The Digital Battlefield: How Three Major DDoS Attacks in July 2025 Reveal Evolving Cyber Warfare Tactics

The third week of July 2025 witnessed a surge in coordinated cyberattacks that paint a concerning picture of how digital warfare is evolving across different theaters of conflict. Three distinct distributed denial-of-service (DDoS) campaigns targeted critical infrastructure in occupied Crimea, independent media in Ukraine, and commercial enterprises in Russia, each revealing unique aspects of modern cyber operations and their strategic implications.

The Crimean Communication Blackout: Infrastructure as a Weapon
Fixed-line communication operators across occupied Crimea found themselves under siege as a massive DDoS attack disrupted telecommunications infrastructure throughout the peninsula. The assault, reported by the region's "ministry of internal policy, information, and communications," caused periodic service unavailability that affected thousands of residents and businesses.
The attack's primary focus on Sevastopol, Crimea's largest city, demonstrated surgical precision in targeting. Miranda Media, the city's main internet provider and a subsidiary of Russian national telecom giant Rostelecom, bore the brunt of the assault. This targeting is particularly significant given that Miranda Media was sanctioned by the European Union in 2023 for providing services to illegal authorities and institutions in the occupied territory.
The incident follows a documented pattern of Ukrainian cyber operations against Russian-occupied territories. Previous attacks by Ukraine's Main Intelligence Directorate (HUR) have successfully left 250,000 people without communication services, affecting subscribers across occupied Crimea and parts of Zaporizhzhya and Kherson oblasts. These operations represent a strategic shift toward using cyber capabilities to degrade Russian control mechanisms in occupied territories without the need for kinetic military action.
Strategic Implications
The Crimean attacks serve multiple strategic purposes beyond immediate disruption. By targeting communication infrastructure, these operations:
- Degrade Administrative Control: Communication blackouts complicate the ability of occupying authorities to coordinate administrative functions and maintain control over civilian populations.
- Demonstrate Reach: The attacks signal that Ukrainian cyber capabilities can penetrate deep into Russian-controlled territory, challenging assumptions about the security of occupied zones.
- Create Economic Pressure: Disrupted telecommunications impact both civilian and military operations, imposing costs on the occupying power while undermining confidence in Russian protection capabilities.

The Kyiv Independent Under Fire: When Journalism Meets Cyber Warfare
The timing of the DDoS attack against The Kyiv Independent between July 22-23, 2025, reveals how cyber operations increasingly target independent media during politically sensitive moments. The assault, generating over 10,000 requests per second, coincided precisely with the outlet's critical coverage of controversial legislation affecting Ukraine's anti-corruption agencies.
The attack followed The Kyiv Independent's publication of a scathing editorial titled "Zelensky just betrayed Ukraine's democracy — and everyone fighting for it," which criticized President Zelensky's role in legislation that effectively stripped Ukraine's National Anti-Corruption Bureau (NABU) and Special Anti-Corruption Prosecutor's Office (SAPO) of their independence. The new law, adopted by Ukraine's parliament on July 22, 2025, granted the prosecutor general expanded control over these key anti-corruption bodies.
While the media outlet's technical infrastructure proved resilient—with public-facing content remaining largely accessible despite admin dashboard slowdowns and partial outages—the symbolic impact of the attack cannot be understated. The operation appears designed to send a clear message about the costs of critical journalism during politically sensitive periods.
The Information Warfare Dimension
This attack highlights several troubling trends in the intersection of cyber operations and press freedom:
- Precision Timing: The coordination between the legislative vote and the cyber attack suggests sophisticated intelligence gathering and operational planning.
- Plausible Deniability: DDoS attacks allow state or state-affiliated actors to pressure media outlets while maintaining deniability about direct involvement.
- Chilling Effect: Even unsuccessful attacks can discourage investigative reporting by demonstrating the technical and operational costs of critical coverage.
The resilience of The Kyiv Independent's infrastructure, however, also demonstrates how media organizations are adapting to the reality of operating in contested information environments, implementing technical measures to maintain operations under cyber assault.
Russian Restaurant Chains: When Commerce Becomes Collateral
The most economically disruptive of the three campaigns targeted Russia's food service industry through a coordinated assault on shared technology infrastructure. Beginning July 18, 2025, attackers launched a sustained five-day DDoS campaign against automation provider iiko and its hosting partner ESTT, paralyzing operations across multiple major restaurant chains.
The affected businesses read like a who's who of Russia's post-sanctions food service landscape: Vkusno i Tochka (McDonald's successor), coffee chain Cofix, and Sushi Master, among others. By targeting iiko—a central automation provider that manages point-of-sale systems, inventory management, and customer-facing applications for hundreds of Russian restaurants—the attackers achieved maximum disruption with surgical precision.

The attack methodology demonstrated sophisticated understanding of supply chain vulnerabilities. Rather than attempting to overwhelm each individual restaurant chain's systems, the operation focused on the shared infrastructure that connected them all. This approach multiplied the impact while potentially reducing the technical resources required for execution.
Economic Warfare in the Digital Age
The restaurant chain attacks illuminate how cyber operations are expanding beyond traditional government and critical infrastructure targets to encompass commercial supply chains:
- Cascade Effects: By targeting shared service providers, attackers can disrupt dozens of businesses simultaneously, multiplying economic impact while minimizing technical overhead.
- Consumer Impact: Unlike attacks on government systems, disruptions to restaurant chains directly affect civilian populations, potentially eroding public confidence in digital infrastructure.
- Economic Signaling: The five-day duration of the attacks suggests a calculated effort to impose sustained economic costs rather than achieve symbolic impact through brief disruption.
The choice to target restaurant chains—businesses that serve ordinary Russians rather than government or military functions—may represent an evolution in cyber warfare tactics toward broader economic pressure campaigns designed to impact civilian morale and economic confidence.
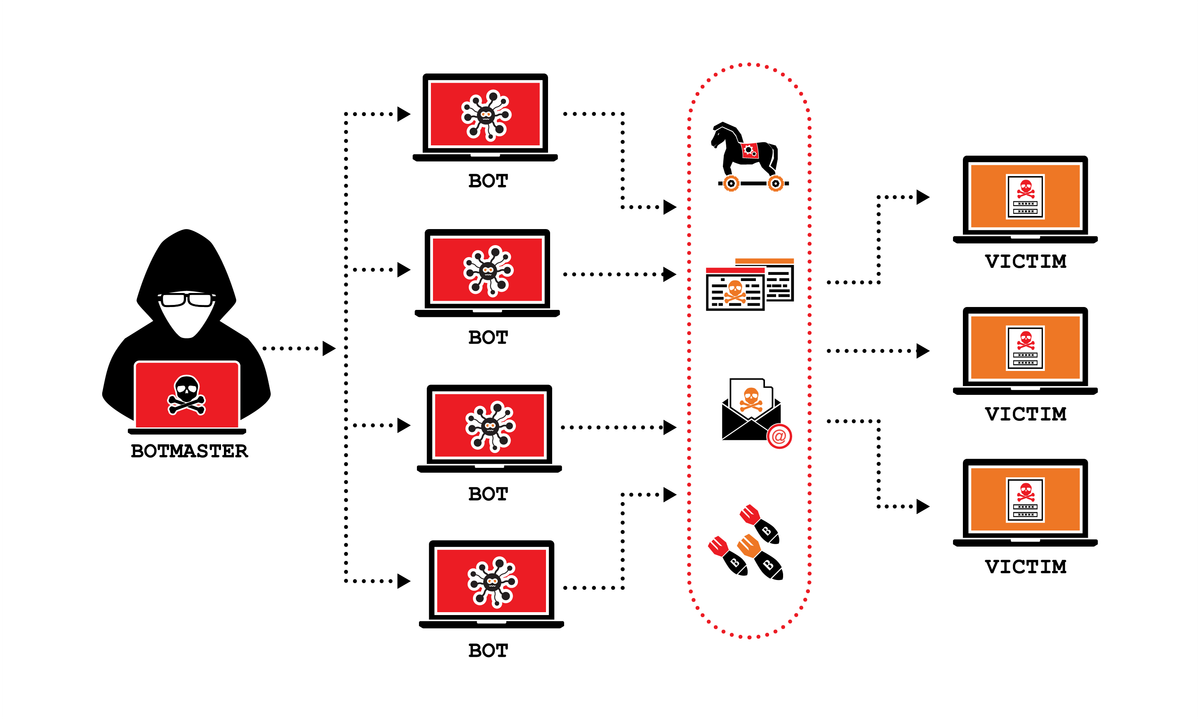
Technical Analysis: Evolution of DDoS Methodologies
The three campaigns demonstrate significant sophistication in their technical execution, revealing several important trends in DDoS attack methodologies:
Volume and Persistence
The Kyiv Independent attack's peak of 10,000 requests per second, while substantial, represents the lower end of modern DDoS capabilities. More significant was the sustained nature of these operations—particularly the five-day assault on Russian restaurant chains—indicating attackers' access to substantial botnet resources or amplification techniques.

Target Selection Intelligence
Each campaign demonstrated detailed reconnaissance and strategic target selection:
- Infrastructure Mapping: The Crimean attacks precisely targeted key nodes in the telecommunications infrastructure, suggesting detailed knowledge of network topology.
- Timing Coordination: The Kyiv Independent attack's synchronization with legislative proceedings required sophisticated intelligence gathering and operational coordination.
- Supply Chain Analysis: The restaurant chain attacks revealed deep understanding of shared infrastructure dependencies within Russia's food service sector.
Resilience Testing
The varying degrees of success across the three campaigns provide insights into defensive capabilities:
- Media Resilience: The Kyiv Independent's ability to maintain public-facing services despite admin disruptions suggests investment in distributed content delivery and attack mitigation infrastructure.
- Infrastructure Vulnerability: The telecommunications disruptions in Crimea indicate potential weaknesses in critical infrastructure protection within occupied territories.
- Commercial Preparedness: The complete paralysis of restaurant chain operations suggests limited DDoS preparedness within Russia's commercial sector.
Attribution Challenges and Strategic Implications
While none of the three campaigns included explicit attribution claims, the targeting patterns and timing provide circumstantial evidence about potential actors:
State-Level Capabilities
The coordination required for the Kyiv Independent attack—particularly its precise timing with legislative proceedings—suggests resources and intelligence capabilities typically associated with state actors or their proxies. Similarly, the sustained nature of the restaurant chain campaign indicates access to substantial technical resources.
Proxy Operations
The use of DDoS attacks provides convenient cover for state actors seeking to pressure targets while maintaining plausible deniability. This dynamic complicates both attribution and response, as victims and their allies must navigate the possibility that retaliation could escalate beyond the cyber domain.
Escalation Dynamics
The expansion of targets from traditional government and critical infrastructure to media organizations and commercial enterprises suggests a lowering of thresholds for cyber operations. This trend raises concerns about escalation dynamics, as the boundaries between legitimate targets and civilian infrastructure continue to blur.

Defensive Implications and Future Preparedness
The July 2025 campaigns offer several lessons for organizations seeking to improve their cyber resilience:
Infrastructure Hardening
The mixed success rates across different targets highlight the importance of proactive DDoS mitigation:
- Distributed Architecture: Organizations operating in contested environments should prioritize geographically distributed infrastructure that can maintain operations despite regional attacks.
- Shared Responsibility: The restaurant chain attacks underscore the risks of depending on third-party service providers without adequate resilience guarantees.
- Capacity Planning: Defensive preparations must account for sustained attacks lasting days rather than hours, requiring substantial reserve capacity and automated response systems.
Intelligence Integration
The timing precision demonstrated in several attacks emphasizes the importance of threat intelligence:
- Operational Security: Organizations engaged in sensitive activities should assume their operational timelines are known to potential attackers and plan accordingly.
- Early Warning: Integration with threat intelligence services can provide advance warning of planned operations, enabling proactive defensive measures.
- Context Awareness: Understanding the broader geopolitical context helps organizations assess their risk profile and prioritize defensive investments.
Looking Forward: The Cyber Conflict Continuum
The three July 2025 campaigns represent snapshots of a rapidly evolving cyber conflict landscape where the boundaries between warfare, activism, and criminality continue to blur. Several trends emerge from this analysis:
Democratization of Capabilities
The technical sophistication required for these attacks, while substantial, remains within reach of non-state actors with sufficient resources and motivation. This democratization of cyber capabilities complicates traditional deterrence models and expands the range of potential threat actors.
Target Expansion
The progression from government systems to media organizations to commercial enterprises suggests a continuing expansion of what constitutes legitimate cyber targets. This trend challenges traditional concepts of civilian immunity and raises questions about proportionality in cyber operations.
Economic Integration
The restaurant chain attacks particularly highlight how cyber operations are increasingly integrated into broader economic warfare strategies. As digital infrastructure becomes more central to economic activity, cyber attacks offer increasingly attractive alternatives to traditional economic sanctions or military action.
Conclusion: Preparing for an Uncertain Digital Future
The cyberattacks of July 2025 provide a sobering reminder that digital infrastructure has become both the backbone of modern society and a primary battlefield for contemporary conflicts. The sophistication, coordination, and strategic timing of these operations signal a new phase in cyber warfare where no sector—from telecommunications to journalism to food service—remains immune from digital assault.
For organizations operating in today's threat environment, the lessons are clear: cyber resilience cannot be an afterthought but must be integrated into core operational planning. The attacks also highlight the critical importance of international cooperation in establishing norms and boundaries for cyber operations, particularly as the range of targets continues to expand.
As we move forward, the challenge will be maintaining the openness and connectivity that define modern digital society while building sufficient resilience to withstand attacks from increasingly sophisticated and motivated adversaries. The events of July 2025 remind us that in the digital age, the next battlefield may be just a click away.
For more analysis on cybersecurity trends and threat intelligence, subscribe to our newsletter and follow our ongoing coverage of digital security developments worldwide.