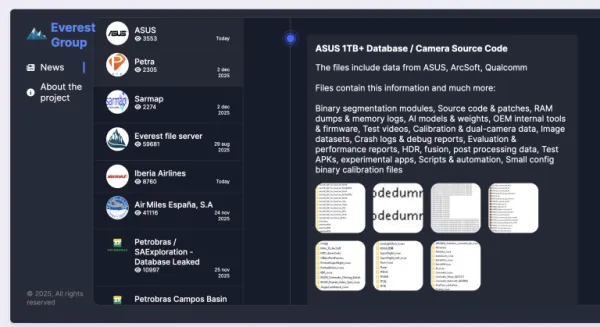
Petco's Application Misconfiguration Exposes Highly Sensitive Customer Data

December 8, 2024 - Pet retail giant Petco has disclosed a significant data breach affecting an undetermined number of customers, with exposed information including Social Security numbers, driver's license details, financial account data, and credit card information. The incident, caused by a misconfigured application setting, highlights the ongoing vulnerability retailers face from basic security oversights that can have devastating consequences.
What Happened: A Classic Misconfiguration Incident
According to legally required filings with multiple state attorney general offices, Petco discovered that a setting within one of its software applications inadvertently made certain files accessible online. The company states it identified the issue internally and "immediately took steps to correct the issue and to remove the files from further online access."
However, several critical questions remain unanswered:
- How many customers were affected? Petco has not disclosed the total number of victims
- How long were files exposed? The timeline of exposure remains unclear
- What was the specific vulnerability? Technical details about the misconfiguration have not been revealed
- Did attackers access the data? Petco has not confirmed whether it has logs showing unauthorized access
Scope of Compromised Data
The Texas attorney general filing reveals the full extent of potentially compromised information:
- Full names
- Social Security numbers
- Driver's license numbers
- Dates of birth
- Financial account numbers
- Credit and debit card numbers
This represents some of the most sensitive personally identifiable information (PII) a consumer can possess, creating substantial identity theft and fraud risks for affected individuals.
Geographic Impact
Based on state disclosure requirements, we can infer minimum impact numbers:
- California: At least 500 customers (state law requires disclosure for breaches affecting 500+ residents)
- Massachusetts: Unspecified number of customers
- Montana: 3 confirmed affected customers
- Texas: Unknown number of customers
Given Petco's scale—the company reported serving over 24 million customers as of 2022—the actual number of affected individuals could be substantially higher than the minimums suggested by state filings.
The Application Misconfiguration Threat
Security misconfigurations rank as the fifth most serious risk to web applications according to OWASP, with approximately 4% of tested applications found to have some form of security misconfiguration. But that statistic understates the problem—OWASP found that 90% of applications tested showed some form of misconfiguration.
How Misconfigurations Create Exposure
Application misconfigurations can manifest in several ways:
1. Insecure Default Settings Applications often ship with default configurations prioritizing functionality over security. When organizations fail to harden these settings before production deployment, sensitive data may become inadvertently accessible.
2. Improper Access Controls Misconfigured permissions can allow unauthorized users to access sensitive resources. This appears to be the root cause in Petco's case, where files containing customer data were made accessible without proper authentication requirements.
3. Unprotected Storage When sensitive data is stored without proper encryption or access restrictions, even a minor configuration error can expose massive amounts of information.
4. Missing Security Headers Failure to implement proper security headers and directives can leave applications vulnerable to various attack vectors.
The Retail Sector's Unique Vulnerabilities
Retailers face particularly acute risks from misconfigurations for several reasons:
Digital Transformation Pressure: As retailers rush to implement e-commerce platforms, mobile apps, loyalty programs, and omnichannel experiences, the complexity of their technical infrastructure explodes. Each integration point represents a potential misconfiguration risk.
Third-Party Dependencies: Modern retail operations typically rely on numerous third-party services for payment processing, customer relationship management, analytics, and more. A misconfiguration in any of these integrated services can expose customer data. Reports suggest Petco's incident may involve Salesforce, highlighting this third-party risk.
Extensive Data Collection: Retailers collect vast amounts of customer data across multiple touchpoints—from online purchases and in-store transactions to loyalty programs and marketing campaigns. This creates a large attack surface where misconfigurations can have outsized impact.
Financial Impact: The Real Cost of Misconfigurations
While Petco hasn't disclosed its breach costs, industry data provides sobering context:
- Retail sector average: Data breaches in retail cost an average of $3.54 million in 2025
- Per-record cost: Approximately $160 per compromised customer record
- Detection and containment: Organizations typically take 204 days to identify a breach and another 73 days to contain it
- Legal and regulatory penalties: Costs extend beyond immediate response to include potential regulatory fines, class-action lawsuits, and mandatory credit monitoring services
For perspective, if Petco's breach affected just 10,000 customers (a conservative estimate given California's 500+ threshold), the per-record cost alone could reach $1.6 million, not including investigation, notification, legal fees, and reputation damage.
The Broader Retail Threat Landscape
Petco's incident occurs against a backdrop of escalating retail cybersecurity challenges:
- 80% of retailers experienced some form of cyberattack in 2024
- Credential phishing accounts for nearly 60% of retail cyber incidents
- Ransomware attacks against retail jumped 58% from Q1 to Q2 2025
- Third-party breaches originated from vendor vulnerabilities in 60% of cases
Response and Customer Impact
Petco's Actions
The company has taken several steps following the discovery:
- Corrected the misconfiguration immediately upon discovery
- Removed files from online access
- Implemented additional security measures (unspecified)
- Begun customer notification process
- Offered free credit monitoring to affected customers in California, Massachusetts, and Montana
The offer of credit monitoring services is particularly telling. Under California law, companies must provide these services only when driver's license numbers or Social Security numbers are compromised, confirming the severity of the exposed data.
Questions About Texas Victims
Notably, it remains unclear whether Petco is offering the same credit monitoring services to affected customers in Texas, despite that state's notification filing revealing the same types of compromised data.
Learning from Petco: Prevention Strategies
For organizations handling sensitive customer data, Petco's breach offers several critical lessons:
1. Implement Configuration Management
Automated scanning: Deploy tools that continuously monitor for misconfigurations across your application stack
Configuration as code: Treat security configurations as version-controlled code, ensuring consistency across development, staging, and production environments
Regular audits: Conduct periodic security configuration reviews, especially after software updates or new deployments
2. Adopt Secure-by-Default Principles
Principle of least privilege: Configure applications to deny access by default, requiring explicit permission grants
Disable unnecessary features: Turn off debugging modes, verbose error messages, and development tools in production
Regular hardening: Establish repeatable hardening processes that can be quickly applied to new environments
3. Strengthen Third-Party Risk Management
Vendor security assessments: Evaluate the security posture of all third-party services before integration
Continuous monitoring: Don't treat vendor assessment as a one-time activity—continuously monitor third-party configurations
Contractual protections: Ensure vendor contracts include clear security requirements and breach notification obligations
4. Implement Defense in Depth
Data encryption: Encrypt sensitive data both at rest and in transit, so configuration errors don't directly expose readable information
Network segmentation: Isolate sensitive data stores from public-facing applications
Access logging: Maintain comprehensive logs to detect and respond to unauthorized access attempts
5. Invest in Security Testing
Penetration testing: Regular pen tests can identify misconfigurations before attackers exploit them
Automated security scanning: Deploy SAST, DAST, and infrastructure scanning tools in your CI/CD pipeline
Bug bounty programs: Leverage the security research community to identify vulnerabilities
The Salesforce Connection
Multiple sources suggest Petco's breach may be connected to its use of Salesforce, which has faced its own security challenges in 2025. A threat group known as "Scattered LAPSUS$ Hunters" reportedly exploited Salesforce databases to extort multiple organizations, releasing stolen data samples in October 2025.
This potential connection underscores a critical reality: even when organizations make sound security choices in selecting enterprise-grade platforms like Salesforce, the responsibility for proper configuration ultimately rests with the implementing organization. Security is a shared responsibility model, and misconfigurations in how these platforms are deployed can undermine even the most secure underlying infrastructure.
Regulatory and Legal Implications
Petco faces potential consequences across multiple fronts:
State-Level Enforcement
Different states have varying breach notification requirements and enforcement approaches:
- California: CCPA provides for statutory damages of $100-$750 per affected consumer per incident
- Texas: No private right of action, but attorney general can seek civil penalties up to $100,000 per violation
- Massachusetts: Data breach law requires comprehensive information security programs
Federal Considerations
While the U.S. lacks a comprehensive federal data breach law, affected customers could pursue claims under:
- FTC Act Section 5 (unfair or deceptive practices)
- Various consumer protection statutes
- Common law negligence theories
Class Action Exposure
Given the sensitive nature of the compromised data, class action litigation seems likely. Petco previously faced legal action following a 2012 incident affecting employee data, suggesting the company may be preparing for similar challenges now.
Comparing to Historical Precedent
This isn't Petco's first security incident. The company's history includes:
- 2004: FTC settlement over website privacy promise violations
- 2012: Employee data breach affecting hundreds in Massachusetts
- 2025: Current misconfiguration incident
This pattern suggests that despite evolving technology, fundamental issues around configuration management and access control continue to plague the organization.
What Customers Should Do
If you're a Petco customer, take these immediate steps:
1. Monitor Your Accounts
- Check credit reports from all three bureaus (Equifax, Experian, TransUnion)
- Review bank and credit card statements for unauthorized transactions
- Watch for suspicious activity across all financial accounts
2. Consider Credit Freezes
A credit freeze prevents new accounts from being opened in your name, providing stronger protection than credit monitoring alone.
3. Enable Multi-Factor Authentication
For all financial and sensitive accounts, enable strong multi-factor authentication to prevent credential-based attacks.
4. Be Alert for Phishing
Exposed data enables highly targeted phishing attacks. Be extremely cautious with:
- Emails referencing personal details from the breach
- Phone calls claiming to be from Petco or financial institutions
- Requests for additional personal information
5. Document Everything
Keep records of all breach notifications, credit monitoring services, and any suspicious activity related to your Petco account. This documentation may be valuable if class action litigation proceeds.
The Bigger Picture: Retail Security in 2025
Petco's breach is part of a broader pattern affecting retail organizations:
- Hot Topic (October 2024): 57 million customer accounts compromised
- Marks & Spencer (April 2025): Ransomware attack causing £300M in losses
- JD Sports (2023): 10 million customers' data leaked
- Ace Hardware (2023): Operations disrupted, franchise owners targeted with phishing
These incidents share common threads: sophisticated attackers, complex technical infrastructure, third-party dependencies, and massive collections of valuable customer data.
Industry Recommendations
For retail organizations looking to avoid Petco's fate:
Prioritize Configuration Management
Misconfigurations shouldn't be treated as IT problems—they're business risks requiring executive-level attention and resources.
Embrace Zero Trust Architecture
Move away from perimeter-based security models toward zero trust principles where every access request is authenticated, authorized, and encrypted.
Invest in Security Automation
Manual configuration management doesn't scale. Organizations need automated tools that can detect, prevent, and remediate misconfigurations across their entire stack.
Build Security into Development
Security cannot be an afterthought. Integrate security testing and configuration validation into every stage of the software development lifecycle.
Plan for Incidents
Despite best efforts, breaches will occur. Organizations need tested incident response plans, including:
- Clear escalation procedures
- Communication templates
- Legal and PR coordination
- Customer notification processes
- Forensic investigation protocols
Looking Forward
As Petco works to contain the damage from this breach, several questions remain:
- Will the company provide more transparency about the specific technical vulnerability and timeline of exposure?
- Are credit monitoring services being offered to all affected customers, including those in Texas?
- What specific "additional security measures" has Petco implemented?
- Were there prior security assessments that might have identified this vulnerability?
- How will this impact Petco's broader security program and investment priorities?
Conclusion
Petco's misconfiguration breach serves as a stark reminder that in cybersecurity, the fundamentals matter. While organizations chase sophisticated AI-driven security solutions and threat intelligence platforms, basic configuration errors continue to expose massive amounts of sensitive data.
The incident underscores several critical realities:
- Security is never finished: Configuration drift and oversight can undermine even well-designed security programs
- Third-party risk is your risk: Organizations remain accountable for data exposure regardless of where it originates in their technology stack
- Transparency matters: Petco's limited disclosure has created more questions than answers, potentially amplifying customer concern
- Prevention costs less than remediation: The investment required to prevent misconfigurations is trivial compared to breach response costs
For Petco's 24 million customers, this breach represents more than statistics—it's a violation of trust that will require years to rebuild. For the broader retail industry, it's a warning that operational complexity and digital transformation cannot come at the expense of basic security hygiene.
As we close out 2025, organizations across all sectors should audit their application configurations, review third-party integrations, and ask themselves: Could a single misconfigured setting expose our most sensitive data? For Petco, the answer was yes. The question is whether other organizations will learn from their mistake or become the next headline.
Stay Informed: Subscribe to our daily cybersecurity podcast covering the latest breaches, threats, and security trends affecting businesses worldwide.
Related Resources:
- Visit breached.company for ongoing breach coverage
- Explore compliancehub.wiki for regulatory guidance
- Check myprivacy.blog for consumer privacy protection tips