Trump-Putin Summit Documents Left Behind: Security Breach or Administrative Oversight?

Government papers containing sensitive details about the Trump-Putin Alaska summit were accidentally abandoned in a hotel printer, sparking debate over security protocols
Three hotel guests at the Hotel Captain Cook in Anchorage, Alaska, made an unexpected discovery on Friday morning that has reignited debates about the Trump administration's handling of sensitive government information. At around 9 a.m. on Friday, three guests at Hotel Captain Cook, a four-star hotel located 20 minutes from the Joint Base Elmendorf-Richardson in Anchorage where leaders from the U.S. and Russia convened, found the documents left behind in one of the hotel's public printers.





What the Documents Revealed
Eight pages, that appear to have been produced by U.S. staff and left behind accidentally, shared precise locations and meeting times of the summit and phone numbers of U.S. government employees. The documents, which bore U.S. State Department markings, contained previously undisclosed details about the August 15 meetings between President Donald Trump and Russian President Vladimir Putin.
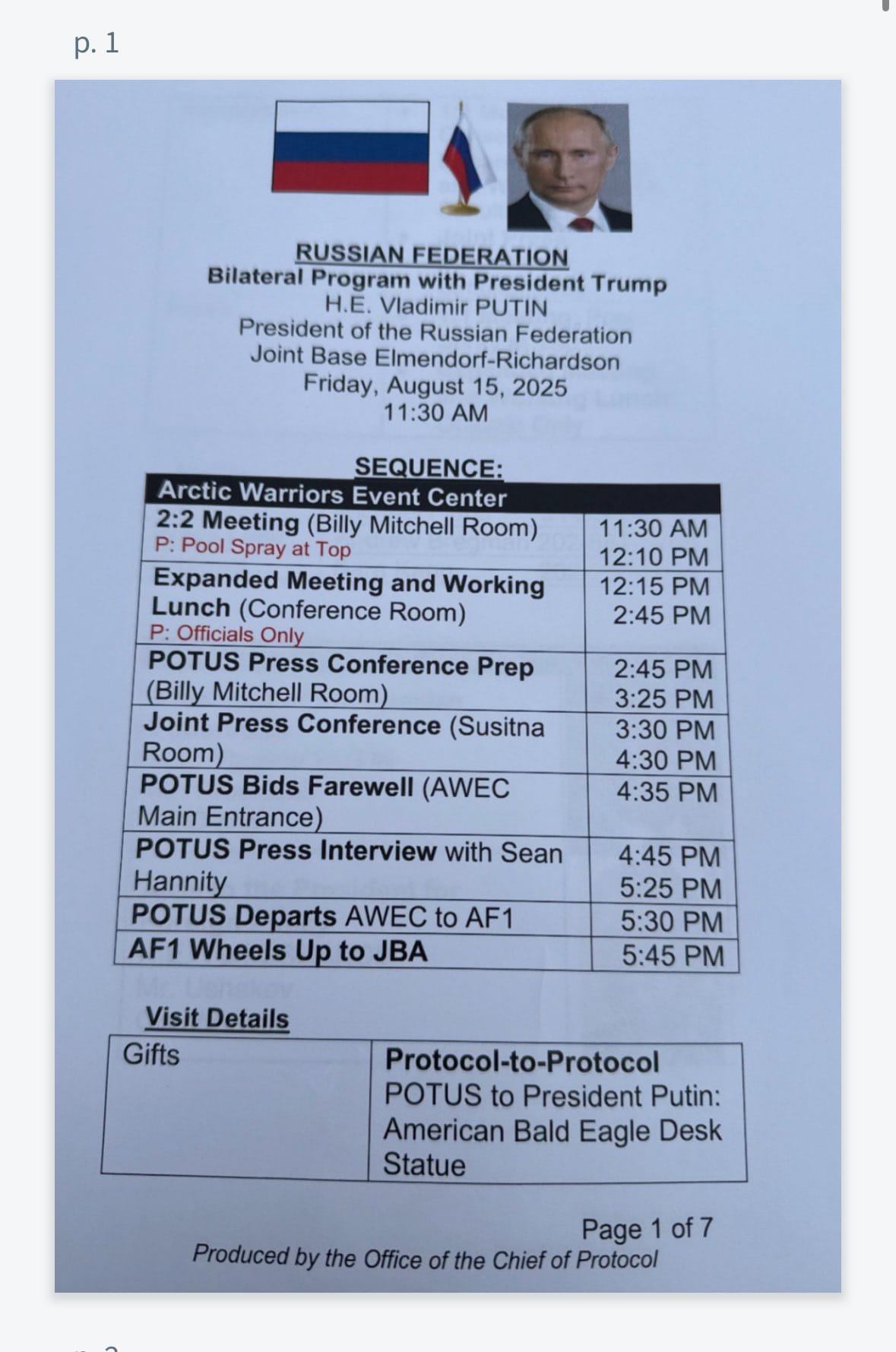
The leaked materials provided an intimate look at the summit's logistics. The first page in the printed packet disclosed the sequence of meetings for August 15, including the specific names of the rooms inside the base in Anchorage where they would take place. It also revealed that Trump intended to give Putin a ceremonial present. That gift was to be "American Bald Eagle Desk Statue," according to the documents.
Beyond ceremonial details, the papers contained operationally sensitive information. Pages 2 through 5 listed the names and phone numbers of three U.S. staff members as well as the names of 13 U.S. and Russian state leaders. The list included phonetic pronouncers for all the Russian men expected at the summit, including "Mr. President POO-tihn."
The Cancelled Lunch That Never Was
Perhaps the most detailed portion of the documents focused on a planned luncheon that ultimately never took place. Pages 6 and 7 in the packet described how lunch at the summit would be served, and for whom. A menu included in the documents indicated that the luncheon was to be held "in honor of his excellency Vladimir Putin."
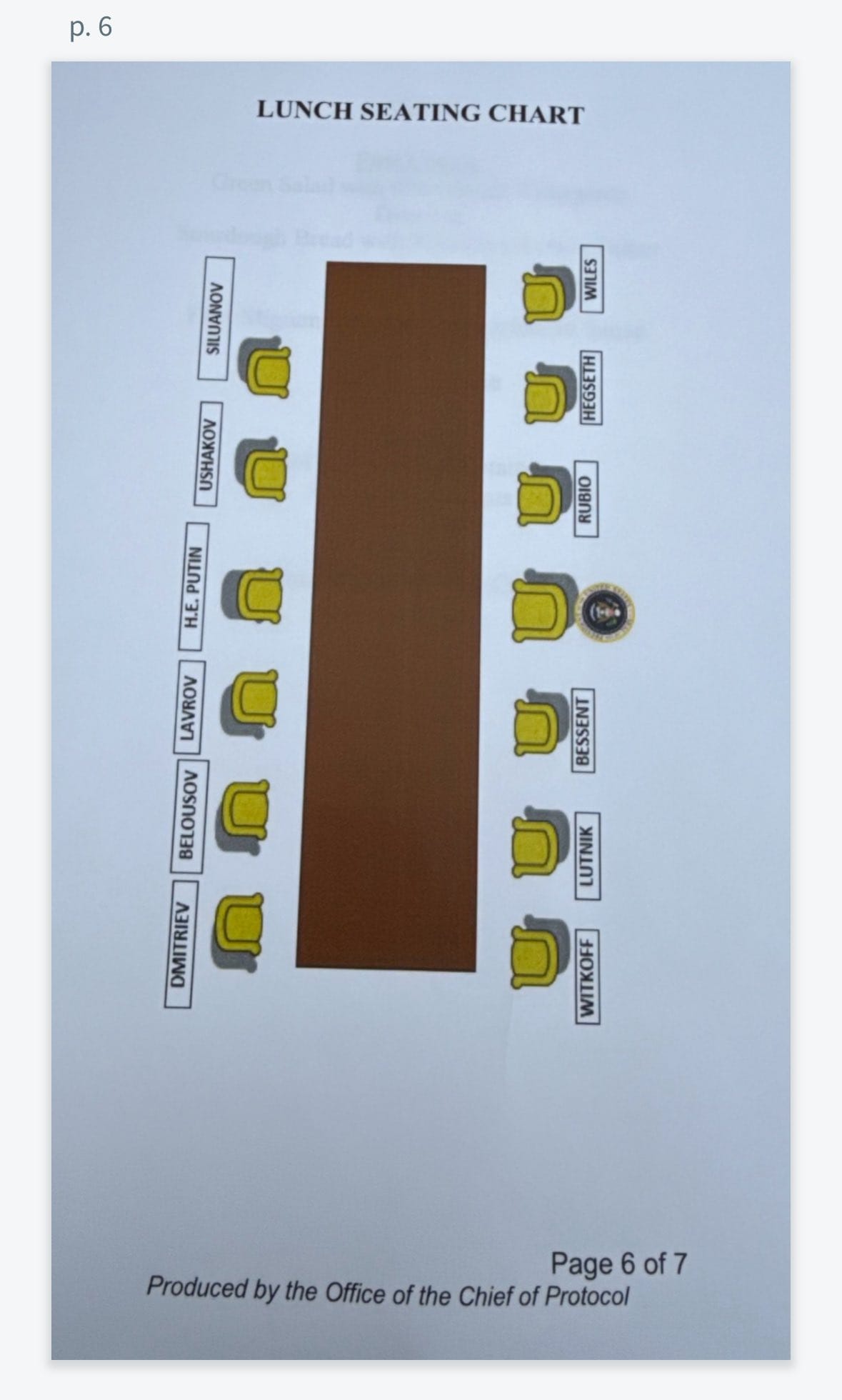
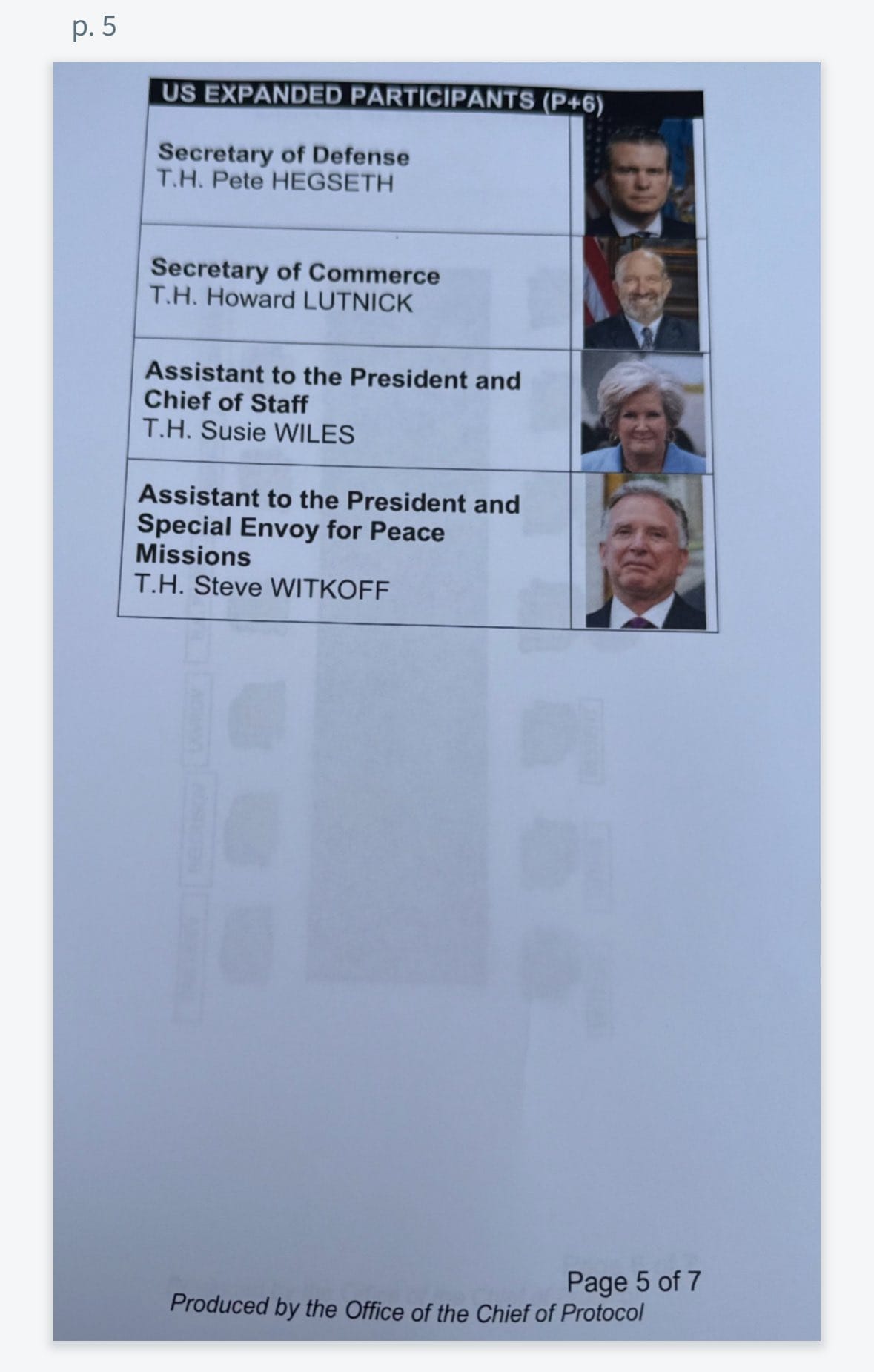
The seating arrangements revealed the diplomatic choreography planned for the meal. A seating chart shows that Putin and Trump were supposed to sit across from each other during the luncheon. Trump would be flanked by six officials: Secretary of State Marco Rubio, Secretary of Defense Pete Hegseth and White House Chief of Staff Susie Wiles to his right, and Secretary of the Treasury Scott Bessent, Secretary of Commerce Howard Lutnick and Special Envoy for Peace Missions Steve Witkoff to his left. Putin would be seated immediately next to his Minister of Foreign Affairs, Sergey Lavrov, and his Aide to the President for Foreign Policy, Yuri Ushakov.
During the summit Friday, lunch was apparently cancelled. But it was intended to be a simple, three-course meal, the documents showed. After a green salad, the world leaders would choose between either filet mignon or halibut olympia. Crème brûlée would be served for dessert.
White House Response: "Hilarious" Claims
The White House moved quickly to downplay the significance of the discovery. White House Deputy Press Secretary Anna Kelly referred to the materials as a "multi-page lunch menu" and said their discovery by hotel guests does not compromise national security. "It's hilarious that NPR is publishing a multi-page lunch menu and calling it a 'security breach,'" Kelly told NewsNation.
Kelly's response was notably dismissive of both the incident and the reporting. "This type of self-proclaimed 'investigative journalism' is why no one takes them seriously and they are no longer taxpayer-funded thanks to President Trump," she added, referencing the administration's defunding of NPR.
Expert Analysis: A Pattern of Security Lapses
National security experts viewed the incident more seriously than the White House's characterization suggests. Jon Michaels, a professor of law at UCLA who lectures about national security, said that the documents found in the printer of the Alaskan hotel reveal a lapse in professional judgement in preparation for a high-stakes meeting. "It strikes me as further evidence of the sloppiness and the incompetence of the administration," said Michaels. "You just don't leave things in printers. It's that simple."
The incident fits into a broader pattern of information security issues within the Trump administration. The printed papers are the latest example of a series of security breaches by officials of the Trump administration. Earlier this week, members of a law enforcement group chat that included members of U.S. Immigration and Customs Enforcement (ICE) added a random person to a conversation about an ongoing search for a convicted attempted murderer. In March, U.S. national security leaders accidentally included a journalist in a group chat about impending military strikes in Yemen.
The "Signalgate" Scandal: A Deeper Security Crisis
The Alaska hotel printer incident gains additional significance when viewed alongside the Trump administration's most serious communication security breach to date: the "Signalgate" scandal that erupted in March 2025. According to detailed reporting by Breached, this incident revealed far more concerning security lapses than a forgotten lunch menu.
The controversy began when Jeffrey Goldberg, editor-in-chief of The Atlantic, was inadvertently added to a Signal group chat by National Security Advisor Mike Waltz. The group chat included high-ranking officials such as Vice President JD Vance, Defense Secretary Pete Hegseth, CIA Director John Ratcliffe, Director of National Intelligence Tulsi Gabbard, and National Security Advisor Michael Waltz. These officials were discussing sensitive military operations against Houthi targets in Yemen.
The breach was particularly significant because it involved real-time military planning discussions outside of secure government channels. CBS News national security contributor Sam Vinograd noted that "by communicating classified information on a nonsecure platform like Signal, senior U.S. government officials... increased the chance that foreign governments could get access to sensitive operational security plans — and that could put our own troops in harm's way."
The Signal controversy highlighted several critical security failures. Some messages in the group chat were designed to disappear after one week, and others after four weeks, potentially violating federal laws requiring the preservation of official records. Legal experts suggested that the Signal chat might have violated provisions of the Espionage Act, particularly the section making it illegal to inadvertently share "through gross negligence" sensitive national security information.
Compromised Communications: The TeleMessage Breach
The security situation became even more complex when hackers breached TeleMessage, an Israeli company that provides modified versions of encrypted messaging apps, including a Signal clone reportedly used by Trump administration officials. As reported by Breached, this breach exposed archived government messages and revealed critical vulnerabilities in the administration's communication security.
The hacker claimed they were able to breach TeleMessage's systems in just "15 to 20 minutes," suggesting significant vulnerabilities in the platform's security infrastructure. The breach exposed archived chat logs, contact information of U.S. government officials, backend login credentials, and data related to U.S. Customs and Border Protection.
Most concerning was the revelation that archived chat logs were not end-to-end encrypted between the modified version of Signal and the archive destination, creating a significant security vulnerability. Software engineer Micah Lee found several vulnerabilities in the TM SGNL app, including hardcoded credentials that made it an easier target for hackers.
DNI Gabbard's Password Practices: Personal Security Failures
The security concerns extend beyond communication platforms to basic cybersecurity hygiene. A Wired investigation covered by Breached revealed that Director of National Intelligence Tulsi Gabbard repeatedly used the same weak password across multiple personal online accounts for years.
According to the investigation, Gabbard used an "easily cracked" password across multiple email addresses and online accounts during her time in Congress from 2013 to 2021. The password contained the word "shraddha," which appears to have personal significance related to her reported connection to the Science of Identity Foundation.
While Gabbard's spokesperson dismissed these concerns as historical issues, cybersecurity experts warn that password reuse can have long-term security implications, as credentials from old breaches are often used in newer attacks. The combination of weak password practices and improper use of messaging platforms raises legitimate concerns about information security at the highest levels of government.
Iran's Cyber Targeting: An Active Threat
These internal security failures become even more concerning when viewed against the backdrop of active foreign threats targeting the Trump administration. As detailed by Breached, Iran's cyber warfare capabilities, particularly through groups like APT42, have directly targeted Trump campaign infrastructure.
APT42, affiliated with the Islamic Revolutionary Guard Corps (IRGC), specializes in credential theft, espionage, and targeted phishing campaigns against high-profile targets including government officials and political campaigns. The group's successful penetration of Trump campaign systems demonstrates the real-world consequences of inadequate security practices.
The Iranian cyber threat is not theoretical – it represents an active, ongoing campaign by a sophisticated adversary. When combined with the administration's documented security lapses, including forgotten documents, compromised communication platforms, and weak password practices, the vulnerability profile becomes deeply concerning from a national security perspective.
Summit Context and Outcomes
The document leak overshadowed what was already a controversial summit. The 2025 Russia–United States Summit (also known as the Alaska 2025 or the Trump–Putin Summit) was a summit meeting between United States president Donald Trump and Russian president Vladimir Putin. It was held on August 15, 2025, at Joint Base Elmendorf–Richardson in Anchorage, Alaska. The main topic of discussion was the ongoing Russia–Ukraine war, which Trump wants to end. The summit ended without an agreement being announced, although Trump later intimated that in his view the onus was now on Ukraine to cede territory in order to end the war.
The meeting marked several historic firsts. It was the first time Putin was invited to a Western country since he ordered the full-scale Russian invasion of Ukraine in 2022. Putin faces an arrest warrant issued by the International Criminal Court for alleged war crimes.
The Bigger Picture: A Cascade of Security Failures
While the White House characterizes the leaked documents as merely logistical materials, the incident represents more than an isolated administrative oversight. When viewed alongside the Signalgate scandal, the TeleMessage breach, Director Gabbard's password practices, and active threats from Iranian cyber actors, a pattern emerges of systemic security vulnerabilities at the highest levels of government.
The documents contained not just menu details but also precise meeting locations, timing, staff contact information, and ceremonial plans that could potentially be valuable to foreign intelligence services. The timing of the discovery – on the morning of the summit itself – suggests the documents were freshly printed and immediately forgotten, pointing to possible last-minute preparation issues that security experts warn could create vulnerabilities in sensitive diplomatic operations.
These incidents collectively highlight several critical security challenges:
Communication Security: The combination of the Signalgate incident and the TeleMessage breach demonstrates that the administration's approach to secure communications has been fundamentally flawed. Using consumer messaging apps for sensitive military planning, even modified versions, creates unnecessary risk.
Information Handling: From forgotten printer documents to disappearing Signal messages, the administration has repeatedly struggled with proper information management protocols that are essential for both security and legal compliance.
Personal Security Hygiene: When the nation's top intelligence official uses weak, reused passwords, it reflects broader institutional failures in cybersecurity education and enforcement.
Foreign Threat Response: With Iranian APT groups actively targeting the administration, these security lapses provide multiple attack vectors for sophisticated adversaries.
As the Trump administration continues to face scrutiny over its information security practices, the Alaska hotel printer incident provides a tangible example of how seemingly minor oversights can expose sensitive government operations. Whether viewed as a simple administrative mistake or part of a broader pattern of security negligence, these incidents collectively raise serious questions about the administration's ability to protect sensitive information in an increasingly hostile cyber environment.
The convergence of internal security failures and external cyber threats creates a perfect storm of vulnerability that extends far beyond any single document left in a hotel printer. For an administration conducting high-stakes diplomacy with adversaries like Russia while facing active cyber campaigns from Iran, such security lapses represent more than embarrassing mistakes – they constitute potential national security risks with far-reaching implications.
The White House and U.S. Department of State did not respond to additional requests for comment about the documents or their security protocols.





