The Mixpanel Breach: How a Single Smishing Attack Exposed Millions of Users Across 8,000 Corporate Customers
On November 8, 2025, analytics giant Mixpanel fell victim to a sophisticated SMS phishing attack that would ultimately expose customer data across hundreds of major organizations—from OpenAI and PornHub to SoundCloud and cryptocurrency platforms. The breach highlights critical vulnerabilities in the analytics industry, where third-party providers collect massive amounts of behavioral data about millions of users, creating high-value targets for sophisticated threat actors.

Executive Summary
What Happened: Mixpanel, a major web and mobile analytics provider with approximately 8,000 corporate customers, suffered a security breach on November 8, 2025, following a successful smishing (SMS phishing) campaign targeting its employees.
Who Was Affected: Confirmed victims include OpenAI (API users), CoinTracker, CoinLedger, SwissBorg, PornHub (Premium members), and SoundCloud (20% of users, approximately 28 million accounts). The full scope remains unclear, but with each customer potentially having millions of users, the total impact could affect hundreds of millions of people.
What Was Stolen: The type of exposed data varies by customer configuration but generally includes names, email addresses, location data, device information, behavioral analytics, and user activity patterns—precisely the kind of metadata that enables highly targeted phishing and social engineering attacks.
Who's Responsible: ShinyHunters, the notorious cybercrime group behind some of 2025's most significant breaches, has claimed responsibility and is actively extorting affected customers.
Current Status: Mixpanel claims to have contained the breach, while ShinyHunters continues extortion campaigns. Several major customers including OpenAI have terminated their relationships with Mixpanel.
Understanding Mixpanel: The Analytics Giant You've Never Heard Of
Mixpanel is one of the largest web and mobile analytics companies operating behind the scenes of thousands of apps and websites you likely use every day. Founded in 2009 and serving approximately 8,000 corporate customers, Mixpanel provides event analytics that help companies understand how users interact with their products.
How Mixpanel Works
When you use an app or website that has integrated Mixpanel, a piece of tracking code embedded in the application monitors your every action:
- Every click, tap, and swipe you make
- Every page or screen you visit
- How long you spend on each section
- What features you use most frequently
- Your device information: screen size, operating system, browser version
- Your network details: whether you're on WiFi or cellular, carrier name
- Your approximate location: derived from IP address
- Session duration and frequency: when and how often you use the app
This creates what security experts call a "digital shadow"—a detailed behavioral profile of how you interact with digital services. For legitimate businesses, this data helps improve user experience and product development. For attackers who steal it, this same data becomes ammunition for highly personalized attacks.
The Scale of Mixpanel's Data Collection
With 8,000 corporate customers and each customer potentially serving millions of users, Mixpanel's systems likely contain behavioral data on hundreds of millions to potentially billions of people worldwide. This concentration of sensitive information makes analytics providers like Mixpanel extraordinarily valuable targets for cybercriminals.
The Attack: November 8, 2025
Initial Compromise via Smishing
On November 8, 2025, threat actors launched a targeted SMS phishing (smishing) campaign against Mixpanel employees. Smishing attacks use deceptive text messages to trick recipients into revealing credentials or clicking malicious links.
Attack Methodology:
- Social Engineering: Attackers likely researched Mixpanel's organizational structure to identify high-value employee targets
- Credential Harvesting: Deceptive SMS messages convinced employees to divulge authentication credentials
- MFA Bypass: The attackers successfully bypassed multi-factor authentication—though Mixpanel has not disclosed how this was accomplished
- Lateral Movement: Once inside, attackers pivoted through Mixpanel's internal environment to access customer data repositories
Detection and Timeline
November 8, 2025: Mixpanel's security operations center detected the smishing campaign and unauthorized access
November 9, 2025: Attackers exfiltrated datasets containing customer identifiable information and analytics data
November 21-25, 2025: Mixpanel began notifying affected customers about the breach (16-day delay from detection to customer notification for some victims)
November 27, 2025: Mixpanel publicly disclosed the incident in a bare-bones blog post just before the U.S. Thanksgiving holiday
December 2025: Major customers began publicly disclosing their involvement and ShinyHunters initiated extortion campaigns
Mixpanel's Immediate Response
According to CEO Jen Taylor, Mixpanel took the following actions upon detecting the breach:
- Secured affected accounts immediately
- Revoked all active sessions and sign-ins
- Rotated compromised credentials
- Blocked threat actor IP addresses
- Reset passwords for all employees
- Implemented new security controls
- Engaged external cybersecurity partners for incident response
The Victims: A Growing List of Compromised Organizations
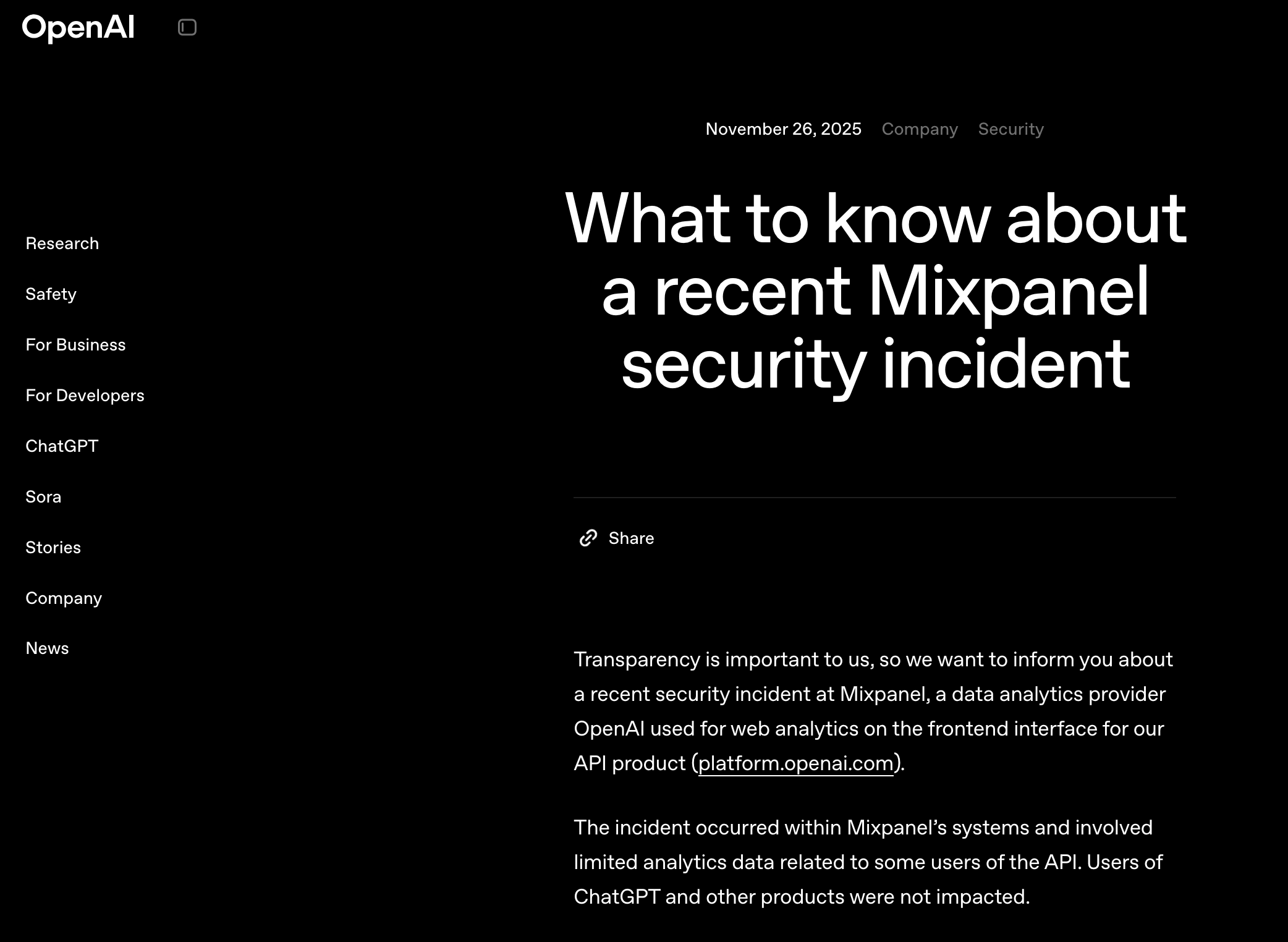
OpenAI: The First Major Disclosure
Disclosed: November 27, 2025
OpenAI became the first major customer to publicly acknowledge being affected by the Mixpanel breach. The AI company used Mixpanel to track user interactions on its API platform (platform.openai.com).
Exposed Data:
- Names provided on API accounts
- Email addresses associated with accounts
- Approximate location (city, state, country) based on IP addresses
- Operating system and browser information
- Referring websites
- Organization or User IDs associated with API accounts

Impact: API users only—ChatGPT users were not affected. The exposed metadata could enable highly convincing phishing campaigns against developers and organizations using OpenAI's API.
OpenAI's Response:
- Immediately terminated use of Mixpanel across all production services
- Launched comprehensive security review of entire vendor ecosystem
- Elevated security requirements for all partners and vendors
- Directly notified all affected users and organizations
- Stressed that no API keys, passwords, chat content, or payment details were compromised
CoinTracker: Cryptocurrency Platform Exposure
Disclosed: November 27, 2025
CoinTracker, a cryptocurrency portfolio tracker and tax platform, confirmed exposure of customer data.
Exposed Data:
- Email addresses
- Location derived from IP addresses
- Device metadata
- Limited transaction count summaries
Significance: The targeting of cryptocurrency platforms suggests ShinyHunters may have been specifically seeking wallet associations and transaction patterns for potential follow-up attacks.
CoinLedger: Additional Crypto Platform Impact
Disclosed: December 2025
CoinLedger, another cryptocurrency tax and portfolio tracking service, also confirmed being affected.
Exposed Data:
- First and last names (if set in user profiles)
- Email addresses
- Transaction-related metadata
Risk: Users who provided names for tax reporting purposes face elevated phishing risks, as attackers can craft highly personalized messages.
SwissBorg: European Cryptocurrency Platform
Disclosed: December 2025
SwissBorg, a European cryptocurrency wealth management platform, was confirmed as an affected Mixpanel customer, though specific details about the exposed data remain limited.
PornHub: The Controversial Disclosure
Disclosed: December 13, 2025
Adult entertainment platform PornHub disclosed that "select Premium users" were affected by the Mixpanel breach, though the situation is complicated by conflicting claims about the data's origin.
PornHub's Claims:
- Data came from Mixpanel's November 2025 breach
- Only affects users from before 2021, when PornHub stopped using Mixpanel
- All data is at least 4 years old
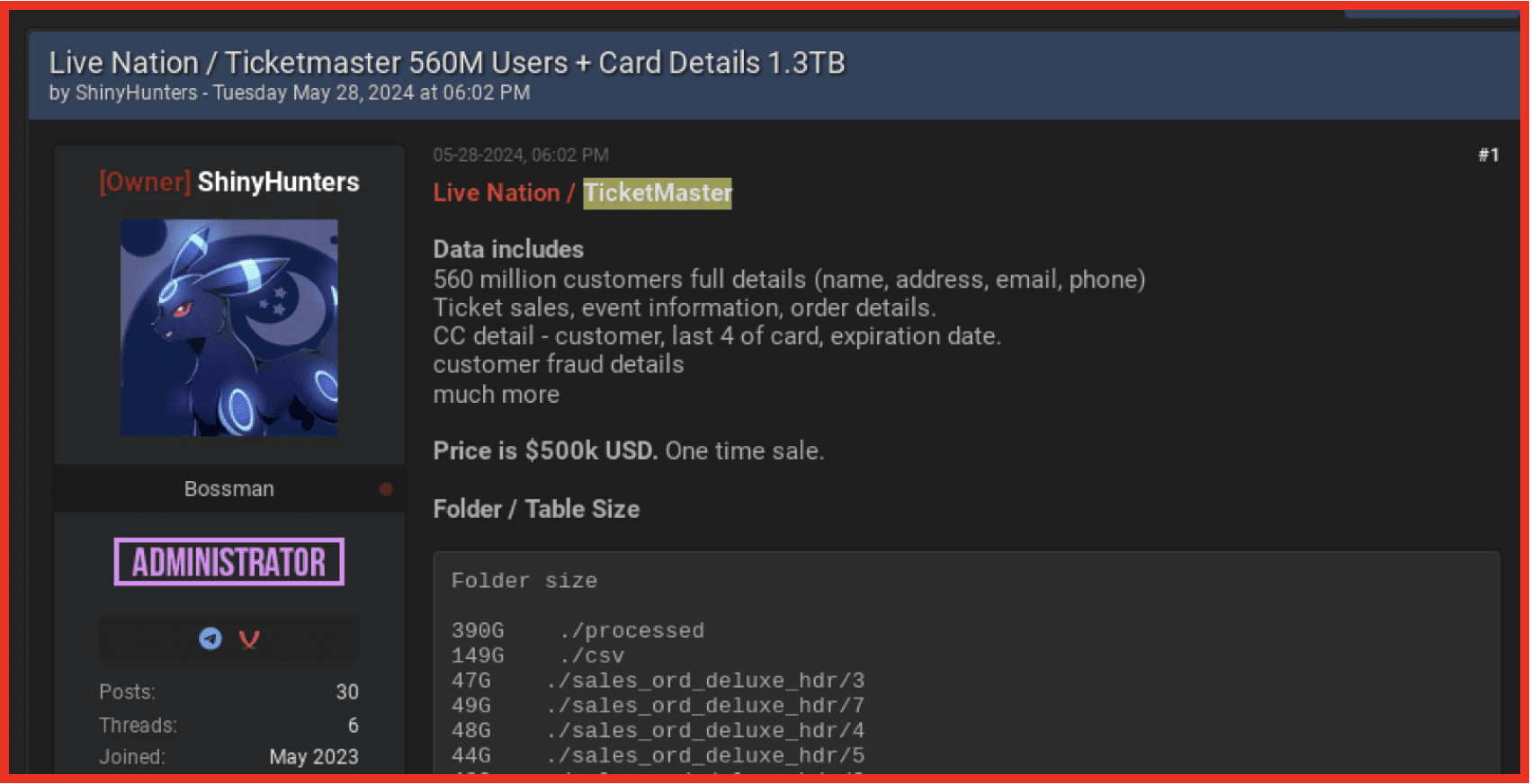
ShinyHunters' Claims:
- 94GB of data containing 201,211,943 records
- Includes detailed viewing history, search queries, downloads
- Contains records as recent as 2023 (contradicting PornHub's timeline)
- Currently extorting PornHub with threats to publish the data
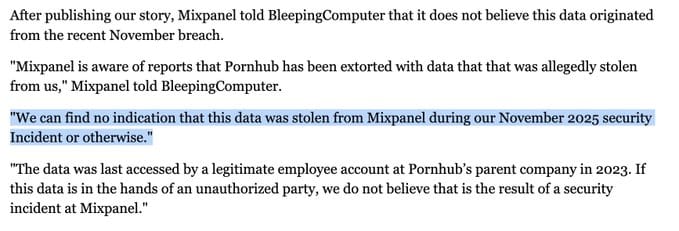
Mixpanel's Rebuttal: In a statement to BleepingComputer, Mixpanel disputed that PornHub data came from the November breach:
"We can find no indication that this data was stolen from Mixpanel during our November 2025 security incident or otherwise. The data was last accessed by a legitimate employee account at Pornhub's parent company in 2023. If this data is in the hands of an unauthorized party, we do not believe that is the result of a security incident at Mixpanel."
Exposed Data (according to samples reviewed by security researchers):
- Email addresses tied to Premium accounts
- Complete viewing history including video URLs and titles
- Search queries and keywords
- Download activity records
- Geographic location data
- Activity timestamps
- Activity types (watched, downloaded, viewed channel)
Significance: This represents one of the most sensitive data exposures of 2025, with severe implications for blackmail, extortion, and privacy violations. The dispute over the data's origin suggests either a separate breach at PornHub's parent company Aylo, or that multiple datasets from different time periods have been combined.
SoundCloud: Mass User Data Exposure
Disclosed: December 13, 2025
Music streaming platform SoundCloud confirmed a breach affecting approximately 20% of its user base—roughly 28 million accounts—following days of VPN connectivity issues reported by users.
Exposed Data:
- Email addresses
- Information already visible on public SoundCloud profiles
- No financial data or passwords compromised
Associated Attacks: Following the data breach, SoundCloud experienced:
- Multiple denial-of-service (DoS) attacks
- Two severe DoS incidents that temporarily took the website offline
- VPN access disruptions caused by security configuration changes
SoundCloud's Response:
- Activated incident response protocols
- Engaged independent cybersecurity experts
- Enhanced monitoring and threat detection systems
- Reviewed and reinforced identity and access controls
- Implemented configuration changes (which inadvertently disrupted VPN access)
Attribution: Security sources confirmed to BleepingComputer that ShinyHunters is responsible for the SoundCloud breach and is now extorting the company.
Unknown Additional Victims
Given that Mixpanel has approximately 8,000 customers and CEO Jen Taylor stated only that "all impacted customers have been contacted directly," the true scope of the breach remains unclear. Many affected organizations may not have publicly disclosed their involvement.
ShinyHunters: The Threat Actor Behind the Breach
ShinyHunters, tracked by Google Threat Intelligence as UNC6040, has claimed responsibility for the Mixpanel breach and is actively conducting extortion campaigns against affected customers. As detailed in our comprehensive analysis of ShinyHunters' evolution, this group has transformed from Pokémon-inspired database thieves in 2020 into one of the most dangerous cybercrime operations of 2025.
2025: A Year of Unprecedented Success
The Mixpanel breach is just the latest in ShinyHunters' remarkable 2025 campaign:
Salesforce Supply Chain Attacks:
- Salesloft Drift breach (August 2025): ~760 companies affected
- Gainsight breach (November 2025): 285+ Salesforce instances compromised
- Combined impact: Nearly 1,000 organizations
Other Major 2025 Breaches:
- Oracle E-Business Suite zero-day exploitation (CVE-2025-61884)
- Red Hat GitLab server: 28,000+ repositories stolen
- Discord third-party breach: User data exposed
- Multiple insurance companies including Allianz Life
- Major airlines including Qantas (5 million records)
Total 2025 Impact: ShinyHunters claims to have compromised approximately 1,500 organizations and stolen data affecting over 1 billion users. This includes the massive Google Salesforce breach affecting 2.5 billion Gmail users and dozens of other major organizations documented in our August 2025 unprecedented attack wave overview.
Extortion Tactics
ShinyHunters has begun sending extortion emails to Mixpanel customers that begin with "We are ShinyHunters" and threaten to publish stolen data unless ransom demands are paid in Bitcoin.
Extortion Strategy:
- Direct victim contact: Emails sent to compromised organizations
- Data sampling: Providing samples to prove legitimacy of stolen data
- Publication threats: Deadlines for payment before public release
- Media engagement: Confirming attacks to security researchers to increase pressure
The Scattered LAPSUS$ Hunters Collective
ShinyHunters operates as part of Scattered LAPSUS$ Hunters—a merger of three notorious cybercrime groups:
- ShinyHunters: Data theft and underground marketplace operations
- Scattered Spider: Social engineering and sophisticated targeting
- LAPSUS$: Destructive attacks and high-profile victims
This collective represents one of the most dangerous English-speaking cybercrime syndicates currently operating, with Microsoft describing them as "one of the most dangerous financially motivated threat groups." Our investigation into the Crimson Collective alliance provides deeper insight into how these groups merged to create an unprecedented cybercrime supergroup.
The Data at Risk: Why Analytics Breaches Matter
The Power of Behavioral Metadata
While many people focus on "sensitive data" like passwords or payment information, the behavioral metadata collected by analytics platforms can be equally—or more—damaging in the hands of attackers.
What Attackers Can Do With Analytics Data:
1. Hyper-Targeted Phishing: With names, email addresses, location data, and usage patterns, attackers can craft extremely convincing phishing emails that reference:
- Specific products or services the victim actually uses
- Legitimate-looking account alerts based on real usage patterns
- Geographic details that add authenticity
- Device and browser information that mimics real system messages
2. Social Engineering: Behavioral data reveals:
- When users are most active (optimal timing for attacks)
- What features they use most (context for convincing requests)
- Company affiliations and organizational structures
- Technology stack and platform preferences
3. Account Takeover Preparation: Analytics data helps attackers:
- Identify high-value targets based on usage intensity
- Understand normal behavior patterns to avoid detection
- Build profiles for credential stuffing attacks
- Map relationships between users and organizations
4. Corporate Espionage: For business customers, leaked analytics reveal:
- Product development priorities and timelines
- User adoption rates and engagement metrics
- Feature usage that indicates business strategies
- Customer retention and churn patterns
The "Shadow Profile" Problem
Every time you interact with an app or website using Mixpanel (or similar analytics), you're creating what privacy advocates call a "shadow profile"—a detailed record of your behavior that you never explicitly consented to and may not even know exists.
These profiles:
- Persist long after you stop using a service
- Can be cross-referenced with other data breaches
- May reveal sensitive information through behavioral patterns
- Create permanent attack surfaces even if you practice good security hygiene
Technical Analysis: How the Breach Unfolded
The Attack Chain
Phase 1: Initial Access (November 8)
- Smishing campaign targets Mixpanel employees
- Social engineering convinces victims to provide credentials
- MFA bypass achieved (method undisclosed by Mixpanel)










