Qantas Data Breach: 5 Million Customer Records Leaked as Scattered Lapsus$ Hunters Escalate Global Extortion Campaign

Major Airline Falls Victim to Sophisticated Cybercrime Coalition in Year-Long Supply Chain Attack
Australia's flagship carrier Qantas Airways has become the latest high-profile victim of an aggressive extortion campaign orchestrated by Scattered Lapsus$ Hunters, a notorious cybercriminal coalition that has targeted dozens of Fortune 500 companies in what security experts are calling one of the most significant supply chain attacks of 2025.
The Breach: A Timeline of Compromise
The attack on Qantas began on June 30, 2025, when the airline detected unusual activity on a third-party platform used by one of its customer service contact centers. What initially appeared to be an isolated incident has now revealed itself as part of a coordinated, year-long campaign affecting nearly 40 major corporations worldwide.
After containing the initial breach, Qantas launched a forensic investigation that revealed the true scope of the compromise. On July 9, 2025, the airline confirmed that approximately 5.7 million unique customers had their personal information exposed—making it one of the largest data breaches in Australian aviation history.
The compromised data varied by customer but included:
- 4 million records containing names, email addresses, and Qantas Frequent Flyer details (including tier status, points balance, and status credits for some)
- 1.7 million records with additional sensitive information including:
- Residential and business addresses (1.3 million)
- Dates of birth (1.1 million)
- Phone numbers (900,000)
- Gender information (400,000)
- Meal preferences (10,000)
Critically, the attack did not expose credit card details, financial information, passport details, or Qantas account passwords and PINs—data that was not stored in the compromised system.

October Escalation: The Ransom Deadline
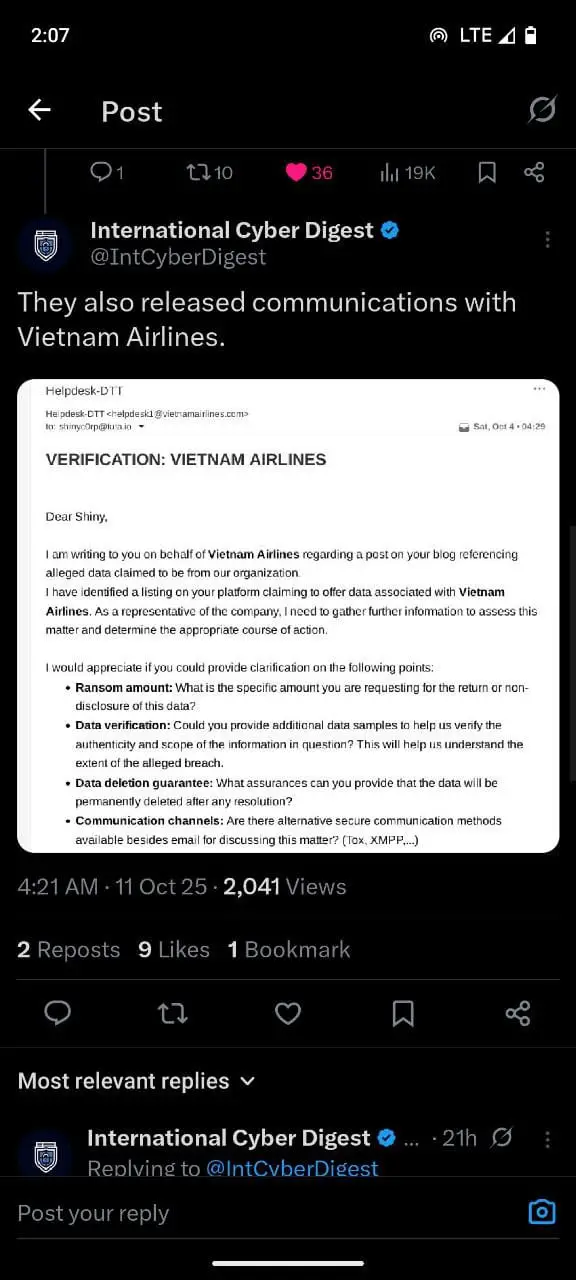
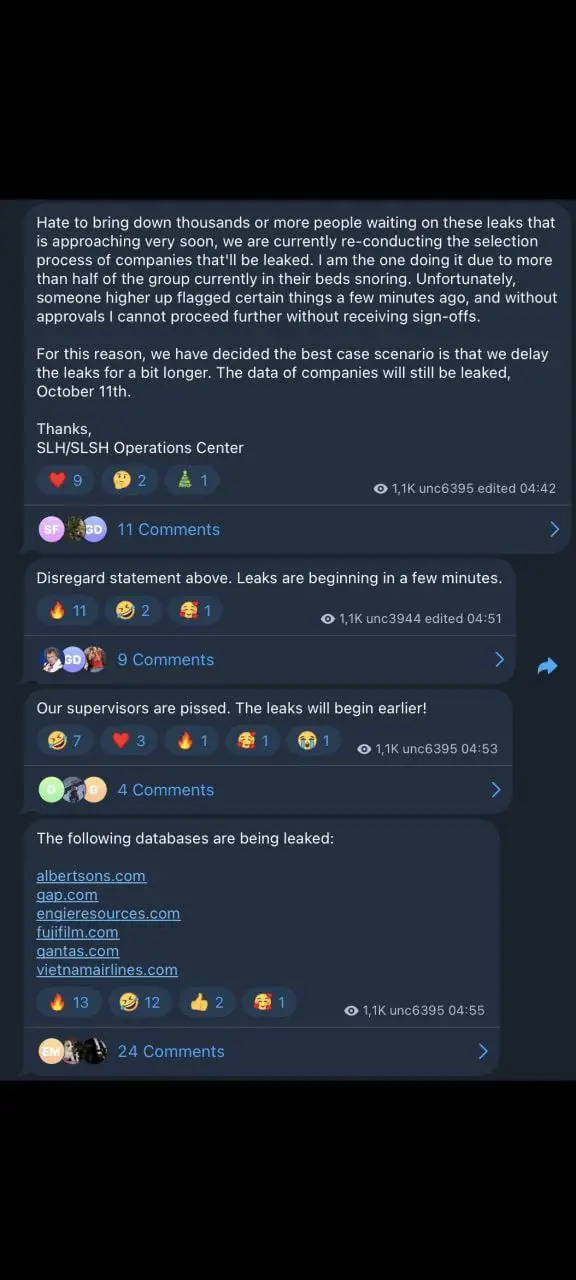
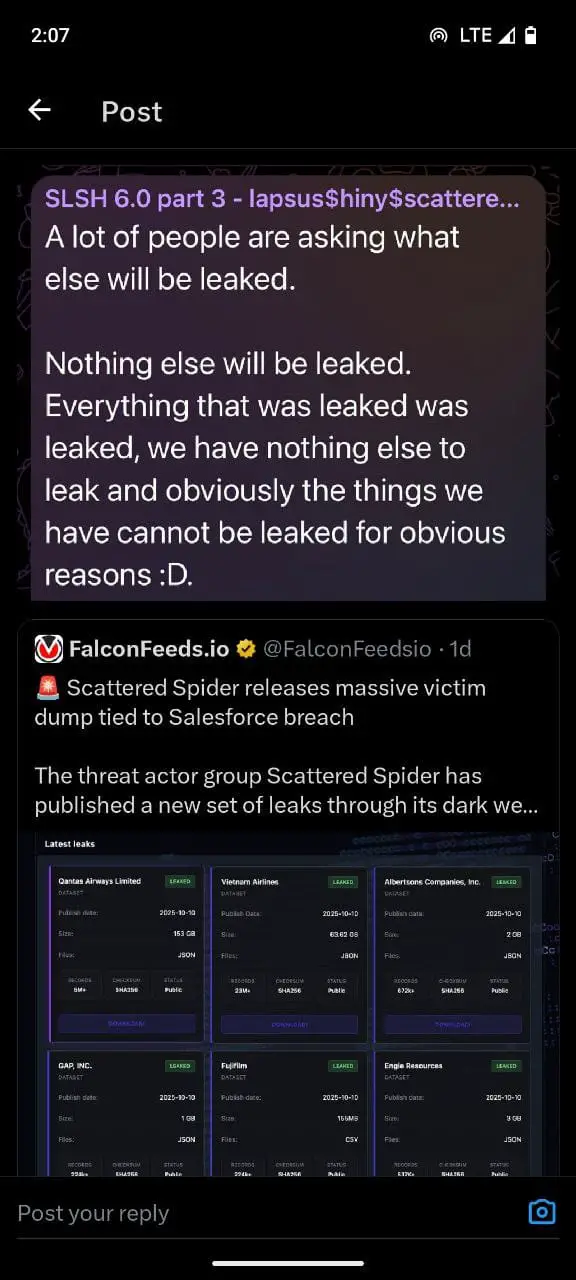
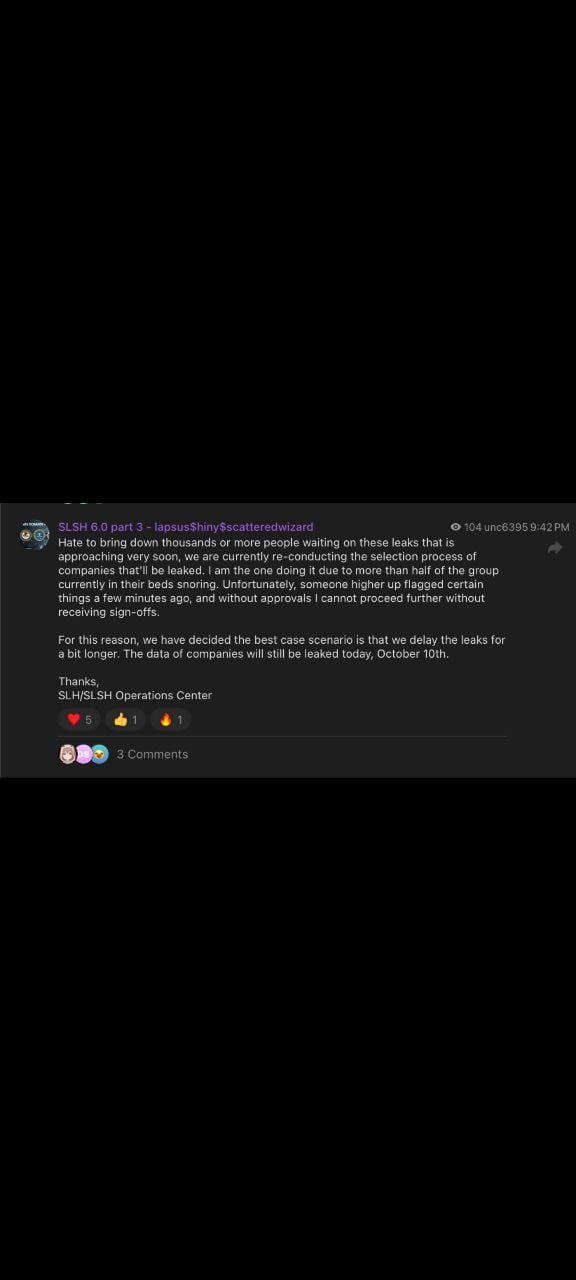
On October 3, 2025, the threat actors escalated their campaign by launching a darknet data leak site, publicly listing 39 companies—including Qantas—and threatening to release stolen data unless ransoms were paid by October 10, 2025. The extortion site claimed possession of over 5 million Qantas customer records and displayed sample data to prove the authenticity of the breach.
The leak site has since become a focal point of international law enforcement action. On October 10, the FBI, in coordination with France's Central Brigade of Cybercrime, seized the group's clearnet domain, though their dark web operations continue.

The Threat Actors: Scattered Lapsus$ Hunters
The perpetrators represent an unprecedented coalition of three of the most notorious cybercrime groups in recent history:
ShinyHunters
A financially motivated threat group that gained notoriety in 2020 through large-scale data breaches and extortion campaigns. ShinyHunters built a reputation for assertive self-promotion and operated as administrators of the infamous BreachForums platform. After several member arrests in 2024, the group remained largely dormant until resurfacing in mid-2025.
Scattered Spider
Perhaps the most dangerous element of this coalition, Scattered Spider (also tracked as Muddled Libra, Octo Tempest, and UNC3944) represents a new generation of cybercriminals. Composed primarily of English-speaking members aged 19-22 from the US, UK, and Europe, the group has demonstrated exceptional social engineering capabilities.
Microsoft has described Scattered Spider as "one of the most dangerous financially motivated threat groups currently active." The group gained widespread attention in September 2023 following high-profile attacks on MGM Resorts and Caesars Entertainment in Las Vegas, which caused operational disruptions and millions in losses.
Lapsus$
Originally operating independently before law enforcement actions in 2022, remnant members of Lapsus$ bring additional expertise in data theft and extortion to the coalition.
This alliance operates through a decentralized community known as "The Com," communicating primarily through Discord and Telegram channels to coordinate attacks, share techniques, and taunt authorities.
The Attack Vector: Social Engineering at Scale
What makes this breach particularly concerning is not technical sophistication, but rather the exploitation of the human element. The attackers employed a multi-stage social engineering approach that has proven devastatingly effective:
1. Voice Phishing (Vishing)
Attackers called help desk employees, impersonating legitimate employees or contractors. Using publicly available information and data from previous breaches, they crafted convincing narratives to trick support staff into granting access or resetting credentials.
2. MFA Bypass Techniques
The attackers convinced help desk personnel to add unauthorized devices to multi-factor authentication systems, effectively bypassing one of cybersecurity's strongest defenses.
3. Malicious OAuth Applications
In the Salesforce-related attacks, victims were tricked into connecting malicious OAuth "Connected Apps" to their corporate Salesforce instances, granting the attackers API access and enabling bulk data exports without triggering standard security alerts.
4. Third-Party Platform Exploitation
The Qantas breach specifically targeted a third-party customer service platform, highlighting how attackers increasingly focus on supply chain vulnerabilities rather than directly attacking well-defended corporate networks.
The Salesforce Connection: A Billion Records at Risk
The Qantas breach is part of a broader attack campaign targeting Salesforce customers. The Scattered Lapsus$ Hunters coalition claims to have stolen approximately 1 billion records from companies using Salesforce CRM systems, making it one of the largest data theft operations in history.
Other prominent victims include:
Technology: Google, Cisco, Palo Alto Networks, Cloudflare, Rubrik, Zscaler
Retail: Home Depot, Gap, Walgreens, Ikea, Puma, Adidas
Automotive: Toyota, Stellantis
Aviation: Air France-KLM, Vietnam Airlines
Luxury Brands: Gucci, Balenciaga, Cartier, Chanel, Louis Vuitton, Tiffany & Co.
Hospitality: Marriott, McDonald's, KFC
Logistics: FedEx, UPS
Entertainment: Disney/Hulu, HBO Max
Financial Services: TransUnion, Allianz Life
Importantly, Salesforce itself was not compromised through a platform vulnerability. Instead, attackers exploited customer-side security lapses and third-party integrations, particularly targeting the Salesloft Drift AI chatbot integration that many companies used to connect their Salesforce instances with customer service tools.
The Aviation Industry Under Siege
Qantas was not the only airline targeted in 2025. Security researchers tracked a coordinated campaign by Scattered Spider against the aviation sector beginning in late June:
- Hawaiian Airlines (June 23, 2025): Cyberattack affected IT systems
- WestJet (June 13, 2025): Cybersecurity incident disrupted systems and mobile app
- Multiple other aviation companies faced similar attacks
The FBI issued a public warning on June 28, 2025, specifically alerting the aviation industry about Scattered Spider's targeting of airlines and their third-party IT providers.
Charles Carmakal, Chief Technology Officer at Google-owned Mandiant, noted: "Scattered Spider has a history of focusing on sectors for a few weeks at a time before expanding their targeting. Given the habit of this actor to focus on a single sector, we suggest that the industry take steps immediately to harden systems."
Corporate Response and Accountability
Qantas Response
Qantas immediately established a 24/7 support line (1800 971 541 in Australia, +61 2 8028 0534 internationally) and began progressively notifying affected customers. The airline engaged federal authorities including the Australian Cyber Security Centre, the Office of the Australian Information Commissioner, and international privacy regulators.
In an unprecedented move reflecting the severity of the breach, Qantas reduced short-term executive compensation by 15 percentage points. CEO Vanessa Hudson's bonus was cut by $250,000, with the company's Board of Directors citing "shared accountability" for the impact on customers.
Salesforce Response
Salesforce has firmly stated it will not engage with or pay any extortion demands. The company maintains that its core platform was not compromised and emphasized that the breaches resulted from customer-side security lapses and third-party integration vulnerabilities.
In August 2025, Salesforce implemented hardening measures for connected apps functionality and disabled all integrations with Salesloft after the OAuth token compromise was discovered.
Law Enforcement Action
The FBI and international law enforcement agencies have actively pursued the Scattered Lapsus$ Hunters coalition. Recent arrests in France and the UK of suspected members have disrupted but not eliminated the group's operations. The October 10 domain seizure represents ongoing efforts to dismantle their infrastructure, though the group's decentralized nature makes complete elimination challenging.
Legal and Financial Ramifications
Class Action Lawsuits
By September 2025, Salesforce faced 14 lawsuits related to the data theft campaign. Australian law firm Maurice Blackburn lodged a complaint with the Office of the Australian Information Commissioner on behalf of affected Qantas customers, alleging the airline failed to take reasonable steps to protect personal information.
Regulatory Scrutiny
The breach has intensified calls for stronger cybersecurity regulations in the aviation sector and tighter controls on third-party data handling. Australia's upcoming Privacy Act reforms are expected to impose stricter notification requirements and penalties for data breaches.
Industry-Wide Implications
The Evolution of Ransomware
The Scattered Lapsus$ Hunters campaign represents an evolution in cybercrime tactics. Rather than encrypting data with ransomware, modern threat actors focus on data exfiltration and extortion, often causing greater reputational and regulatory damage than traditional ransomware attacks.
The Third-Party Risk Crisis
Tim Eades, CEO of Anetac, described the Qantas incident as a "textbook case of island hopping," where attackers target third-party platforms with less stringent security controls to access well-defended organizations.
Andrew Obadiaru, Chief Information Security Officer at Cobalt, noted: "The Qantas incident reveals a systemic issue: security validation rarely extends to the third-party platforms that store massive volumes of customer data."
The Human Factor
Despite billions spent on cybersecurity technology, the most common attack vector remains social engineering. Praneil Kumar, Coalition's Incident Response Lead for Australia, observed: "Hackers don't need to write code to breach your systems. They just need someone to click the wrong link, answer the wrong call, or ignore security protocol."

What Customers Should Do
Qantas and security experts recommend affected customers take immediate action:
- Monitor accounts closely for suspicious activity
- Enable two-factor authentication on all accounts
- Be vigilant against phishing attempts using stolen information
- Never share passwords or sensitive information via phone or email
- Report suspicious contacts to Scamwatch (Australia) or equivalent agencies
- Consider credit monitoring services given the breadth of exposed personal information
Security Recommendations for Organizations
Based on analysis of the Qantas breach and broader Salesforce campaign, cybersecurity experts recommend:
Immediate Actions
- Strengthen help desk security protocols with enhanced identity verification procedures
- Review and audit all OAuth applications and connected apps with access to critical systems
- Implement phishing-resistant MFA that cannot be bypassed through social engineering
- Monitor third-party access to corporate systems continuously
- Conduct social engineering awareness training for all staff, especially help desk personnel
Strategic Measures
- Adopt zero-trust architecture that verifies every access request regardless of source
- Implement 24/7 threat detection and incident response capabilities
- Regularly audit third-party security posture and data handling practices
- Develop incident response playbooks specifically for supply chain attacks
- Maintain offline backups of critical data that cannot be accessed remotely
- Establish executive accountability for cybersecurity outcomes
For Smaller Organizations
Coalition's Kumar warns that while large-scale breaches capture headlines, smaller enterprises with fewer resources and less comprehensive cybersecurity infrastructure face even greater vulnerability. "Although large corporations might be better equipped to recover from such attacks, smaller firms often lack the means to respond effectively, making cyber risk a critical threat to business continuity."
The Ongoing Threat
Despite law enforcement disruptions, Scattered Lapsus$ Hunters continues to operate. Following the October 10 domain seizure, the group posted on Telegram: "Seizing a domain does not really affect our operations FBI... try harder ;)."
However, subsequent posts suggest internal discord, with the group's Telegram channel being locked down after some members appeared to go missing, potentially indicating successful law enforcement actions.
The group has threatened to begin a second wave of extortion targeting the approximately 760 companies affected by the Salesloft Drift OAuth token theft, potentially exposing an additional 1.5 billion records.
Conclusion
The Qantas data breach serves as a stark reminder that in an era of interconnected technology ecosystems, cybersecurity is only as strong as the weakest link in the supply chain. The success of Scattered Lapsus$ Hunters in compromising dozens of major corporations through relatively simple social engineering tactics demonstrates that advanced persistent threats don't always require technical sophistication—just patience, research, and the ability to exploit human psychology.
As the October 10 deadline has passed and law enforcement continues its pursuit, the full extent of data that may be released remains uncertain. What is certain is that the aviation industry, along with every sector handling customer data, must fundamentally rethink their approach to security, placing equal emphasis on technical controls, human factors, and supply chain risk management.
For Qantas's 5.7 million affected customers, the breach represents not just an invasion of privacy but a warning about the persistent vulnerabilities in how personal data is stored, accessed, and protected across the digital ecosystem. The airline's response—combining customer support, executive accountability, and cooperation with authorities—may serve as a model for corporate crisis management, but the underlying security failures that enabled the breach demand industry-wide transformation.
This article is based on information available as of October 12, 2025. The situation continues to develop as law enforcement pursues the perpetrators and potentially affected organizations complete their security assessments.
Key Takeaways
For Consumers:
- 5.7 million Qantas customers' personal information was compromised
- No financial or passport information was exposed
- Vigilance against phishing and identity theft is essential
- Two-factor authentication remains critical despite vulnerabilities
For Businesses:
- Social engineering remains the primary attack vector
- Third-party platforms represent significant security risks
- Help desk security protocols need immediate strengthening
- Executive accountability for cybersecurity is becoming standard
For the Industry:
- Supply chain security requires fundamental rethinking
- OAuth and API access controls need enhanced monitoring
- The human element cannot be patched—only trained
- Collaboration between companies and law enforcement is essential
References
For more information:
- Qantas Customer Support: 1800 971 541 (Australia) or +61 2 8028 0534 (International)
- Australian Cyber Security Centre: cyber.gov.au
- Scamwatch: scamwatch.gov.au
- FBI Internet Crime Complaint Center: ic3.gov