Two Breaches, One Company: Rainbow Six Siege's $339 Trillion Hack Exposes Years of Helpdesk Corruption at Ubisoft

Executive Summary: Ubisoft faces dual security crises as Rainbow Six Siege remains offline following a devastating December 27, 2025 breach that flooded players with billions in premium currency—while VX-Underground simultaneously reveals that outsourced helpdesk staff have been accepting bribes for panel access since 2021. The combination exposes catastrophic failures in both technical security and human oversight.
Crisis One: The December 27 Rainbow Six Siege Breach
What Happened
On Saturday morning, December 27, 2025, Rainbow Six Siege players logged in to find chaos:
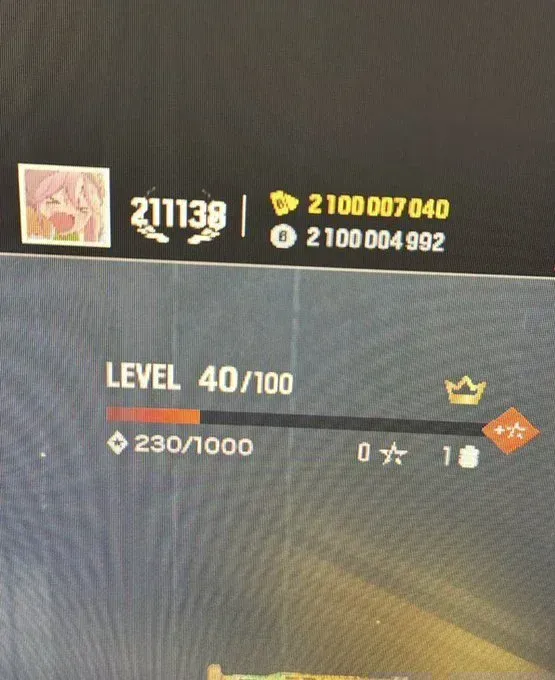
- 2 billion R6 Credits suddenly appeared in accounts (worth approximately $13.3 million per player at Ubisoft's pricing of $99.99 per 15,000 credits)
- 2 billion Renown (free currency) added to every account
- All cosmetic items unlocked, including ultra-rare "Glacier" skins and developer-only items
- Random bans and unbans affecting ordinary players, streamers, and even official Ubisoft accounts
- Custom messages in the ban ticker mocking Ubisoft leadership
The total economic impact: approximately $339 trillion in virtual currency distributed across the player base.

Ubisoft's Response Timeline
9:10 AM EST, December 27: Official acknowledgment via X (Twitter)
"We're aware of an incident currently affecting Rainbow Six Siege. Our teams are working on a resolution."
~30 minutes later: Complete server shutdown across PC, PlayStation, and Xbox platforms. Marketplace taken offline.
Later December 27: Ubisoft clarifies:
- No players will be banned for receiving or spending the illicit credits
- Full rollback of all transactions since 11:00 AM UTC underway
- Ban ticker messages were NOT from Ubisoft (the feature had been disabled in a previous update)
December 28, 2025 (as of this writing): Servers remain offline indefinitely. Status page shows "unplanned outage" across all platforms. Ubisoft states rollback is "being handled with extreme care" but provides no ETA for restoration.
Chat, we've solved the mystery of the Ubisoft Rainbow Six Siege incident. Unfortunately, I cannot go too deep into details (yet), but it is very silly.
— vx-underground (@vxunderground) December 29, 2025
Okay, we have FIVE GROUPS of people now.
GROUP ONE - Responsible for the Rainbow Six Siege incident, they gave away…
The Technical Attack: NOT MongoBleed (That Was a Lie)
Initial Reports Were Wrong: Early reporting, including from VX-Underground, suggested attackers used CVE-2025-14847 ("MongoBleed") to breach Ubisoft. This has since been proven FALSE.
According to VX-Underground's follow-up investigation, Group 2 lied about using MongoBleed to gain access to Ubisoft's internal Git repositories. While they DO have Ubisoft internal source code, they obtained it through different means and used the MongoBleed story as a cover.
What Actually Happened (Per VX-Underground):
The December 27 Rainbow Six Siege chaos was caused by Group 1, who exploited a Rainbow Six Siege service endpoint directly, allowing them to:
- Ban and unban players at will
- Modify player inventories and grant items
- Distribute massive amounts of in-game currency
- Control the ban ticker messaging system
Critically: Group 1 did NOT touch user data and likely couldn't even access it. Their exploit targeted game service APIs, not the underlying database or customer information systems.

The Real Technical Method:
VX-Underground reports that Group 5 (which appeared later to call out the lies) provided a comprehensive technical breakdown showing exactly how Group 1 performed their actions. Group 5 appears to be highly skilled reverse engineers who likely make and sell cheats for Ubisoft games and were annoyed that Group 2 was lying about MongoBleed.
The actual exploitation method involved reverse engineering Ubisoft's game services and finding authentication/authorization flaws in the Rainbow Six Siege backend APIs - NOT database exploitation.
Five Hacker Groups: The Complete Breakdown
VX-Underground's investigation ultimately identified FIVE distinct groups involved in the Ubisoft chaos, each with different motives, capabilities, and levels of truthfulness:
GROUP ONE - "The Chaos Crew" (VERIFIED REAL)
- What they did: Exploited a Rainbow Six Siege service to grant $339 trillion in currency, ban/unban players, unlock all items
- Method: Direct exploitation of game service APIs (NOT MongoBleed, NOT database breach)
- Access: Game inventory and moderation systems only - did NOT access user data
- Status: Laying low after the December 27 incident
- Motive: Pure disruption and "for the lulz"
- VX Assessment: "Only group with verifiable, tangible impact on live environment"
GROUP TWO - "The Liars" (PARTIALLY VERIFIED)
- Claims: Exploited MongoDB via MongoBleed to steal Ubisoft source code from 1990s to present
- Truth: They DO have Ubisoft internal source code, BUT they LIED about how they got it
- Reality: Had access to Ubisoft source code for a while, used MongoBleed story as cover to release it
- Status: Trying to hide behind Group 1's actions to justify leaking their previously obtained data
- VX Assessment: "Medium to high confidence they have source code, but MongoBleed claim proven to be A LIE"
GROUP THREE - "The Frauds" (COMPLETELY FAKE)
- Claims: Compromised Ubisoft and exfiltrated user data via MongoBleed
- Status: Actively trying to extort Ubisoft on Telegram
- Reality: Using FAKE data to intimidate Ubisoft and customers
- VX Assessment: "They did NOT compromise Ubisoft customer data, they're LYING"
- Note: Multiple imposter Group 3s have appeared, also lying
GROUP FOUR - "The Critics" (VERIFIED)
- Role: Calling out Group 2 as liars, frustrated that Group 1 might get blamed for Group 2's actions
- Claims: Group 2 had Ubisoft source code for a long time, is trying to frame Group 1
- Status: Laying low, annoyed at the drama
- Relationship: Loosely affiliated with Group 1, part of the "hardcore Ubisoft gaming nerd community"
GROUP FIVE - "The Receipts" (HIGHEST CREDIBILITY)
- Who they are: Highly skilled reverse engineers, likely professional cheat developers for Ubisoft games
- Why they appeared: Annoyed that Group 2 lied about MongoBleed, wanted to set the record straight
- What they provided:
- Step-by-step technical breakdown of how Group 1 performed all actions
- Photographic evidence of how Group 2 actually got Ubisoft internal access (NOT MongoBleed)
- Code demonstrating Group 1's methods and other unreported capabilities
- Analysis of how Ubisoft detected and responded to the incidents
- VX Assessment: "Has a big swinging dick and isn't fucking around. Very intelligent and calculated. Make and sell cheats for Ubisoft games, very talented reverse engineers"
- Promise: Will release full technical write-up publicly once drama between Groups 1 and 2 settles
The "Hardcore Ubisoft Gaming Nerd Community"
According to VX-Underground, Groups 1, 2, 4, and 5 all know each other and "operate loosely together, in some capacity" - essentially a community of hardcore gamers, reverse engineers, and cheat developers who understand Ubisoft's systems intimately.
Group 3 (the extortionists) appears to be outsiders trying to capitalize on the chaos.
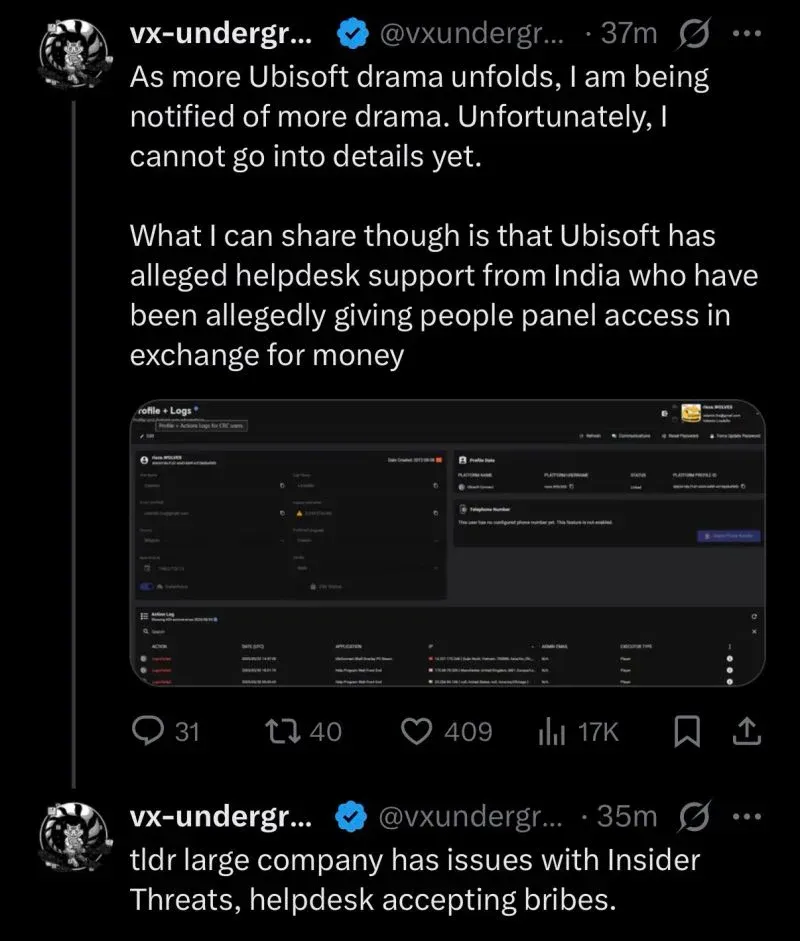
Crisis Two: The Helpdesk Bribery Scheme (2021-Present)
A Completely Separate Security Failure
VX-Underground Clarification (Posted After Initial Reports):
"This is not related to the recent Rainbow 6 siege compromise and/or chaos which unfolded recently. This is a separate issue."
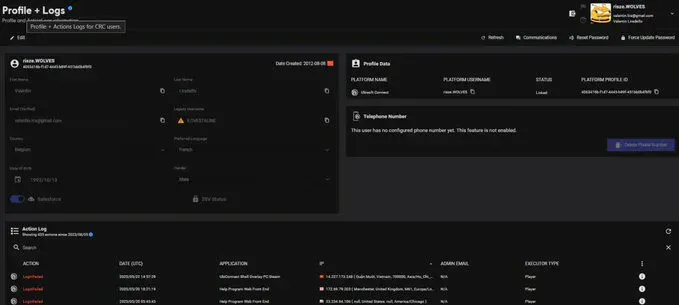
Since at least 2021, Ubisoft has had persistent issues with insider threats from helpdesk personnel. Customer support representatives, most notably from India, South Africa, and Egypt, were allegedly accepting monetary bribes to give threat actors access to other users' Rainbow Six Siege accounts.
What Bribed Support Staff Provided
When threat actors paid off customer support representatives, they gained access to a support panel showing:
Customer Personal Information:
- Full legal name
- Email address
- Date of birth
- Country
- Historical information (username changes)
- IP addresses
- Telephone numbers
Account Control Capabilities:
- Password reset functionality
- Account access grants
- Ability to modify account details
The Criminal Business Model:
Threat actors could use bribed support access to:
- Dox people - Harvest personal information for harassment, swatting, or identity theft
- Steal accounts - Reset passwords and sell high-value accounts on underground markets
- Facilitate social engineering - Use harvested data for targeted phishing or further account compromises
Proof: June 2025 Screenshot
VX-Underground shared photographic evidence from June 2025 showing helpdesk employees demonstrating their panel access - proving this vulnerability persisted at least through mid-2025, months before the December 27 breach.
Ubisoft's Response (or Lack Thereof)
According to VX-Underground:
"Ubisoft has internally taken action against rogue Helpdesk agents. However, despite their actions of firing these Bad Actors, or threatening them with legal action, the issue remains somewhat persistent."
Translation: Ubisoft knows about the problem, has fired some staff and threatened legal action, but has not fixed the underlying systemic issues that allow bribery to continue.
Not Unique to Ubisoft
VX-Underground notes this insider threat pattern has plagued multiple companies:
- xAI (Twitter/X AI division)
- PlayStation
- T-Mobile
- AT&T
- The United States Government
- Rockstar Games
- Discord
- Coinbase
- "...and (probably) many more"
The gaming "hacker/leak scene" community apparently knew about Ubisoft's helpdesk bribery for years, though VX-Underground notes "many others were unaware of this issue" until the December 2025 disclosure.
The Convergence: Why Two Separate Issues Expose Systemic Failure
Different Attack Vectors, Same Broken Security Culture
The simultaneous revelation of these two crises—the game service API exploitation (NOT MongoBleed) and the multi-year helpdesk corruption—exposes systemic security failures at Ubisoft:
Technical Failures:
- Game service APIs with insufficient authentication/authorization controls
- Backend systems that accepted malicious admin-level commands as "legitimate"
- Lack of rate limiting or anomaly detection on inventory/currency operations
- Inadequate logging and monitoring of administrative actions
- No apparent security testing of game service endpoints
Human/Process Failures:
- Outsourced support operations without adequate oversight for 4+ years (2021-2025)
- No detection of bribery patterns despite ongoing corruption
- Insufficient background checks and security training for support staff
- Economic incentives where bribes (potentially $500-1000) exceed monthly wages for support workers
- Firing individual bad actors without addressing systemic vulnerabilities
The Compounding Effect:
While Group 1's December 27 breach used game service exploitation (NOT helpdesk bribery), the existence of both vulnerabilities simultaneously creates a "swiss cheese" security model:
- If game APIs are exploitable → Backend chaos, virtual economy destruction
- If helpdesk staff are bribable → Account theft, PII exposure, social engineering
- If both exist together → No trust in ANY part of Ubisoft's infrastructure
Even worse: Group 2 had Ubisoft source code for an extended period (obtained through methods Group 5 documented but hasn't publicly released). This suggests a third parallel vulnerability beyond both the game services AND the helpdesk issues.
Four Hacker Groups
As detailed above, at least four groups simultaneously exploited Ubisoft during this crisis period, though the helpdesk bribery scheme and MongoBleed exploitation appear to be separate attack vectors used by different actors.
The Outsourced Support Vulnerability
Why Helpdesks Are Prime Targets
Customer support operations represent a critical attack surface that organizations frequently overlook:
Economic Pressures:
- Support staff often earn significantly less than technical employees
- Financial incentives from bribes can exceed months of legitimate wages
- Cost-cutting outsourcing creates quality and oversight gaps
Access Privileges:
- Customer service panels have elevated permissions by design
- Support agents can reset passwords, modify account details, and access personal data
- Administrative tools often lack adequate logging or oversight
Training Deficiencies:
- Rapid staff turnover reduces institutional security knowledge
- Security awareness training frequently deprioritized for support roles
- Lack of experience detecting social engineering and suspicious requests
Geographic Distribution:
- Oversight challenges across multiple time zones and jurisdictions
- Cultural and language barriers complicate security policy enforcement
- Different regulatory environments create compliance gaps
Industry-Wide Pattern
Ubisoft is far from alone. Similar helpdesk compromise incidents include:
- Roblox (2020): Support staff bribed to reset passwords and facilitate account theft
- PlayStation Network: Attackers targeting underpaid workers for account access
- Adidas (May 2025): Customer support provider hacked, compromising user information
- Multiple gaming platforms: Ongoing reports of social engineering attacks against support personnel
According to the 2024 Insider Threat Report by Cybersecurity Insiders:
- 76% of organizations detected increased insider threat activity over five years
- 74% of cybersecurity professionals are most concerned with malicious insiders (up from 60% in 2019)
- 29% of organizations report remediation costs exceeding $1 million per incident
- 89% of malicious insider breaches are motivated by personal financial gain
Ubisoft's Response: Swift But Incomplete
What Ubisoft Did Right
Speed of Response:
- Acknowledged the breach within hours of first player reports
- Shut down servers and marketplace within 30 minutes of confirmation
- Immediately communicated no-ban policy to prevent player panic
- Began rollback process same day
Player-Friendly Policies:
- No bans for players who received or spent illicit credits
- Transparent communication via official X account
- Commitment to account integrity via quality control testing post-rollback
What Ubisoft Has NOT Addressed
The Helpdesk Bribery Scandal: Ubisoft has made zero public statements regarding the VX-Underground allegations of support staff accepting bribes since 2021. No acknowledgment of:
- Whether the helpdesk bribery allegations are true
- What investigations have been conducted into outsourced support operations
- Whether any support staff have been terminated or prosecuted
- What corrective measures are being implemented for third-party vendors
The Source Code Mystery:
- No explanation of how Group 2 obtained Ubisoft source code (Group 5 knows but hasn't shared publicly)
- No disclosure of what source code was compromised or when the breach actually occurred
- No confirmation whether the "1990s to present" claim is accurate
- Group 5 promises technical write-up "at a later time" once Group 1/Group 2 drama settles
Player Data Exposure:
- No confirmation whether player personal data was compromised in December 27 breach
- Group 1 reportedly did NOT access user data (per VX-Underground)
- Group 3's claims of user data theft deemed FAKE by VX-Underground
- However, helpdesk bribery scheme means PII was accessible to threat actors since 2021
Recovery Timeline:
- Servers remain offline as of December 28 with no ETA for restoration
- "Extreme care" and "quality control testing" mentioned but no specifics
- Community frustration growing with vague updates
Recommended Immediate Actions for Players
Security experts recommend Rainbow Six Siege players:
- Change Ubisoft password immediately and enable two-factor authentication (2FA)
- Remove payment methods from Ubisoft accounts temporarily
- Monitor financial statements for unauthorized charges
- Stay offline until Ubisoft provides all-clear confirmation
- Be wary of phishing emails claiming to be from "Ubisoft Support"
- Do not respond to unsolicited account recovery requests
What We Got Wrong (And What VX-Underground Corrected)
Early Reporting vs. Current Understanding
Initial Narrative (Dec 27-28):
- Attackers used MongoBleed (CVE-2025-14847) to breach Ubisoft
- MongoDB vulnerability allowed database compromise
- Four hacker groups involved
Corrected Narrative (After VX-Underground Investigation):
- MongoBleed was a LIE told by Group 2 to cover their tracks
- December 27 breach was game service API exploitation, not database breach
- FIVE hacker groups, including Group 5 who exposed the lies
- Group 2 HAD source code but obtained it through different means (not yet publicly disclosed)
- Group 3 is completely fake, using fabricated data for extortion
Why This Matters:
The security industry initially focused on MongoDB patching and database hardening based on false Group 2 claims. The real vulnerability was in Ubisoft's game service authentication/authorization - a completely different attack surface requiring different defensive measures.
This is a cautionary tale about:
- Not taking initial breach claims at face value
- Waiting for technical validation before recommending remediation
- Understanding that threat actors lie strategically to misdirect defenders
Credit Where Due: VX-Underground's continued investigation and Group 5's technical intervention prevented the industry from chasing the wrong threat model.
Lessons for Enterprise Security
1. Third-Party Risk Management Failures
The Problem: Organizations treat outsourced support as a commodity service rather than a critical security function.
The Solution:
- Conduct rigorous security audits of all outsourced providers
- Implement mandatory security training and certification for support staff
- Require background checks and security clearances for personnel with elevated access
- Establish clear contractual security requirements with financial penalties
2. Insufficient Access Controls
The Problem: Support panels grant excessive privileges without adequate monitoring or time-based restrictions.
The Solution:
- Implement principle of least privilege for all support tools
- Use just-in-time access that requires manager approval for sensitive operations
- Deploy session recording and monitoring for all administrative actions
- Create anomaly detection for unusual support panel activity patterns
3. Detection and Response Gaps
The Problem: Organizations lack visibility into insider threat indicators until catastrophic damage occurs.
The Solution:
- Deploy User and Entity Behavior Analytics (UEBA) to detect anomalous access patterns
- Monitor for unusual after-hours activity, geographic anomalies, and bulk data access
- Implement data loss prevention (DLP) to prevent unauthorized exfiltration
- Create automated alerting for high-risk support actions (password resets, bulk account access)
4. Cultural and Compensation Issues
The Problem: Underpaid, undervalued support staff are vulnerable to bribery and corruption.
The Solution:
- Pay competitive wages that reduce financial incentive for corruption
- Create whistleblower protection programs that reward reporting of bribery
- Foster a security-conscious culture where support staff understand their role in protecting users
- Recognize and reward security-conscious behavior
The MongoDB Dimension: CVE-2025-14847
The MongoBleed vulnerability adds a technical exploitation layer to the insider threat:
Technical Details:
- Allows unauthenticated remote attackers to leak memory from exposed MongoDB instances
- Public proof-of-concept exploit already released
- Approximately 87,000 MongoDB servers exposed globally
- Can expose credentials, authentication keys, and sensitive configuration data
Cascading Impact:
- Stolen credentials enable pivoting to internal systems
- Combined with insider access, creates devastating attack chains
- Organizations using MongoDB must immediately patch and audit exposed instances
Recommendations for Gaming Companies
Immediate Actions
- Audit all outsourced support relationships for security gaps
- Implement mandatory multi-factor authentication for all support panel access
- Review and restrict support tool permissions to minimum necessary
- Deploy continuous monitoring of support account activity
- Patch MongoDB instances and audit for CVE-2025-14847 exposure
Strategic Initiatives
- Develop comprehensive insider threat programs that specifically address support operations
- Create financial incentives for support staff to report bribery attempts
- Implement zero-trust architecture where no account or system is trusted by default
- Conduct regular tabletop exercises simulating insider threat scenarios
- Establish incident response playbooks specifically for insider-facilitated breaches
Policy Recommendations
- Require security awareness training for all support personnel quarterly
- Implement separation of duties so no single support agent can execute high-risk actions alone
- Create audit trails for all support activities with 5+ year retention
- Deploy deception technology (honeypot accounts) to detect unauthorized access
- Mandate security assessments before outsourcing any customer-facing operations
The $339 Trillion Question
The Ubisoft breach raises fundamental questions about the gaming industry's security maturity:
- How many other gaming companies have similar helpdesk vulnerabilities?
- What is the true scope of bribery-facilitated account compromises since 2021?
- Why did it take a catastrophic public breach to expose a three-year insider threat?
- What personal data has been exfiltrated through bribed support channels?
The reality is sobering: According to industry research, 48% of organizations experienced more frequent insider attacks in the past 12 months, yet only 29% believe they have the right tools to address the threat.
The Ubisoft incident demonstrates that technical security measures are worthless when insiders sell the keys to the kingdom for cash.
Conclusion: When Lies, Corruption, and Chaos Converge
The Rainbow Six Siege crisis is a masterclass in how complex modern security incidents actually are:
The December 27 Technical Attack:
- NOT MongoBleed (that was Group 2 lying)
- Game service API exploitation by skilled reverse engineers (Group 1)
- $339 trillion virtual currency disaster
- Complete server shutdown lasting days
- Likely required deep understanding of Ubisoft's game architecture
The Multi-Year Human Attack:
- Outsourced helpdesk corruption since at least 2021
- Persistent despite Ubisoft firing staff and threatening legal action
- Proof as recent as June 2025 that the scheme continues
- Systemic economic/oversight issues, not individual bad actors
The Source Code Mystery:
- Group 2 has Ubisoft source code but lied about how they got it
- Group 5 knows the truth but hasn't shared publicly (yet)
- Possible third parallel vulnerability beyond game services and helpdesk
The Misinformation Campaign:
- Group 3 fabricating user data breaches for extortion
- Group 2 weaponizing MongoBleed narrative to justify leaking source code
- Multiple imposter groups emerging to capitalize on chaos
- Security industry initially chasing wrong threat model
The Real Lessons
For Defenders:
- Game service APIs are attack surfaces - Authentication/authorization on backend game services needs same rigor as external APIs
- Reverse engineering communities know your systems better than you do - Groups 1 and 5 are cheat developers who deeply understand Ubisoft's architecture
- Outsourcing support = outsourcing trust - Bribery schemes persist when economic incentives favor corruption
- Initial breach narratives are often wrong - Wait for technical validation before pivoting defensive strategies
- Threat actors lie strategically - MongoBleed claims were cover story to misdirect investigators
For the Industry:
The gaming sector continues treating security as an afterthought despite:
- $200+ billion annual revenue
- Massive player PII databases
- Real-money virtual economies
- Sophisticated adversaries (cheat developers, nation-states, organized crime)
Ubisoft's dual crisis proves that scale and revenue don't correlate with security maturity.
The Open Questions
As of December 28, 2025:
- When will Group 5 release their technical write-up? (Waiting for Group 1/2 drama to settle)
- How DID Group 2 actually get the source code? (Group 5 has proof but hasn't shared)
- Will Group 2 leak the source code? (Positioning suggests extortion attempt)
- Has Ubisoft fixed the helpdesk bribery systemic issues? (Evidence suggests no)
- What were the actual game service API vulnerabilities? (Group 5 knows, hasn't disclosed)
The Bottom Line
Rainbow Six Siege has survived for a decade because it's exceptional. But you can't patch culture, and you can't firewall corruption.
Ubisoft faces:
- Immediate: Server restoration, rollback completion, player trust recovery
- Medium-term: Source code extortion, regulatory investigations, helpdesk reform
- Long-term: Rebuilding security culture from game services to support operations
The $339 trillion price tag isn't just virtual currency—it's the cost of:
- Years of ignored insider threats
- Unpatched game service vulnerabilities
- Economic systems that incentivize corruption
- Technical debt in critical infrastructure
- A security team apparently outmatched by cheat developers
VX-Underground summarized it best: "The anime saga has concluded."
But for Ubisoft's security team, the work has just begun.
UPDATE PROMISE: This article will be updated when Group 5 releases their technical write-up detailing exactly how Groups 1 and 2 achieved their respective breaches. VX-Underground has confirmed this documentation is coming "at a later time.






