) to maintain persistence713.
4. Network and Data Obfuscation
- SystemBC Proxy:Routes traffic through SystemBC, a proxy/RAT tool, to mask C2 communications as benign HTTPS traffic35.
- Encrypted Configuration:Stores evasion parameters (e.g., excluded directories, target file types) in an AES-encrypted configuration block, hindering static analysis310.
5. Environment Awareness
- Geographic Avoidance:Checks system locales to avoid infecting devices with Cyrillic language settings, likely to evade scrutiny in Eastern European regions3.
- Low-Profile Encryption:Limits encryption to non-privileged folders to reduce detection likelihood while maximizing impact on critical user files6.
6. Credential and Privilege Exploitation
- LSASS Dumping:Uses tools like Mimikatz to extract credentials from memory, enabling lateral movement without triggering authentication alerts13.
- Active Directory Enumeration:Leverages Bloodhound and Sharphound to map network permissions, targeting high-value assets stealthily1314.
7. Exfiltration Evasion
- Cloud Storage Abuse:Exfiltrates data via Mega.io and WinSCP, blending malicious transfers with legitimate cloud traffic513.
- Archiving Sensitive Data:Compresses stolen files intotext
.ziportext.rararchives to bypass data loss prevention (DLP) systems13.
By blending these techniques, Phobos operators maintain a low detection profile while maximizing operational impact. Mitigation requires layered defenses, including endpoint detection and response (EDR) for behavioral analysis, strict RDP security, and frequent offline backups11314.

What are the key differences between Phobos and Dharma ransomware
Phobos and Dharma ransomware share a common lineage but have evolved distinct characteristics in their operations, technical mechanisms, and impact. Below is a breakdown of their key differences:
Origins and Evolution
- Dharma:First observed in 2016 as an offshoot of CrySiS ransomware, Dharma relies heavily on manual deployment via compromised Remote Desktop Protocol (RDP) services621. Its source code was leaked in 2020, enabling widespread variant creation24.
- Phobos:Emerged in 2019 as a refined variant of Dharma, adopting a Ransomware-as-a-Service (RaaS) model. Phobos incorporates code from Dharma and CrySiS but introduces modular configurations and affiliate-driven attacks47.

Encryption Methods
| Feature | Dharma | Phobos |
|---|---|---|
| Symmetric Algorithm | AES-256-CBC (unique key per file)58 | AES-256-CBC (custom implementation)17 |
| Asymmetric Layer | RSA-1024 (variable public keys per variant) | RSA-1024 (static public key across variants)74 |
| Key Management | Decrypts keys from encrypted .data section | Embeds hardcoded public key; AES keys encrypted with RSA and stored in files110 |
| File Extensions | Variant-specific (e.g., text .nqixtext .dharma | Configurable (e.g., text .ekingtext .acute |
Phobos’ use of a hardcoded RSA public key (consistent across variants since 2019) makes decryption without the attacker’s private key nearly impossible7. Dharma’s encryption keys vary by campaign, enabling occasional decryption via leaked keys58.
Infection and Persistence
- Initial Access:
- Evasion:
- Persistence:
Operational Tactics
- Targeting:
- Monetization:
- Affiliate Structure:
Technical Complexity
- Configuration:
- Performance:
Mitigation Challenges
- Dharma: Restorable via backups if detected early; decryption tools exist for some variants2022.
- Phobos: Resilient due to static RSA key and hybrid encryption; recovery often requires paying ransoms410.
Summary
While Dharma laid the groundwork for RDP-based attacks, Phobos represents a more sophisticated evolution with RaaS scalability, advanced evasion, and systemic targeting of critical sectors. Phobos’ static encryption key and affiliate network make it a larger-scale threat, whereas Dharma persists through its simplicity and adaptability via leaked code.

Conclusion
The dismantling of Phobos and 8Base underscores the evolving threat of RaaS models and the critical role of international cooperation in cybercrime investigations. While these arrests disrupt current operations, the adaptability of ransomware ecosystems necessitates continued vigilance. For organizations, proactive defense measures remain the best safeguard against emerging threats[2][12][21].
Citations:
[1] https://www.europol.europa.eu/media-press/newsroom/news/key-figures-behind-phobos-and-8base-ransomware-arrested-in-international-cybercrime-crackdown
[2] https://www.avertium.com/resources/threat-reports/phobos-ransomware
[3] https://blog.qualys.com/vulnerabilities-threat-research/2023/11/23/unveiling-the-deceptive-dance-phobos-ransomware-masquerading-as-vx-underground
[4] https://www.trellix.com/blogs/research/phobos-stealthy-ransomware-that-operated-under-the-radar-until-now/
[5] https://www.trendmicro.com/vinfo/us/security/news/ransomware-spotlight/ransomware-spotlight-8base
[6] https://www.checkpoint.com/cyber-hub/threat-prevention/ransomware/8base-ransomware-group/
[7] https://www.lepide.com/blog/what-is-phobos-ransomware/
[8] https://www.s-rminform.com/latest-thinking/cyber-threat-advisory-phobos-ransomware-launches-new-leak-site-and-pivots-towards-extortion
[9] https://sosransomware.com/en/ransomware-groups/the-irresistible-rise-of-8base-ransomware-understanding-the-threat-and-defenses/
[10] https://blog.talosintelligence.com/deep-dive-into-phobos-ransomware/
[11] https://www.sentinelone.com/anthology/8base/
[12] https://www.picussecurity.com/resource/blog/phobos-ransomware-analysis-simulation-and-mitigation-cisa-alert-aa24-060a
[13] https://www.provendata.com/blog/8base-ransomware/
[14] https://www.hhs.gov/sites/default/files/overview-phobos-ransomware.pdf
[15] https://blogs.vmware.com/security/2023/06/8base-ransomware-a-heavy-hitting-player.html
[16] https://www.logpoint.com/wp-content/uploads/2023/08/logpoint-etpr-8base.pdf
[17] https://www.fortinet.com/blog/threat-research/phobos-ransomware-variant-launches-attack-faust
[18] https://www.europol.europa.eu/media-press/newsroom/news/key-figures-behind-phobos-and-8base-ransomware-arrested-in-international-cybercrime-crackdown
[19] https://malpedia.caad.fkie.fraunhofer.de/details/win.phobos
[20] https://hivepro.com/threat-advisory/in-depth-analysis-of-phobos-ransomware/
[21] https://www.cisa.gov/news-events/cybersecurity-advisories/aa24-060a
[22] https://heimdalsecurity.com/blog/phobos-ransomware/
[23] https://www.threatdown.com/blog/a-deep-dive-into-phobos-ransomware/
[24] https://www.fortinet.com/blog/threat-research/deep-analysis-the-eking-variant-of-phobos-ransomware
[25] https://www.hipaajournal.com/law-enforcement-operation-takes-down-8base-ransomware-group/
[26] https://malpedia.caad.fkie.fraunhofer.de/details/win.8base
[27] https://www.hhs.gov/sites/default/files/8base-ransomware-analyst-note.pdf
[28] https://socradar.io/international-operation-target-8base-phobos-ransomware/
[29] https://blog.talosintelligence.com/deep-dive-into-phobos-ransomware/
[30] https://www.linkedin.com/posts/jspasswaters_a-deep-dive-into-phobos-ransomware-recently-activity-7231763350286647297-BMSb
[31] https://www.picussecurity.com/resource/blog/phobos-ransomware-analysis-simulation-and-mitigation-cisa-alert-aa24-060a
[32] https://therecord.media/8base-ransomware-site-taken-down-4-arrested
[33] https://www.sentinelone.com/anthology/8base/
[34] https://cyberint.com/blog/research/all-about-that-8base-ransomware-group-the-details/
[35] https://www.helpnetsecurity.com/2025/02/11/8base-ransomware-group-leaders-arrested-leak-site-seized-phobos/
[36] https://www.infosecurity-magazine.com/news/8base-ransomware-phobos-arrested/
[37] https://www.provendata.com/blog/8base-ransomware/
[38] https://www.trendmicro.com/vinfo/us/security/news/ransomware-spotlight/ransomware-spotlight-8base
[39] https://www.logpoint.com/wp-content/uploads/2023/08/logpoint-etpr-8base.pdf