The Great NPM Heist: How 2 Billion Weekly Downloads Were Weaponized in History's Largest JavaScript Supply Chain Attack

Date: September 8, 2025
Impact: 2+ Billion Weekly Downloads
Affected Packages: 18+ Core JavaScript Utilities
Attack Vector: Phishing-Enabled Account Takeover
Primary Target: Cryptocurrency Wallets and Transactions
Executive Summary
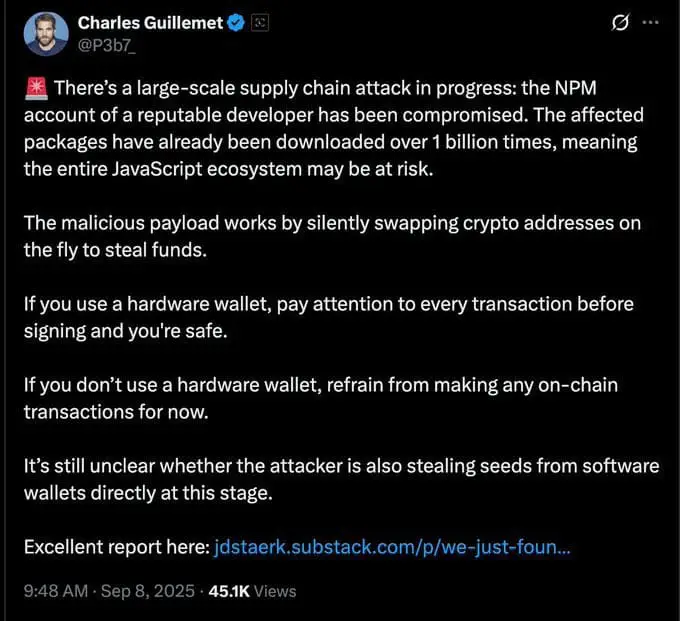
On September 8, 2025, the JavaScript ecosystem experienced its most devastating supply chain attack to date when threat actors compromised the npm account of Josh Junon (known as "Qix-"), a prolific open-source maintainer responsible for some of the most fundamental packages in modern web development. Through a sophisticated phishing campaign, attackers gained control of 18 critical packages with a combined download count exceeding 2 billion per week, injecting cryptocurrency-stealing malware that targeted both passive wallet addresses and active blockchain transactions.
The attack represents a watershed moment in supply chain security, demonstrating how a single compromised maintainer account can potentially impact millions of applications worldwide, from startup projects to Fortune 500 enterprise systems.

The Anatomy of Compromise
Initial Breach Vector
The attack began with what appeared to be a routine security notification. At approximately 13:00 UTC on September 8, Josh Junon received an email purporting to be from npm support at [email protected]. The domain, registered just three days prior on September 5, was a carefully crafted lookalike designed to mimic npm's legitimate support channels.
The phishing email employed a classic urgency tactic, warning maintainers that their two-factor authentication needed immediate updating or their accounts would be locked by September 10. In what Junon later described as occurring during "a long week and a panicky morning," he clicked the malicious link rather than navigating directly to npm as he normally would.
> do largest supply chain attack in history
— vx-underground (@vxunderground) September 8, 2025
> potentially infect millions of apps
> doesnt do the thing good
> makes $0 from compromise
I don't wanna support the villain here, but my guy, you gotta lock in. You could have infected hundreds of millions of apps and you FUMBLE IT pic.twitter.com/MUQ0foTC8j
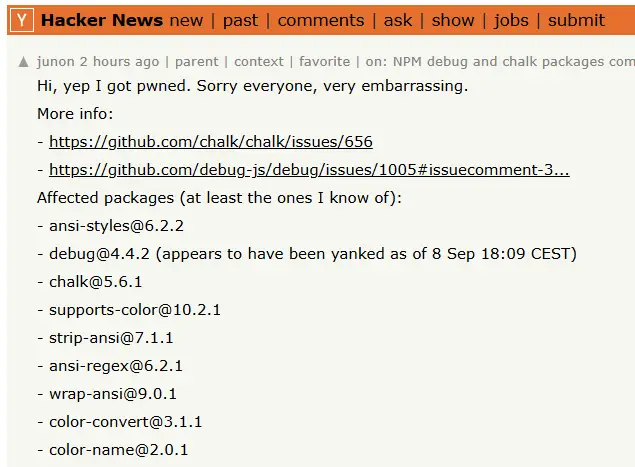
"Hi, yep I got pwned. Sorry everyone, very embarrassing," Junon candidly admitted in a HackerNews comment, demonstrating the transparency that would characterize his response throughout the incident.
The Phishing Infrastructure
The attackers had established a sophisticated phishing infrastructure centered around the npmjs.help domain. Investigation revealed the site included a convincing login form that exfiltrated credentials to:
https://websocket-api2.publicvm.com/images/jpg-to-png.php?name=[name]&pass=[password]
The phishing campaign wasn't limited to Junon alone. Multiple developers reported receiving similar emails, suggesting a broader targeting of high-value npm maintainers. The use of mailtrap for email delivery added another layer of legitimacy to the deceptive communications.
We tested one of the compromised samples.
— Florian Roth ⚡️ (@cyb3rops) September 8, 2025
- 0 detections on VirusTotal
- Detected by THOR with three different YARA rules
Sample:https://t.co/bwDv4i4zL4 https://t.co/upIfI8ddHA pic.twitter.com/yGcs3tU9Es
The Malicious Payload: A Crypto-Heist in Code
Technical Analysis
The injected malware represented a sophisticated piece of engineering specifically designed to operate in browser environments while avoiding detection in server-side Node.js contexts. Security researchers at Aikido, who detected the attack within five minutes of the first malicious package publication, described it as "a browser-based interceptor that hijacks both network traffic and application APIs."
The malware employed a two-pronged approach to cryptocurrency theft:
1. Passive Address Replacement The code monkey-patched critical browser functions including fetch and XMLHttpRequest, allowing it to intercept all network traffic. It then scanned for cryptocurrency addresses across multiple blockchain networks:
- Bitcoin (Legacy and SegWit formats)
- Ethereum
- Solana
- Tron
- Litecoin
- Bitcoin Cash
When detected, legitimate addresses were silently replaced with attacker-controlled alternatives using sophisticated string-matching algorithms designed to produce visually similar addresses, making detection during casual review nearly impossible.
2. Active Transaction Hijacking For users with wallet browser extensions like MetaMask or Phantom, the malware took a more aggressive approach. It hijacked the window.ethereum object and other wallet APIs, intercepting transaction requests before they could be signed. This allowed attackers to modify transaction parameters in real-time, redirecting funds to their addresses while displaying the original, legitimate address to the user.
Obfuscation and Evasion
The malicious code was heavily obfuscated to evade detection by automated security scanners. Researchers noted that the payload included checks for typeof window == undefined to ensure it only executed in browser environments, avoiding server-side execution that might trigger security alerts in CI/CD pipelines.
Ironically, it was this very evasion technique that led to the attack's discovery. Build pipelines began failing with ReferenceError: fetch is not defined errors when the malware attempted to communicate with command-and-control servers in Node.js environments lacking global fetch support.
The Affected Packages: Core Infrastructure Under Attack
The compromised packages read like a who's who of JavaScript development fundamentals:
Primary Targets (with weekly downloads):
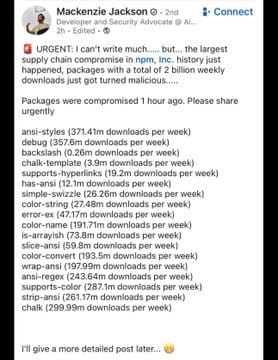
- debug (357.6M) - The ubiquitous debugging utility
- chalk (300M) - Terminal string styling used by countless CLI tools
- ansi-styles (371.4M) - Terminal styling primitives
- supports-color (287.1M) - Color support detection
- strip-ansi (261.2M) - ANSI escape code removal
- ansi-regex (243.6M) - ANSI pattern matching
- wrap-ansi (198M) - String wrapping with ANSI support
- color-convert (193.5M) - Color space conversions
Additional Compromised Packages:
- error-ex (47.2M)
- color-name
- is-arrayish
- slice-ansi
- simple-swizzle
- color-string
- has-ansi
- supports-hyperlinks
- chalk-template
- backslash
Many of these packages are co-maintained with Sindre Sorhus, npm's most popular maintainer by download count, significantly amplifying the attack's potential blast radius.
Timeline of Events
September 5, 2025
- Attackers register the
npmjs.helpphishing domain
September 8, 2025
- 13:00 UTC: Phishing email sent to Josh Junon
- 13:16 UTC: First malicious package versions published to npm
- 13:21 UTC: Aikido Security's threat intelligence systems detect anomalous package updates
- 14:16 UTC: Charlie Eriksen (Aikido) publicly warns about the compromise
- 15:15 UTC: Josh Junon confirms compromise on Bluesky, begins cleanup
- ~16:00 UTC: Junon loses access to his npm account during cleanup
- Evening: NPM begins removing malicious package versions
September 9, 2025
- Some packages like
simple-swizzleremain compromised - Security community continues analysis and remediation efforts
Industry Response and Remediation
Immediate Actions by npm
The npm security team responded by removing identified malicious versions from the registry, though the response was complicated by Junon losing access to his account during the cleanup process. This highlighted a critical gap in incident response procedures when dealing with compromised maintainer accounts.
Detection and Disclosure
Aikido Security's rapid detection and disclosure played a crucial role in limiting the attack's impact. Charlie Eriksen, Aikido's lead malware researcher, noted that the attack was "identified within five minutes and disclosed within an hour," demonstrating the value of real-time package monitoring in the modern threat landscape.
Community Response
The open-source community rallied quickly, with developers sharing warnings across social media platforms, GitHub issues, and security forums. The transparency shown by Josh Junon in immediately acknowledging the compromise and providing detailed information helped coordinate the response effort.
Protecting Your Infrastructure
Immediate Mitigation Steps
For Development Teams:
- Use npm ci in CI/CD Replace
npm installwithnpm ciin your build pipelines to ensure exact versions from lock files are used.
Regenerate Lock Files
rm -rf node_modules package-lock.json
npm install
Pin to Safe Versions Add to your package.json:
{
"overrides": {
"chalk": "5.3.0",
"debug": "4.3.4",
"ansi-styles": "6.2.1",
"color-convert": "2.0.1",
"strip-ansi": "7.1.0",
"error-ex": "1.3.2"
}
}
Audit Your Dependencies
npm audit
npm list chalk debug ansi-styles color-convert
Long-term Security Measures
- Implement Package Cooldown Periods: Don't immediately adopt new package versions in production
- Enable Dependency Scanning: Use tools like Socket.dev, Snyk, or GitHub's Dependabot
- Review Lock File Changes: Treat
package-lock.jsonmodifications with the same scrutiny as application code - Establish Update Policies: Define clear procedures for dependency updates, especially for critical packages
For End Users
- Transaction Vigilance: Carefully verify all cryptocurrency transaction details before signing
- Hardware Wallets: Consider using hardware wallets for significant holdings
- Monitor Wallet Activity: Set up alerts for unexpected transactions
- Update Applications: Ensure all applications are updated to versions using clean dependencies
Initial analysis of the supply chain NPM crypto hack code 👇
— Tal Be'ery (@TalBeerySec) September 8, 2025
Targets Metamask (?) to replace addresses in Tx with similar, attacker controlled addresses https://t.co/KQ64nn097E pic.twitter.com/oqkNdWYiA1
The Year of Living Dangerously: 2025's npm Attack Epidemic
The September 8 compromise represents the culmination of an unprecedented year of npm supply chain attacks, each building on the last in sophistication and impact. Understanding this broader context reveals not isolated incidents but a coordinated assault on the JavaScript ecosystem's foundations.
The Prettier Campaign (July 2025): Testing the Waters
In July 2025, attackers executed a surgical strike against the Prettier ecosystem, compromising five high-profile packages through phishing attacks on maintainer accounts:
- eslint-config-prettier (8.10.1, 9.1.1, 10.1.6, 10.1.7)
- eslint-plugin-prettier (4.2.2, 4.2.3)
- synckit (0.11.9)
- @pkgr/core (0.2.8)
- napi-postinstall (0.3.1)
The attack leveraged a typosquatted domain ("npnjs.com" instead of "npmjs.com") to harvest maintainer credentials. What made this campaign particularly insidious was the discovery that over 14,000 packages had incorrectly declared eslint-config-prettier as a direct dependency rather than a devDependency, causing automated tools like Dependabot to merge malicious updates without human review.
The s1ngularity Incident (August 2025): AI Weaponization
The August 26 "s1ngularity" attack on the Nx build system marked a watershed moment in supply chain warfare, introducing AI as an offensive tool. The malware:
- Weaponized AI assistants including Claude Code, Gemini, and Amazon Q to scan for sensitive files
- Compromised 2,180+ GitHub accounts and leaked thousands of credentials
- Affected 400+ organizations with 5,500+ repositories exposed
- Pioneered the tactic of creating public repositories under victims' own accounts to host stolen data
The attack's use of AI tools to automate reconnaissance represented a new paradigm: turning the very tools developers trust for productivity into instruments of exploitation.
The Flashbots Impersonation Campaign (September 2023-2025): The Long Game
Running for nearly two years, Vietnamese-speaking threat actors maintained a persistent campaign impersonating the trusted Flashbots MEV infrastructure:
- @flashbotts/ethers-provider-bundle - Full API compatibility as cover for wallet theft
- flashbot-sdk-eth - Triggered private key exfiltration
- sdk-ethers - Transmitted mnemonic seeds to Telegram bots
- gram-utilz - Modular data exfiltration framework
This campaign demonstrated remarkable patience and sophistication, with malicious packages remaining undetected for months while quietly harvesting Ethereum developer credentials.
A massive supply chain attack just hit the JavaScript ecosystem.
— StarPlatinum (@StarPlatinumSOL) September 8, 2025
18 core NPM packages were hacked, including chalk, strip ansi and debug.
These libraries have over 2 billion weekly downloads.
Here’s what happened, how it affects crypto and how to stay safe 🧵
(1/8) pic.twitter.com/KcUnfxjNIH
The nodejs-smtp Wallet Drainer (April-September 2025): Electron Exploitation
The nodejs-smtp package showcased a novel attack vector by targeting installed Electron applications:
- Impersonated nodemailer with identical branding and documentation
- Modified Atomic and Exodus wallets by unpacking and reinjecting app.asar files
- Maintained legitimate SMTP functionality to avoid detection
- Redirected cryptocurrency transactions across multiple blockchain networks
This attack proved that npm packages could be used as trojan horses to compromise entirely separate applications on developer machines.
The @0xengine/xmlrpc Campaign (October 2023-November 2024): The Survivor
Perhaps the most remarkable for its longevity, the @0xengine/xmlrpc package operated for over a year:
- Started legitimate then introduced malware in version 1.3.4
- Received 16 updates to maintain appearance of active development
- Combined cryptomining with data theft in a dual-purpose payload
- Infected 68+ machines actively mining Monero
- Harvested SSH keys and credentials every 12 hours
The package's ability to evade detection for 13 months highlights the challenge of monitoring the vast npm ecosystem.
North Korean APT Activity (2025): State-Sponsored Supply Chain Warfare
Microsoft and SecurityScorecard identified the Lazarus Group's "Marstech1" campaign targeting Web3 developers:
- State-sponsored attacks from North Korean threat actors
- Targeted cryptocurrency infrastructure across Windows, macOS, and Linux
- Used port 3000 for C2 communications to blend with development traffic
- Focused on wallet metadata extraction and transaction interception
This represented the intersection of nation-state capabilities with criminal financial motivations.
Common Threads and Evolution
Analyzing 2025's npm attacks reveals disturbing patterns:
1. Cryptocurrency as Primary Target Nearly every major attack targeted cryptocurrency infrastructure, reflecting both the value concentration in Web3 development and the irreversible nature of blockchain transactions.
2. Social Engineering Over Technical Exploits Phishing campaigns proved more effective than zero-days, with maintainer accounts becoming the weakest link in the security chain.
3. Legitimate Functionality as Cover Attackers increasingly maintained legitimate package functionality while hiding malicious code, making detection through testing nearly impossible.
4. AI and Automation The weaponization of AI tools and automated dependency management systems transformed isolated compromises into ecosystem-wide threats.
5. Extended Dwell Time Packages remained malicious for weeks or months, suggesting insufficient real-time monitoring across the npm registry.
Broader Implications: The Supply Chain Security Crisis
A Pattern of Escalation
The September 8 attack didn't occur in isolation but represents the apex of a year-long campaign against JavaScript infrastructure. From the Prettier phishing in July to the AI-powered s1ngularity attack in August, each incident has built upon lessons learned from the last.
The Trust Problem
The incident exposes a fundamental tension in the open-source ecosystem. The same trust and openness that enables rapid innovation also creates vulnerabilities that can be exploited at scale. When packages with billions of weekly downloads can be compromised through a single phishing email, the entire model of distributed package management comes into question.
Economic Impact
While the full financial impact remains to be calculated, the potential for cryptocurrency theft alone could reach millions of dollars. The broader economic cost—including incident response, security audits, and lost productivity across thousands of organizations—may be orders of magnitude higher.
Lessons Learned
For Maintainers
- 2FA Is Not Enough: Even with two-factor authentication enabled, account takeover is possible through reset mechanism exploitation
- Verify Communication Channels: Always navigate directly to official sites rather than clicking email links
- Incident Response Plans: Have clear procedures for responding to account compromises
- Shared Responsibility: Consider requiring multiple maintainer approval for critical package updates
For Organizations
- Supply Chain Risk Assessment: Understand and document your dependency tree
- Defense in Depth: Implement multiple layers of security from development to production
- Incident Preparedness: Have playbooks ready for supply chain compromises
- Zero Trust Dependencies: Treat all external code as potentially hostile
For the Ecosystem
- Enhanced Authentication: npm and other registries need stronger, phishing-resistant authentication methods
- Automated Detection: Investment in real-time malware detection for package registries
- Transparency Requirements: Clearer attribution and audit trails for package modifications
- Community Vigilance: Continued emphasis on responsible disclosure and rapid response
The Road Ahead
The September 2025 npm supply chain attack represents a pivotal moment in JavaScript security history. It demonstrated that even the most fundamental building blocks of modern web development can be turned into weapons against their users. The attack's focus on cryptocurrency theft reflects the evolving motivations of threat actors, who increasingly view supply chain compromises as lucrative financial opportunities rather than mere technical achievements.
As the dust settles, the JavaScript community faces difficult questions about the sustainability of current development practices. The convenience of vast package ecosystems must be balanced against the reality that any update could potentially introduce malicious code affecting millions of users.
The era of blindly trusting package managers may be ending, replaced by a new paradigm of continuous verification and active security monitoring. Organizations must now treat their software supply chain with the same rigor previously reserved for their own code, recognizing that in an interconnected ecosystem, everyone's security depends on everyone else's vigilance.
Conclusion
The Great NPM Heist of September 2025 will be remembered not just for its scale—affecting packages with over 2 billion weekly downloads—but for its demonstration of how human factors remain the weakest link in technical systems. A single moment of fatigue, a convincing phishing email, and suddenly critical infrastructure serving millions of applications worldwide becomes a vector for financial crime.
Yet the incident also showcased the strength of the open-source community: rapid detection, transparent communication, and coordinated response limited what could have been a catastrophic breach. As Josh Junon's forthright acknowledgment showed, there's no shame in falling victim to increasingly sophisticated attacks—only in failing to learn from them.
The path forward requires not just better technology but better processes, stronger community standards, and a recognition that in the modern software ecosystem, security is not a feature but a fundamental requirement. The question is not whether another attack will come, but whether we'll be ready when it does.
This article is part of breached.company's ongoing coverage of major cybersecurity incidents. For real-time updates on this and other security events, follow our threat intelligence feed.