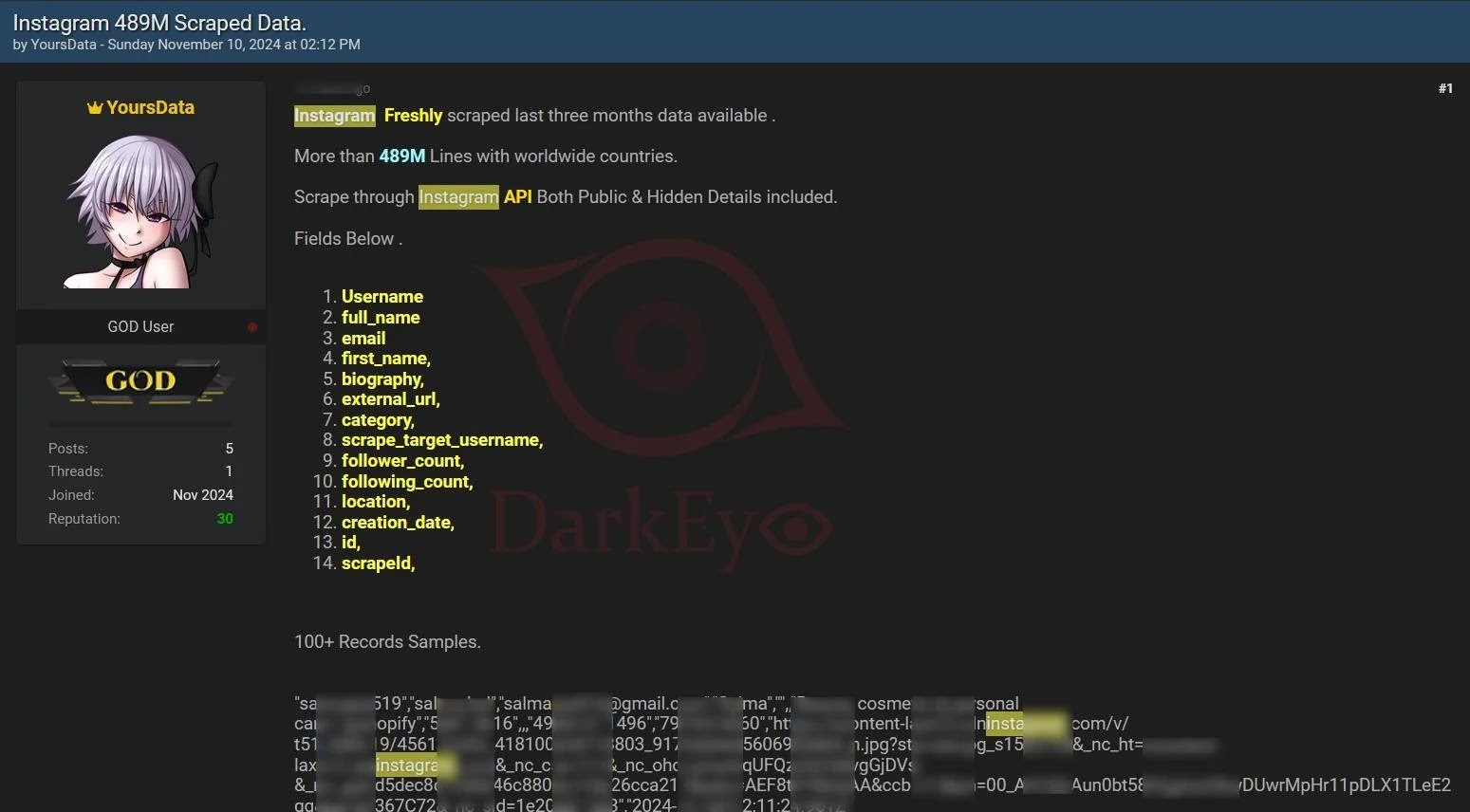
On January 7, 2026, a threat actor operating under the alias “Solonik” dropped a dataset titled “INSTAGRAM.COM 17M GLOBAL USERS — 2024 API LEAK” on BreachForums. The dump contained approximately 17.5 million records including usernames, display names, email addresses, phone numbers, and partial physical addresses—all formatted in structured JSON that strongly suggests automated API harvesting.
Within 48 hours, millions of Instagram users worldwide started receiving legitimate password reset emails they never requested. Panic spread. Headlines screamed “breach.” Meta denied everything.
Here’s what actually happened—and why the real story isn’t the breach itself.
The Timeline: From Silent Leak to Chaos
2024 (estimated): Data harvested via Instagram API exposure. The structured JSON format and field consistency indicate this wasn’t manual scraping—it was systematic extraction through a misconfigured or over-permissive endpoint.
January 7, 2026: Solonik publishes the dataset on BreachForums, offering it for free download in JSON and TXT formats.
January 8, 2026 (~4-5 AM EST): Users globally begin receiving unsolicited password reset emails from Instagram’s legitimate security@mail.instagram.com domain. Some report receiving dozens.
January 9-10, 2026: Malwarebytes issues alert via X (Twitter), warning that 17.5 million accounts were compromised. Security community erupts.
January 11, 2026: Instagram responds on X: “We fixed an issue that let an external party request password reset emails for some people. There was no breach of our systems and your Instagram accounts are secure.”
January 12, 2026: Have I Been Pwned adds the dataset, confirming 17 million rows with 6.2 million unique email addresses. Troy Hunt notes the data “appears to be unrelated to password reset requests initiated on the platform, despite coinciding in timeframe.”
What Was Actually Exposed
Let’s be precise about what’s in this dump:
- Instagram usernames and user IDs
- Display names
- Email addresses (6.2 million confirmed unique)
- International phone numbers
- Partial physical addresses and geolocation data
- Account metadata
What’s NOT in the dump: passwords, authentication tokens, or direct account access credentials.
The “So What” Question
Here’s where most coverage gets it wrong. The immediate reaction from security professionals was essentially: “It’s 2024 data. Just contact details. Hackers already have billions of these. What’s the big deal?”
That reaction is simultaneously correct and dangerously incomplete.
Yes, this is old data. The structured API responses clearly indicate 2024 harvesting. This sat dormant for roughly two years before someone decided to monetize—or more accurately, weaponize—it.
Yes, attackers already have enormous contact databases. Between LinkedIn scrapes, Facebook leaks, and countless other breaches, threat actors have compiled datasets covering a significant percentage of internet users globally.
But here’s what makes this different:
The Instagram data links usernames to real identities and physical locations. When you combine a username (public persona) with a home address (physical world), you’ve handed stalkers, swatters, and identity thieves a complete roadmap. As one security analyst noted: “This elevates the threat from ‘digital nuisance’ to ‘physical danger.’”
The real-world impact was immediate. Attackers used the exposed email addresses to trigger Instagram’s legitimate password reset mechanism at scale—not to gain access (they didn’t have passwords), but to create confusion, verify which accounts were active, and prime targets for phishing campaigns.
Meta’s Response: Technically Accurate, Structurally Evasive
Meta’s official position: “There was no breach of our systems.”
This is technically true in the narrowest sense. The data wasn’t extracted through a server compromise. It was harvested through an API—Instagram’s own interface designed for programmatic access.
But calling this “not a breach” is like saying your house wasn’t robbed because the thief used the unlocked back door instead of breaking a window. The outcome is identical: user data that should have been protected is now circulating on criminal forums.
Meta’s statement also conveniently ignores:
- Why the API allowed this level of data extraction in the first place
- Why the exposure went undetected (or unaddressed) for approximately two years
- Why Instagram needed to store physical addresses linked to user accounts
- Why the password reset mechanism could be triggered at scale by external parties
The password reset “fix” they announced addresses a symptom, not the disease.
The Pattern: Why This Keeps Happening
This incident fits a depressingly familiar template in Meta’s security history:
2017 - “The Celebrity Bug”: API vulnerability allowed hackers to scrape phone numbers and emails of high-profile accounts.
2019 - “The Chtrbox Leak”: Unprotected AWS database containing 49 million influencer records, including location data.
2021 - “The Socialarks Leak”: 214 million records exposed across Facebook, Instagram, and LinkedIn.
September 2024: Meta fined €91 million ($101 million) after Ireland’s Data Protection Commission discovered the company had stored 600 million Facebook and Instagram passwords in plaintext—some accessible to over 20,000 employees since 2012.
January 2026: Here we are again.
The recurring theme isn’t sophisticated attackers. It’s structural negligence: over-permissive APIs, excessive data collection, weak internal access controls, and years of technical debt justified as “growth.”
The Real Issue: Data Minimization Failure
The question users should be asking isn’t “Was my password strong enough?”
It’s: “Why did Instagram have my physical address at all?”
Instagram doesn’t need your home address to function. It doesn’t need long-lived access to your contact details. It doesn’t need to expose that surface area through API endpoints.
But collecting more data makes ad targeting easier, analytics richer, and third-party integrations faster. The business model incentivizes maximum data accumulation. Security becomes a downstream concern—something to address after the damage is done.
This is the structural problem that fines don’t fix. Meta paid $101 million for the plaintext password incident. That’s roughly 0.07% of their 2024 revenue. The cost of compliance is still lower than the cost of restraint.
What Actually Matters for Defense
The standard advice applies and remains important:
- Enable multi-factor authentication using an authenticator app, not SMS
- Use unique, strong passwords via a password manager
- Ignore unsolicited password reset emails—go directly to the app if concerned
- Check Have I Been Pwned to see if your email was in this dump
- Review connected apps and revoke access to anything unnecessary
- Monitor for targeted phishing that references your Instagram activity
But let’s be honest about what this does and doesn’t protect against:
Individual users cannot defend against invisible backend exposures, silent API leaks, or data they never chose to share in the first place. MFA won’t help if the platform itself is hemorrhaging your contact information through misconfigured interfaces.
The Uncomfortable Truth About Ad-Supported Platforms
Ad networks trade user data with third parties as if it were candy. The entire business model depends on detailed user profiles, behavioral tracking, and data enrichment. Every integration point, every API, every third-party partnership creates potential exposure.
The question isn’t whether these platforms will have incidents. It’s how long the data will sit on criminal forums before someone notices.
In this case: approximately two years.
Recommendations for Security Leaders
For organizations allowing Instagram for business:
- Audit which employee accounts have business profile access
- Review what personal information is linked to business accounts
- Ensure business accounts use dedicated email addresses, not personal ones
- Implement monitoring for credential stuffing attempts against corporate SSO using leaked email addresses
For policy and procurement:
- Factor platform security history into vendor risk assessments
- Require data minimization commitments in enterprise social media agreements
- Establish protocols for responding to third-party platform breaches affecting employees
For the industry:
Until companies are held accountable not just for breaches but for unnecessary data accumulation and unsafe interfaces, this pattern will continue. Silently. Predictably. At scale.
The Instagram incident isn’t remarkable because of its size—17.5 million is modest by modern breach standards. It’s remarkable because it demonstrates, once again, that the data collection practices driving these platforms create inevitable exposure.
The business model is the vulnerability.
Key Takeaways:
- Data harvested via 2024 API exposure, published January 7, 2026
- 17.5 million records total; 6.2 million unique emails confirmed by Have I Been Pwned
- No passwords exposed, but physical addresses linked to usernames create elevated risk
- Meta denies “breach” while acknowledging password reset mechanism exploit
- This is Meta’s latest in a pattern of API-related exposures dating to 2017
- Individual security measures remain important but cannot address platform-level data governance failures