The Immutable Threat: North Korea's EtherHiding Attack Marks a Dangerous New Era in Cyber Warfare
Nation-State Actors Turn Blockchain Into an Indestructible Malware Platform
Executive Summary: In a watershed moment for cybersecurity, North Korean state-sponsored hackers have begun embedding malware directly into blockchain smart contracts, creating a decentralized, nearly indestructible command-and-control infrastructure. This technique, called "EtherHiding," represents a fundamental shift in how malware is distributed and managed—transforming the very properties that make blockchain revolutionary into weapons for cyber espionage and financial crime.
The $1.37 Malware Update That Changes Everything
For just $1.37 in blockchain transaction fees, North Korean hackers can now update their malware payload and distribute it to victims worldwide. This isn't just another cybersecurity threat—it's a paradigm shift that transforms decentralized technology into what researchers call "next-generation bulletproof hosting."
Google Threat Intelligence Group has identified the North Korea-linked threat actor UNC5342 as using EtherHiding to deliver malware and facilitate cryptocurrency theft, marking the first time a nation-state actor has adopted this method. The campaign, active since February 2025, has already led to numerous cryptocurrency heists and represents a troubling evolution in state-sponsored cyber operations.


What Is EtherHiding?
EtherHiding involves embedding malicious code within smart contracts on public blockchains like BNB Smart Chain or Ethereum, essentially turning the blockchain into a decentralized and highly resilient command-and-control server.
Unlike traditional malware infrastructure that can be seized by law enforcement or blocked by cybersecurity firms, blockchain-based malware offers attackers four critical advantages:
1. Decentralization and Resilience
Because malicious code is stored on a decentralized and permissionless blockchain, there is no central server that law enforcement can take down. The malicious code remains accessible as long as the blockchain itself is operational.
2. Anonymity
The pseudonymous nature of blockchain transactions makes it difficult to trace the identity of attackers who deployed the smart contract.
3. Immutability
Once deployed to the blockchain, the malicious smart contract becomes a permanent fixture that cannot be easily removed or altered by anyone except the contract owner.
4. Flexibility and Stealth
Attackers can retrieve malicious payloads using read-only calls that do not leave visible transaction history on the blockchain, making their activities harder to track. The attacker who controls the smart contract can update the malicious payload at any time.
The Contagious Interview: Social Engineering Meets Blockchain
The attack vector is as sophisticated as the technology behind it. North Korean threat actors create convincing but fraudulent profiles on professional networking sites like LinkedIn and job boards, often impersonating recruiters from well-known tech or cryptocurrency firms.
The attack unfolds in several carefully orchestrated stages:
Phase 1: The Lure
Fake recruiters approach developers, particularly those working in cryptocurrency and technology sectors, with attractive job offers. They often move conversations to platforms like Telegram or Discord.
Phase 2: The Trojan Horse
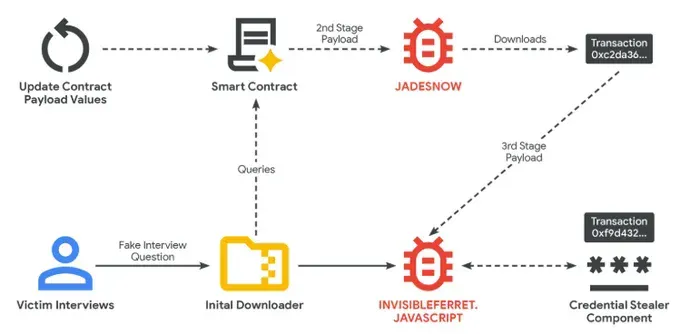
During a technical assessment phase, candidates are asked to perform a coding test or review a project, which requires them to download files from repositories like GitHub. These files contain malicious code.
Phase 3: The Infection Chain
Once executed, the malware initiates a multi-stage infection process targeting Windows, macOS, and Linux systems:
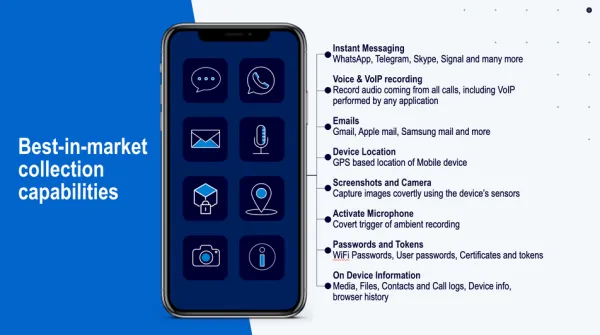
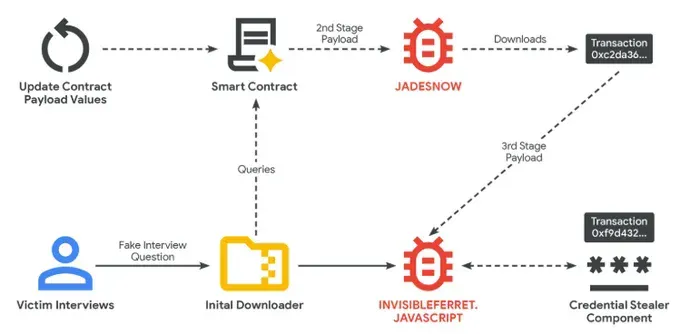
- JADESNOW: A JavaScript-based downloader that queries blockchain smart contracts to retrieve the next stage payload
- BEAVERTAIL: A credential stealer focused on cryptocurrency wallets, browser extensions, and sensitive data
- INVISIBLEFERRET: A sophisticated JavaScript backdoor providing remote control and long-term access to compromised systems
The Technical Deep Dive: How the Blockchain Attack Works
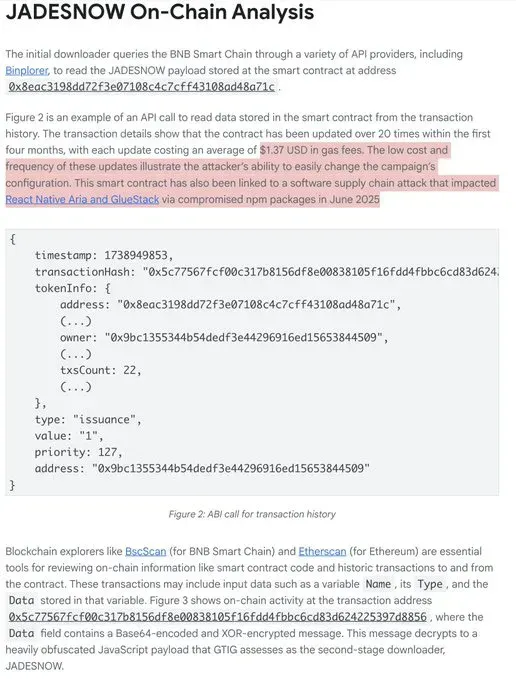
The initial downloader queries the BNB Smart Chain through various API providers to read the JADESNOW payload stored in smart contracts. In one analyzed case, the transaction details showed the contract had been updated over 20 times within the first four months, with each update costing an average of $1.37 USD in gas fees.
What makes this attack particularly sophisticated is UNC5342's use of multiple blockchains within a single operation. It is unusual to see a threat actor make use of multiple blockchains for EtherHiding activity; this may indicate operational compartmentalization between teams of North Korean cyber operators.
The malware can switch between Ethereum and BNB Smart Chain, complicating analysis and leveraging lower transaction fees offered by alternate networks.
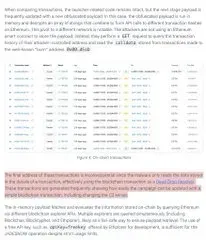
The Clever Dead Drop Resolver
Rather than storing all malicious code in smart contracts, the attackers have developed an even stealthier approach. They perform GET requests to query transaction history of attacker-controlled addresses and read data stored from transactions made to the well-known "burn" address, effectively using blockchain transactions as a Dead Drop Resolver.
This means the malware simply reads transaction data rather than executing smart contract functions, making detection even more challenging.
The Dual Purpose: Espionage and Financial Crime
North Korea's adoption of EtherHiding serves the regime's twin strategic objectives:
Financial Gain
North Korean hackers stole over $1.3 billion across 47 incidents in 2024 and $2.2 billion in the first half of 2025 alone, funding the regime's weapons program through elaborate money laundering networks.
Cyber Espionage
By compromising developers at technology companies, North Korea gains intelligence and establishes footholds for future operations. For high-value targets, a persistent backdoor provides remote control over compromised systems, allowing for long-term espionage and lateral movement within networks.
The Frightening Evolution: What Comes Next?
Security researchers are already warning about the next phase of blockchain-based attacks. As one expert noted in recent analysis, we should expect attackers to experiment with directly loading zero-click exploits onto blockchains, targeting systems and applications that process blockchain data—especially if hosted on the same systems that handle cryptocurrency transactions or store wallets.
The implications are staggering:
The Zero-Click Blockchain Threat
Zero-click exploits bypass user awareness entirely. A single malicious image or file could grant attackers full control over a device, enabling irreversible transactions or exfiltration of private keys.
If attackers successfully embed zero-click exploits in blockchain smart contracts, they could potentially compromise:
- Blockchain explorers and analysis tools
- Cryptocurrency wallet applications
- DeFi platforms and exchanges
- Development environments where blockchain code is tested
The Agentic AI Wild Card
The convergence of agentic AI, low-skill "vibe coding," and blockchain-based malware creates a perfect storm. Developers increasingly use AI coding assistants on the same machines where they store cryptocurrency wallets. This practice, combined with blockchain-based malware that can persist indefinitely, represents what one researcher called "a gold seam that is going to be productive for a long time."
Blockchain Explorers: The Next Natural Target
Platforms like BscScan, Etherscan, and other blockchain explorers process enormous amounts of data and are used by millions of cryptocurrency users. Blockchain explorers are essential tools for reviewing on-chain information like smart contract code and historic transactions. These platforms represent high-value targets for attackers looking to compromise large numbers of users simultaneously.
The Ironic Weakness: Centralization
Despite leveraging decentralized technology, the attack contains a critical vulnerability. Neither UNC5342 nor other threat actors are interacting directly with blockchains when retrieving information from smart contracts; both are utilizing centralized services like API providers and blockchain explorers.
These centralized intermediaries represent points of observation and control, where traffic can be monitored and malicious activity can be addressed through blocking, account suspensions, or other methods.
However, the report notes a troubling reality: When contacted by Google Threat Intelligence Group, responsible API service providers were quick to take action against this malicious activity; however, several other platforms have remained unresponsive. This indifference and lack of collaboration is a significant concern, as it increases the risk of this technique proliferating among threat actors.
Defensive Strategies: How Organizations Can Protect Themselves
For Individuals and Developers
1. Scrutinize Job Offers
Be immediately suspicious of recruiters asking you to download and run code, especially during technical assessments. Legitimate companies provide sandboxed environments for coding tests.
2. Isolate Development Environments
Never store cryptocurrency wallets or sensitive credentials on machines used for running untrusted code or evaluating third-party software.
3. Verify Recruiter Identities
Cross-reference LinkedIn profiles with company websites. Contact companies directly through official channels to verify recruiter identities.
4. Use Hardware Wallets
Store cryptocurrency in hardware wallets that remain offline and are only connected when needed for specific transactions.
For Organizations
1. Implement Browser-Level Controls
Chrome Enterprise can prevent EtherHiding attacks by blocking downloads of dangerous file types like .exe, .msi, .bat, and .dll through the DownloadRestrictions policy.
2. Centralize Update Management
Chrome Enterprise allows administrators to control and automate browser updates, pushing them silently in the background. Employees can be trained with a simple message: "You will never be asked to manually update Chrome."
3. Network-Level Monitoring
Monitor traffic to blockchain API providers and explorers. Establish baselines for normal blockchain interaction patterns and alert on anomalies.
4. Enhanced Endpoint Detection
Deploy endpoint detection and response (EDR) solutions capable of identifying suspicious JavaScript execution, especially code that queries blockchain APIs.
5. Security Awareness Training
Educate employees about the Contagious Interview campaign and similar social engineering tactics. Make them aware that fake job offers are being used to distribute malware.
For API Providers and Blockchain Platforms
The blockchain ecosystem must accept responsibility for preventing abuse of its infrastructure:
1. Implement Abuse Detection
Develop machine learning models to identify suspicious patterns in smart contract deployments and API usage.
2. Rapid Response Protocols
Establish clear processes for responding to reports of malicious smart contracts and suspicious API usage.
3. Collaborative Threat Intelligence
Share indicators of compromise and attack patterns across the blockchain security community.
4. User Warnings
Display prominent warnings when users interact with flagged smart contracts, similar to browser phishing warnings.
The Broader Implications: A New Chapter in Cyber Warfare
The adoption of EtherHiding by a nation-state actor represents more than just another attack technique—it signals a fundamental shift in the cyber threat landscape.
The End of Takedowns
For decades, cybersecurity defenders and law enforcement have relied on the ability to seize servers, block domains, and disrupt command-and-control infrastructure. Blockchain-based malware makes these traditional approaches obsolete.
The Democratization of Sophisticated Attacks
If North Korea is using EtherHiding now, how long before the technique proliferates to ransomware gangs, financially motivated cybercriminals, and hacktivist groups? The low cost and high resilience make it attractive to any threat actor.
The Web3 Security Reckoning
EtherHiding marks a new chapter in the convergence of state cyber operations, financial motives, and Web3 infrastructures. The cryptocurrency and blockchain communities must confront the reality that the same properties making their technology revolutionary also make it attractive to adversaries.
The Attribution Challenge
The pseudonymous nature of blockchain transactions makes it difficult to trace the identity of attackers. This compounds an already difficult attribution problem in cybersecurity, potentially emboldening more aggressive state-sponsored operations.
The Road Ahead: Adaptation or Exploitation?
We stand at a crossroads. The blockchain ecosystem can either:
Option 1: Adapt
Develop robust abuse detection systems, establish industry-wide security standards, and create mechanisms for rapid response to malicious smart contracts—all while preserving the decentralized ethos that makes blockchain valuable.
Option 2: Remain Complacent
Continue treating blockchain security as someone else's problem, watching as EtherHiding proliferates across threat actor groups and becomes the new standard for resilient malware infrastructure.
The choice isn't just about cryptocurrency exchanges or DeFi platforms. As blockchain technology becomes more integrated into enterprise systems, supply chains, and critical infrastructure, the stakes grow exponentially higher.
Conclusion: The Immutable Threat Demands Immediate Action
North Korea's adoption of EtherHiding isn't just another cybersecurity news story—it's a warning shot across the bow of the entire digital ecosystem. For $1.37 per update, nation-state actors can now deploy malware that is effectively immune to traditional takedown efforts.
EtherHiding represents a shift toward next-generation bulletproof hosting, where the inherent features of blockchain technology are repurposed for malicious ends. This technique underscores the continuous evolution of cyber threats as attackers adapt and leverage new technologies to their advantage.
The question isn't whether other threat actors will adopt this technique—it's how quickly they'll do so and whether defenders can develop effective countermeasures before blockchain-based malware becomes ubiquitous.
The immutable threat is here. The only question is whether our response will be equally resolute.
Indicators of Compromise
Organizations should monitor for the following indicators associated with UNC5342's EtherHiding campaigns:
Malicious Smart Contracts:
- BNB Smart Chain:
0x8eac3198dd72f3e07108c4c7cff43108ad48a71c
Ethereum Transaction Addresses:
0x86d1a21fd151e344ccc0778fd018c281db9d40b6ccd4bdd3588cb40fade1a33a0xc2da361c40279a4f2f84448791377652f2bf41f06d18f19941a96c720228cd0f0xf9d432745ea15dbc00ff319417af3763f72fcf8a4debedbfceeef4246847ce41
Malware Families:
- JADESNOW (JavaScript downloader)
- BEAVERTAIL (credential stealer)
- INVISIBLEFERRET.JAVASCRIPT (backdoor)
Associated Threat Actor Names:
- UNC5342 (Google/Mandiant)
- CL-STA-0240 (Palo Alto Networks)
- DeceptiveDevelopment (ESET)
- DEV#POPPER (Securonix)
- Famous Chollima (CrowdStrike)
- Gwisin Gang (DTEX)
- Tenacious Pungsan (Datadog)
- Void Dokkaebi (Trend Micro)
Additional Resources
- Google Cloud Blog: DPRK Adopts EtherHiding
- MITRE ATT&CK: Dead Drop Resolver (T1102.001)
- Chrome Enterprise Security Policies
This article was researched and compiled on October 17, 2025. Given the rapidly evolving nature of this threat, readers are encouraged to monitor updates from Google Threat Intelligence Group and other cybersecurity vendors for the latest information.