The IntelBroker Unmasking: Inside the $25 Million Cybercrime Empire That Shook the Dark Web
How the arrest of Kai West revealed the scope of modern cybercrime and the resilience of underground forums
https://www.justice.gov/usao-sdny/media/1404616/dl?inline
The cybersecurity world was shaken this week when federal prosecutors in New York unveiled criminal charges against Kai West, the 25-year-old British national behind the notorious "IntelBroker" identity. The unsealing of the Department of Justice complaint marks the end of one of the most prolific cybercriminal careers in recent memory, revealing a sophisticated operation that caused over $25 million in damages across dozens of victims worldwide.







The Rise of IntelBroker: From Minor Player to Criminal Kingpin
IntelBroker's journey from obscurity to becoming one of the most feared names in cybercrime began in late 2022. Operating primarily through BreachForums, a successor to the dismantled RaidForums, West built a reputation for high-profile breaches targeting everything from Fortune 500 companies to government agencies.
What set IntelBroker apart from typical cybercriminals wasn't just the scale of the attacks, but the brazen publicity surrounding them. From approximately 2023 to 2025, West offered hacked data for sale approximately 41 times and offered to distribute hacked data for free approximately 117 times, turning data theft into a form of digital theater.
The criminal complaint reveals staggering numbers: West and his co-conspirators sought to collect at least approximately $2,000,000 by selling stolen data, while causing victim losses of at least $25,000,000. These figures represent just the documented cases—the true scope may be far larger.
IntelBroker has been arrested by French authorities. He has been in custody since February 22nd according to news reports. It has been suspected that he was compromised a few months ago but there hasn’t been a report till now.
— vxdb (@vxdb) June 25, 2025
French Media outlet LeParisien reported that the… pic.twitter.com/n0w7ub8z6h
Inside the Criminal Enterprise: The CyberN[——] Collective
West didn't operate alone. The DOJ documents reveal his leadership of an evolving criminal collective, initially known as "The Boys" before rebranding as the "CyberN[------]." This group represented a new model of cybercrime organization—part criminal gang, part social media influencer network.
The group's recruitment strategy was surprisingly open. On August 5, 2024, West authored a Forum-1 public message seeking to recruit members to join his hacking group, treating cybercrime recruitment like a startup pitch. This brazen approach reflected the increasing professionalization of the cybercrime ecosystem.
Notable Victims and Attack Methods:
- Telecommunications Provider (Victim-1): Accessed via misconfigured server, resulting in theft of marketing data and customer information
- Municipal Healthcare Provider (Victim-3): Breach exposed 56,415 individuals' health insurance data, sold to undercover FBI agents for $1,000
- Multiple ISPs and Government Contractors: Systematic targeting of infrastructure providers and defense contractors
How LE was able to connect IntelBroker to Kai West according to his criminal complaint:
— vxdb (@vxdb) June 25, 2025
- Law Enforcement did a control buy of data from IB and were able to get his Bitcoin address. He sent funds to a Coinbase account that he signed up for with his real info.
- Agents executed… pic.twitter.com/nujHPaZsoI
Technical Sophistication Meets Operational Security Failures
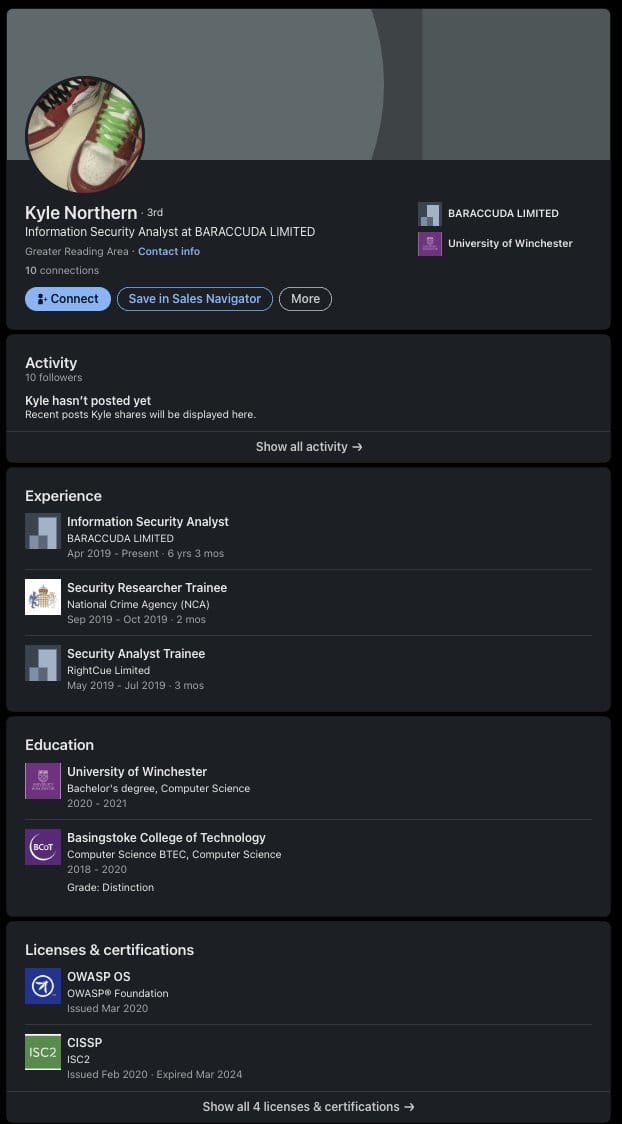
IntelBroker's technical methods were surprisingly varied, exploiting everything from misconfigured software to API vulnerabilities. The complaint details attacks ranging from simple misconfigurations to sophisticated multi-stage operations. However, despite this technical prowess, West's operational security ultimately failed him.
The Digital Forensics Trail:
The FBI's investigation revealed a complex web of digital evidence linking West to his criminal persona:
- Cryptocurrency Connections: Bitcoin wallet addresses connected to Ramp and Coinbase accounts registered under West's real identity
- Email Forensics: Personal email accounts containing university correspondence, invoices, and identification documents
- Behavioral Analysis: YouTube viewing patterns that precisely matched IntelBroker's Forum-1 posts
- Geographic Correlation: IP address overlaps between West's personal accounts and IntelBroker activities
One particularly damning piece of evidence involved West's YouTube viewing habits. On multiple occasions, West viewed YouTube videos shortly before IntelBroker posted the same videos to Forum-1, creating a digital fingerprint that helped establish his identity.
The BreachForums Ecosystem: A Criminal Marketplace in Constant Flux
IntelBroker's rise paralleled the evolution of BreachForums, which became the primary marketplace for stolen data after law enforcement dismantled its predecessor, RaidForums. From August 2024 through January 2025, IntelBroker was identified as the site's "owner", giving him unprecedented influence over the cybercrime community.
The forum's history illustrates the cat-and-mouse game between cybercriminals and law enforcement:
- March 2022: Original BreachForums launched by "Pompompurin" (Conor Fitzpatrick)
- March 2023: FBI arrests Fitzpatrick
- June 2023: BreachForums 2.0 launches under "ShinyHunters" and "Baphomet"
- May 2024: FBI seizes BreachForums again
- May 2024: Forum resurfaces within two weeks
- January 2025: IntelBroker resigns as owner
- April 2025: Forum goes offline amid rumors of infiltration

Law Enforcement Response: International Cooperation and New Strategies
The IntelBroker case represents a significant evolution in international cybercrime enforcement. French authorities arrested West in February 2025, with the U.S. now seeking his extradition. This cross-border cooperation demonstrates increasing coordination between international law enforcement agencies.
Innovative Investigative Techniques:
The FBI's investigation showcased sophisticated digital forensics and undercover operations:
- Undercover Purchases: FBI agents directly purchased stolen data from IntelBroker
- Blockchain Analysis: Tracing cryptocurrency transactions across multiple wallets and exchanges
- Social Engineering: Leveraging West's own publicity-seeking behavior against him
- International Intelligence Sharing: Coordinating with multiple countries' law enforcement agencies
Cybersecurity Community Reactions: Lessons and Concerns
The cybersecurity community's response to the IntelBroker revelations has been mixed, highlighting both satisfaction with the arrest and concern about broader implications.
Key Community Observations:
- Attribution Vindication: Many researchers who had tracked IntelBroker's activities felt vindicated by the confirmation of their analysis
- Operational Security Education: The case serves as a masterclass in how even sophisticated criminals can be undone by seemingly minor mistakes
- Ecosystem Resilience Concerns: Despite law enforcement actions, cybercrime forums continue to demonstrate remarkable resilience, with new platforms emerging within weeks of takedowns
The Broader Implications: What IntelBroker's Fall Means for Cybersecurity
The Professionalization of Cybercrime
IntelBroker's operation exemplified the increasing professionalization of cybercrime. Unlike traditional hackers motivated primarily by technical challenge or ideology, West operated more like a criminal entrepreneur, building brand recognition and customer loyalty.
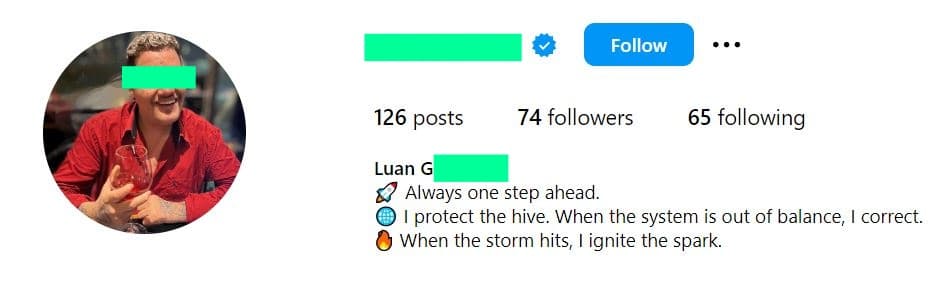
The Social Media Criminal
West's approach represented a new breed of cybercriminal—one who leveraged social media and public forums for both operational purposes and personal branding. IntelBroker maintained an Instagram account with nearly 12,000 followers, surrounding himself with symbols of wealth.
Forum Fragmentation and Evolution
The repeated takedowns of major forums like BreachForums haven't eliminated the cybercrime marketplace—they've fragmented it. Multiple forums now compete for market share, potentially making the ecosystem more resilient but also more unpredictable.
Technical Lessons: Attack Vectors and Defense Strategies
The IntelBroker case provides valuable insights into modern attack methodologies:
Common Attack Vectors Exploited:
- Misconfigured Servers: Multiple breaches involved improperly configured software with default credentials
- API Vulnerabilities: Several attacks targeted application programming interfaces
- Third-Party Contractor Compromise: Many breaches involved attacking vendors to access primary targets
- Social Engineering: Combination of technical and human elements in attack chains
Defense Implications:
- Configuration Management: The prevalence of misconfiguration-based attacks underscores the need for robust configuration management
- Third-Party Risk: Organizations must extend security considerations to their entire vendor ecosystem
- Behavioral Analytics: The behavioral patterns that ultimately led to West's identification suggest opportunities for proactive threat detection
- International Cooperation: The case demonstrates the importance of cross-border law enforcement cooperation
The Future of Cybercrime Forums
IntelBroker's arrest represents a significant victory for law enforcement, but it's unlikely to eliminate the cybercrime marketplace. Historical patterns suggest that new forums will emerge, possibly with enhanced security measures informed by the mistakes that led to West's capture.
Emerging Trends:
- Increased Operational Security: Future forum operators will likely learn from West's mistakes
- Decentralization: The marketplace may fragment further, making coordinated law enforcement action more difficult
- Enhanced Anonymity Tools: Criminals will likely adopt more sophisticated privacy protection measures
- Alternative Platforms: Migration to more secure communication channels and platforms
Conclusion: A Victory with Broader Implications
The unmasking of IntelBroker represents more than just another cybercriminal arrest—it's a window into the evolving nature of digital crime and the international efforts to combat it. Kai West's transformation from university student to criminal kingpin illustrates how the digital age has democratized both opportunity and risk.
While law enforcement's success in this case should be celebrated, the rapid resurgence of BreachForums and similar platforms demonstrates the resilience of criminal ecosystems. The cybersecurity community must prepare for a future where taking down individual actors and platforms, while important, is just one part of a broader defensive strategy.
Key Takeaways:
- Individual Actions, Massive Impact: A single individual can cause tens of millions in damages
- Digital Forensics Evolution: Modern investigations require sophisticated technical and behavioral analysis
- International Cooperation Works: Cross-border law enforcement can successfully pursue global cybercriminals
- Ecosystem Resilience: Criminal marketplaces adapt and evolve faster than many anticipated
- Prevention Remains Critical: Technical controls and configuration management remain fundamental
As we move forward, the IntelBroker case serves as both a warning about the scale of modern cybercrime and a demonstration that even the most sophisticated criminal operations can be successfully dismantled through international cooperation and advanced investigative techniques. The challenge now lies in applying these lessons to stay ahead of the next generation of cyber threats.







