ShinyHunters: The Evolution of a Cybercrime Empire - From Pokémon-Inspired Hackers to Global Threat
Bottom Line: ShinyHunters emerged in 2020 as a data theft collective that has stolen information from over 1 billion users across hundreds of companies. From their early days selling databases for profit to their current sophisticated voice phishing campaigns targeting Salesforce instances, they've evolved from opportunistic hackers into one of the most dangerous cybercrime groups of the decade. Recent arrests haven't stopped their operations—instead, they've become more decentralized and dangerous.
The Birth of a Digital Nightmare
In the spring of 2020, as the world grappled with a global pandemic, a new threat emerged from the dark corners of the internet. ShinyHunters is a black-hat criminal hacker group that is believed to have formed in 2020, taking its name from the Pokémon gaming community where players hunt for rare "shiny" versions of creatures. But unlike the innocent game that inspired their moniker, ShinyHunters began hunting something far more valuable: human data.
ShinyHunters first appeared on the scene at the beginning of May 2020, and in just two weeks the hacking group offered for sale on the dark web over 200 million user records stolen from a number of companies. Their explosive debut would mark the beginning of one of the most prolific cybercrime campaigns in modern history.
Stage 1: The Great Data Harvest (May 2020 - July 2021)
The Tokopedia Breakthrough
ShinyHunters' first major coup came with their attack on Tokopedia, Indonesia's largest e-commerce platform. On 2 May 2020 Tokopedia was breached by ShinyHunters, which claimed to have data for 91 million user accounts, revealing users' gender, location, username, full name, email address, phone number, and hashed passwords. The group initially offered this treasure trove of data for sale on the dark web marketplace Empire Market.

The Microsoft GitHub Incident
Perhaps their most audacious early claim involved tech giant Microsoft. In May 2020, ShinyHunters also claimed to have stolen over 500 GB of Microsoft source code from the company's private GitHub account. The group published around 1GB of data from the hacked GitHub account to a hacking forum. Some cybersecurity experts doubted the claims until analyzing the code; upon analysis, ShinyHunters' claims were no longer in question.
The Data Deluge Begins
Following their initial successes, ShinyHunters embarked on what they called "Stage 1" of their operations. The affected companies included the dating app Zoosk (30 million affected users), the meal kit company HomeChef (8 million), the wellness site Mindful (2 million), the photo printing service Chatbooks (15 million), and the design-focused marketplace Minted (5 million).
The group's most devastating attack during this period targeted the storytelling platform Wattpad. In July 2020, ShinyHunters gained access to the Wattpad database containing 270 million user records. Information leaked included usernames, real names, hashed passwords, email addresses, geographic location, gender, and date of birth.
The Free Data Strategy
Interestingly, ShinyHunters began giving away much of their stolen data for free, a strategy that would become their trademark. Among the most high-profile affected companies were the social storytelling platform Wattpad (270 million users affected), the interior design website Havenly (1.3 million users affected), and the digital banking service Dave (7 million users affected). The databases of all 25 breached companies were offered for download free of charge.
This approach served multiple purposes: it increased their notoriety in cybercrime circles, made their data more widely distributed (and thus harder to contain), and built their reputation as a group that delivered on their promises.
Targeting India: A Focused Campaign
In 2021, the hacking group appears to have targeted in particular Indian companies, as in January alone it leaked the databases of the global cryptocurrency and wallet BuyUCoin, the payment processing service Juspay, the wedding platform WedMeGood, the e-marketplace ClickIndia, and the fintech startup Chqbook, all of which are based in India.

The Complete Victim List: A Catalog of Digital Devastation
2020: The Foundation Year
- Mathway (January 2020): 25 million user records stolen
- Tokopedia (May 2020): 91 million user accounts
- Wishbone (May 2020): Full user database leaked
- Microsoft GitHub (May 2020): 500 GB of source code
- Unacademy (May 2020): 22 million user records
- Wattpad (July 2020): 270 million user records
- Pluto TV (November 2020): 3.2 million Pluto TV users
- Animal Jam (November 2020): 46 million accounts
- BigBasket (November 2020): over 20 million customers
- Mashable (November 2020): 5.22GB worth of the Mashable database
2021: The Expansion
- Pixlr (January 2021): 1.9 million user records
- Nitro PDF (January 2021): 77 million user records
- Bonobos (January 2021): 7 million customers; 1.8 million registered customers; 3.5 million partial credit card records
- MeetMindful (2021): 2.28 million users
- Multiple Indian Companies: BuyUCoin, Juspay, WedMeGood, ClickIndia, Chqbook
2021-2024: The Evolution
- AT&T Wireless: In 2021, ShinyHunters began selling information on 70 million AT&T wireless subscribers. In April 2024, hackers affiliated with ShinyHunters hacked AT&T Wireless and stole data on over 110 million customers. In May, AT&T paid a $370,000 ransom to one of the group's members to delete the data
- Aditya Birla Fashion and Retail (December 2021): 5.4 million unique email addresses

Stage 2: The Snowflake Campaign - A New Level of Sophistication (2024)
By 2024, ShinyHunters had evolved from opportunistic data thieves into sophisticated operators capable of targeting cloud infrastructure at scale. Their most devastating campaign targeted customers of cloud data platform Snowflake.
The Technical Evolution
The attackers allegedly acquired login credentials from a Snowflake employee using information-stealer malware. After gaining access, the attackers created session tokens with the stolen credentials. This marked a significant evolution in their tactics, moving from basic website exploitation to sophisticated supply chain attacks.

The Major Victims
The Snowflake campaign resulted in some of the most high-profile breaches in recent history:
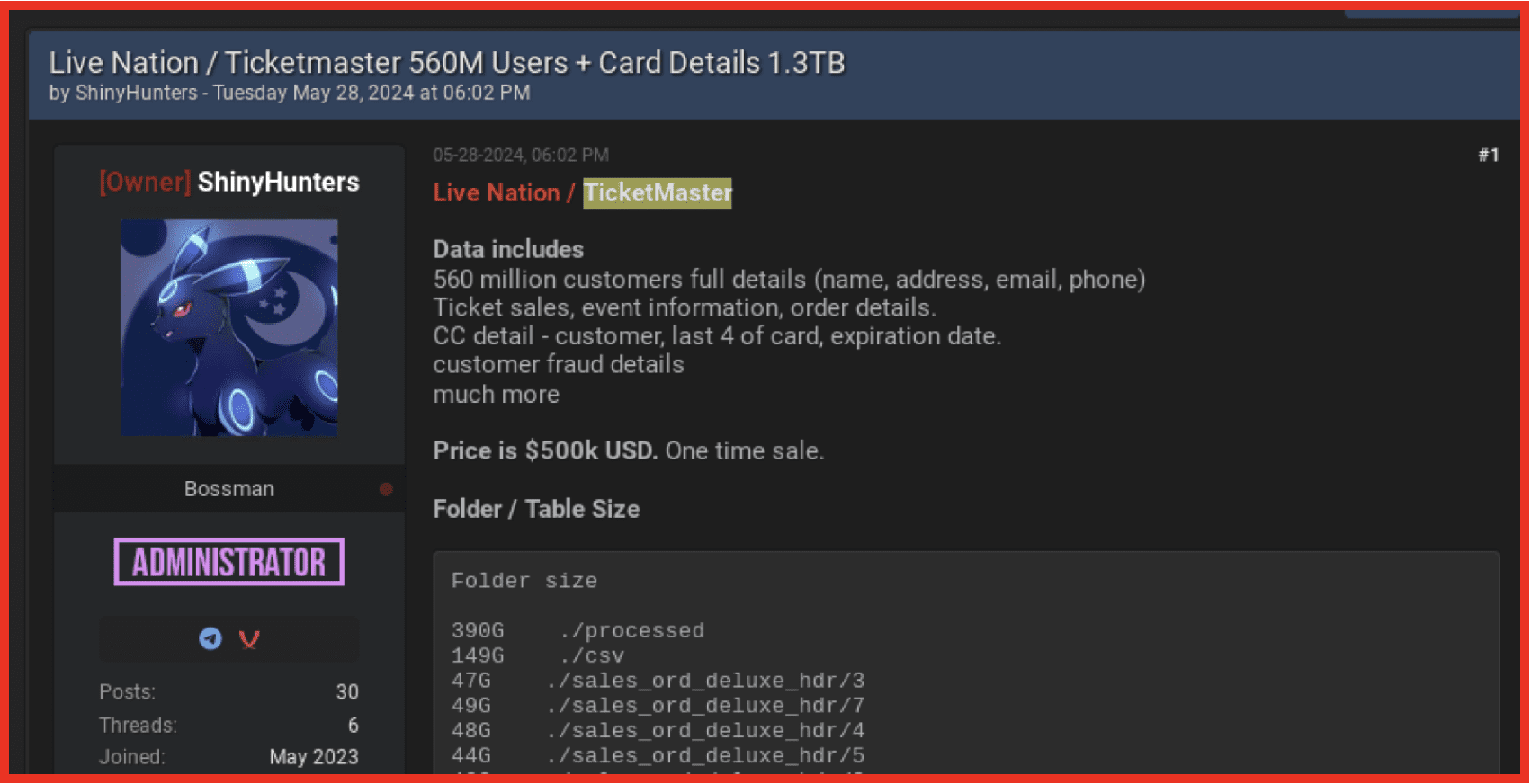
Ticketmaster (May 2024): ShinyHunters claimed responsibility for the Ticketmaster breach, affecting over 560 million users, involving up to 1.3 terabytes of data. On July 4, 2024, the ShinyHunters threat group escalated their conflict with Ticketmaster by posting about a further breach. The hackers claimed they initially accepted a hasty $1 million offer from LiveNation, however, upon realizing the data's true value, they raised their demand to $8 million.
Santander Bank: All staff and 30 million customers from Spain, Chile, and Uruguay affected
AT&T: Multiple breaches totaling over 180 million customers affected
Neiman Marcus, Advance Auto Parts, Los Angeles Unified: All suffered significant data theft
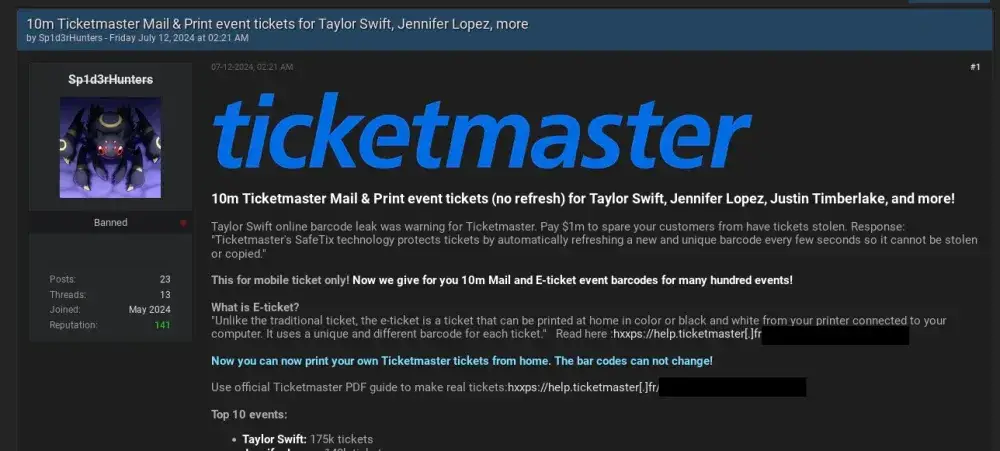
The RapeFlake Tool
RapeFlake is a custom tool created by the threat actors to perform reconnaissance and exfiltrate data from Snowflake's databases. This tool demonstrated ShinyHunters' growing technical sophistication and ability to create custom malware for specific targets.

Stage 3: The Salesforce Revolution - Voice Phishing Mastery (2025)
The group's most recent evolution has seen them master the art of social engineering through sophisticated voice phishing campaigns targeting Salesforce instances.
The New Methodology
Google Threat Intelligence Group (GTIG) is tracking UNC6040, a financially motivated threat cluster that specializes in voice phishing (vishing) campaigns specifically designed to compromise organizations' Salesforce instances for large-scale data theft and subsequent extortion.
According to Google's Threat Intelligence Group (GTIG), which tracks the threat cluster as 'UNC6040,' the attacks target English-speaking employees with voice phishing attacks to trick them into connecting a modified version of Salesforce's Data Loader application.

The Attack Process
The current Salesforce campaign follows a sophisticated methodology:
- Initial Contact: During a vishing call, the actor guides the victim to visit Salesforce's connected app setup page to approve a version of the Data Loader app with a name or branding that differs from the legitimate version
- Data Exfiltration: This methodology of abusing Data Loader functionalities via malicious connected apps allows attackers to steal vast amounts of customer data
- Lateral Movement: The app is used to export data stored in Salesforce instances and then use the access to move laterally through connected platforms such as Okta, Microsoft 365, and Workplace
- Delayed Extortion: In some instances, extortion activities haven't been observed until several months after the initial UNC6040 intrusion activity
Major Salesforce Victims (2025)
The current campaign has targeted numerous high-profile organizations:
- Google: On August 5, 2025, Google confirmed that a corporate Salesforce instance containing contact information and notes for small and medium-sized businesses had been compromised
- Fashion Giants: Adidas, Dior, Louis Vuitton, Chanel, Tiffany & Co.
- Airlines: Qantas Airways, Air France-KLM
- Insurance: Allianz Life
- Technology: Cisco, Pandora
The BreachForums Connection: Building a Criminal Empire
Beyond their hacking activities, ShinyHunters played a crucial role in the cybercrime ecosystem by operating major underground forums.
Forum Administration
The ShinyHunters threat group has been active since 2020 and has compromised organizations in industries such as telecommunications, e-commerce, technology, and retail. The group is known for selling stolen data exclusively on RaidForums and BreachForums. The ShinyHunters persona was a key participant in these forums as a contributor and administrator.
The ShinyHunters persona partnered with Baphomet to relaunch the second instance of BreachForums (v2) in June 2023 and later launched the June 2025 instance (v4) alone.
The Forum Timeline
Since its original creation as RaidForums in 2015, BreachForums had been taken down numerous times and had been administered by multiple personas. The group's involvement in forum administration gave them unprecedented influence over the global cybercrime marketplace.

The Human Cost: Arrests and Prosecutions
Sébastien Raoult: The First Major Takedown (2022-2024)
In May 2022, Sébastien Raoult (aka "Sezyo Kaizen"), a 22-year-old French programmer, was arrested in Morocco and extradited to the United States in January 2023. At the sentencing hearing, U.S. District Judge Robert S. Lasnik said, "This is an extraordinarily serious offense. We're talking about him robbing people of millions of dollars."

In January 2024, Raoult was sentenced to three years in prison and ordered to pay more than $5 million in restitution for conspiracy to commit wire fraud and aggravated identity theft. Twelve months of the sentence were for conspiracy to commit wire fraud and the remainder for aggravated identity theft, with 36 months of supervised release afterward.
According to prosecutors, Raoult helped create websites that pretended to be login pages belonging to legitimate businesses, and between April 2020 and July 2021, ShinyHunters posted sales of hacked data from more than 60 companies under his participation. "He sold hacked data. He stole people's cryptocurrency. He even sold his hacking tools so that he could profit while other hackers attacked additional victims," said Criminal Chief Sarah Vogel.
The Snowflake Campaign Arrest (2024)
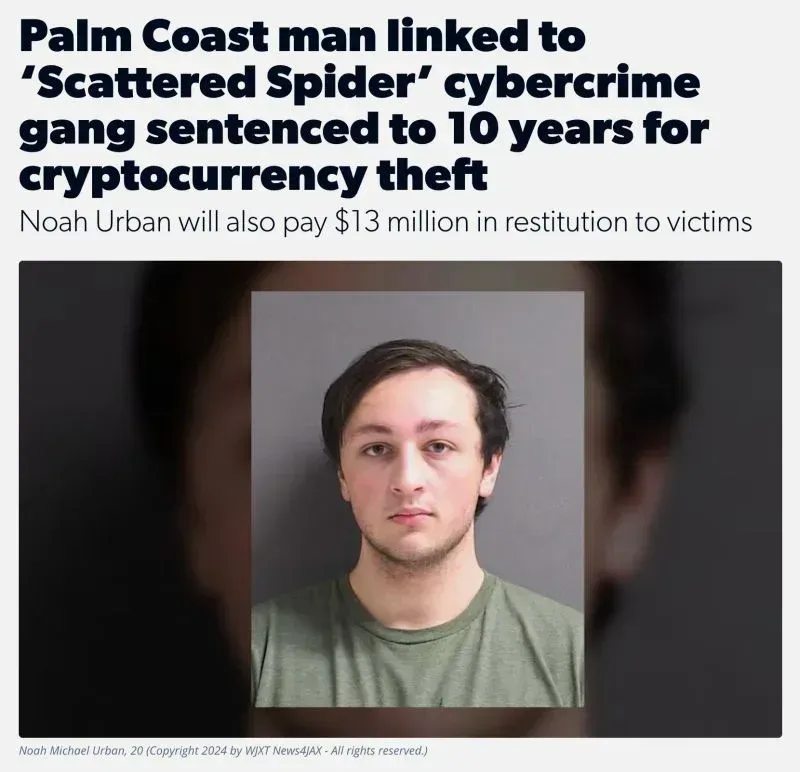
Canadian authorities arrested Alexander "Connor" Moucka (aka "Waifu" and "Judische") on October 30, 2024, at the request of the United States. He was suspected of having stolen the data of hundreds of millions after targeting over 165 organizations, all customers of cloud storage company Snowflake.
The Major French Takedown (2025)
On June 25, 2025, French authorities announced that four members of the ShinyHunters cybercriminal group were arrested in multiple French regions by France's Cybercrime Brigade (BL2C). The arrests targeted individuals known by their online handles: ShinyHunters, Hollow, Noct, and Depressed, all in their twenties.
These arrests followed an earlier operation in February 2025, which saw the arrest of another prominent suspect known as IntelBroker, identified as British national Kai West. These individuals are suspected of pulling off major data breaches against prominent French entities, including the retail giant Boulanger, telecom provider SFR, the employment agency France Travail, and the French Football Federation.
The IntelBroker Connection
In January 2025, IntelBroker stepped down as BreachForums' owner, and rumors of their arrest circulated. These rumors were confirmed on June 25, when the U.S. Department of Justice (DOJ) announced the unsealing of an indictment against Kai West, who operated under the IntelBroker alias.
IntelBroker had a colorful history of releasing stolen data on BreachForums, including personally identifiable information from members of Congress stolen from DC Health Link in March 2023, from General Electric Co. including Defense Advanced Research Projects Agency documents in November 2023, as well as from Advanced Micro Devices Inc. in June 2024 and from Hewlett Packard Enterprise Co. in January.
The Psychology and Motivation
Financial Motivation
ShinyHunters' motivations are believed to be financially driven, with the group seeking to profit from the sale of stolen data and hacking services. However, some researchers have suggested that the group may also be motivated by a desire for notoriety and to demonstrate their technical capabilities.

The Pokémon Connection
Primarily operating on Raid Forums, the collective's moniker and motivation can partly be derived from their avatar on social media and other forums: a shiny Umbreon Pokémon. As Pokémon players hunt and collect "shiny" characters in the game, ShinyHunters collects and resells user data.

Corporate Criticism
In an online chat with the cybersecurity researcher Rajshekhar Rajaharia, a persona claiming to be a member of ShinyHunters, criticised companies for their poor cyber hygiene, and for their use of poor encryption methods when storing users' data. As stated by the hacking group, many companies save their data in plaintext, or encrypt it by using old algorithms that have already been compromised.
Connections to the Broader Cybercrime Ecosystem
The Com Connection
ShinyHunters is assessed to consist of cybercriminals tied to the cybercrime network known as "the Com". This is the same ecosystem of young cybercriminals that has spawned several cybercrime brands.

Scattered Spider Collaboration
On August 8, a new Telegram channel conflating ShinyHunters, Scattered Spider, and LAPSUS$ called "scattered lapsu$ hunters" emerged, with the channel members also claiming to be developing a ransomware-as-a-service solution called ShinySp1d3r.
Supporting this theory is evidence such as the appearance of a BreachForums' user with the alias 'Sp1d3rHunters,' who was linked to a past ShinyHunters breach, as well as overlapping domain registration patterns.

GnosticPlayers Links
Cybersecurity researchers believe that ShinyHunters might have ties to GnosticPlayers, a well-known hacking group, which is said to have leaked over a billion user records. According to researchers, the push and staggered release of data dumps displayed by ShinyHunters shares similarities with the strategy used by GnosticPlayers.
Technical Evolution: From Script Kiddies to Elite Operators
Early Methods (2020-2021)
ShinyHunters has a checkered history of compromising websites and developer repositories to steal credentials or API keys to a company's cloud services, which are subsequently abused to gain access to databases and gather sensitive information.
ShinyHunter starts by identifying companies that are using Microsoft Office 365. Next, they look for companies that store GitHub open authorization tokens. Once identified, ShinyHunters work to identify research and development employees within the same organization.

Current Sophisticated Tactics
GTIG has observed an evolution in UNC6040's TTPs. While the group initially relied on the Salesforce Dataloader application, they have since shifted to using custom applications. These custom applications are typically Python scripts that perform a similar function to the Dataloader app.
The group now employs:
- Voice phishing with professional-grade social engineering
- Custom malware development (RapeFlake tool)
- Supply chain attacks through cloud service providers
- Advanced persistence techniques in corporate networks
The Current Threat: Law Enforcement Warnings
FBI Assessment
In the U.S. Department of Justice announcement about the arrest and indictment of Kai West, FBI Assistant Director in Charge Christopher G. Raia stated that the arrests "should serve as a warning to anyone thinking they can hide behind a keyboard and commit cybercrime with impunity; the FBI will find and hold you accountable no matter where you are."
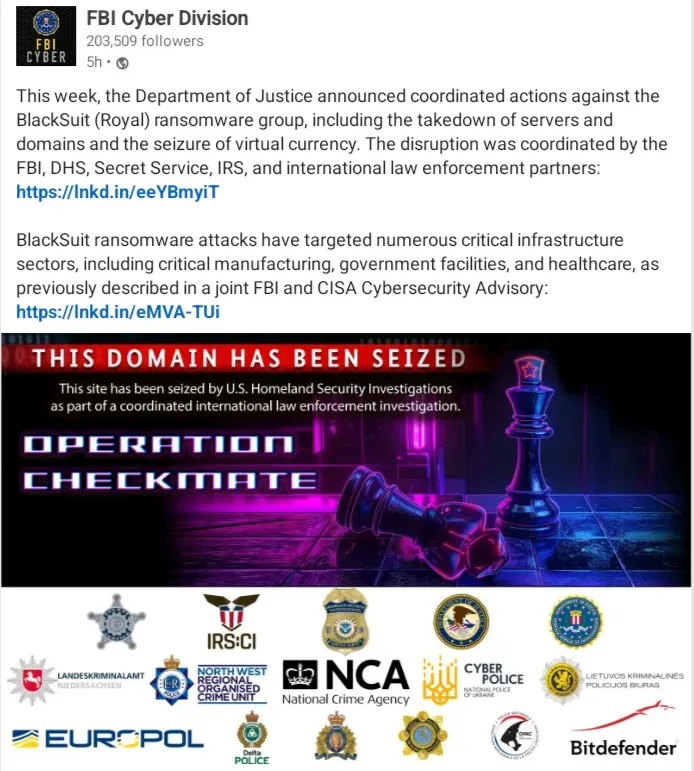
The Honeypot Revelation
The threat actor collective ShinyHunters has announced that BreachForums has been commandeered by international law enforcement agencies, and that the site has been turned into a honeypot.
"If BreachForums remains online following this notice, it is operating as a honeypot under the control of multiple international law enforcement agencies. BreachForums will not be returning under legitimate operation. Any reappearance of the site should be regarded as a law enforcement trap."
The Decentralized Future: Why Arrests Haven't Stopped Them
The Brand Model
"For cybercriminals, this brand name is pure gold," explains Aditya Sood, vice president of security engineering and artificial intelligence (AI) strategy at Aryaka. "It provides instant street cred on the Dark Web, commanding higher prices for stolen data and giving them leverage for extortion".
This persistence indicates that ShinyHunters functions as a decentralized, extortion-as-a-service collective rather than a single coordinated team.
Continued Operations
Despite numerous arrests, the group is clearly now branching out into outright extortion and continues to evolve their tactics. In addition, we believe threat actors using the 'ShinyHunters' brand may be preparing to escalate their extortion tactics by launching a data leak site (DLS).
The Scale of Damage: A Billion Users Compromised
Statistical Impact
Claiming responsibility for multiple significant cyberattacks, ShinyHunters has leaked the personal information of over a billion internet users.
An assessment by Risk Based Security found that the threat actor has exposed a total of more than 1.12 million unique email addresses belonging to S&P 100 organizations, education, government and military entities as of late 2020.

Financial Impact
- AT&T paid $370,000 ransom in 2024
- Ticketmaster ransom demands escalated from $1 million to $8 million
- Countless organizations faced regulatory fines, legal costs, and remediation expenses
- Millions of individuals subjected to identity theft and fraud risks
Lessons for Organizations: Defending Against the Next Evolution
The Human Factor
"Google published the playbook yet still lost data, which shows that layered controls crumble once an insider agrees to bypass them," says Jason Soroko, senior fellow at Sectigo. "UNC6040 and ShinyHunters have industrialized voice phishing to penetrate the soft underbelly of third-party SaaS".
Key Defense Strategies
- Voice Phishing Awareness: Train employees to recognize and resist social engineering attacks
- Multi-Factor Authentication: The affected account that was breached lacked multi-factor authentication (MFA), which allowed the attackers to log in as if they were a legitimate, trusted user
- Third-Party Risk Management: Scrutinize cloud service configurations and vendor access
- Continuous Monitoring: Implement real-time detection of unusual access patterns
- Incident Response: Prepare for fast containment and notification procedures
The Future: What's Next for ShinyHunters?
Predicted Evolution
Based on their history of innovation and adaptation, ShinyHunters will likely continue evolving:
- AI-Enhanced Social Engineering: Using deepfakes and AI to make voice phishing more convincing
- Supply Chain Focus: Targeting managed service providers and cloud infrastructure
- Ransomware Integration: developing a ransomware-as-a-service solution called ShinySp1d3r
- Data Leak Sites: launching a data leak site (DLS) to increase extortion pressure

The Broader Threat Landscape
"The information ShinyHunters gathers is often turned around and sold on the same underground marketplaces where ransomware actors use it to launch their own attacks. If enterprises can move to detect activity like ShinyHunters, they in turn can stop ransomware attacks before they are ever launched".
Conclusion: The Unstoppable Evolution
From their humble beginnings as Pokémon-inspired data collectors to their current status as masters of social engineering and cloud exploitation, ShinyHunters represents the evolution of cybercrime itself. They've shown remarkable adaptability, surviving multiple arrests, law enforcement takedowns, and security improvements to emerge stronger and more sophisticated.
Their story is a cautionary tale about the persistent nature of cybercrime and the human element that remains the weakest link in any security chain. As they continue to evolve and inspire other groups, ShinyHunters has cemented their place as one of the most significant cyberthreat actors of the digital age.
The billion people whose data they've compromised, the hundreds of organizations they've breached, and the millions of dollars in damages they've caused represent just the beginning. As long as there are vulnerabilities to exploit and humans to deceive, groups like ShinyHunters will continue to adapt, evolve, and threaten our digital world.

The hunt continues—and they're always looking for their next shiny target.


























