The Stanford Catfish: Inside the Chinese Academic Espionage Network Targeting America's Elite Universities

How a fake student named "Charles Chen" exposed a sophisticated intelligence operation hiding in plain sight
Executive Summary: A groundbreaking investigation by Stanford students has uncovered a sophisticated Chinese espionage network operating within one of America's most prestigious universities. The case of "Charles Chen," a fabricated persona used to target and potentially recruit Stanford students, represents a new frontier in insider threats—one where traditional security boundaries dissolve and foreign adversaries exploit the open, collaborative nature of academic institutions.
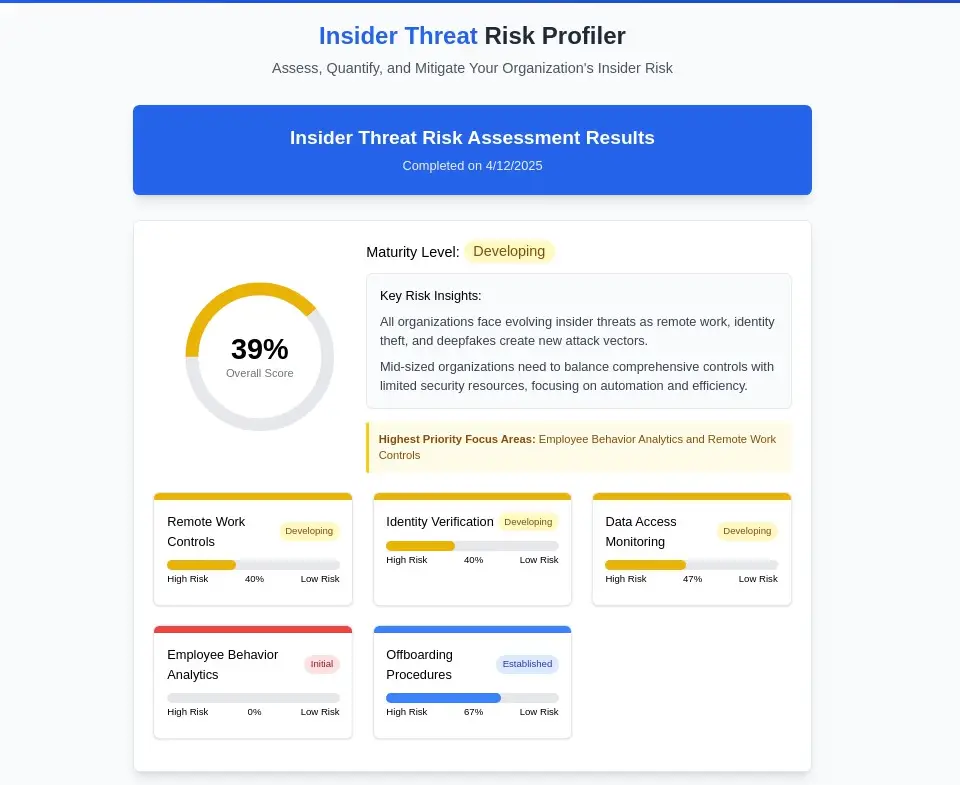
The Modern Campus Spy: No Trench Coat Required
The spy thriller image of shadowy figures meeting in parking garages feels antiquated in light of recent revelations from Stanford University. Today's academic espionage unfolds through Instagram direct messages, WeChat conversations, and the promise of all-expenses-paid trips to Beijing. This isn't fiction—it's the documented reality of how China's Ministry of State Security (MSS) operates on American college campuses.
On June 10, 2024, Stanford student Elsa Johnson received what appeared to be an innocent Instagram message: "Have we met on campus?" The sender, calling himself "Charles Chen," claimed to be an international student at Stanford. What followed was a three-month cat-and-mouse game that would ultimately expose a sophisticated espionage network targeting American universities, with implications that extend far beyond campus boundaries.

Anatomy of a Digital Recruitment Operation
The "Charles Chen" case study reveals the sophisticated methodology employed by modern state-sponsored actors. The operation followed a predictable playbook that security professionals should recognize:
Initial Contact Phase: Chen's approach followed a predictable pattern. "Have we met on campus?" he asked Johnson, followed by "You seem familiar. How are you?" His Instagram showed carefully crafted photos of a young Chinese man at Stanford locations, graduation ceremonies, and California destinations—all designed to establish credibility.
Intelligence Gathering: Despite claiming his knowledge was "just a guess," Chen demonstrated sophisticated preliminary intelligence. He knew Johnson spoke Mandarin despite this information not appearing on her social media, and he named specific Stanford students, asking if she knew them. This suggests extensive background research and possibly broader surveillance networks.
Trust Building and Incentivization: The recruitment process escalated systematically. Chen sent videos of American women who had "become famous" in China, positioned as success stories Johnson could emulate. He offered to pay for flights ($912 for LA to Shanghai), accommodations, and transportation, providing bank wire screenshots showing $5,485 to prove his financial capacity. "A bunch of people at Stanford have been to China this summer," he claimed. "If someone pays for you, would you come?"
Lifestyle Temptation: Beyond financial incentives, Chen painted pictures of luxury and success—showing videos of an expensive Bentley he claimed to own and a house in LA. The message was clear: cooperation could lead to wealth and status.
Communication Control: Chen persistently pushed to migrate conversations to WeChat, China's heavily monitored messaging platform. His behavior revealed operational discipline: if Johnson didn't respond within hours, he would delete and resend messages. This tactic served dual purposes—maintaining pressure while eliminating evidence trails.
Operational Security Failures: The operation's exposure came through Chen's own mistake. After three months of patient relationship-building, he publicly commented on Johnson's Instagram in Mandarin, asking her to delete screenshots she had taken—despite never being told she was documenting their conversations. This security breach revealed either surveillance of her device or a significant operational error that ultimately exposed the entire network.

The Broader Network: Beyond One Fake Student
Johnson's experience reveals the psychological manipulation at the heart of these operations. As she documented the conversations through screenshots, the relationship took increasingly troubling turns. When she questioned the trip's value, Chen responded with veiled aggression: "Can't you afford a thousand-dollar flight ticket?" When she continued to resist, the mask began to slip.
The operation's conclusion was telling. After months of patient relationship-building, Chen's final messages revealed the true nature of the interaction. When Johnson confronted him about knowing she had taken screenshots, he responded: "I see, you think too highly of yourself." He quickly deleted that message and replaced it with: "You are worthless." After this exchange, Chen deleted all Instagram messages and vanished—classic behavior when an intelligence operation is compromised.
Johnson's investigation, conducted with FBI assistance and Stanford experts, revealed Chen's operation extended far beyond her case. She identified at least ten other women targeted since 2020, with the perpetrator using slight variations of his identity (previously "Charles Chan"). All targets were young women, primarily studying China-related topics or STEM fields.
The Strategic Targeting of Demographics
FBI analysis revealed the strategic reasoning behind targeting young white American women. As Johnson learned from her consultations with experts, including Glenn Tiffert at Stanford's Hoover Institution, the CCP views such individuals as particularly valuable propaganda assets—people who can give the impression that "there is nothing to fear from China."
The targeting extends beyond individual students to specific research areas and military connections. Johnson documented cases of Stanford Graduate School of Business students with military backgrounds being physically approached by Chinese nationals who somehow knew their military status. These contacts followed the same pattern: friendly questions escalating to inquiries about U.S. military base locations and capabilities.
The Broader Intimidation Campaign
The operation extends beyond recruitment to intimidation of Chinese and Chinese-American students. Johnson documented a particularly chilling example: a Chinese-American friend, a U.S. citizen born in America, received an anonymous email on June 26, 2024, threatening to kill him and his Chinese father "for betraying the CCP by living in America."
This aligns with documented cases of transnational repression, including the 2023 conviction of a Chinese student at Berklee College of Music for cyberstalking a pro-democracy Chinese student. The message is clear: in Beijing's view, "anyone with Chinese blood is Chinese—even if they're born in America—and they should be loyal to the People's Republic of China."

The Legal Framework Behind the Coercion
China's 2017 National Intelligence Law mandates that all Chinese citizens support state intelligence work, regardless of their location. This legal requirement transforms every Chinese national studying abroad into a potential intelligence asset, whether willing or not.
The mechanism is particularly insidious at the student level. The China Scholarship Council (CSC), which funds an estimated 15% of Chinese students at American universities, requires recipients to:
- Pass loyalty tests to the Chinese Communist Party
- Align research with state priorities outlined in the "Made in China 2025" initiative
- Submit regular "situation reports" to Chinese diplomatic missions
- Engage in peer surveillance of other Chinese nationals
Students who resist these requirements face scholarship termination, visa revocation, and—most chillingly—threats to family members remaining in China.
The Strategic Target: Why Stanford?
Stanford's selection as a primary target reflects China's strategic priorities under its "Made in China 2025" plan, which aims to achieve technological dominance in artificial intelligence, robotics, and other frontier technologies. As one anonymous expert told the Stanford Review, given Stanford's AI dominance, it represents "academic target number one."
The university's culture of openness and collaboration—traditionally viewed as strengths—have become vulnerabilities in this new threat landscape. The same characteristics that drive breakthrough research also create opportunities for foreign adversaries to exploit academic freedom and international cooperation.
Insider Threat Implications for Organizations
The Stanford case offers critical lessons for organizations beyond academia:
Evolution of Insider Threats
Traditional insider threat models focus on individuals with legitimate access who abuse their privileges. The Stanford case represents a hybrid threat where external adversaries create the appearance of legitimate access through identity deception and social engineering.
Social Media as Attack Vectors
Professional networking and social media platforms have become primary vectors for initial contact and trust-building. Security awareness programs must evolve to address these sophisticated social engineering tactics.
Long-term Relationship Building
Unlike typical cybercriminals seeking quick financial gain, state-sponsored actors invest months or years building relationships with targets. This patient approach requires organizations to think differently about threat detection timelines.
Information Gathering Without System Access
The Stanford operation succeeded without requiring network penetration or system access. Valuable intelligence was gathered through conversation, relationship building, and leveraging the target's own research interests.

The Silence Problem: Why Institutions Don't Speak Up
Johnson's case illustrates why reporting remains challenging. Despite her extensive documentation and FBI consultation, she initially remained silent due to fear of retaliation. "I was extremely frightened to talk about what happened to me out of fear of being further targeted," she explained. "I love Chinese culture, and I want to be able to visit the country, but speaking out could lead to retaliation by the Chinese authorities."
Even after going public, the intimidation continues. Johnson reports receiving weekly phone calls from U.S. numbers, with callers greeting her in English before switching to Chinese—a pattern suggesting continued monitoring or harassment. She hangs up immediately when these calls occur.
The fear extends beyond individual targets. Most faculty, students, and experts interviewed for investigations request anonymity, creating an environment where:
- Transnational Repression: Chinese students and faculty fear retaliation against themselves or family members in China
- Accusations of Racism: American faculty and administrators worry that raising concerns about Chinese espionage will be labeled as racial profiling
- Financial Relationships: Universities have significant financial relationships with China—Stanford received over $64 million in anonymous donations from China since 2010
Policy Implications and Timing Concerns
Johnson's case takes on additional significance given recent policy developments. President Trump announced plans to allow up to 600,000 Chinese nationals to study in the U.S.—more than doubling the current 277,000. While Johnson acknowledges that "the vast majority pose no threat," she notes that "increasing these numbers leaves us more vulnerable to espionage."
Her recommendations are practical and immediate: "The FBI should set up tip lines so American students can report any threats or suspicious contact." She emphasizes the need for awareness: "I tell my friends all the time: if you ever get a message out of the blue from a stranger telling you to visit China, be on your guard."
Organizational Response Strategies
Based on the Stanford case and broader insider threat research, organizations should consider the following defensive measures:
Sophisticated Social Engineering Recognition
The Johnson case reveals several advanced social engineering techniques that organizations should train personnel to recognize:
- Credential Establishment: Using fake but convincing social media profiles with location-specific photos and apparent peer connections
- Knowledge Display: Demonstrating research about targets that suggests legitimate access to information or social networks
- Incremental Escalation: Beginning with innocent networking before gradually introducing financial incentives and travel opportunities
- Pressure Tactics: Using time-sensitive offers and financial proof to create urgency and overcome resistance
- Platform Migration: Insisting on communication through specific platforms that may offer operational advantages to adversaries
- Persistence Through Silence: Deleting and resending messages when targets don't respond, maintaining pressure while eliminating evidence

Advanced Behavioral Analysis
The Johnson case also demonstrates the importance of behavioral consistency analysis:
- Story Inconsistencies: Chen claimed to be from Shanghai, then later Nanjing (200 miles away)
- Educational Claims: Stated he was a junior studying economics but couldn't be found in Stanford directories
- Lifestyle Display: Showed expensive cars and homes while ostensibly being a student
- Communication Patterns: Systematic deletion and resending of messages revealed operational training rather than normal social behavior
Research Security Protocols
- Develop classification systems for sensitive research that consider not just traditional "classified" information, but also methodologies, preliminary findings, and collaborative structures
- Establish clear guidelines for international collaboration and information sharing
- Create reporting mechanisms for suspicious inquiries about research activities
Social Media and Communication Hygiene
- Provide guidance on professional social media use, particularly regarding information that could be used for targeting or intelligence gathering
- Establish protocols for international communication, particularly with individuals in countries of concern
- Consider communication monitoring tools for high-risk research areas
Cultural Sensitivity with Security Awareness
- Develop training programs that distinguish between legitimate security concerns and racial profiling
- Create safe reporting mechanisms that protect both reporters and subjects from retaliation
- Establish clear policies regarding international partnerships and foreign funding transparency

Government and Industry Response
The Stanford case has prompted significant government attention. The Department of Education, alongside the National Counterintelligence and Security Center, has issued guidance to help colleges and universities mitigate foreign threats to research.
Key government recommendations include:
- Funding Transparency: Tracking the true source of overseas grants and donations
- Research Security: Implementing controls for sensitive research areas
- Incident Reporting: Establishing clear channels for reporting suspicious activities
- Partnership Evaluation: Carefully assessing international collaboration opportunities
The Broader Academic Espionage Landscape
The Stanford case is not isolated. Similar operations have been documented at universities across the United States and internationally. The FBI has warned that American universities are "soft targets" for state-sponsored intellectual property theft, with particular concern about:
- Technology Transfer: Unauthorized sharing of research methodologies and findings
- Talent Recruitment: Efforts to recruit researchers to work directly for foreign governments
- Infrastructure Mapping: Intelligence gathering about research capabilities and institutional structures
- Influence Operations: Attempts to shape academic discourse and research priorities
Looking Forward: Balancing Security and Academic Freedom
The challenge facing universities—and by extension, all organizations engaged in sensitive research or development—is maintaining openness and collaboration while protecting against sophisticated foreign intelligence operations.
This balance requires:
Institutional Changes
- Risk Assessment: Regular evaluation of research areas and personnel most likely to be targeted
- Security Integration: Incorporating threat awareness into standard onboarding and training programs
- Incident Response: Developing procedures specifically designed for handling suspected espionage activities
Cultural Evolution
- Awareness Without Paranoia: Creating security-conscious cultures that don't stifle legitimate collaboration
- Reporting Normalization: Making threat reporting a routine part of institutional safety, similar to other security protocols
- Transparency Commitment: Open discussion of security challenges and protective measures
Policy Development
- Clear Guidelines: Establishing explicit policies regarding international collaboration, foreign funding, and research sharing
- Enforcement Consistency: Ensuring security measures apply equally regardless of nationality or ethnicity
- Regular Updates: Adapting policies as threat actors evolve their tactics

Conclusion: The New Reality of Academic Security
The "Charles Chen" operation represents a watershed moment in our understanding of how foreign intelligence services exploit academic institutions. The sophistication, patience, and psychological manipulation demonstrated in this case should serve as a wake-up call for all organizations handling sensitive information.
The Johnson case represents a paradigm shift in how we must think about security awareness and threat detection. Her experience—documented in real-time through screenshots and later verified through FBI investigation—provides a detailed playbook of how modern state-sponsored social engineering operations work.
Several key lessons emerge from her three-month ordeal:
- Trust Your Instincts: Johnson began screenshotting conversations when something felt "off," despite the initial interactions seeming benign
- Verify Identity Claims: Simple verification through student directories or institutional contacts could have exposed the deception earlier
- Document Everything: Johnson's systematic documentation proved crucial for investigation and analysis
- Seek Expert Consultation: Her decision to consult with China experts and ultimately the FBI provided professional analysis of the threat
- Understand the Broader Pattern: Recognition that her experience was part of a larger operation helped contextualize the threat

Perhaps most importantly, Johnson's decision to go public despite personal risks demonstrates the importance of transparency in combating these operations. As she notes, "It is frightening yet ingenious what the CCP is doing, and other American students like me need to be aware of the threat we're facing."
For security professionals, the Stanford case offers several critical insights:
- Traditional perimeter security is insufficient when adversaries operate through social engineering and relationship manipulation
- Long-term relationship building by unknown contacts should trigger security protocols regardless of how benign initial interactions appear
- Information classification must extend beyond traditional secrets to include research methodologies, collaborative structures, and preliminary findings
- Cultural sensitivity and security awareness are not mutually exclusive—organizations can protect against foreign intelligence operations without engaging in racial profiling
- Institutional silence creates vulnerability—security requires a culture where reporting suspicious activities is normalized and protected
The future of academic and research security will require a fundamental rethinking of how we protect intellectual property and institutional knowledge. The Stanford case shows us that the battlefield has shifted from classified government facilities to university campuses, research laboratories, and social media platforms.
As we move forward, the question isn't whether foreign intelligence services will continue targeting American institutions—it's whether we'll develop the awareness, tools, and cultural frameworks necessary to protect our intellectual assets while preserving the openness that drives innovation.

The "Charles Chen" operation may have been exposed, but it represents just one instance in what experts believe is a much larger, ongoing campaign. For organizations serious about protecting their intellectual property and personnel, the Stanford case should serve as both a warning and a roadmap for building more robust defenses against the insider threats of tomorrow.
This analysis is based on extensive reporting by The Stanford Review, first-person testimony by Stanford student Elsa Johnson published in The Times of London, FBI investigations, and expert interviews conducted between 2024 and 2025. Special acknowledgment to Johnson's courage in going public with her experience despite personal security risks. Organizations seeking additional guidance on insider threat mitigation should consult with the Department of Homeland Security's Cybersecurity and Infrastructure Security Agency (CISA) and the National Counterintelligence and Security Center (NCSC).
















