The Bulletproof Fortress: Inside the Shadowy World of Cybercrime Hosting Infrastructure

How 'bulletproof' hosting providers enable billions in ransomware attacks—and why law enforcement is finally fighting back
In the ongoing war against cybercrime, there's a critical battlefield that rarely makes headlines: the digital infrastructure that keeps criminal operations running. While ransomware gangs like LockBit and malware operators grab attention with devastating attacks, they couldn't function without a specialized underground service that keeps them online despite law enforcement efforts. Welcome to the world of bulletproof hosting.
The recent sanctions against Russian provider Media Land—accused of enabling cyber-attacks costing the UK £14.7 billion in a single year—have thrust this shadowy industry into the spotlight.
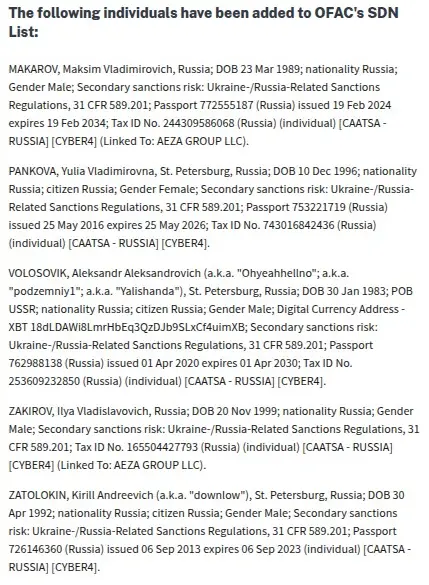




On November 19, 2025, the U.S. Treasury Department's Office of Foreign Assets Control (OFAC), in coordination with Australia and the United Kingdom, announced comprehensive sanctions targeting Media Land LLC and its entire operational network. The detailed sanctions designations named three key executives, three sister companies, and revealed the cryptocurrency wallets used to facilitate their operations.
Under Secretary of the Treasury for Terrorism and Financial Intelligence John K. Hurley emphasized the significance: "These so-called bulletproof hosting service providers like Media Land provide cybercriminals essential services to aid them in attacking businesses in the United States and in allied countries."
But Media Land is just one player in a global ecosystem that has evolved from crude server farms to sophisticated corporate networks designed to resist takedowns and shield criminals from accountability.

What Makes Hosting 'Bulletproof'?
Bulletproof hosting providers are internet infrastructure services that deliberately resist complaints about illicit activities, serving as a foundational building block for various cyberattacks. Unlike legitimate hosting companies that respond to abuse reports and comply with law enforcement requests, these providers actively market their resistance to takedowns.
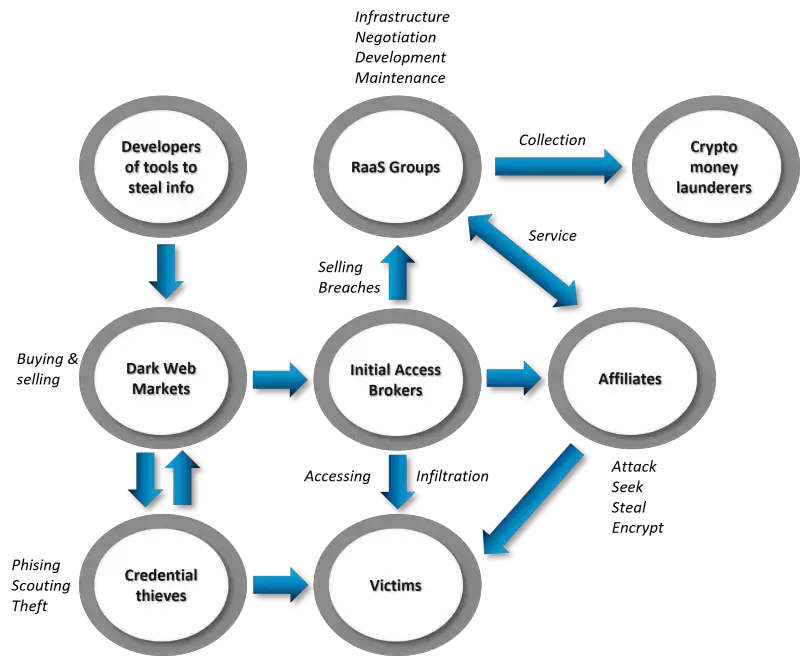
Bulletproof hosting providers neither engage in good faith with legal processes nor with third-party or victim complaints, creating safe havens where cybercriminals can operate with impunity. They host everything from ransomware command-and-control servers to phishing sites, malware distribution networks, and darknet marketplaces.
The business model is brutally simple: charge criminals premium rates for infrastructure that won't disappear when victims complain or authorities investigate. These providers enable malicious activities such as ransomware, phishing, malware delivery, and denial-of-service attacks, posing significant risks to critical systems and services.
From NATO Bunkers to Corporate Camouflage
The evolution of bulletproof hosting reveals how cybercrime has matured into a sophisticated industry. Early providers like the Russian Business Network, exposed in 2006, operated relatively openly until scrutiny forced them underground.
McColo, a provider responsible for more than 75% of global spam, was shut down in 2008 after public disclosure by security journalist Brian Krebs. The infamous CyberBunker literally operated from a decommissioned NATO bunker in the Netherlands, brazenly hosting everything except child exploitation content and terrorism-related material before authorities dismantled it in 2019.
But today's bulletproof hosting operations have evolved far beyond physical bunkers. The industry has undergone a fundamental transformation from "monolithic" operations—where a single entity owned everything from the datacenter to the virtual machines—to sophisticated "separation of liabilities" models that deliberately compartmentalize functionality across multiple business entities.
According to Spamhaus research, this shift has accelerated particularly among bulletproof hosters in Western jurisdictions. Modern operations leverage reseller schemes, shell corporations, and IP address brokers to create "firewalls of plausible deniability" between different layers of their infrastructure. When investigators contact these entities, they face a frustrating shell game: the datacenter blames the colocation customer, who blames the server owner, who claims to only rent virtual machines with no customer vetting beyond an email address and cryptocurrency wallet.
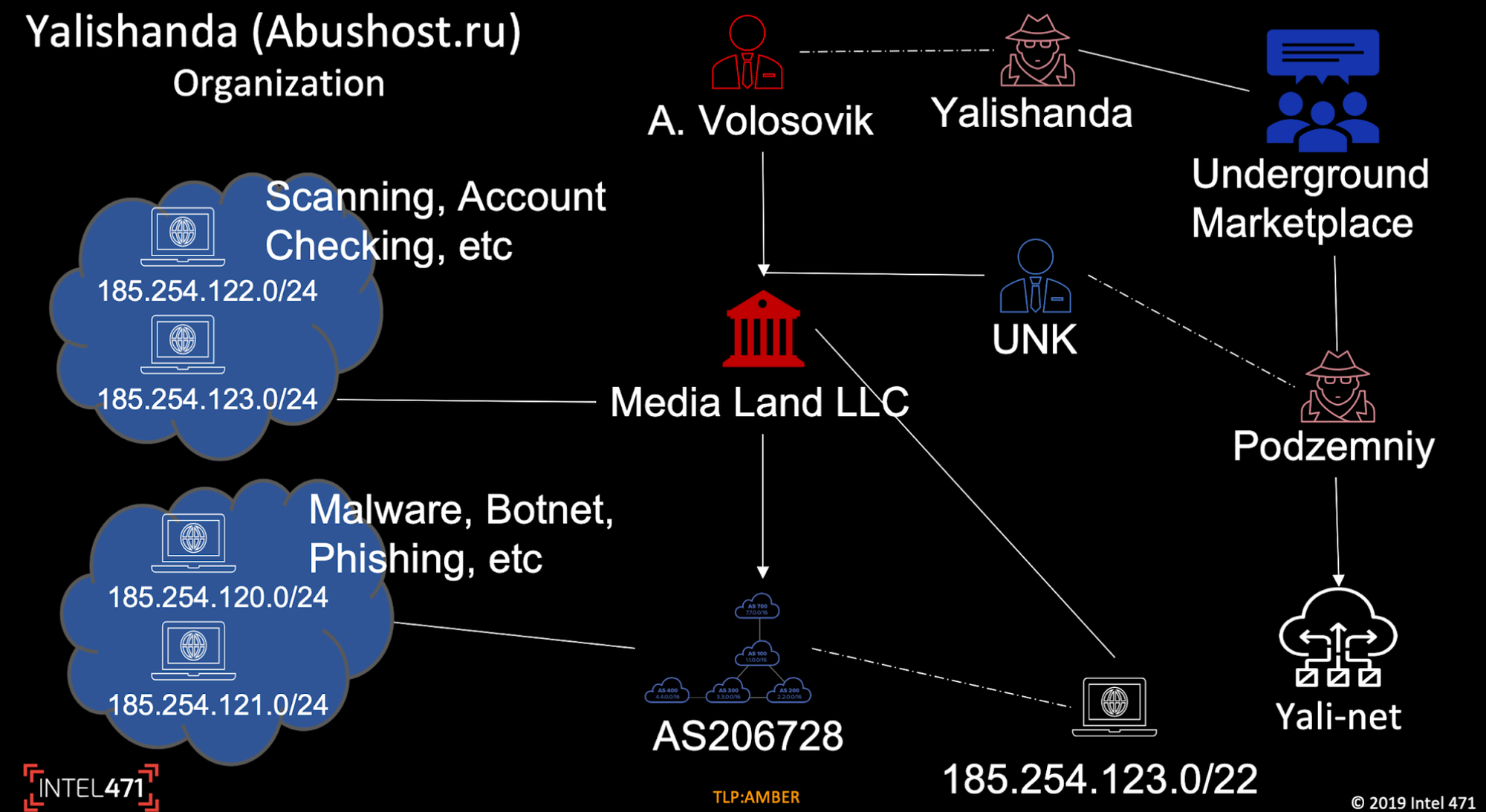
The Media Land case illustrates this corporate evolution perfectly. Operating from St. Petersburg, the company maintained a sophisticated corporate structure with subsidiaries including Media Land Technology (MLT), Data Center Kirishi (DC Kirishi), and sister firm ML Cloud—all designated in the coordinated sanctions action.
Alexander Volosovik, the alleged ringleader using aliases "Yalishanda," "podzemniy1," and "Ohyeahhellno," served as general director and advertised services on criminal forums. The Treasury Department identified his Bitcoin wallet (18dLDAWi8LmrHbEq3QzDJb9SLxCf4uimXB) used for receiving payments from cybercriminals.
Investigative journalist Brian Krebs first exposed Volosovik's identity in 2019, revealing that the bulletproof hoster had been operating under various aliases for at least a decade. Krebs uncovered Volosovik's Russian passport through leaked ChronoPay payment processor records, showing he was born in Ukraine around 1983 and operated from Vladivostok before relocating to St. Petersburg.
At a 2017 Black Hat security conference, researchers from Cisco and Intel 471 labeled Yalishanda as one of the "top tier" bulletproof hosting providers worldwide. In just one 90-day period that year, his infrastructure hosted sites tied to advanced malware including Dridex and Zeus banking trojans, along with numerous ransomware operations. Jason Passwaters, Intel 471's COO, noted: "Bulletproof hosting is probably the biggest enabling service that you find in the underground. If there's any one group operation or actor that touches more cybercriminals, it's the bulletproof hosters."
The 2019 investigation documented that Volosovik brazenly operated under his real name in some domain registrations, running services like "real-hosting.biz" and "abushost.ru" that explicitly advertised their willingness to host malware, exploits, and other illegal content while promising to ignore abuse complaints.
His 2011 forum advertisements were remarkably explicit about what was permitted: "ordinary sites, doorway pages, satellites, codecs, adware, tds, warez, pharma, spyware, exploits, zeus, IRC" along with passive spam and web spam tools like Hrumer. The only forbidden activities were outgoing email spam, child exploitation, and most phishing—demonstrating how bulletproof hosters strategically avoid the most scrutinized crimes while enabling nearly everything else.
By the time of the 2025 sanctions, Volosovik had rebranded his operation as Media Land LLC, maintaining his St. Petersburg base while expanding his infrastructure to support the world's most dangerous ransomware operations.
Kirill Zatolokin, operating under the alias "downlow," worked closely with Volosovik on overall operations and collected payments from customers. Yulia Pankova, aware of Volosovik's illicit activities, handled his finances and assisted with legal issues—demonstrating the knowing complicity of key staff in the criminal enterprise.
This corporate camouflage enabled Media Land to allegedly provide infrastructure for some of the world's most notorious ransomware gangs—LockBit, BlackSuit, Evil Corp, and Play—fueling a global wave of digital extortion. The Treasury Department's designations specifically noted Media Land's infrastructure was also utilized in multiple distributed denial-of-service (DDoS) attacks against U.S. companies and critical infrastructure.

The Technical Shell Game
Bulletproof hosting providers have honed an internet version of the shell game that makes it difficult to permanently boot them from the internet, using fast-flux hosting and routing malicious traffic through ever-shifting proxy and gateway servers in other regions.
This technical sophistication includes:
Fast-Flux DNS: Rapidly cycling through IP addresses and domain names to avoid static blocklists, making it nearly impossible to maintain effective blacklists.
IP Space Migration: When one network gets blacklisted, providers quickly move operations to new IP ranges, often purchased from other bulletproof hosters or unknowingly leased from legitimate providers. Spamhaus researchers have documented a phenomenon they call "IP broker hopping," where bulletproof hosters respond to terminations by rapidly switching between IP address brokers, making IPv4 address space a disposable asset.
Reseller Relationships: Bulletproof hosting conceals itself behind lower-end hosting providers, leveraging their better reputation while simultaneously operating both bulletproof and legitimate services through sub-allocated network blocks.
Proxy Chains: Building layers of reverse proxy servers across multiple jurisdictions, obscuring the true location of malicious infrastructure.
Compromised Assets: Some operations run on hacked servers whose owners remain unaware their systems are being used for criminal activity.
Living Off Trusted Services: Perhaps most concerning, Spamhaus observes bulletproof hosters increasingly moving domains behind major CDNs like Cloudflare—abusing "too big to block" infrastructure to shield their operations. Security researchers documented one Malaysia-based ISP routinely advising criminal clients to leverage Cloudflare's CDN services rather than pointing domains directly to their networks, effectively weaponizing legitimate internet infrastructure.
The recent Dutch police action demonstrates the scale of these operations. Law enforcement seized 250 servers running an unnamed bulletproof hosting service that had appeared in more than 80 cybercrime investigations since 2022. This follows earlier disruptions like Operation Endgame, which dismantled CrazyRDP and seized thousands of servers, showing sustained law enforcement pressure on this critical infrastructure.

The Economics of Underground Hosting
The bulletproof hosting industry operates on different economic models tailored to criminal needs:
Premium Dedicated Infrastructure: High-end providers maintain their own data centers and IP space, offering maximum uptime and resistance to takedowns. These command premium prices but provide the stability ransomware operations require.
VPS Reselling: Newer operations rent virtual private servers from legitimate providers using stolen or fake identities, then resell them to criminals. This model is cheaper and more agile, though less stable.
Compromised Assets: The cheapest option involves hosting on hacked systems, though these rarely survive long-term.
The Aeza Group, sanctioned in July 2025, exemplified the modern bulletproof hosting business. Headquartered in St. Petersburg, Aeza provided services to ransomware groups including BianLian, and infostealer operations like Meduza and Lumma, targeting U.S. defense and technology companies.
After the initial sanctions, Aeza demonstrated the resilience of these operations by immediately rebranding. Aeza leadership initiated a rebranding strategy focused on removing any connections between Aeza and their new technical infrastructure, utilizing front companies like Hypercore Ltd. in the UK and entities in Serbia and Uzbekistan.
The November 19, 2025 Treasury designations exposed this evasion network in detail. Maksim Vladimirovich Makarov emerged as Aeza's new director, making key decisions regarding sanctions evasion. Ilya Vladislavovich Zakirov helped establish new companies and payment methods to obfuscate Aeza's continuing activity.

The sanctions also targeted:
- Hypercore Ltd.: A UK company (registered July 3, 2025) used to move Aeza's IP infrastructure after designation
- Smart Digital Ideas DOO: A Serbian company utilized to set up technical infrastructure not publicly associated with Aeza
- Datavice MCHJ: An Uzbek company (also registered July 3, 2025) acting on behalf of Aeza
OFAC's action serves as a stark reminder that authorities will pursue sanctions evaders across multiple jurisdictions and corporate shells.
Russia's Role as a Safe Haven
A disturbing pattern has emerged: many bulletproof hosting providers operate from Russia, benefiting from weak enforcement and suspected state protection. The Media Land sanctions announcement noted that "Putin has turned Russia into a safe haven for these malicious cyber criminals, cultivating a dark criminal ecosystem with deep ties to the Kremlin."
This isn't coincidental. Russia hosts multiple major bulletproof providers, from Aeza Group to the previously sanctioned Zservers. The connections run deeper when examining specific ransomware operations.
The case of Evil Corp and LockBit reveals these ties. UK authorities unmasked LockBit affiliate "Beverley" as Russian national Aleksandr Ryzhenkov, who served as second-in-command at Evil Corp, demonstrating direct overlaps between state-adjacent cybercrime groups and ransomware operations.
Ryzhenkov's father-in-law, Eduard Benderskiy, is a former high-ranking FSB official, underscoring deep connections between Russian cybercrime groups and intelligence services.
Russia's role as a safe haven extends to other former Soviet republics. The 2019 arrest of Mikhail Rytikov ("AbdAllah") in Ukraine illustrated both the reach and limitations of enforcement. Despite being named by the U.S. Justice Department as infrastructure provider for hackers behind massive breaches of NASDAQ, 7-Eleven, Heartland, and others, Rytikov faced minimal consequences due to Ukraine's non-extradition policy and endemic corruption.
As Krebs documented, Ukrainian authorities have repeatedly raided major cybercriminals only to see them resume operations shortly after, with prosecutions going nowhere—reportedly because operators maintain connections to influential government and law enforcement figures.

The Ransomware Connection
The relationship between bulletproof hosting and ransomware is symbiotic. Ransomware operations require stable infrastructure for multiple functions:
Command and Control: Maintaining persistent connections with infected systems to receive encryption keys and ransom demands.
Data Exfiltration: Many modern ransomware gangs steal data before encrypting systems, requiring substantial bandwidth and storage.
Leak Sites: Public-facing websites where stolen data is published to pressure victims into paying.
Negotiation Portals: Secure communication channels between victims and attackers.
Payment Processing: Infrastructure for receiving and laundering cryptocurrency payments.
All of this requires hosting that won't disappear when victims report the attacks. Media Land's infrastructure was used by LockBit, BlackSuit, and Play ransomware groups, as well as in distributed denial-of-service attacks against U.S. companies and critical infrastructure.
The scale is staggering. LockBit alone, at its peak, accounted for over a quarter of all known ransomware attacks worldwide before Operation Cronos disrupted its operations in February 2024.
Law Enforcement Strikes Back
The tide may finally be turning. Recent years have seen unprecedented coordination between international law enforcement agencies targeting not just ransomware gangs but their enabling infrastructure.
Operation Cronos (February 2024): International coalition led by the UK's National Crime Agency and FBI infiltrated and seized LockBit's infrastructure, exploiting vulnerabilities in their own systems.
Zservers Takedown (February 2025): Three nations sanctioned ZServers/XHost, another Russia-based bulletproof hosting provider that supplied LockBit with attack infrastructure, while Dutch police dismantled its infrastructure by seizing 127 servers.
Operation Endgame (May 2024): Authorities dismantled CrazyRDP, seizing over 100 servers and arresting multiple operators in a coordinated strike against bulletproof infrastructure.
Aeza Group Sanctions (July 2025): The U.S. Treasury sanctioned Aeza Group for supporting cybercriminal activity, targeting not just the Russian entity but its UK subsidiary Aeza International and front companies.

Media Land Sanctions (November 2025): Coordinated sanctions by the UK, US, and Australia targeted the provider's complex corporate structure, including executives and multiple subsidiaries. The Treasury Department simultaneously released guidance in coordination with CISA on mitigating bulletproof hosting risks.
In conjunction with these actions, CISA released guidance in November 2025 titled "Bulletproof Defense: Mitigating Risks from Bulletproof Hosting Providers," offering internet service providers and network defenders recommendations to combat these threats.
The advisory, developed by the Joint Ransomware Task Force in collaboration with the NSA, FBI, and international partners, marks a strategic shift in how authorities approach bulletproof hosting. Rather than playing endless whack-a-mole with individual providers, the focus is on making the entire business model less viable by targeting the legitimate infrastructure that bulletproof hosters exploit.
The New Defense Strategy
The CISA guidance marks a strategic shift in how authorities approach bulletproof hosting. Rather than playing endless whack-a-mole with individual providers, the focus is on making the entire business model less viable.
The advisory developed by the Joint Ransomware Task Force encourages ISPs to adopt stricter "Know Your Customer" protocols to prevent bulletproof providers from easily acquiring infrastructure.
The guidance specifically addresses the sophisticated evasion techniques documented by researchers, including fast-flux methods where bulletproof hosters rapidly cycle through IP addresses and domain names, or migrate between Autonomous System Numbers to bypass static blocklists.
Key recommendations include:
Enhanced Customer Vetting: ISPs should collect and verify identifiable information from prospective customers, including banking details and business documentation.
Traffic Analysis: Regular monitoring of network traffic patterns to identify suspicious hosting activity.
Malicious Resource Lists: Curating high-confidence lists of malicious IP addresses, domains, and autonomous system numbers based on threat intelligence.
Rapid Response: Establishing standards for blocking malicious IP ranges for up to 90 days to disrupt criminal operations.
Customer Notification: Informing customers when their traffic is filtered due to malicious associations, with opt-out capabilities for organizations with lower risk tolerance.
Industry Standards: Creating sector-wide codes of conduct for responding to abuse reports and law enforcement requests.
ASN-Based Blocking: Deploy Autonomous System-based blocklists in addition to IP-based ones to preemptively block traffic from criminal operations quickly cycling through IP address space, as recommended by Spamhaus.
Outbound Traffic Filtering: Don't just monitor incoming traffic—robust filtering of outgoing network traffic can spot and prevent imminent security threats. Restrict such traffic as tightly as possible and investigate any attempts by internal infrastructure to communicate with blocked destinations.
The goal is to force cybercriminals onto legitimate infrastructure providers who will comply with takedown requests, making it harder for them to maintain persistent operations.
The Arms Race Continues
Despite these successes, the bulletproof hosting industry shows remarkable resilience. The Aeza Group case demonstrates how quickly providers can rebrand and restructure after sanctions. Within months of being designated, Aeza had established new front companies and continued operations under different names.
Some providers are moving operations to anonymization networks like Tor, though these come with disadvantages including slow speeds and unreliability for bandwidth-intensive operations like botnet command and control.
Others are adopting a "new kid in town" approach: renting virtual private servers at legitimate hosting providers using stolen or fake identities, with front-end servers acting as reverse proxies forwarding traffic to hidden backends.
This model offers several advantages for criminals: lower costs, reduced exposure to law enforcement in their home countries, and the ability to quickly spin up new infrastructure when one network is discovered.
The £14.7 Billion Question
The Media Land sanctions highlighted a sobering statistic: cyber-attacks cost the UK economy £14.7 billion in a single year. This isn't just about stolen data or ransomed files—it's lost productivity, recovery costs, reputational damage, and economic opportunity destroyed by criminal operations enabled by bulletproof hosting providers.
The scale of the problem demands the multi-faceted response now emerging:
Sanctions and Seizures: Targeting both the infrastructure and the finances of bulletproof providers, making it harder for them to operate and profit.
Technical Countermeasures: Implementing network-level filtering and monitoring to identify and block malicious hosting activity.
International Cooperation: Coordinating actions across jurisdictions to prevent providers from simply relocating to more permissive countries.
Private Sector Engagement: Working with legitimate hosting providers and cloud services to prevent bulletproof operators from hiding within their networks.
Public Attribution: Naming and shaming operators to disrupt their business relationships and make recruitment harder.

The Treasury Department's comprehensive approach demonstrates this commitment. As emphasized in their November 19 announcement: "OFAC will take all possible steps to counter sanctions evasion activity by malicious cyber actors and their enablers." The sanctions not only block all property and interests within U.S. jurisdiction but expose financial institutions to enforcement action if they facilitate transactions with designated persons—creating a powerful deterrent against supporting bulletproof infrastructure.
Looking Ahead
The fight against bulletproof hosting is far from over. As one provider falls, others emerge with new techniques for evading detection. The corporate structures grow more complex, the technical methods more sophisticated, and the jurisdictional challenges more daunting.
But the recent wave of enforcement actions suggests a new era in cybercrime disruption. Rather than just going after individual hackers, authorities are systematically dismantling the infrastructure that makes modern cybercrime possible.
Foreign Secretary Yvette Cooper captured this shift: "Cyber criminals think they can act in the shadows, targeting hardworking British people and ruining livelihoods with impunity. But they are mistaken—together with our allies, we are exposing their dark networks and going after those responsible."
The message is clear: providing the infrastructure for cybercrime now carries consequences. Whether it's sufficient to turn the tide remains to be seen, but the pressure on bulletproof hosting providers has never been greater.
As ransomware gangs scramble to find new hosting arrangements and bulletproof providers implement elaborate evasion techniques, one thing is certain: the digital arms race between law enforcement and cybercriminals has entered a new and critical phase. The outcome will shape the security of critical infrastructure, businesses, and individuals for years to come.

Key Takeaways for Organizations
For security teams and organizations, the bulletproof hosting threat landscape demands proactive defense:
- Monitor for Bulletproof Indicators: Watch for connections to known bulletproof hosting IP ranges and autonomous systems using updated threat intelligence feeds. Be aware that Spamhaus has observed a rise in shell corporations in the UK and USA—jurisdictions that are more likely to fly under the radar during superficial customer vetting.
- Implement Network Filtering: Deploy border gateway filtering targeting high-confidence malicious resources while minimizing impacts on legitimate traffic. Use both IP-based and ASN-based blocklists to counter rapid IP cycling tactics.
- Stay Informed on Sanctions: Track OFAC and international sanctions lists to ensure your organization doesn't inadvertently interact with designated entities.
- Report Suspicious Activity: Contribute to the fight by reporting abuse and sharing indicators with information sharing organizations.
- Deploy Domain-Based Blocklists: IP-based filtering alone is insufficient when bulletproof hosters abuse trusted services like CDNs. Implement domain-based blocklists such as Spamhaus's Domain Blocklist (DBL) on mail and perimeter infrastructure.
- Don't Focus Exclusively on Known Bulletproof Hosters: Spamhaus warns that miscreants deliberately place botnet controllers and malicious infrastructure at abused, semi-legitimate hosting providers with sloppy abuse prevention procedures to maintain clean IP reputations and evade blocklists.
- Assume Breach Mentality: Given the resilience of these operations, implement defense-in-depth assuming that attackers will find hosting infrastructure regardless of disruption efforts.
The bulletproof hosting industry has evolved from crude server farms to sophisticated corporate operations. But as law enforcement adapts its strategies and international cooperation deepens, the days of consequence-free criminal hosting may finally be numbered.

Yet Spamhaus researchers caution that a lasting decline in bulletproof hosting activity remains unlikely given its fundamental importance to cybercrime. Instead, they expect non-monolithic operations—with their separation of liabilities and disposable infrastructure—to continue thriving in Western jurisdictions under law enforcement pressure, while monolithic operators persist in regions like Russia where enforcement remains less effective.

Academic research supports this assessment. A 2019 study by researchers at New York University and Delft University of Technology examined MaxiDed, a bulletproof hosting operation dismantled in the Netherlands. Their findings revealed that profit margins for bulletproof hosting are remarkably thin—so slim that even marginal increases in operating costs can render the business unsustainable. This suggests that sustained pressure through sanctions, infrastructure seizures, and increased operational costs may prove more effective than attempting to arrest operators in non-cooperative jurisdictions.
The abuse of trusted legitimate services and ongoing failures to thwart platform abuse will likely continue at high operational tempo. For defenders, this means the challenge isn't just identifying bulletproof hosters, but anticipating how they'll exploit the next vulnerability in legitimate internet infrastructure.

For more coverage of law enforcement operations targeting cybercrime infrastructure, see our previous reporting on Operation Endgame and the CrazyRDP takedown.