Salt Typhoon: Chinese Hackers Expand Beyond Telecom to Target Critical US Data Infrastructure

How Chinese state-sponsored hackers penetrated America's telecommunications backbone and expanded into data centers, exposing the vulnerabilities in our most critical digital infrastructure

Executive Summary
In what cybersecurity experts are calling the most egregious national security breach by a nation-state actor in recent history, the Chinese government-sponsored hacking group Salt Typhoon has significantly expanded its campaign beyond traditional telecommunications targets to infiltrate critical data center infrastructure and residential internet providers. Recent intelligence assessments reveal that data center giant Digital Realty and mass media titan Comcast have been identified as likely victims, marking a dramatic escalation in the scope and sophistication of the multi-year espionage operation.
The campaign, which has compromised at least nine major US telecommunications companies and dozens of nations worldwide, represents a fundamental threat to American national security and the global communications infrastructure that underpins modern society.
The Expanding Scope: From Telecom to Data Centers
New Victims Identified
Two U.S. security agencies listed mass-media provider Comcast and data center giant Digital Realty among companies likely ensnared by Salt Typhoon, according to three people familiar with the matter. The National Security Agency determined that Comcast had likely been affected by Salt Typhoon, according to two of the people. The Cybersecurity and Infrastructure Security Agency believes Digital Realty may have been compromised, the third person said.
Strategic Significance of Data Center Targeting
Chinese access into datacenter and colocation firms would provide the hackers with a different target set compared to messaging services operated by traditional carriers. "The additional risk would be gaining the ability to monitor intra-service and intra-application communications traffic that doesn't normally traverse the internet backbone. That could include storage traffic moving from colocation environments into cloud or traffic moving from hosted environments into on-premises infrastructure," said Eric Hanselman, the chief technology, media and telecommunications research analyst at S&P Global Market Intelligence.

The Digital Realty Factor
Digital Realty has more than 300 data centers in 25 countries and 50 metropolitan areas, according to a company marketing webpage, which lists Amazon Web Services, Google Cloud, IBM, Microsoft and Nvidia among its clients. This infrastructure supports the physical systems where cloud and telecom networks exchange data, making it a high-value target for state-sponsored espionage operations.
Understanding Salt Typhoon: The Threat Group
Origins and Attribution
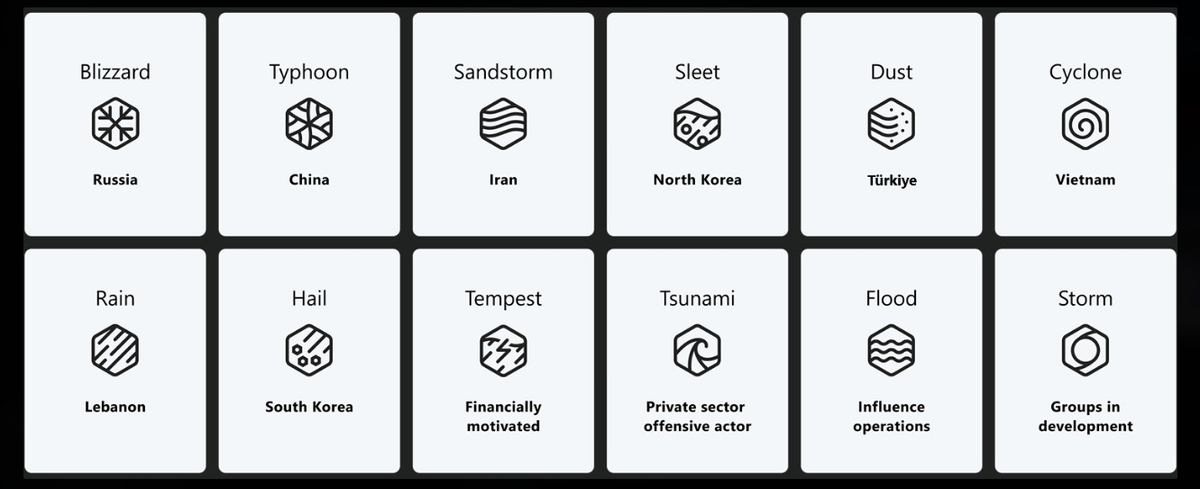
Salt Typhoon breached major telecom carriers in a global, multiyear espionage campaign whose scope and scale have gradually come to light since September. The hacking unit is part of a broader syndicate of state-backed groups tied to military and intelligence arms of China's central government.
There are indications that China's foreign spy service, the Ministry of State Security, which has long targeted the United States for intelligence, is involved in the breach. Officials internally are referring to it as having been carried out by an arm of the MSS known as Salt Typhoon, a moniker given to the group by Microsoft, which monitors Chinese hacking activity.
Attack Timeline and Persistence
The complex cyberattack, carried out by a group of Chinese hackers dubbed Salt Typhoon, began as far back as 2022. Its purpose, according to U.S. officials, was to give Chinese operatives persistent access to telecommunications networks across the U.S. by compromising devices like routers and switches run by companies like AT&T, Verizon, Lumen and others.
Confirmed Victims and Attack Surface
Major Telecommunications Providers
The confirmed list of Salt Typhoon victims continues to expand, with U.S. officials adding a ninth telecommunications company to the list of entities compromised by the sweeping Chinese-linked cyberespionage operation as of December 2024.
Confirmed telecommunications victims include:
- AT&T
- Verizon
- Lumen Technologies
- T-Mobile
- Charter Communications
- Consolidated Communications
- Windstream
- Viasat (satellite communications)
- One additional unnamed provider
Global Reach
The number of countries impacted by the hack is currently believed to be in the "low, couple dozen," according to a senior administration official. This international scope demonstrates the campaign's sophisticated coordination and the threat group's significant resources.
Attack Methods and Techniques
Technical Exploitation
Salt Typhoon exploited technical vulnerabilities in some of the cybersecurity products like firewalls used to protect large organizations. Once inside the network, the attackers used more conventional tools and knowledge to expand their reach, gather information, stay hidden and deploy malware for later use.
Infrastructure Targeting
Hackers also exploited unpatched network devices from security vendor Fortinet and compromised large network routers from Cisco Systems, the newspaper reported. This systematic targeting of critical network infrastructure demonstrates a sophisticated understanding of telecommunications architecture.
Law Enforcement Systems Compromise
Perhaps most concerning, the attackers may have gained access to systems used by the targeted ISPs to work with government agencies in response to court-authorized wiretapping requests. The incident has raised concerns of national security risks because these systems enable investigations into criminal and national security matters.
National Security Implications
Intelligence Gathering Capabilities
According to the FBI, Salt Typhoon allowed Chinese officials to obtain a large amount of records showing where, when and who specific individuals were communicating with. In some cases, they noted that Salt Typhoon gave access to the contents of phone calls and text messages as well.

Counterintelligence Concerns
As a result, Salt Typhoon attackers may have obtained information about which Chinese spies and informants counterintelligence agencies were monitoring – knowledge that can help those targets try to evade such surveillance.
Political Targeting
The U.S. believes that the hackers were able to gain access to communications of senior U.S. government officials and prominent political figures through the hack. Federal authorities confirmed in October that hackers linked to China targeted the phones of then-presidential candidate Donald Trump and his running mate, Sen. JD Vance, along with people associated with Democratic candidate Vice President Kamala Harris.
Geolocation and Mass Surveillance Capabilities
Officials said Friday that the "Chinese gained access to networks and essentially had broad and full access," giving them the capability to "geolocate millions of individuals, to record phone calls at will."
Government Response and Challenges
Detection and Discovery
Cybersecurity and Infrastructure Security Agency Director Jen Easterly said the hacking group — dubbed Salt Typhoon — "was first seen by us on federal networks that then enabled law enforcement to unravel and ask for process in virtual private servers." This early detection on government networks provided crucial intelligence that helped uncover the broader telecommunications campaign.

Ongoing Eradication Challenges
"I think it would be impossible for us to predict a time frame on when we'll have full eviction," said Jeff Greene, executive assistant director for cybersecurity at the Cybersecurity and Infrastructure Security Agency. "Right now, the hardening guidance that we put out specifically would make the activities that we've seen across the victims much harder to continue."
Complexity of Response
"Each victim is unique. These are not cookie-cutter compromises in terms of how deeply compromised the victim might be or what the actor has been able to do," Greene said. "So it really is case-specific in terms of how to mitigate the specific activity."
Industry Complications and Legal Strategies
Corporate Response Challenges
Making investigations into the breach more complicated is that multiple telecom providers have invoked legal strategies to protect themselves from disclosing compromise by the hackers. Inside two major U.S. telecom operators, incident response staff have been instructed by outside counsel not to look for signs of Salt Typhoon, said one of the people, declining to name the firms because the matter is sensitive.
Assessment Inconsistencies
There's uncertainty among U.S. officials about who was affected by Salt Typhoon. Lists of confirmed or potential victims are held by various agencies, but they don't always match. CISA, for instance, has a list of telecom and information-technology companies, but an FBI tabulation shows different entities, two of the people said.
Technical Guidance and Mitigation Strategies
Enhanced Security Guidance
The Cybersecurity and Infrastructure Security Agency (CISA), the National Security Agency (NSA), and the FBI issued guidance to the sector on addressing the threat. The detailed recommendations include guidance for quickly detecting Salt Typhoon activity, improving visibility, reducing existing vulnerabilities, eliminating common misconfigurations, and limiting the attack surface.

Specific Hardening Measures
The guidelines include a section devoted to hardening Cisco network gear, which the authoring agencies described as a popular target for the attacker in the ongoing campaign.
Consumer Protection Recommendations
Individuals concerned about the privacy of their communications should consider using encrypted messaging apps and encrypted voice communications, CISA and FBI officials say. "People looking to further protect their mobile device communications would benefit from considering using a cellphone that automatically receives timely operating system updates, responsibly managed encryption, and phishing resistant MFA for email, social media, and collaboration tools," the FBI official said.
Regulatory Response
FCC Action
The FCC proposed a Declaratory Ruling confirming that telecommunications carriers are legally obligated to take steps to secure their networks against hackers under the Communications Assistance for Law Enforcement Act. If adopted, the Declaratory Ruling would take effect immediately. The FCC also published a Notice of Proposed Rulemaking that would require telecommunications providers to make an annual attestation certifying that they have a cybersecurity risk management plan in place and are complying with such plan.
The Broader Chinese Cyber Threat Landscape
Part of Larger Campaign
Easterly cautioned during Wednesday's event that Salt Typhoon and the related Volt Typhoon hacking groups are "the tip of the iceberg" when it comes to Beijing-connected cyber espionage actors. She noted that other Chinese-backed espionage groups have burrowed into U.S. critical infrastructure systems "for the purposes of launching disruptive or destructive attacks in the event of a major crisis in the Taiwan Strait."
Infrastructure Pre-positioning
The Cybersecurity and Infrastructure Security Agency (CISA), National Security Agency (NSA), and Federal Bureau of Investigation (FBI) assess that People's Republic of China (PRC) state-sponsored cyber actors are seeking to pre-position themselves on IT networks for disruptive or destructive cyberattacks against U.S. critical infrastructure in the event of a major crisis or conflict with the United States.
Expert Analysis and Industry Implications
Scale and Severity Assessment
As a cybersecurity researcher, I find this attack is indeed breathtaking in its scope and severity. But it's not surprising that such an incident took place. Many organizations of all sizes still fail to follow good cybersecurity practices, have limited resources, or operate IT infrastructures that are too complex to effectively monitor, manage and secure.

Strategic Implications
"This has all the hallmarks of an espionage campaign — one with potentially deep access to the most important communication companies in the country," said Brandon Wales, former executive director at the DHS's Cybersecurity and Infrastructure Security Agency and now a vice president at SentinelOne, a cybersecurity firm. "The impacts are potentially staggering."
Data Center Security Implications
Expanded Attack Surface
The inclusion of Digital Realty in the Salt Typhoon campaign represents a significant escalation in targeting strategy. "We can reasonably assume that these attackers already have sufficient access into internet infrastructure and are looking to expand the depth with which they can monitor other activities that are taking place within data center environments," Hanselman said.
Cloud Infrastructure Risks
With Digital Realty hosting infrastructure for major cloud providers including AWS, Google Cloud, IBM, Microsoft, and Nvidia, the potential for secondary impacts across the technology ecosystem is substantial. This targeting pattern suggests Chinese intelligence services are adapting their approach to target the infrastructure that supports cloud computing and modern digital services.
Looking Forward: Long-term Security Challenges
Infrastructure Resilience
"At the end of the day, we need to be prepared for disruption," Easterly cautioned. "It's not about preventing; it is really about architecting our systems, building our infrastructure and training and exercising our people to be prepared for this disruption so that we can respond to it and we can recover as rapidly as possible."
Equipment Replacement Considerations
The government still needs to work with the telecommunications providers on whether, in the long term, they will need to replace equipment, Greene said. This suggests the compromise may be so deep that hardware replacement could be necessary for complete remediation.
Conclusion: A Watershed Moment for US Cybersecurity
The Salt Typhoon campaign represents more than just another cyberattack—it's a wake-up call about the vulnerabilities inherent in America's critical communications infrastructure. The expansion from traditional telecommunications targets to data centers and internet service providers demonstrates the sophisticated understanding Chinese intelligence services have developed of American digital infrastructure.
Sen. Ben Ray Lujan, a Democrat from New Mexico, called Salt Typhoon the "largest telecommunications hack in our nation's history" during a Dec. 11 hearing, while Texas Republican Sen. Ted Cruz said the U.S. "must plug any vulnerabilities in communications networks."
The ongoing nature of the threat, with telecommunications providers still trying to evict the Chinese government-linked hackers, underscores the persistent and sophisticated nature of state-sponsored cyber operations. As CISA continues to work with victims to identify and evict PRC cyber actors from their networks, the full scope of the compromise continues to emerge.
This campaign highlights the urgent need for comprehensive cybersecurity reforms across critical infrastructure sectors, enhanced public-private cooperation, and a fundamental rethinking of how America protects its most vital digital assets from sophisticated nation-state adversaries. The expansion into data center infrastructure suggests that no component of America's digital ecosystem can be considered safe from persistent, well-resourced adversaries like the Chinese Ministry of State Security.
As the investigation continues and remediation efforts proceed, Salt Typhoon serves as a stark reminder that in the digital age, national security depends not just on military might, but on the resilience and security of the communications infrastructure that connects our society, economy, and government.
This analysis is based on ongoing government investigations and public disclosures. The situation continues to develop as authorities work to understand the full scope of the compromise and implement comprehensive remediation measures.