Shadow Fleet Strikes Again: Finland Seizes Turkish-Managed Vessel After Baltic Cable Damage

NATO's Baltic Sentry mission faces its first test as yet another subsea telecommunications link falls victim to suspected hybrid warfare tactics
Executive Summary: Finnish authorities seized the cargo vessel Fitburg on New Year's Eve 2025 following damage to critical telecommunications infrastructure linking Helsinki and Tallinn. The incident marks the first cable disruption since NATO launched its Baltic Sentry mission specifically to deter such attacks, exposing ongoing vulnerabilities in critical undersea infrastructure protection despite enhanced military surveillance.

The Incident: A Familiar Pattern Emerges
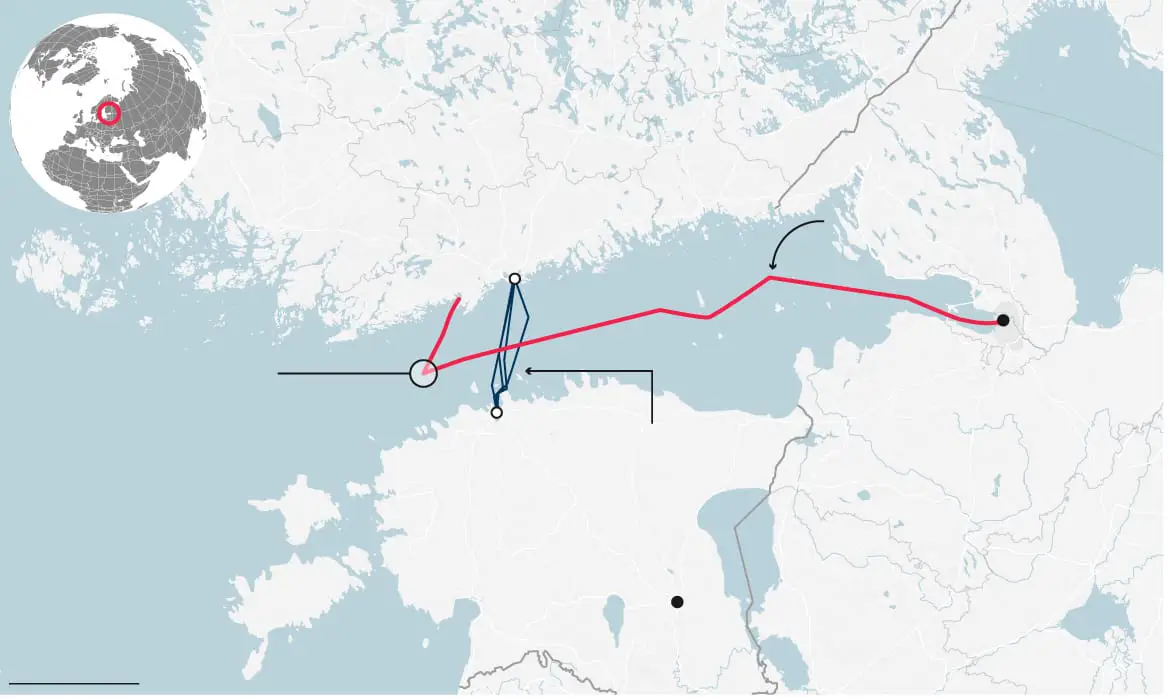
Early morning on December 31, 2025, Finnish telecommunications provider Elisa detected a fault in its subsea cable connecting Helsinki to Estonia's capital Tallinn. The damage occurred within Estonia's exclusive economic zone (EEZ), approximately 40 miles across the strategically vital Gulf of Finland.
Finnish Border Guard forces, coordinating with special police units, rapidly identified the suspect vessel—the Fitburg, a cargo ship sailing under the flag of Saint Vincent and the Grenadines. When intercepted, the vessel was found with its anchor chain deployed into the water, the telltale signature of previous cable-cutting incidents in the region.
Armed personnel fast-roped from helicopters to board the vessel in a coordinated operation that demonstrated Finland's increasingly assertive posture toward infrastructure threats. All 14 crew members—nationals of Russia, Georgia, Kazakhstan, and Azerbaijan—were detained for questioning by Helsinki police.
The Vessel: A Turkish Connection to Russia's Shadow Fleet
The Fitburg presents a complex ownership structure characteristic of Russia's shadow fleet operations. According to maritime tracking data:
- Registered Owner: Fitburg Shipping Co. Ltd.
- Operator: Albros Shipping & Trading Ltd. (Istanbul-based)
- Majority Shareholder: Raim Alekperov (76% stake), an Azerbaijani businessman residing in Turkey
- Route: St. Petersburg, Russia → Haifa, Israel
- Cargo: Sanctioned Russian structural steel products
Albros Shipping & Trading is one of Turkey's largest shipping companies, controlling dozens of dry cargo vessels and tankers operating in Russian, Azerbaijani, and Turkish markets. The company's subsidiary previously violated Crimea-related sanctions in 2017 when the vessel Amur 2515 called at the port of Sevastopol in Russian-occupied Crimea.
Finnish customs officials discovered the Fitburg was transporting EU-sanctioned Russian steel products, adding a sanctions evasion dimension to the suspected infrastructure sabotage. Authorities detained the cargo while conducting a formal inquiry into potential criminal violations of EU sectoral sanctions.
The Open Sanctions database had previously flagged the Fitburg as a "vessel of interest"—a designation used to identify ships potentially involved in Russia-linked sanctions evasion networks.
Investigation Status: Three Criminal Charges
Helsinki Police Department has assumed control of the investigation from the Gulf of Finland Coast Guard. The Prosecutor General has issued indictments under three separate criminal statutes:
- Aggravated Criminal Damage: The actual severing of telecommunications infrastructure
- Attempted Aggravated Criminal Damage: A second cable owned by Swedish provider Arelion was also damaged
- Aggravated Interference with Telecommunications: Disruption of critical communications systems
Two crew members have been formally arrested, while two others face travel bans as the investigation continues. Finnish authorities characterize the crew as cooperative, though the complex ownership structure and jurisdictional questions pose significant prosecutorial challenges.
The Eagle S Precedent: Legal Jurisdiction Challenges
This incident comes exactly one year after Finland seized the Eagle S, a Russia-linked oil tanker that damaged five cables on Christmas Day 2024 by dragging its anchor across 90 kilometers of seabed. That case ultimately collapsed when Helsinki's District Court ruled in October 2025 that Finland lacked jurisdiction to prosecute the vessel's senior officers from Georgia and India, determining that responsibility lay with the ship's flag state (Cook Islands) or the defendants' home countries.
This jurisdictional defeat highlights a critical vulnerability in maritime law enforcement. Under the United Nations Convention on the Law of the Sea (UNCLOS), coastal states face significant constraints in interdicting vessels within their exclusive economic zones, even with compelling evidence of deliberate infrastructure damage.
The Fitburg case may encounter similar obstacles. Despite the vessel's arrest and cargo seizure, Finland must navigate complex international maritime law to successfully prosecute those responsible.
NATO's Baltic Sentry: First Test, Mixed Results
NATO launched Operation Baltic Sentry on January 14, 2025, following a spate of cable incidents that collectively damaged at least 10 undersea installations since 2023. The mission deployed:
- Naval frigates from multiple NATO members
- Maritime patrol aircraft for aerial surveillance
- Naval drone fleets providing 24/7 monitoring
- Integration of national surveillance systems with NATO's Allied Maritime Command
- The NATO Maritime Centre for Security of Critical Underwater Infrastructure (NMCSCUI)
Prior to the Fitburg incident, NATO officials claimed zero malicious cable damages since Baltic Sentry's inception. The New Year's Eve attack marks the mission's first apparent failure to deter infrastructure disruption, though NATO maintains it successfully enabled rapid response and information sharing that facilitated Finland's swift interdiction.
A NATO official stated: "Baltic Sentry plays a role in our deterrence efforts along with expedient responses when suspicious incidents occur. In this case, NATO is supporting Finland with analysis and information exchange from our NATO shipping center."
The UK-Led Nordic Warden Initiative
Complementing NATO's efforts, the UK-led Joint Expeditionary Force (JEF) activated "Nordic Warden" in early January 2025. This 10-nation consortium employs artificial intelligence to analyze data from multiple sources including:
- Automatic Identification System (AIS) broadcasts
- Radar tracking systems
- Satellite surveillance imagery
- Pattern analysis of vessel behavior
Nordic Warden calculates risk scores for vessels entering areas of interest, with particular focus on Russia's shadow fleet. When elevated risks are detected, alerts propagate across NATO and allied intelligence networks.
Redundancy Saves Services: Infrastructure Resilience in Action
Despite the cable damage, telecommunications companies reported no service disruptions to customers. Both Elisa and Arelion maintained operations through redundant connections—multiple cable routes that provide failover capacity when one path fails.
This stands in stark contrast to earlier 2025 incidents where cable damage created more severe impacts. As we detailed in our Red Sea Cable Cuts analysis, when four major submarine cable systems were severed in the Red Sea, over 100 million people across 17 African countries experienced significant service degradation, and Microsoft Azure customers globally faced increased latency requiring emergency traffic rerouting.
This redundancy architecture represents a critical defensive posture for critical infrastructure:
- Geographic diversity: Multiple physical cable routes avoid single points of failure
- Capacity overprovisioning: Redundant cables maintain full service during repairs
- Rapid fault detection: Automated monitoring systems identify damage within minutes
- Pre-positioned repair capabilities: Specialized cable ships stand ready for emergency response
Estonian Ministry of Justice officials confirmed that connections remain "sufficiently backed up through other sea and land cables, ensuring the continuity of all services."
The Broader Hybrid Warfare Context
Since Russia's February 2022 invasion of Ukraine, at least 10 undersea cable incidents have occurred in the Baltic Sea. European officials increasingly view these disruptions as elements of a coordinated "hybrid warfare" campaign designed to:
- Test NATO response capabilities and identify gaps in maritime security
- Gather intelligence on critical infrastructure locations and protection measures
- Create uncertainty about the security of digital and energy systems
- Normalize infrastructure attacks as background noise rather than acts of war
- Exploit legal ambiguities in maritime law to avoid direct attribution
NATO Secretary General Mark Rutte stated: "Across the alliance, we have seen elements of a campaign to destabilize our societies through cyberattacks, assassination attempts and sabotage, including possible sabotage of undersea cables in the Baltic Sea."
However, some European officials privately express skepticism about Kremlin orchestration. One official briefed on the incidents suggested that incompetent ship-masters on poorly maintained shadow fleet vessels often simply refuse to properly raise anchors in bad weather, preferring to drag them across the seabed rather than send crew forward in dangerous conditions.
Shadow Fleet Economics: A $6 Billion Western Payday
The Fitburg incident underscores the economic contradictions fueling Russia's shadow fleet. Investigative reporting reveals that more than 230 vessels in the shadow fleet were previously owned by Western shipowners—the same nations sanctioning Russian oil trade.
These aging tankers and cargo vessels were sold for exceptionally high prices, with Western owners pocketing over $6 billion since February 2022 for ships that would otherwise have been sold for scrap. Greek owners lead in shadow fleet sales, followed by British and German shipowners.
The Kyiv School of Economics estimates Russia's shadow fleet now exceeds 1,240 vessels, with approximately 600 tankers transporting 70% of Russian oil exports. This clandestine network operates through:
- Opaque ownership structures registered in tax havens
- Flags of convenience (Panama, Saint Vincent, Liberia, Cook Islands)
- Fake or inadequate insurance documentation
- Deliberate AIS spoofing and identity changes
- Byzantine corporate layers obscuring beneficial ownership
Turkey occupies a particularly complex position, serving as NATO member while simultaneously being one of Russia's top trading partners. Turkish-managed vessels frequently transit the Bosphorus Strait carrying sanctioned Russian oil, creating environmental risks and diplomatic tensions.
Technical Security Implications for CISOs
This incident carries several critical lessons for cybersecurity and infrastructure protection leaders:
1. Physical-Layer Attacks Remain Viable Threat Vectors
While organizations invest heavily in cybersecurity controls, physical attacks on telecommunications infrastructure can achieve similar disruptive effects. Security programs must account for:
- Supply chain vulnerabilities in internet backbone infrastructure
- Single points of failure in connectivity dependencies
- Geographic concentration risks in data center connectivity
2. Redundancy is Non-Negotiable for Critical Services
The incident demonstrated that properly architected redundancy can maintain service availability during infrastructure attacks. Organizations should:
- Maintain geographically diverse network paths
- Avoid single-provider dependencies for critical links
- Test failover capabilities through regular exercises
- Ensure redundant capacity can handle full production loads
3. Attribution Challenges Enable Persistent Campaigns
The jurisdictional ambiguities that derailed the Eagle S prosecution will likely recur with the Fitburg. These legal obstacles create an "attribution gap" where:
- Threat actors operate with reduced accountability
- Deterrence effects diminish over time
- Incidents normalize as acceptable background risk
- Response costs exceed attack costs, favoring adversaries
4. Hybrid Threats Blur Traditional Security Boundaries
The convergence of physical sabotage, sanctions evasion, and potential state-sponsored operations demonstrates how modern threats transcend traditional security categories. Security leaders must:
- Integrate physical and cyber threat intelligence
- Understand geopolitical contexts affecting infrastructure
- Coordinate with government agencies on critical infrastructure threats
- Prepare for scenarios combining multiple attack vectors
Geopolitical Implications: The Baltic as Testbed
The Baltic Sea has emerged as a critical testbed for how democratic nations respond to ambiguous infrastructure attacks that fall short of conventional warfare. With eight NATO members bordering the sea alongside Russia, the region concentrates multiple strategic tensions:
- Energy security: Nord Stream pipeline sabotage remains unsolved
- Information warfare: Undersea cables carry massive volumes of data traffic
- Economic pressure: Sanctions enforcement versus shadow fleet evasion
- Legal warfare: Exploitation of maritime law gaps to avoid consequences
- Alliance cohesion: Testing NATO's willingness to respond to hybrid attacks
Finnish President Alexander Stubb emphasized Finland's readiness posture: "Finland is prepared for security challenges of various kinds, and we respond to them as necessary." This declarative policy aims to deter future incidents through demonstrated resolve.
Technical Prevention: Emerging Solutions
The challenge of protecting thousands of kilometers of undersea infrastructure has spurred technological innovation:
Unmanned Systems Deployment
NATO has committed 20 unmanned surface vehicles (USVs) to Baltic Sentry operations, providing:
- Continuous 24/7 monitoring of critical areas
- Electromagnetic spectrum surveillance
- High-resolution imagery of vessel activities
- Rapid response without risking personnel
However, unmanned underwater vehicles (UUVs) face significant limitations:
- Operational depth constraints due to pressure and power requirements
- Limited communication range at depth
- Inability to reach deepest cable installations
- High acquisition and maintenance costs
AI-Powered Threat Detection
Nordic Warden's artificial intelligence system analyzes multiple data streams to identify suspicious vessel behavior patterns:
- Unusual course deviations near infrastructure
- AIS transponder manipulation or shutdown
- Speed and maneuvering inconsistent with cargo type
- Historical patterns suggesting sanctions evasion
- Corporate ownership anomalies indicating shadow fleet membership
Acoustic Monitoring Networks
Emerging solutions include seabed-mounted acoustic sensors that can detect:
- Anchor dragging sounds
- Cable tension changes
- Unusual vessel propeller signatures
- Subsea construction or interference activities
Legal Framework Evolution
Baltic nations are exploring more assertive interpretations of maritime law to strengthen enforcement:
- Expanded boarding authority within EEZs
- Environmental safety regulations enabling detention
- Enhanced information sharing reducing investigation timelines
- Coordinated sanctions targeting beneficial owners
Economic Impact: The $10 Trillion Question
NATO Secretary General Mark Rutte highlighted the economic stakes: "More than 95% of internet traffic is secured via undersea cables, and 1.3 million kilometers of cables guarantee an estimated $10 trillion worth of financial transactions every day."
The Baltic incidents are part of a larger pattern of global submarine cable vulnerability. Our comprehensive analysis of the Red Sea cable crisis revealed that submarine cables carry 99% of data traffic across oceans, with capacity measured in terabits per second—over 1,000 times faster than satellite alternatives. When the AAE-1, EIG, SEACOM, and TGN cables were severed in the Red Sea during 2024-2025, the resulting disruptions affected 25% of traffic between Asia, Europe, and the Middle East.
A sustained campaign against subsea infrastructure could:
- Disrupt international financial transactions
- Partition internet connectivity between regions
- Damage energy markets dependent on real-time data
- Undermine confidence in digital economy reliability
- Trigger insurance market disruptions for maritime and communications sectors
The relatively low cost of conducting anchor-dragging attacks versus the massive economic value at risk creates an asymmetric threat landscape favoring attackers.
Looking Forward: The Shadow Fleet Endgame
The Fitburg incident demonstrates that despite enhanced NATO presence and AI-powered surveillance, determined adversaries continue finding ways to disrupt critical infrastructure while maintaining plausible deniability.
Several scenarios could alter this dynamic:
Escalation Pathway
- More frequent or coordinated attacks testing NATO response limits
- Expansion beyond Baltic to North Sea, Mediterranean, and Atlantic cables
- Combination of physical attacks with simultaneous cyberattacks
- Targeting of repair vessels to prolong outage durations
De-escalation Pathway
- Successful prosecutions creating deterrent precedent
- Enhanced surveillance making attacks too risky
- Diplomatic breakthroughs reducing geopolitical tensions
- Economic pressures forcing Russia to curtail shadow fleet operations
Legal Warfare Pathway
- International maritime law reforms closing jurisdiction gaps
- Coordinated sanctions targeting beneficial owners and flag states
- EU/NATO consensus on expanded interdiction authorities
- Creation of international tribunal for infrastructure crimes
Recommendations for Critical Infrastructure Operators
Based on this incident analysis, organizations operating or depending on critical infrastructure should:
- Conduct infrastructure dependency mapping identifying all physical links in your connectivity chain
- Implement and test redundancy across multiple carriers, routes, and geographic regions
- Establish intelligence sharing relationships with government agencies tracking infrastructure threats
- Develop incident response playbooks for infrastructure disruption scenarios
- Advocate for policy reforms strengthening critical infrastructure protection
- Consider cyber insurance implications of physical infrastructure attacks
- Engage in industry consortia coordinating infrastructure security efforts
Conclusion: The Long Game in Baltic Waters
The seizure of the Fitburg represents a tactical victory in an ongoing strategic challenge. While Finland successfully interdicted the suspect vessel and prevented service disruptions through infrastructure redundancy, the fundamental vulnerabilities remain:
- Thousands of kilometers of undefended cable routes
- Legal frameworks inadequate for modern hybrid threats
- Economic incentives enabling shadow fleet growth
- Attribution challenges that reduce accountability
As one NATO official acknowledged, the Baltic Sea's size means "we can't be everywhere all the time." In hybrid warfare, adversaries need only succeed occasionally to achieve strategic effects through cumulative disruption and uncertainty.
The incident serves as a stark reminder that in an era of increasing geopolitical competition, the physical infrastructure underpinning our digital economy remains surprisingly vulnerable. For security professionals, the message is clear: comprehensive security requires protecting not just the digital layer, but also the physical foundations that make modern communications possible.
As the investigation into the Fitburg proceeds, the cybersecurity community watches closely. Whether Finland can successfully prosecute this case may determine how emboldened future attackers become in targeting the arteries of global digital connectivity.
This article is based on open-source intelligence gathered from Finnish authorities, NATO official statements, maritime tracking data, and European security analyses. The investigation remains ongoing, and additional details may emerge that provide greater clarity on the incident's circumstances and attribution.
Related Reading from the CISO Marketplace Network
- Red Sea Cable Cuts: The Hidden Crisis Threatening Global Internet Infrastructure - Our comprehensive September 2025 analysis of the Houthi-linked cable disruptions that affected 100 million African users and forced Microsoft Azure to implement emergency rerouting
- The Imperative of Convergence: Why Data Center Security Demands an Integrated Physical and Cyber Defense Strategy - Essential reading on how physical infrastructure protection intersects with cybersecurity strategy