The Ransomware Playbook Problem
How Cl0p and ShinyHunters Built Repeatable Business Models That Are Destroying Enterprise Security
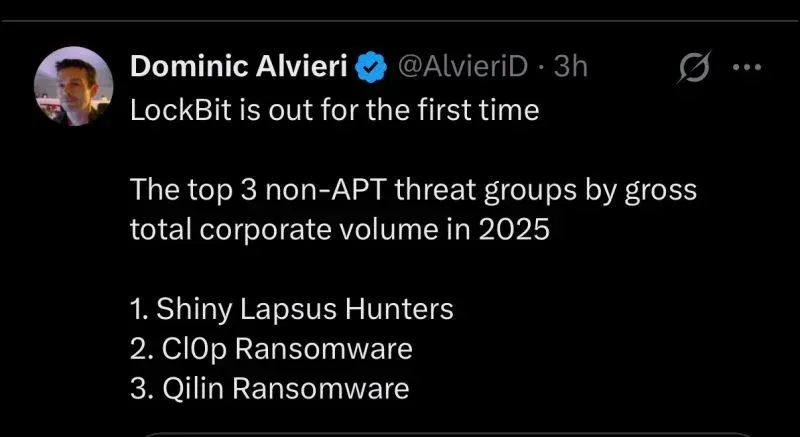
For the first time since its emergence in 2019, LockBit has been knocked out of the top three most impactful threat groups—a seismic shift following Operation Cronos and sustained law enforcement pressure that fractured the ransomware landscape into 85+ distinct operations. The new leaders? Two groups with methodical, repeatable exploitation frameworks that should terrify every CISO: Shiny Lapsus$ Hunters (the collaborative entity encompassing ShinyHunters, Scattered Spider, and Lapsus$ alumni), and Cl0p (TA505).
Both achieved their rankings not through technical sophistication alone, but through business model innovation—and 2025 wasn't their first successful campaign, it was their most successful year doing what they've refined for over half a decade.
Key Findings
- ShinyHunters' Salesforce campaign compromised nearly 1,000 organizations through OAuth token abuse of third-party integrations—applying lessons learned from their 2024 Snowflake breaches
- Cl0p's Cleo exploitation marks their sixth major file transfer appliance campaign since 2019, affecting 200+ companies with the same architectural vulnerability pattern
- Qilin claimed the #3 spot with 700+ attacks in 2025, capitalizing on the LockBit vacuum through aggressive affiliate recruitment and MSP compromises
- LockBit's fall from dominance dropped from 34% market share in 2023 to approximately 8% in 2025 following Operation Cronos
ShinyHunters: The Third-Party Integration Hunters
From Snowflake to Salesforce: Evolution of the Playbook
In 2024, ShinyHunters proved their thesis with the Snowflake campaign—compromising at least 165 organizations including Ticketmaster (560 million records), AT&T, Santander, and Neiman Marcus. The attack vector was elegant in its simplicity: credentials stolen via infostealer malware, accounts lacking MFA, and data sitting unencrypted in cloud warehouses. AT&T reportedly paid $370,000 attempting to have their data deleted.
In 2025, they pivoted to Salesforce—but they didn't attack Salesforce directly. They went after the third-party integrations that unlocked the keys to the kingdom.
For a comprehensive look at ShinyHunters' transformation from Pokémon-inspired hackers to global threat actors, see our in-depth profile: ShinyHunters: The Evolution of a Cybercrime Empire.
The 2025 Salesforce Campaign
Starting in March 2025, attackers compromised a Salesloft GitHub account and stole OAuth tokens from Salesloft Drift's integration with Salesforce. The blast radius was devastating—Google's Threat Intelligence Group confirmed over 200 potentially affected Salesforce instances, with ShinyHunters claiming nearly 1,000 organizations were compromised across both the Salesloft and subsequent Gainsight waves.
Victims included household names: Google, Adidas, Chanel, Louis Vuitton, Dior, Tiffany & Co., Cisco, Pandora, Qantas Airways, Air France-KLM, Allianz Life, Toyota, FedEx, Disney/Hulu, and UPS. Over 2.55 million records were exposed from Google's Salesforce instance alone.
Related Coverage:
- The Gmail Security Crisis: 2.5 Billion Users at Risk After ShinyHunters Breach
- Major Supply Chain Attack: Palo Alto Networks and Zscaler Hit by Salesloft Drift Breach
- Salesforce-Gainsight Breach: ShinyHunters Strike Again with Third-Party Attack Affecting 200+ Companies
- Qantas Data Breach: 5 Million Customer Records Leaked
The Attack Formula
The pattern is predictable and repeatable:
- Target third-party integration providers (Salesloft Drift, Gainsight) rather than the primary platform
- Compromise OAuth tokens through GitHub repository access or social engineering
- Target accounts without MFA—still the most common enabler
- Mask activity through privacy tools (Mullvad VPN, Tor services)
- Use legitimate API access to export massive volumes of CRM data
- Extort victims with pay-or-leak demands, sometimes months after exfiltration
The FBI issued a FLASH advisory confirming two distinct campaigns (UNC6040 and UNC6395) both leveraging compromised OAuth tokens. Voice phishing (vishing) and helpdesk social engineering were the primary initial access methods—convincing employees to authorize malicious "Connected Apps" or share credentials. This mirrors the methodology of Scattered Spider, reinforcing the collaborative nature of these groups.
The Business Model Innovation
What makes ShinyHunters particularly dangerous is their evolution into what security researchers describe as a "decentralized, extortion-as-a-service collective." When French authorities arrested a BreachForums administrator linked to ShinyHunters in June 2025, the Salesforce campaign continued unabated. This resilience suggests a distributed operational model where affiliated actors—potentially including Scattered Spider operatives and former Lapsus$ members—conduct attacks under the ShinyHunters brand.
For more on this alliance, see: The Crimson Collective: Inside the Alliance That Created Cybercrime's Most Dangerous Supergroup.
As one individual claiming to be "Shiny" told The Register: "The data from Salesloft Drift breached has enabled entry points into so many systems. Very lucrative systems. I do not like Salesforce at all, would be nice if they stopped acting all high and mighty and just pay to fix this mess."
Cl0p: The Edge Device Specialists
Six Years of the Same Exploit Pattern
Cl0p has extorted over $500 million in ransom payments since emerging in 2019. Their signature? Finding zero-day vulnerabilities in edge file transfer appliances—systems that sit at the network boundary, housing sensitive data that organizations routinely transmit, often stored unencrypted.
For a deep dive into Cl0p's operations, tactics, and complete history, see our comprehensive profile: Clop Ransomware: Inside One of the World's Most Dangerous Cybercrime Operations.
The hit list reads like a catalog of architectural failures:
- 2020-2021: Accellion FTA — Zero-day exploits installed the DEWMODE web shell on internet-facing servers. Victims included Shell, Stanford University, Kroger, and Morgan Stanley.
- January 2023: Fortra GoAnywhere MFT — CVE-2023-0669 exploited over 10 days, impacting 130+ organizations including Rubrik and Community Health Systems.
- May 2023: Progress MOVEit Transfer — CVE-2023-34362 deployed over Memorial Day weekend. At least 975 organizations affected, including the BBC, Shell, and the US Department of Energy. Estimated impact: 58+ million individuals, $9.7 billion in potential costs.
- December 2024-2025: Cleo Software — CVE-2024-50623/55956 exploited in Cleo Harmony, VLTrader, and LexiCom. Over 200 victims documented, attack ongoing as of publication. For more context on this attack pattern, see: Svenska Kraftnät Breach: Everest Ransomware Strikes Sweden's Critical Power Infrastructure.
- September-October 2025: Oracle E-Business Suite — CVE-2025-61882 exploited as a zero-day for at least two months before patches. 29 named victims including Harvard University, The Washington Post, American Airlines, Logitech, and Cox Enterprises.
Related Coverage on the Oracle Campaign:
- Oracle E-Business Suite Zero-Day Exploitation: Inside Cl0p's Latest Mass Data Extortion Campaign
- The Perfect Supply Chain Storm: How Cl0p's Oracle Rampage Exposes the Hidden Vulnerabilities in Enterprise Software
- American Airlines Subsidiary Hit by Clop Ransomware in Oracle Zero-Day Attack
- Washington Post Becomes Latest Victim in Massive Oracle E-Business Suite Breach Campaign
- When a Phone Call Costs a Billion Dollars: Harvard's Vishing Attack and the Ivy League Breach Epidemic
- University of Phoenix and Baker University Join Growing List of Oracle EBS Breach Victims
The Formula
Cl0p's playbook is "dead simple but effective":
- Find internet-facing edge device used for file transfers
- Confirm data sits unencrypted on the appliance
- Deploy zero-day exploit (often SQL injection or arbitrary file upload)
- Install web shell for persistence and data exfiltration
- Exfiltrate at scale—speed is critical before patches deploy
- Monetize through extortion—often without deploying ransomware encryption
Kroll's analysis revealed that Cl0p likely had the MOVEit exploit ready before they executed the GoAnywhere campaign—they chose to attack sequentially rather than in parallel. Evidence suggests testing against MOVEit Transfer began as early as July 2021, nearly two years before the mass exploitation event.
The Architectural Failure We Keep Ignoring
This is exactly like Fortra, MOVEit, Accellion, and now Cleo. The same architectural anti-pattern enables every single campaign: sensitive data sitting unencrypted on internet-facing edge devices, with no monitoring for outbound traffic anomalies.
As an industry, how are we not seeing this pattern? Cl0p isn't inventing new attack techniques—they're exploiting the same systemic weakness year after year. The only thing changing is the vendor name.
Check Point Research confirms that in Q1 2025, Cl0p surpassed LockBit as the most prolific ransomware group based on publicly disclosed breaches. Their recent campaigns have increasingly adopted "smash-and-grab" data exfiltration without encryption—recognizing that the threat of data exposure is often more effective than system disruption.
Qilin: The New Volume Leader
Taking the third position, Qilin has emerged as the most active ransomware operation in 2025. The Russia-linked group first appeared in 2022 but gained traction rapidly—from 45 claims in 2023 to 179 in 2024 to over 700 attacks in 2025 alone. In October 2025, they claimed 29% of all ransomware attacks according to NCC Group data.
Qilin's rise directly correlates with LockBit's decline. When RansomHub ceased operations in April 2025, affiliates migrated to Qilin en masse. The group offers 80-85% payouts to affiliates—among the most generous in the ecosystem—and has continuously updated capabilities throughout 2025: spam campaigns, DDoS attacks, automated network propagation, and even "in-house journalists" to pressure victims during negotiations.
Their South Korean campaign in September 2025 exemplified their supply chain focus. By compromising a single MSP (GJTec), Qilin executed what Bitdefender called the "Korean Leaks" operation—28 victims across financial services, over 1 million files and 2TB of data stolen in three publication waves.
Related Coverage:
- The "Korean Leaks" Data Heist: How North Korea's Moonstone Sleet and Qilin Ransomware Weaponized an MSP to Target South Korea's Financial Sector
- Habib Bank AG Zurich Hit by Qilin Ransomware: 2.5TB of Sensitive Data Stolen in Major Banking Breach
- Asahi Group Holdings Breach Investigation Reveals 1.9 Million Affected as Qilin Ransomware Dominates 2025 Attack Landscape
- The Ransomware-as-a-Service Ecosystem in Late 2025: From LockBit's Disruption to the Rise of Qilin, Akira, and DragonForce
LockBit: The Fall of an Empire
On February 19, 2024, visitors to LockBit's dark web leak site encountered an unexpected message: "THIS SITE IS NOW UNDER CONTROL OF LAW ENFORCEMENT." Operation Cronos—a coordinated effort by the UK's National Crime Agency, FBI, Europol, and agencies across ten countries—had seized LockBit's infrastructure, recovered 30,000 Bitcoin addresses (containing $112 million), and obtained decryption keys benefiting thousands of victims.
The psychological warfare was unprecedented. Law enforcement replaced the leak sites with banners styled exactly like LockBit's ransom pages, complete with countdown timers ticking toward press conferences rather than ransom deadlines. They unmasked the administrator "LockBitSupp" as Russian national Dmitry Yuryevich Khoroshev and revealed that despite promises, LockBit never deleted victims' data after receiving payments.
LockBit's market share collapsed from 34% in 2023 to approximately 8% in 2024-2025. Despite attempts to rebuild with LockBit 5.0 (released September 2025), the trust damage proved insurmountable. By late 2025, the group no longer ranks among the top fifteen most active ransomware operations—a stunning fall for what was once the industry's undisputed leader.
Related Coverage:
- Global Cybercrime Crackdown: Major Law Enforcement Operations of 2024-2025
- Global Cybercrime Takedowns in 2025: A Year of Unprecedented Law Enforcement Action
- The Bulletproof Fortress: Inside the Shadowy World of Cybercrime Hosting Infrastructure
- The Global Cybercrime Empire: Mapping the Underground Economy, Partnerships, and Geopolitical Power Structures
Strategic Analysis: What This Means for Defenders
The Business Model Threat
The top two groups achieved their rankings through repeatable business models, not one-time exploits. ShinyHunters proved in 2024 that targeting cloud service customers through credential theft was scalable; they applied that model to Salesforce in 2025 with even greater success. Cl0p has been exploiting the same architectural weakness in file transfer appliances since 2019—and 2025 was their most successful year yet.
These aren't opportunistic attacks. They're industrialized operations with documented playbooks, specialized tooling, and affiliate recruitment that mirrors legitimate SaaS businesses.
The Third-Party Problem
Both leading groups exploited third-party relationships. ShinyHunters compromised Salesforce customers through Salesloft Drift and Gainsight integrations. Qilin's Korean campaign compromised 28 organizations through a single MSP. Cl0p's entire model relies on attacking file transfer vendors used by hundreds of customers simultaneously.
Supply chain security is no longer optional—it's the primary attack surface.
The MFA Gap
In nearly every major breach detailed above, the lack of multi-factor authentication was a critical enabler. The Snowflake campaign succeeded because compromised accounts lacked MFA. ShinyHunters' Salesforce attacks exploited OAuth tokens from accounts without proper authentication controls. This is the lowest-hanging fruit that organizations continue to leave unpicked.
Actionable Recommendations
For the ShinyHunters/OAuth Threat:
- Audit all third-party Connected Apps in Salesforce and other SaaS platforms immediately
- Implement governance controls requiring admin approval for new OAuth integrations
- Deploy behavioral analytics to detect anomalous API access patterns
- Train helpdesk and support staff on vishing attacks and fraudulent IT support scenarios
- Enforce MFA on all accounts—no exceptions for service accounts or demo environments
For the Cl0p/Edge Device Threat:
- Encrypt data at rest on all file transfer appliances—this is the core architectural failure Cl0p exploits
- Monitor outbound traffic from edge devices for anomalous volume or destinations
- Maintain asset inventory of all MFT solutions (Cleo, MOVEit, GoAnywhere, and legacy Accellion)
- Implement network segmentation to limit lateral movement from compromised edge devices
- Subscribe to vendor security advisories and prioritize patches for internet-facing infrastructure
For General Resilience:
- Conduct tabletop exercises for ransomware scenarios including pure data extortion
- Verify backup integrity and recovery procedures—97% of organizations can now recover from encryption, making data theft the primary threat
- Review MSP and contractor access—Qilin's Korean campaign proved one vendor can compromise dozens of clients
- Implement zero-trust architecture for all third-party integrations
Conclusion: The Pattern Recognition Problem
The displacement of LockBit from the top three represents a fundamental shift in the threat landscape—from traditional ransomware encryption toward supply chain exploitation and data extortion. But the more troubling reality is that both leading groups are executing playbooks they've refined for years.
ShinyHunters proved their model in 2024 with Snowflake and scaled it in 2025 with Salesforce. Cl0p has been exploiting the same edge device architecture since the Accellion campaign in 2019. These aren't zero-days in the traditional sense—they're business models.
As an industry, we keep asking "how did this happen?" when the pattern has been visible for half a decade. The question isn't whether there will be another file transfer appliance breach or another OAuth token compromise—it's which vendor is next.
The attackers have figured out their repeatable formula. The question for defenders is: have we figured out ours?
Further Reading
For comprehensive coverage of the 2025 threat landscape, explore our related analyses:
- August 2025: A Month of Unprecedented Cyber Attacks and Data Breaches
- Who's Been Getting Hacked? A Look at Major Cyberattacks in Late 2025
- The Ransomware Revolution: How Attack Economics Are Reshaping the Threat Landscape Entering 2026
- FBI Strikes Major Blow Against Global Cybercrime: BreachForums Seizure Disrupts Elite Hacking Network
- CrowdStrike Confirms Insider Threat Linked to Scattered Lapsus$ Hunters Cybercrime Alliance
Sources include CISA, FBI FLASH advisories, Check Point Research, Mandiant, Barracuda, Cyble, Dragos, CIS, CYFIRMA, and primary security research from multiple incident response firms.