The Cyber Proxy War: How Israel and Iran Are Fighting Through Hacktivist Coalitions

As tensions escalate between Israel and Iran, a shadow war is being fought in cyberspace by dozens of hacktivist groups serving as digital proxies. From coordinated DDoS attacks to infrastructure sabotage, this parallel conflict reveals how modern warfare has evolved beyond traditional battlefields.
On June 13, 2025, as Israeli jets launched Operation Rising Lion—a large-scale aerial assault targeting Iranian nuclear facilities and military sites—a different kind of battle erupted simultaneously in cyberspace. Within hours, dozens of hacktivist groups aligned with Iran unleashed a coordinated wave of cyberattacks against Israeli infrastructure, government websites, and civilian systems. This wasn't coincidental timing; it was the manifestation of an increasingly sophisticated cyber proxy war that has been developing alongside the physical conflict between Israel and Iran.
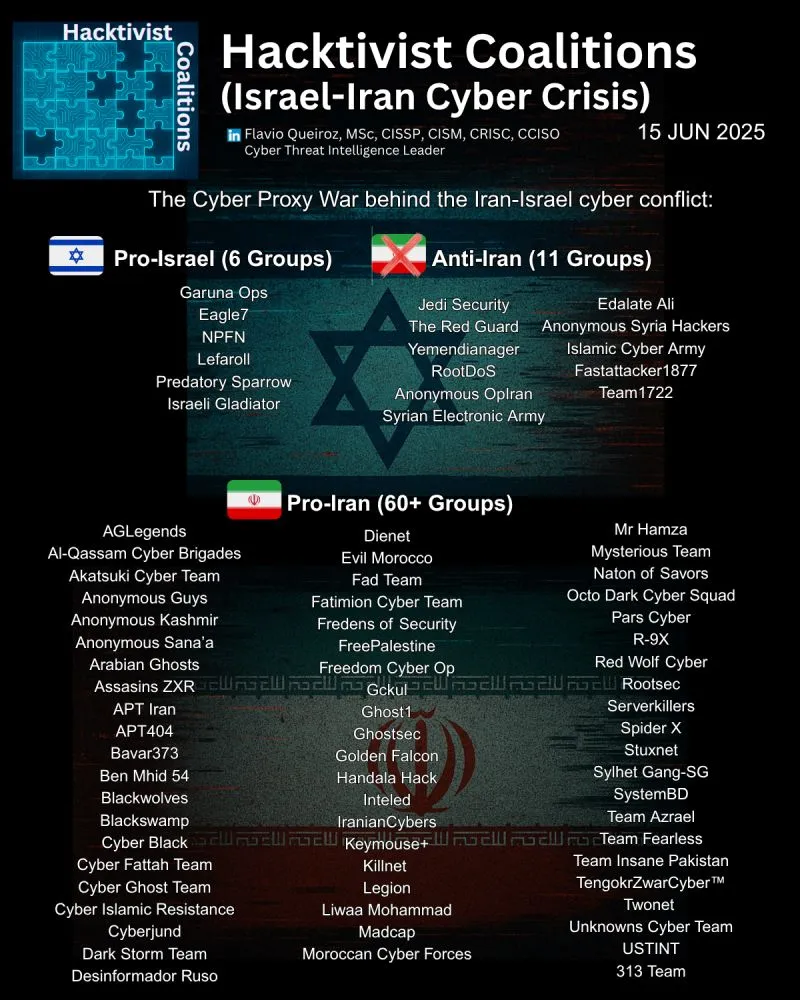
The digital battlefield has become a critical front in the Israel-Iran confrontation, with both sides leveraging vast networks of hacktivist groups to conduct operations that blur the lines between state-sponsored activity and grassroots cyber activism. Intelligence sources indicate that Iran has mobilized over 60 hacktivist groups in support of its objectives, while Israel has rallied approximately 17 groups to defend its interests and conduct counter-operations.
The Architecture of Digital Warfare
Iran's Vast Hacktivist Network
Iran's cyber strategy relies heavily on what intelligence analysts call "hacktivist proxies"—nominally independent groups that receive direction, resources, and protection from Iranian intelligence services, particularly the Islamic Revolutionary Guard Corps (IRGC). These groups operate with varying degrees of sophistication and independence, but share common objectives aligned with Iranian strategic goals.
Among the most prominent Iranian-affiliated groups is CyberAv3ngers, directly linked to the IRGC's Cyber-Electronic Command. This group has claimed responsibility for numerous attacks against critical infrastructure, particularly targeting Israeli-made programmable logic controllers (PLCs) used in U.S. water facilities. Since November 2023, CyberAv3ngers has exploited default credentials in Unitronics devices across multiple U.S. states, leaving defacement messages stating "You have been hacked, down with Israel. Every equipment 'made in Israel' is CyberAv3ngers legal target."
Handala Hack, named after a Palestinian cartoon character, represents another sophisticated Iranian proxy. The group has claimed responsibility for high-profile attacks including breaches of Israeli kindergarten PA systems, where they broadcast threatening messages, and alleged penetration of Israel's Soreq Nuclear Research Center. Security researchers have attributed Handala to Iran's Ministry of Intelligence (MOIS), specifically a cyber unit within the counter-cyber threat division designed for propaganda purposes.
Anonymous Sudan, though geographically distant from the Middle East conflict, has emerged as a key collaborator with Iranian proxies. The group, indicted by U.S. authorities in 2024, conducted over 35,000 DDoS attacks before its main operators were arrested. Their collaboration with pro-Palestinian hacktivist groups demonstrates how Iran has successfully built international coalitions to amplify its cyber capabilities.
Israel's Digital Response Network
Israel's hacktivist ecosystem is smaller but more technologically sophisticated, reflecting the country's status as a global cybersecurity hub. Pro-Israeli groups include Predatory Sparrow, which has conducted high-profile operations against Iranian infrastructure, including a December 2024 attack that disrupted 60% of Iran's gas stations.
Israeli Gladiator and other groups have focused on defensive operations and counter-attacks against Iranian proxies. These groups often coordinate with Israel's National Cyber Directorate (INCD), which reported thwarting 85 Iranian cyberattacks in 2025 alone, including targeted phishing campaigns against senior Israeli officials.
The smaller number of pro-Israeli groups is offset by their technical capabilities and integration with Israel's formal cyber defense infrastructure. Unlike Iran's model of numerous semi-autonomous proxies, Israel's approach emphasizes quality over quantity, with groups that possess advanced capabilities and close coordination with state authorities.

Operational Campaigns and Tactics
The OpIsrael Phenomenon
One of the most visible manifestations of the cyber proxy war is the annual OpIsrael campaign, originally launched by Anonymous in 2013. This coordinated effort occurs every April 7th, coinciding with Holocaust Remembrance Day, and has evolved into a massive international hacktivist operation involving dozens of groups.
Analysis of 2025 OpIsrael preparations revealed unprecedented coordination among approximately 48 hacktivist groups across multiple continents. The campaign's scope has expanded beyond Israel to include what organizers call "Israel's supporters," particularly the United States and European nations. Cybersecurity firm Radware observed extensive reconnaissance and vulnerability scanning beginning in late March, with propaganda and operational coordination intensifying through private Telegram channels.
The campaign demonstrates sophisticated operational planning reminiscent of military operations. Groups conduct preliminary reconnaissance, share intelligence about potential targets, coordinate timing of attacks, and maintain psychological warfare components designed to amplify the perceived impact of their operations.
Infrastructure Targeting and Real-World Impact
Iranian hacktivist proxies have shown particular interest in critical infrastructure, especially systems with Israeli components or connections. The CyberAv3ngers group's targeting of Unitronics PLCs represents a strategic approach to exploiting supply chain vulnerabilities. By focusing on Israeli-made equipment in U.S. infrastructure, Iran achieves dual objectives: demonstrating its reach beyond the Middle East and creating pressure on Israel's international relationships.
Recent attacks have included penetration of kindergarten PA systems, where Iranian hackers broadcast threatening messages to children and staff; disruption of point-of-sale systems used across Israeli gas stations and supermarkets; attacks on digital signage infrastructure, displaying violent propaganda messages; and attempts to compromise emergency response systems and traffic management networks.
The psychological impact of these attacks often exceeds their technical damage. When Iranian proxies successfully broadcast threats through kindergarten speakers, the operational disruption was minimal, but the psychological effect on parents and society was significant.

Technological Evolution and Sophistication
Israeli cyber officials describe the conflict's evolution through three distinct phases. Phase one involved basic DDoS attacks and website defacements using simple tools. Phase two saw increased coordination and more sophisticated targeting. Phase three, which began in 2024, features the use of legitimate remote management tools, purchased infrastructure access, and exploitation of zero-day vulnerabilities within hours of disclosure.
"If previously, exploitation of one-days took the Iranian state a couple of days, or a week, now it's 40 minutes, half an hour. This is new," according to Israeli National Cyber Directorate officials. This rapid exploitation capability suggests significant investment in automated vulnerability research and weaponization systems.
Iranian proxies have also demonstrated improved operational security and attribution management. Groups frequently share resources, collaborate on target development, and coordinate messaging through encrypted channels. This distributed approach makes attribution challenging and provides plausible deniability for Iranian intelligence services.
State Sponsorship and Plausible Deniability
The Proxy Model's Advantages
Iran's reliance on hacktivist proxies provides several strategic advantages over direct state-conducted operations. The model offers plausible deniability, allowing Iran to conduct aggressive cyber operations while maintaining diplomatic flexibility. Distributed operations across multiple groups make comprehensive defense and attribution more difficult for targets. The approach enables rapid scaling of operations during periods of heightened tension without formal escalation declarations.
The hacktivist model also provides ideological cover, as many participants genuinely believe in their stated causes. This authentic motivation makes the groups more effective at recruitment and harder to counter through traditional deterrence mechanisms.

Intelligence Integration and Direction
Despite claims of independence, evidence suggests close coordination between Iranian intelligence services and hacktivist proxies. U.S. and Israeli intelligence agencies have documented direct IRGC involvement in CyberAv3ngers operations, including provision of technical resources and target selection. The timing of major hacktivist campaigns consistently correlates with Iranian strategic objectives and military actions.
Microsoft's 2024 Digital Defense Report noted that since the Gaza war began, Iran "surged its cyber, influence, and cyber-enabled influence operations against Israel." From October 2023 to July 2024, nearly half of Iranian operations targeted Israeli companies, representing a dramatic shift from previous patterns where only 10% of Iranian attacks focused on Israel.
International Dimensions and Collateral Impact
Expanding Target Sets
The cyber proxy war has increasingly expanded beyond Israel and Iran to affect third-party nations and organizations. Iranian proxies have targeted U.S. infrastructure using the rationale that American systems incorporate Israeli technology. European nations supporting Israel have faced increased cyber pressure from Iranian-aligned groups.
This expansion reflects Iran's strategy of using cyber capabilities to pressure Israel's international supporters. By creating costs for countries that support Israel, Iran hopes to isolate Israel diplomatically and reduce international backing for Israeli positions.
Coalition Building and International Alliances
Iranian hacktivist groups have successfully built coalitions with ideologically aligned organizations worldwide. Anonymous Sudan's collaboration with Middle Eastern groups, despite geographical distance, demonstrates how shared opposition to Israeli policies can overcome traditional boundaries.
The involvement of groups like Killnet, originally focused on Russia-Ukraine conflict, in anti-Israeli operations shows how Iran has leveraged broader anti-Western sentiments to build cyber coalitions. These partnerships provide Iran with expanded capabilities and geographic reach while offering partner groups access to Iranian resources and expertise.

Defensive Responses and Countermeasures
Israeli Cyber Resilience
Israel's National Cyber Directorate has adapted to the escalating threat environment through enhanced monitoring, improved coordination with private sector entities, and development of rapid response capabilities. The country's cyber defense benefits from its advanced technology sector and integration between civilian and military cyber capabilities.
Israeli authorities report successfully preventing the vast majority of Iranian attacks, with cyber defenses intercepting approximately 90% of attempted intrusions. However, the sheer volume of attacks—an estimated 3 billion attempts as of July 2024—creates significant resource strain and occasional successful penetrations.
International Cooperation and Law Enforcement
U.S. law enforcement has increased efforts to disrupt hacktivist networks, successfully indicting Anonymous Sudan operators and dismantling some infrastructure. However, the distributed nature of these groups and their operation from jurisdictions with limited law enforcement cooperation makes comprehensive disruption challenging.
The Department of Justice's October 2024 indictment of two Sudanese nationals behind Anonymous Sudan represents a significant success, but dozens of other groups continue operating. The case demonstrates both the potential for law enforcement action and the limitations of traditional legal approaches to this problem.

Future Implications and Escalation Risks
Technological Advancement and Automation
The rapid evolution of hacktivist capabilities suggests continued advancement in automation and artificial intelligence applications. Iranian groups are increasingly using machine learning for target identification, automated vulnerability exploitation, and coordinated attack execution.
The integration of AI into hacktivist operations could dramatically increase the scale and effectiveness of cyber proxy warfare. Current trends suggest movement toward fully automated attack systems capable of identifying, planning, and executing operations with minimal human oversight.
Potential for Physical Escalation
While most hacktivist operations focus on disruption and propaganda rather than destructive effects, the targeting of critical infrastructure creates risks of physical consequences. Successful attacks on power grids, water systems, or transportation infrastructure could cause casualties and trigger more aggressive responses.
Israeli officials have warned that significant cyber attacks causing physical harm could prompt military retaliation against cyber infrastructure. This creates escalation risks where cyber operations could trigger kinetic responses, potentially expanding conflicts beyond their original scope.
Normalization of Cyber Proxy Warfare
The Israel-Iran cyber proxy war represents a potential model for future international conflicts. The success of both sides in mobilizing hacktivist networks suggests that cyber proxy warfare may become a standard component of international competition.
This normalization carries risks for global cybersecurity, as it legitimizes the use of non-state actors for government objectives and blurs traditional distinctions between state and non-state cyber activities. The precedent could encourage other nations to develop similar proxy networks, leading to an increasingly chaotic cyber environment.
Economic and Social Consequences
Impact on Civilian Infrastructure
The targeting of civilian infrastructure by hacktivist groups creates significant economic costs and social disruption. Israeli businesses face increased cybersecurity expenses, reduced operational efficiency, and reputational damage from successful attacks.
The psychological impact on civilian populations, particularly incidents like the kindergarten PA system attacks, creates social costs that extend beyond immediate economic damage. These effects serve Iranian strategic objectives by undermining public confidence in government protection capabilities.
Global Supply Chain Vulnerabilities
The targeting of Israeli-made equipment in third-country infrastructure highlights vulnerabilities in global supply chains. Organizations worldwide using Israeli technology face increased cyber risks, potentially affecting procurement decisions and international trade relationships.
This dynamic creates economic pressure on Israeli technology companies and could influence international perceptions of Israeli cyber capabilities. Iran's strategy of targeting Israeli technology wherever it appears globally represents an innovative approach to economic warfare through cyber means.
The Information Warfare Component
Propaganda and Psychological Operations
Many hacktivist operations prioritize psychological impact over technical damage. Groups frequently exaggerate their successes, claim responsibility for unrelated incidents, and use dramatic messaging to amplify perceived threats.
The information warfare component serves multiple objectives: undermining public confidence in government cybersecurity capabilities, creating fear and uncertainty among target populations, influencing international perceptions of the conflict, and recruiting additional supporters for hacktivist causes.
Social Media Exploitation
Hacktivist groups have become sophisticated users of social media platforms for operational coordination, propaganda dissemination, and recruitment activities. Telegram channels serve as primary coordination mechanisms, while Twitter and other platforms amplify messaging and claim responsibility for attacks.
The decentralized nature of social media makes comprehensive countermeasures difficult, while the global reach of these platforms enables hacktivist groups to build international audiences and support networks.
Conclusion: The New Normal of Digital Conflict
The Israel-Iran cyber proxy war represents a fundamental evolution in how nations conduct international competition. By mobilizing vast networks of hacktivist groups, both sides have created sustained cyber conflict capabilities that operate continuously rather than during discrete conflict periods.
This model offers several advantages over traditional state-sponsored cyber operations: lower attribution risks, expanded operational capacity, ideological legitimacy, and reduced escalation thresholds. However, it also creates risks of uncontrolled escalation, civilian harm, and normalization of aggressive cyber activities.
The involvement of over 60 Iranian-aligned hacktivist groups demonstrates the potential scale of proxy cyber warfare. As these capabilities continue developing, they may become standard components of international competition, fundamentally altering the cybersecurity landscape.
For the international community, the Israel-Iran cyber proxy war provides important lessons about the evolution of digital conflict. Traditional approaches to cyber deterrence and attribution may prove inadequate for addressing distributed proxy networks. New frameworks for international cooperation, law enforcement, and conflict management in cyberspace will be necessary to prevent these tactics from destabilizing global digital infrastructure.
The cyber proxy war is no longer a supplementary component of the Israel-Iran conflict—it has become a primary battleground where both sides conduct sustained operations with significant real-world consequences. As this model spreads to other international disputes, understanding its dynamics and developing effective responses will become critical for global cybersecurity and international stability.
The networks of digital proxy warriors fighting in cyberspace today may represent the future of international conflict—a future where the boundaries between state and non-state actors, military and civilian targets, and virtual and physical consequences become increasingly blurred. The challenge for policymakers, cybersecurity professionals, and the international community is adapting to this new reality while preserving the stability and security of global digital infrastructure.










