The Perfect Insider Threat: How a State-Sponsored Researcher Nearly Smuggled 90GB of Cancer Research to China
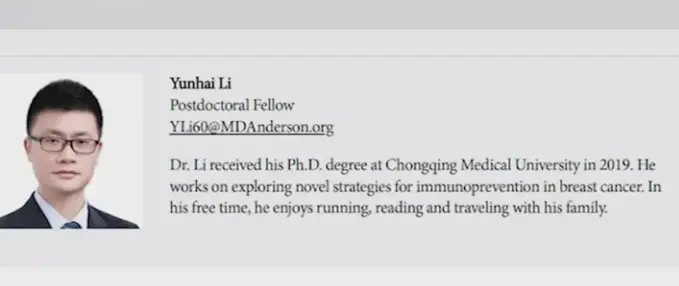
The arrest of Dr. Yunhai Li at Houston's Bush Airport on July 9, 2025, as he attempted to board a flight to China with 90 gigabytes of stolen research data, represents a textbook case of insider threat that should serve as a wake-up call for research institutions nationwide. The 35-year-old Chinese scientist's systematic theft of federally-funded breast cancer vaccine research from the University of Texas MD Anderson Cancer Center demonstrates how sophisticated actors can exploit the open nature of academic research while hiding behind legitimate scholarly credentials.

The Anatomy of an Insider Threat
Li's case illustrates the most dangerous type of insider threat—one that combines legitimate access, advanced technical knowledge, and state-sponsored motivation. Since joining MD Anderson in 2022 on a U.S. State Department research scholar visa, Li had worked on cutting-edge breast cancer vaccine research funded by the National Institutes of Health and the Department of Defense. His position gave him authorized access to some of America's most sensitive medical research, making him virtually invisible to traditional security measures.
The warning signs were there, but hidden in plain sight:
- Undisclosed Foreign Affiliations: While working at MD Anderson, Li maintained his employment at The First Affiliated Hospital of Chongqing Medical University, receiving a "reduced salary" from the Chinese institution through 2023
- Foreign Government Funding: Li received grant funding from the National Natural Science Foundation of China while conducting U.S. government-funded research
- Deceptive Behavior: When confronted by MD Anderson about uploading sensitive data to his personal Google Drive, Li claimed to have deleted the files—while secretly maintaining copies on Baidu, a Chinese cloud service
- Systematic Data Theft: Li admitted to downloading approximately 90GB of research data when the breast cancer vaccine project was about 70% complete
The Cover-Up and Near Escape
The sophistication of Li's operation becomes clear when examining his cover-up tactics. After MD Anderson discovered he had uploaded sensitive data to his personal Google Drive, institutional leaders confronted him about the breach. Li appeared to comply, demonstrating the deletion of files from his Google account. However, investigators later discovered he had already transferred the entire dataset to Baidu's Chinese servers—a fact that only came to light during his attempted departure.

Li resigned from MD Anderson on July 1 and attempted to leave the country just over a week later. U.S. Customs and Border Protection, working with Homeland Security Investigations, intercepted him at the airport carrying devices and files containing the stolen research. The timing suggests a carefully planned exit strategy designed to minimize the window for discovery and investigation.
The Justification Mindset
Perhaps most revealing is Li's stated justification for the theft. In a sworn statement to investigators, Li claimed the research was "going to waste" and that he intended to "continue his research" in China. He further stated, "I believe I have the right to possess and retain this data" because it was "a product of my efforts over the last three years."
This rationalization reflects a common insider threat mindset—the belief that personal contribution justifies ownership of institutional or national assets. Such thinking ignores the fundamental reality that federally-funded research belongs to the American taxpayers who funded it, not to individual researchers regardless of their contributions.
The Broader Intelligence Context
Li's case cannot be viewed in isolation. It represents part of a broader Chinese strategy to acquire American research and development capabilities through seemingly legitimate academic exchanges. The fact that Li maintained employment with a Chinese institution while working on U.S. defense-funded research suggests a level of coordination that goes beyond individual initiative.
Key indicators of state-sponsored activity include:
- Systematic Targeting: Focus on research funded by defense and health agencies with clear national security implications
- Institutional Coordination: Maintaining employment at Chinese state-affiliated institutions while accessing U.S. research
- Technology Transfer Infrastructure: Using Chinese cloud services (Baidu) for data storage and transfer
- Long-term Positioning: Working for years to gain access and trust before executing the theft

Research Security Failures
The Li case exposes several critical failures in research security protocols:
1. Inadequate Background Screening
Despite holding positions requiring access to sensitive, federally-funded research, Li's foreign affiliations and funding sources went undetected or unreported for years. Standard conflict-of-interest disclosure forms appear to have been insufficient to capture the full scope of his foreign entanglements.
2. Insufficient Data Loss Prevention
The fact that Li could download 90GB of sensitive research data and upload it to external cloud services suggests inadequate technical controls over data access and transfer. Modern data loss prevention (DLP) systems should flag such large-scale data movements.
3. Delayed Detection
The theft was only discovered when Li attempted to leave the country, not through proactive monitoring of data access or transfer activities. This suggests a reactive rather than preventive security posture.
4. Limited Coordination
While the case ultimately involved federal agencies, the initial response appears to have been handled at the institutional level, potentially limiting the scope and speed of the investigation.

Legal Consequences and Deterrence
Li faces felony charges for theft of trade secrets, carrying penalties of two to ten years in prison and fines up to $10,000, plus a misdemeanor charge for tampering with government records. However, legal experts suggest these state charges may serve as "placeholders" while federal prosecutors prepare more serious charges related to espionage and theft of federal funds.
The relatively modest penalties highlight a broader challenge in deterring insider threats. For state-sponsored actors, the risk-reward calculation may heavily favor attempting such theft, especially given the potential intelligence value of advanced medical research.
Immediate Lessons for Research Institutions
The Li case provides several actionable lessons for research institutions handling sensitive or federally-funded research:
Enhanced Vetting Procedures
- Implement comprehensive background checks that include verification of all foreign affiliations and funding sources
- Require annual re-certification of conflict-of-interest disclosures
- Establish clear policies regarding simultaneous employment at foreign institutions
Technical Controls
- Deploy advanced data loss prevention systems that monitor large-scale data access and transfer
- Implement network segmentation to limit access to sensitive research data
- Require approval for uploads to external cloud services
- Monitor for unusual data access patterns or large downloads

Human Intelligence
- Train supervisors to recognize behavioral indicators of potential insider threats
- Establish clear protocols for reporting suspicious activities
- Create anonymous reporting mechanisms for colleagues to express concerns
Exit Procedures
- Implement comprehensive exit interviews and data return procedures
- Monitor network activity for unusual patterns preceding resignations
- Coordinate with federal authorities when foreign nationals resign from sensitive positions
The Bigger Picture: Academic Espionage
The Li case represents just one example of what appears to be a systematic effort to exploit America's open academic environment for intelligence gathering. The case has intensified debate over Chinese students and researchers in U.S. universities, with some officials calling for more aggressive vetting and visa revocation policies.
This tension reflects a fundamental challenge: maintaining the open, collaborative nature of academic research while protecting sensitive information and intellectual property. The solution likely requires a more nuanced approach that distinguishes between legitimate academic collaboration and intelligence-gathering operations disguised as research.

Moving Forward: Balancing Openness and Security
The challenge for research institutions is maintaining the benefits of international collaboration while implementing security measures adequate to the current threat environment. This requires:
Risk-Based Approaches: Not all research requires the same level of security. Institutions need frameworks for classifying research based on sensitivity and implementing proportional security measures.
Enhanced Partnership: Closer cooperation between research institutions, federal agencies, and intelligence services to identify and mitigate threats while preserving academic freedom.
Cultural Change: Moving from a purely trust-based academic culture to one that incorporates "trust but verify" principles, especially for sensitive research areas.
Technology Investment: Implementing modern cybersecurity and data protection technologies specifically designed for research environments.

The Stakes Are High
The Li case reminds us that the competition for technological and scientific advantage is increasingly conducted through economic espionage and insider threats. America's research institutions, particularly those handling federally-funded projects, are prime targets for foreign intelligence services seeking to acquire cutting-edge capabilities without the time and expense of independent development.
As Harris County District Attorney Sean Teare noted, "That intellectual property stays with us, so we can save lives." The theft of medical research doesn't just represent economic loss—it potentially delays breakthrough treatments that could benefit patients worldwide while simultaneously advancing the capabilities of strategic competitors.
The investigation into Li's activities continues, with prosecutors indicating that additional charges may be forthcoming and that they are exploring whether others were involved in the conspiracy. As this case develops, it serves as a crucial reminder that protecting America's research infrastructure requires constant vigilance, robust security measures, and a clear understanding that not all collaboration is benign.
The price of maintaining our technological edge—and potentially saving lives through medical breakthroughs—demands nothing less than treating our research institutions as the critical national assets they truly are.
Dr. Yunhai Li remains free on $5,100 bail after surrendering his passport. His case is ongoing in Harris County, Texas, with federal charges potentially forthcoming. This case highlights the ongoing challenges research institutions face in balancing openness with security in an era of increasing technological competition.













