The Publication That Reports on Breaches Just Got Breached
WIRED Magazine's 2.3 Million Subscriber Records Leaked After Month-Long Vulnerability Disclosure Failure
December 30, 2025 - Let's talk about irony. The magazine that's made a career covering data breaches, investigating security failures, and holding companies accountable for protecting user data just exposed 2.3 million of its own subscribers. And there's a worse part: 40 million more records are coming.
This isn't just a breach. It's a masterclass in how not to handle vulnerability disclosure, wrapped in organizational silence, and delivered with a Christmas bow by a frustrated threat actor who spent an entire month trying to warn them.
The Timeline: A Month of Silence
On November 22, 2025, a threat actor using the alias "Lovely" reached out to DataBreaches.net's Dissent Doe, presenting themselves as a security researcher who had discovered serious vulnerabilities in Condé Nast's systems. They weren't asking for money. They wanted to report six security flaws that could expose account profiles and allow attackers to change user passwords.
The vulnerabilities were fundamental: Insecure Direct Object References (IDOR) combined with broken access controls. Translation? Anyone could iterate through user IDs like trying locker combinations in sequence, pulling profile data without any authentication checks. It's Security 101 stuff, and Condé Nast had failed at it spectacularly.
Lovely tried every avenue:
- Direct emails to Condé Nast security teams
- Contact attempts through WIRED reporters
- Requests for help from security bloggers
The response? Crickets.
Condé Nast didn't even have a security.txt file—a basic mechanism recommended by RFC 9116 for receiving vulnerability reports. No clear disclosure process. No monitored security email. Just organizational silence.
After a month of attempted responsible disclosure, Lovely gave up. On December 20, 2025, they posted the WIRED database to the newly launched Breach Stars hacking forum, calling it a "Christmas Lump of Coal" and promising that 40 million more records from across the Condé Nast empire would follow.
What Got Leaked
The leaked WIRED database contains 2,366,576 total records with 2,366,574 unique email addresses. Hudson Rock researchers verified the data's authenticity by cross-referencing it with infostealer malware logs from RedLine and Raccoon infections, finding high-confidence overlap between compromised users and the leaked database.
Here's what's exposed:
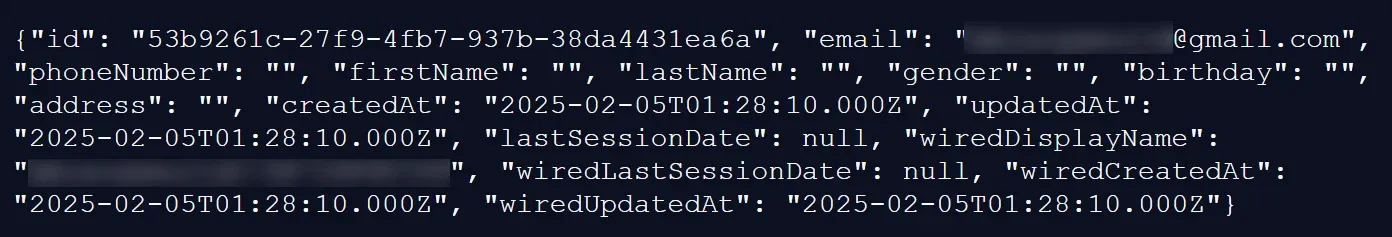
Email Addresses: 2,366,574 unique addresses (2,366,576 total records)
Full Names: 284,196 records (12.01% of total)
Home Addresses: 194,361 physical addresses (8.21% of total)
Phone Numbers: 32,438 records (1.37% of total)
Birthdays: 67,223 records (2.84% of total)
Complete Profiles: 1,529 records (0.06%) with full name, birthday, phone, address, and gender
Additional Data: User IDs, display names, account creation dates (1996-2022), update timestamps, last session data
The most recent entries are dated September 9, 2025, indicating this was pulled from a live, actively used database.
Notably absent: passwords and payment card information. But make no mistake—what's here is more than enough for targeted attacks.
The Technical Failure
The vulnerabilities exploited were textbook examples of broken access controls:
IDOR (Insecure Direct Object Reference): Attackers could scrape user profiles by simply iterating through user ID parameters. Think of it like this: if user ID 12345 works, what about 12346? And 12347? The system had no checks to verify whether the authenticated user should have access to each requested profile.
Broken Access Controls: Critical account management endpoints lacked proper authorization checks. According to reports, attackers could view and potentially modify email addresses and passwords across Condé Nast's centralized identity system without proper authentication.
This wasn't sophisticated. This was fundamentally broken architecture—the kind of vulnerability that should have been caught in basic security testing.
The Bigger Picture: 40 Million Records at Risk
WIRED is just the beginning. Lovely claims access to a centralized Condé Nast account system covering over 40 million users across major brands:
- The New Yorker: 6.8 million accounts
- SELF: 2 million+ accounts
- GQ, Vogue, Vanity Fair: Millions more
- "NIL" (unidentified): 9.5 million accounts
Condé Nast operates a shared identity and subscription management platform across its publications. One vulnerability in this centralized system potentially compromised every brand under the umbrella.
The threat actor has promised to release these additional datasets "over the next few weeks." If they follow through, we're looking at one of the largest media industry breaches in history.
Condé Nast's Deafening Silence
As of December 30, 2025—ten days after the initial leak—Condé Nast has:
- Not issued any public statement
- Not confirmed or denied the breach
- Not warned affected users
- Not forced password resets
- Not responded to media inquiries from BleepingComputer, SecurityWeek, or other outlets
The data is now indexed on Have I Been Pwned. Users are finding out they've been compromised from security blogs and breach notification services, not from the company entrusted with their information.
This silence isn't prudent legal caution. It's reputational damage compounding daily.
The Stunning Irony
WIRED has published countless articles about corporate security failures:
- Coverage of Equifax, Target, and Yahoo breaches
- Interviews with CISOs about "best practices"
- Investigative pieces on vulnerability disclosure failures
- Analysis of how companies fail to protect user data
And when a security researcher spent a month trying to warn them about their own vulnerabilities? Nobody answered.
The publication that holds other companies accountable for security failures couldn't secure its own systems. The magazine that reports on breach after breach had no process for receiving vulnerability reports. The outlet that publishes think pieces about responsible disclosure failed at responsible disclosure response.
Part of a Disturbing Pattern
WIRED isn't alone. 2025 has been brutal for media organizations:
In September, BBC cyber correspondent Joe Tidy was directly approached by the Medusa ransomware gang, offered 25% of ransom payments (potentially tens of millions) for inside access. When recruitment failed, the criminals attempted MFA bombing attacks against his account. The BBC—which reports on ransomware attacks—became a ransomware target.
The Washington Post suffered a breach through Oracle E-Business Suite vulnerabilities, exposing subscriber data. Another media giant reporting on others' security failures while struggling with their own.
Nikkei, the Japanese media conglomerate, had 17,368 Slack credentials compromised through infostealer malware in August—their third major breach in six years.
The pattern is clear: Media organizations built on investigating others' failures are systematically failing at basic security hygiene. And like WIRED, many are responding with silence rather than transparency.
What Went Wrong: A Post-Mortem
This breach represents multiple cascading failures:
1. No Vulnerability Disclosure Process
No security.txt file. No monitored security email. No bug bounty program. For a multi-billion dollar media conglomerate handling millions of user accounts, this is inexcusable.
2. Fundamental Security Architecture Failures
IDOR vulnerabilities combined with broken access controls suggest that security wasn't built into the system from the ground up. These aren't zero-day exploits; they're Security 101 failures.
3. Shared Infrastructure Without Proper Isolation
A centralized identity platform across multiple brands meant one vulnerability could compromise everything. There's no evidence of proper segmentation or defense in depth.
4. Organizational Paralysis
When vulnerability reports came in, they disappeared into a bureaucratic black hole. Even after WIRED's security team eventually engaged (only after third-party intervention), the organization failed to act with appropriate urgency.
5. Communication Breakdown
Ten days post-leak, affected users still haven't been notified. This violates the basic principle of incident response: communicate early, communicate often, communicate honestly.
Real-World Impacts
The exposed data creates serious risks:
Targeted Doxing: 194,361 home addresses are now publicly available, correlating digital identities with physical locations. This enables harassment, intimidation, and worse.
Swatting Potential: The combination of names, addresses, and known brand affiliations could be weaponized for dangerous swatting attacks.
Spear Phishing: Attackers can now craft highly targeted phishing campaigns using legitimate subscriber information and brand-specific context. "Dear WIRED subscriber, we've detected unusual activity on your account..." sounds a lot more convincing when the attacker actually has your subscription details.
Credential Stuffing: Even without passwords, email addresses enable testing across other platforms where users might have reused credentials.
Follow-On Attacks: If the 40 million promised records materialize, the risk multiplies across Vogue, The New Yorker, Vanity Fair, and every other Condé Nast property.
The Vulnerability Disclosure Dilemma
This breach highlights a fundamental problem in vulnerability disclosure: What happens when companies don't respond?
Lovely tried to do the right thing:
- Discovered vulnerabilities
- Attempted responsible disclosure
- Provided proof to third parties
- Waited for a response
- Waited some more
- Tried alternative contact methods
- Still got silence
At what point does "responsible disclosure" become "enabling harm through inaction"? If Condé Nast had engaged immediately, this could have been a quiet remediation story. Instead, it's a public breach affecting millions.
The security community needs better mechanisms for escalation when companies ignore vulnerability reports. Lovely's approach—downloading data and threatening to leak it—crossed ethical lines. But Condé Nast's month-long silence created the conditions that led here.
Lessons for Organizations
If you're responsible for user data, here's what Condé Nast's failure should teach you:
Deploy Basic Disclosure Infrastructure
Create a security.txt file at /.well-known/security.txt. Set up a monitored security@ email. Define clear SLAs: acknowledge within 24 hours, triage within 72 hours, provide remediation timeline within 7 days.
Implement Proper Access Controls
Every API endpoint needs authorization checks. Never rely on obscurity of IDs. Implement object-level authorization where every request validates that the authenticated user has permission to access the specific resource.
Test Your Disclosure Process
Can a security researcher actually reach someone who can act? Or does it disappear into a black hole? Test this regularly.
Prepare Incident Response
Have legal and communications aligned in advance. When (not if) a breach occurs, the first hour matters. Condé Nast's ten-day silence is organizational malpractice.
Segment Your Infrastructure
Don't put all your brands on one centralized platform without proper isolation. Defense in depth means one vulnerability shouldn't compromise everything.
What Should Users Do?
If you've ever subscribed to WIRED or any Condé Nast publication:
- Check Have I Been Pwned: Search your email at haveibeenpwned.com to see if you're in the breach
- Change Passwords: If you used the same password across multiple sites, change it everywhere immediately
- Enable 2FA: Use hardware security keys or authenticator apps, not SMS
- Watch for Phishing: Expect highly targeted spear phishing attempts using your leaked information
- Monitor Financial Accounts: While payment data wasn't exposed, the personal information leaked enables identity theft attempts
- Consider Credit Monitoring: The combination of name and address exposure could enable other forms of fraud
The Bottom Line
WIRED got breached. The magazine that covers data breaches got breached. A publication that has built credibility by holding others accountable for security failures couldn't secure its own subscriber database or respond to vulnerability reports.
The technical vulnerabilities were basic. The disclosure process was nonexistent. The organizational response was silence. And 2.3 million subscribers found out they'd been compromised from security blogs instead of the company they trusted with their information.
When the institution that reports on security failures becomes the security failure, it's not just ironic—it's a wake-up call for every organization handling user data.
Condé Nast still hasn't issued a statement. The 40 million additional records are still coming. And somewhere, a frustrated security researcher who tried to do the right thing is watching a company that should have known better fail every single test of responsible data stewardship.
The irony writes itself. But the real story isn't the irony—it's the systematic failure of basic security practices, organizational accountability, and user protection that this breach represents.
Related Reading from Breached.Company
The WIRED breach is part of a disturbing pattern of media organizations suffering security failures in 2025:
BBC Reporter Targeted by Medusa Ransomware Gang for Insider Recruitment - In September 2025, BBC cyber correspondent Joe Tidy was directly approached by the Medusa ransomware gang offering 25% of ransom payments (potentially tens of millions) for inside access to BBC systems. The criminals attempted MFA bombing attacks when recruitment failed. This case demonstrates how ransomware operations are systematically recruiting media insiders.
Washington Post Becomes Latest Victim in Massive Oracle E-Business Suite Breach Campaign - The Washington Post suffered a data breach through vulnerabilities in Oracle's E-Business Suite, exposing subscriber and operational data. Like WIRED, the Post built its reputation covering security failures at other organizations before becoming a victim themselves.
Nikkei Suffers Slack Breach Through Infostealer Malware: 17,000 Users Exposed - Major Japanese media company Nikkei had 17,368 Slack credentials compromised through infostealer malware in August 2025, marking their third significant breach in six years. The incident exposed the vulnerability of collaboration platforms in media environments.
These incidents reveal a common thread: media organizations reporting on cybersecurity are themselves struggling with basic security hygiene, vulnerability disclosure processes, and incident response. The institutions trusted to hold others accountable for data protection failures are failing to protect their own subscribers' information.
For more breach analysis and CISO intelligence:
Update Status: This is a developing story. Condé Nast has not responded to multiple media inquiries. The data remains publicly available on breach forums and has been indexed by Have I Been Pwned.
Disclosure: This analysis is based on publicly available information from security researchers, breach forums, and technical analysis by Hudson Rock, BleepingComputer, SecurityWeek, and other reputable sources. The author operates CISO Marketplace and has no business relationship with Condé Nast or WIRED.





